This time, I'll try out the setodaNote CTF web.
"setodaNote CTF: https://ctfexh.setodanote.net/About "
The setodaNote CTF is a permanent CTF that was held in 2021, and in terms of difficulty, it is equivalent to an introductory level.
If anyone is thinking of starting CTF, I think you'll enjoy it if you try it!
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Body
When I opened the above URL, I was taken to the following screen.
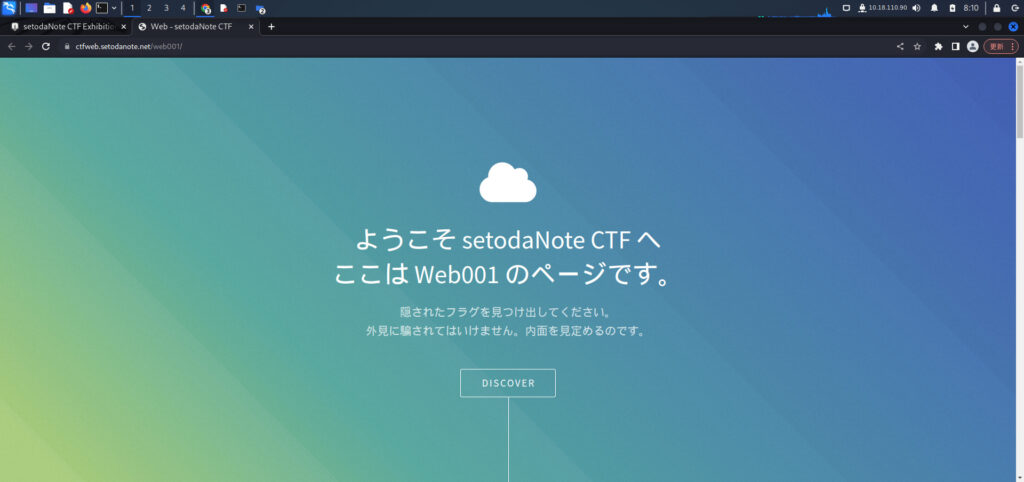
While looking up Body because the title is Body, I found a flag that was commented out!
Answer
flag{Section_9}Header

When I opened the above URL, I got a screen like this:

