This time, we will try out CTF based on TryHackME's Resident Evil.
This is my first time doing CTF like a game, so I'm also curious to see what it will be like!
"TryHackMe-Biohazard: https://tryhackme.com/room/biohazard "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Introduction
Start the target machine from "Start Machine".
As long as the IP Address is displayed, it's OK!
Deploy the machine and start the nightmare
This does not require an answer, so once the target machine is booted, it should be done.
Answer

How many open ports?
Find an open port. I use nmap.
┌──(hacklab㉿hacklab)-[~] └─$ nmap -sV 10.10.156.237 Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-20 20:16 JST Nmap scan report for 10.10.156.237 Host is up (0.24s latency). Not shown: 997 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 39.76 secondsAnswer

What is the team name in operation
http is open, so try accessing it from your browser.
The team name is listed here.
Answer

The Mansion
and
advanced to the next level. The format of the Item flag:
Item_name{32 character} the
doors are locked. Use the item flag to unlock the door. Tips: It is better to
record down
all the information inside a notepad
It seems they will collect item flags and conquer them.
What is the emblem flag
First, look for emblem flag.
There is a link that will move to Main Hall, so let's select it.
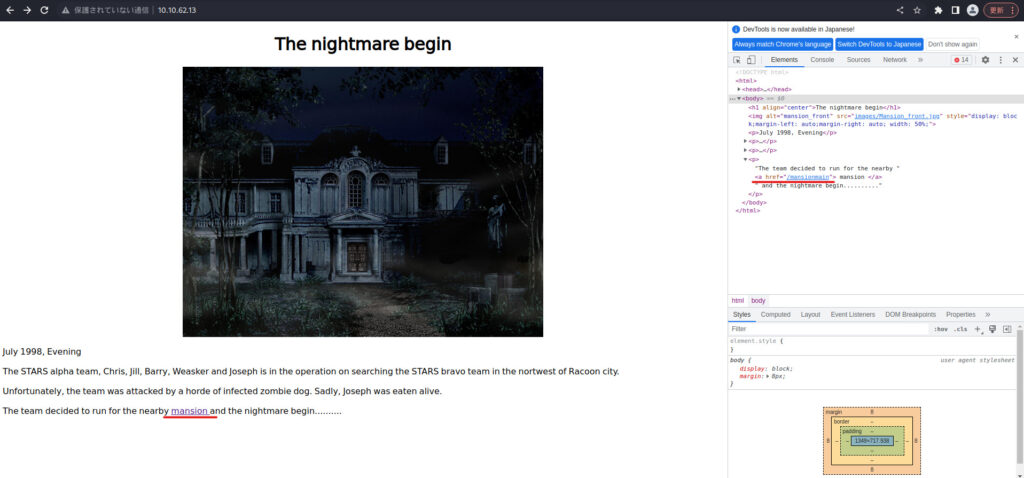
I've moved to Main Holl.
The source comment stated the following:
<!-- It is in the /diningRoom/ -->I'll try moving to Dining Room.
Let's select YES.
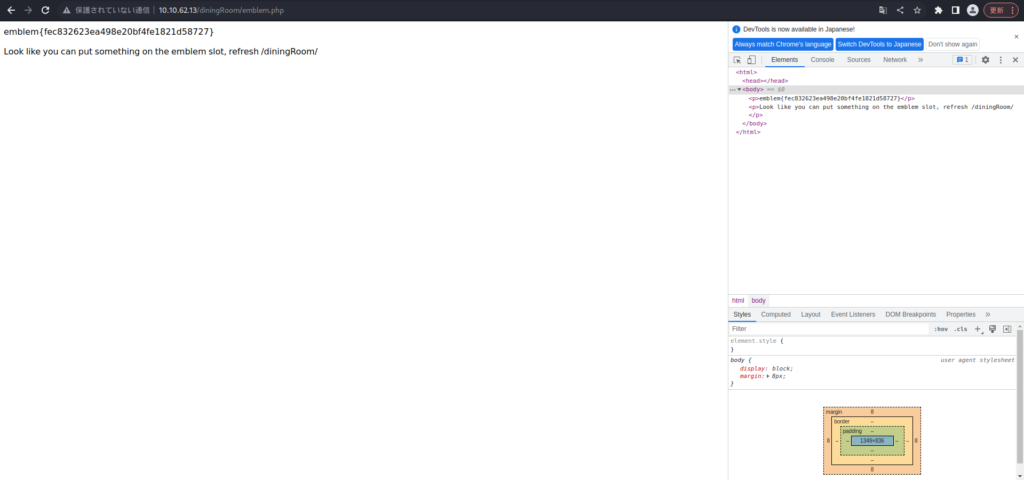
emblem{fec832623ea498e20bf4fe1821d58727} Look like you can put something on the emblem slot, refresh /diningRoom/There was a flag and it also says to refresh /diningRoom/.
Answer

What is the lock pick flag
Look like you can put something on the emblem slot, refresh /diningRoom/
(I think something can be put on the emblem slot, refresh /diningRoom/.)
I'll try to refresh as I said earlier.