Next, I was looking up the Header, and when I found a flag!
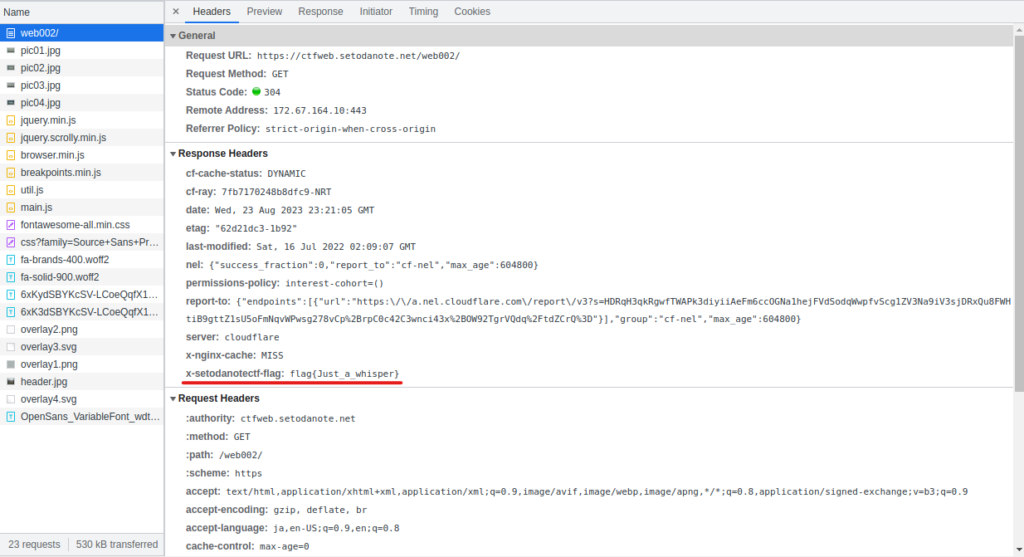
Answer
flag{Just_a_whisper}puni_puni
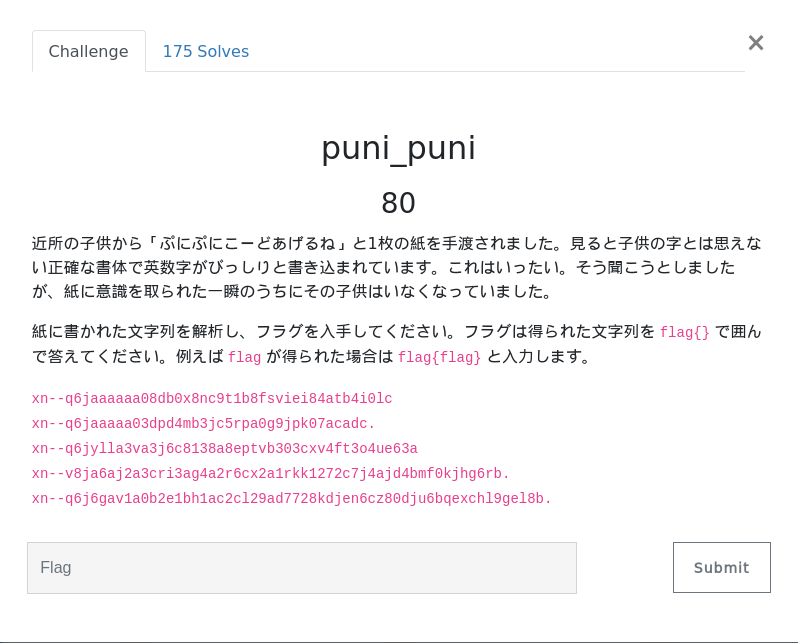
This one is a bit special. It's a Punycode issue.
Punycode is one of the encoding methods that convert Unicode strings into alphabets, numbers, and hyphens to enable internationalized domain names to be used in existing DNS!

You can convert it on the site like the one above.
Anyway, I tried converting it.
The flags are san, san, pe, u, n, y, c, o, dy, yon, yon, yon, yon, katakana notation is in lowercase letters, while hiragana notation is in half-width digit numbers. Please remove the flags as commas are delimited characters.It seems that you should create a flag based on this sentence.
Answer
flag{33punycode44}Mistake
It appears that confidential information has been leaked from the site being created.
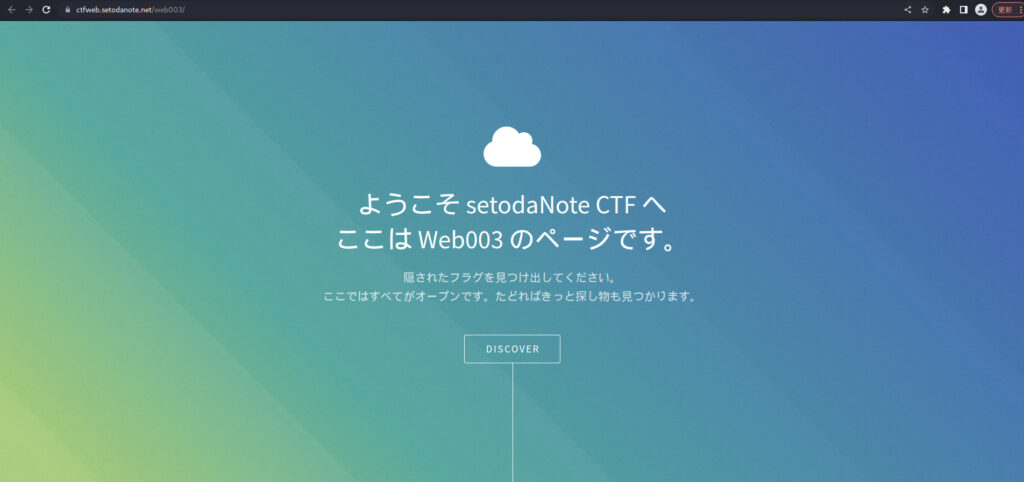
Thankfully, he gives us a polite hint, "Everything is open here. If you follow it, you'll be sure to find what you're looking for."
Judging from the above, I thought it wasn't a directory listing.
So, for now, let's look at the visible directories "/assets/" and "/images/".
I took a look at "/assets/", but it seems there is no information about this.

There was a flag in "/images/"!

Answer
flag{You_are_the_Laughing_Man,_aren't_you?}tkys_royale
When I opened the above URL, I got a login form.
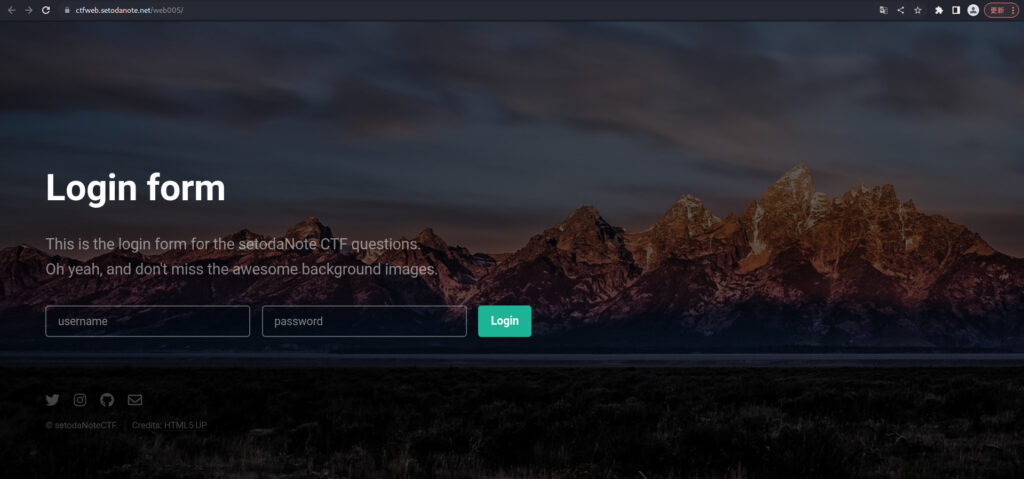
Anyway, while looking at the source, I discovered a test user.
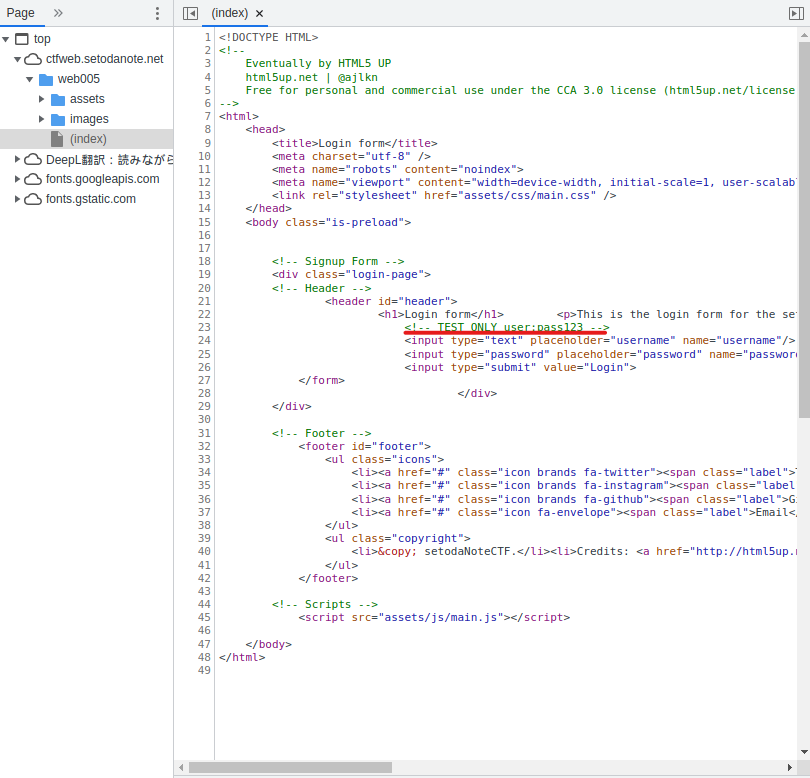
When I logged in, I was told, "You need to be logged in as admin to find the flag."
You are likely to be able to log in using the username "addmin".
Just to be safe, I tried logging in with "admin:admin" or "admin:pass123", but it didn't work.
Next, try SQL injection.
admin:' OR 1 = 1; #I was able to log in and get the flag!

Answer
flag{SQLi_with_b1rds_in_a_b34utiful_landscape}Estimated
It appears that confidential information has been leaked on the blog. When I looked at the URL, I saw the blog.
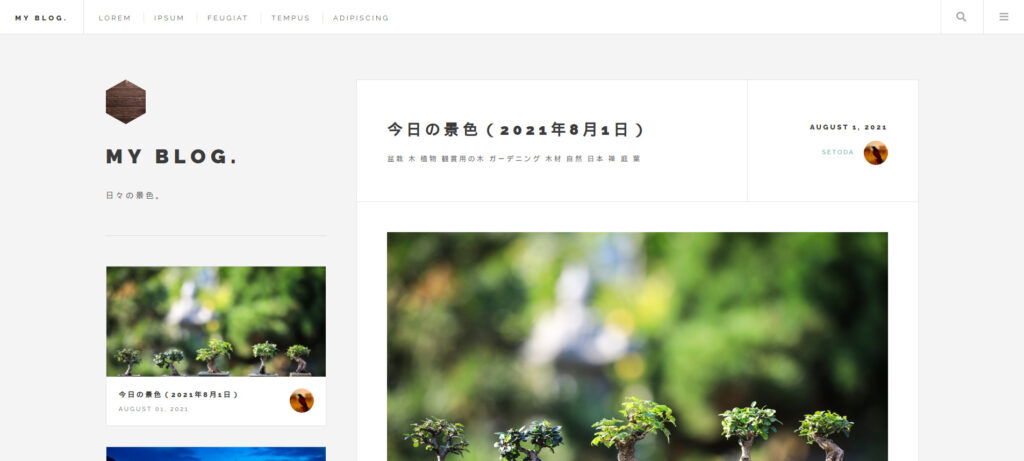
I clearly found an apology article for this incident.
In terms of content, there seems to be a flag in the image.

The image naming convention appears to be "YYYYMMDD001b.jpg".
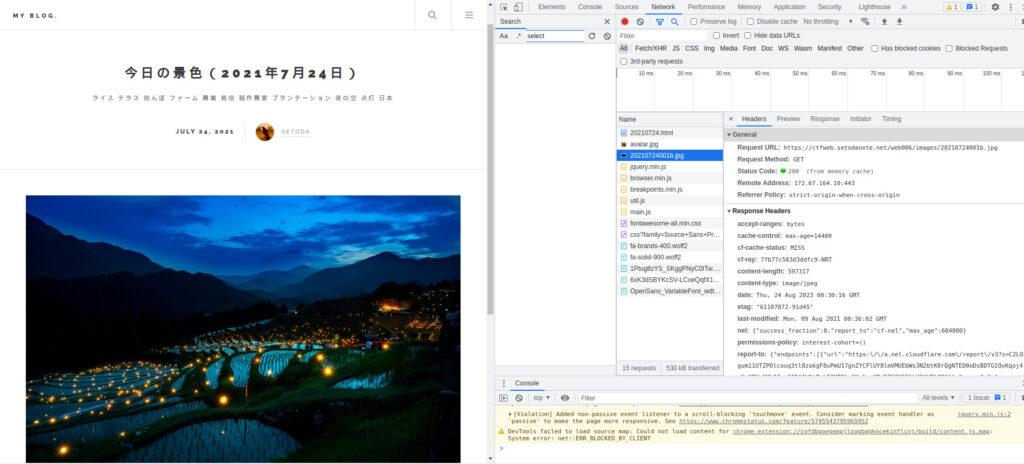
The inappropriate images are one day before June 3, 2021, so they will be June 2, 2021.
This image should probably be "20210602001b.jpg".
I've managed to get the image.

I was looking for a lot from here, but when I enlarged the PC section of the image, I found a flag. . .
Answer
flag{The_flag_wouldn't_like_to_end_up_in_other_peoples_photos}Mx.Flag
The above URL has a letter-like website.
After looking at various things, I noticed that favicon.png was loaded.
However, if you look closely, the favicon is not displayed, so it looks suspicious.

When I checked the meta information using exiftool, it appears that the image was just a txt.
┌──(hacklab㉿hacklab)-[~] └─$ exiftool favicon.png ExifTool Version Number: 12.65 File Name: favicon.png Directory: . File Size: 122 bytes File Modification Date/Time: 2023:08:24 09:49:22+09:00 File Access Date/Time: 2023:08:24 09:49:22+09:00 File Inode Change Date/Time: 2023:08:24 09:49:28+09:00 File Permissions: -rw-r--r-- File Type: TXT File Type Extension: txt MIME Type: text/plain MIME Encoding: us-ascii Newlines: Windows CRLF Line Count: 3 Word Count: 10So, when I checked the contents, I was able to find the flag.
┌──(hacklab㉿hacklab)-[~] └─$ cat favicon.png // flag{Mr_Flag_hiding_in_the_favicon} console.table({place: "favicon.png", png: "false", flag: "true", Look: "me"});
Answer
flag{Mr_Flag_hiding_in_the_favicon}Redirect
There was a blog site. It's called Redirect, so I'll look into redirects.
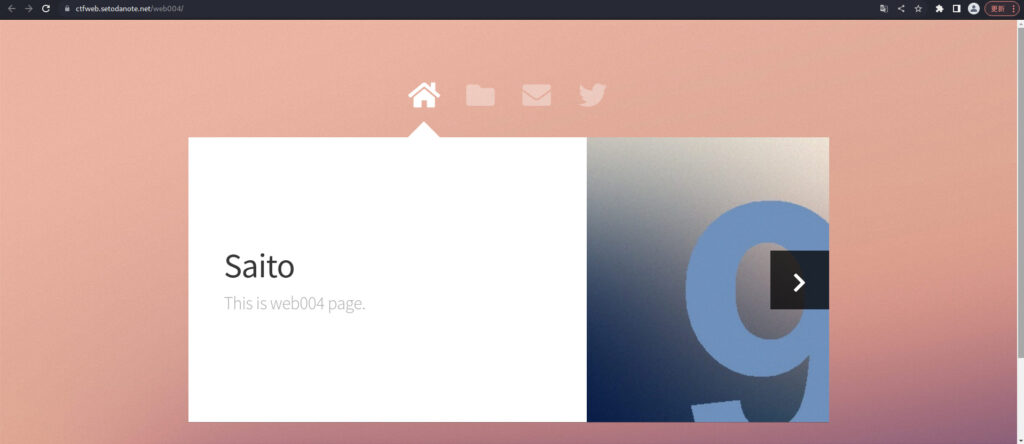
<script>!function(){var ref = document.referrer;var domain = ref.match(/^http([s]?):\/\/([a-zA-Z0-9-_\.]+)(:[0-9]+)?/)[2];if(domain == "www.google.com" || domain == "www.google.co.jp" ){location.href = atob('Li9iV0ZzYTJsMC5odG1s');}}();</script>I found that decoding in Base64 redirects to "./bWFsa2l0.html".
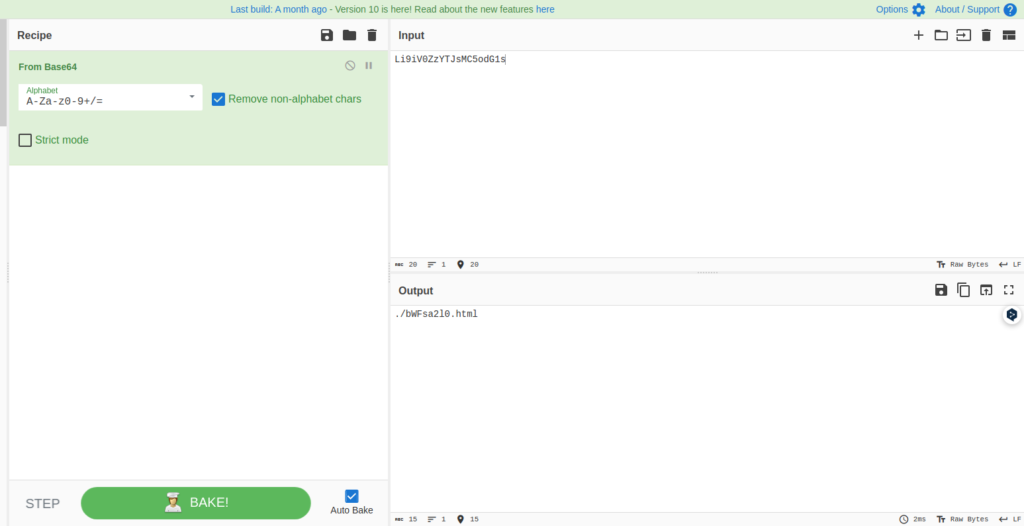
It's difficult to actually redirect, so I'll use API testers.
<!DOCTYPE HTML><html><head><title>start</title><noscript><meta http-equiv=refresh content="1; URL=./noscript.html"></noscript><script> !function() { var params = new URL(window.location.href).searchParams; if(Array.from(params).length > 0){ location.href = './bm9mbGFn/?'+params; }else{ location.href = './bWFsa2l0.html?callback=wantFlag&data1=2045&data2=0907&data3=BiancoRoja&data4=1704067200'; } }(); </script></head><body><p>Find out the flag.</p></body></html>When I checked the contents of the HTML to which I was redirected, it appears that I'm redirecting further.
if(Array.from(params).length > 0){ location.href = './bm9mbGFn/?'+params; }else{ location.href = './bWFsa2l0.html?callback=wantFlag&data1=2045&data2=0907&data3=BiancoRoja&data4=1704067200'; }As far as you can see above, you should make a request as follows:
./bm9mbGFn/?callback=wantFlag&data1=2045&data2=0907&data3=BiancoRoja&data4=1704067200Let's make a request.

<html><head><title>Next</title><noscript><meta http-equiv=refresh content="1; URL=../noscript.html"></noscript><script> !function() { var params = new URL(window.location.href).searchParams; location.href = '../bmV4dG5leHQ/?'+params }(); </script></head><body><p>No flag here. Go to next.</p></body></html>It appears to be redirected again.
The parameters are redirected to "../bmV4dG5leHQ/" with the same parameters.

<html><head><title>Next-Next</title><noscript><meta http-equiv=refresh content="1; URL=../noscript.html"></noscript><script> !function() { var params = new URL(window.location.href).searchParams; location.href = '../b25lLXR3by10aHJlZQ/?'+params }(); </script></head><body><p>No flag here too. Go to next.</p></body></html>It seems that it's still being redirected.
We will redirect the system in the way we have done up until now.

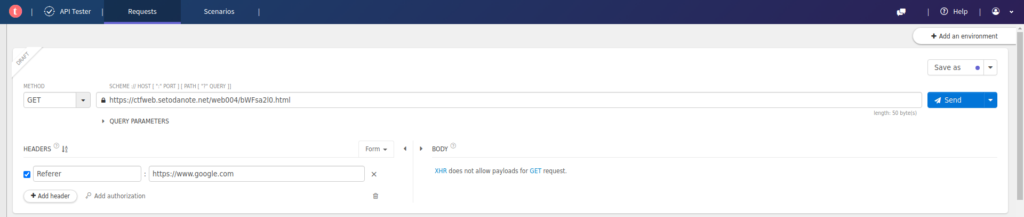
<html><head><title>Branching point</title><noscript><meta http-equiv=refresh content="1; URL=../noscript.html"></noscript><script> !function() { var params = new URL(window.location.href).searchParams; if (params.get('callback') == 'getFlag') { location.href = '../dGFjaGlrb21hX2thd2FpaV95b25l/?' + params; }else{ location.href = '../ZGFtbXlmbGFn/?' + params; } }(); </script></head><body><p>You need the correct parameters to get the flag.</p></body></html>if (params.get('callback') == 'getFlag') { location.href = '../dGFjaGlrb21hX2thd2FpaV95b25l/?' + params;I want to enter this, so I'll turn the callback parameter into getFlag and let it redirect.
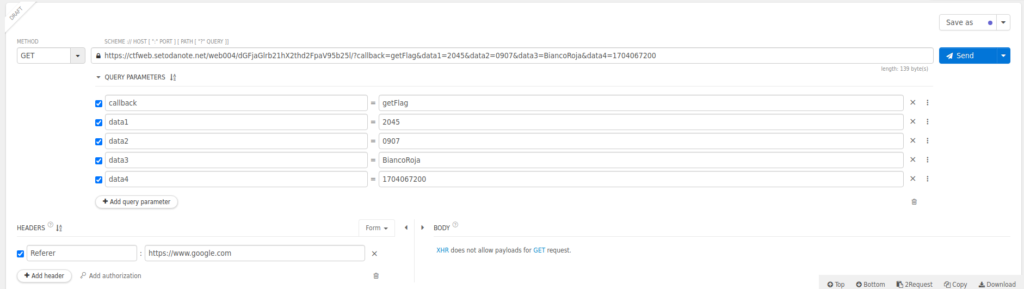
<html><head><title>GO!GO!GO!GO!</title><noscript><meta http-equiv=refresh content="1; URL=../noscript.html"></noscript><script> !function() { var params = new URL(window.location.href).searchParams; var callback = params.get('callback'); var data1 = params.get('data1'); var data2 = params.get('data2'); var data3 = params.get('data3'); var data4 = params.get('data4'); if (callback == 'getFlag' && data1 == "2045" && data2 =="0907" && data3 == "BiancoRoja" && data4 =="1704067200") { location.href = 'https://noisy-king-d0da.setodanote.net/?'+params; }else{ location.href = '../ZGFtbXlmbGFn/hint.html?'+params; } }(); </script></head><body><p>Yes! Go to next.</p></body></html>This seems to be the last one. Let's redirect the parameters as they are.
if (callback == 'getFlag' && data1 == "2045" && data2 == "0907" && data3 == "BiancoRoja" && data4 ==="1704067200") { location.href = 'https://noisy-king-d0da.setodanote.net/?'+params;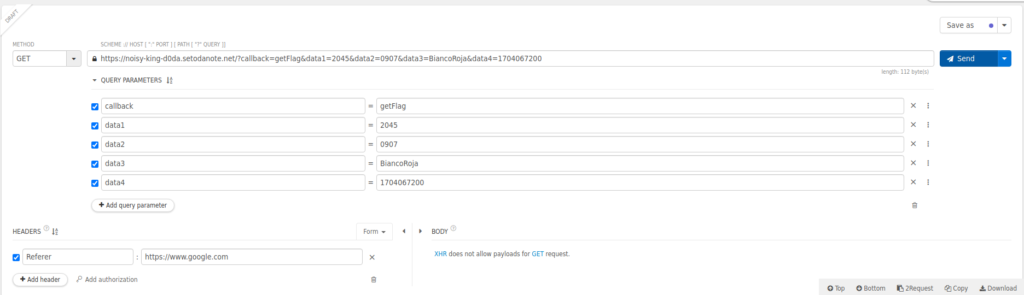
<!DOCTYPE html><body><h1>Nice work!!</h1><p> flag{Analyz1ng_Bad_Red1rects}</p></body>I got the flag!
Answer
flag{Analyz1ng_Bad_Red1rects}summary
This time, I tried out the setodaNote CTF web!
Since it is for beginners, it was more like solving puzzles than using knowledge, but I think it's a fun first step towards starting CTF.
References and Sites
--


![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053] I tried hacking it using the SQL injection vulnerability in CMS Made Simple! (Python3) TryHackMe Simple CTF Writeup](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)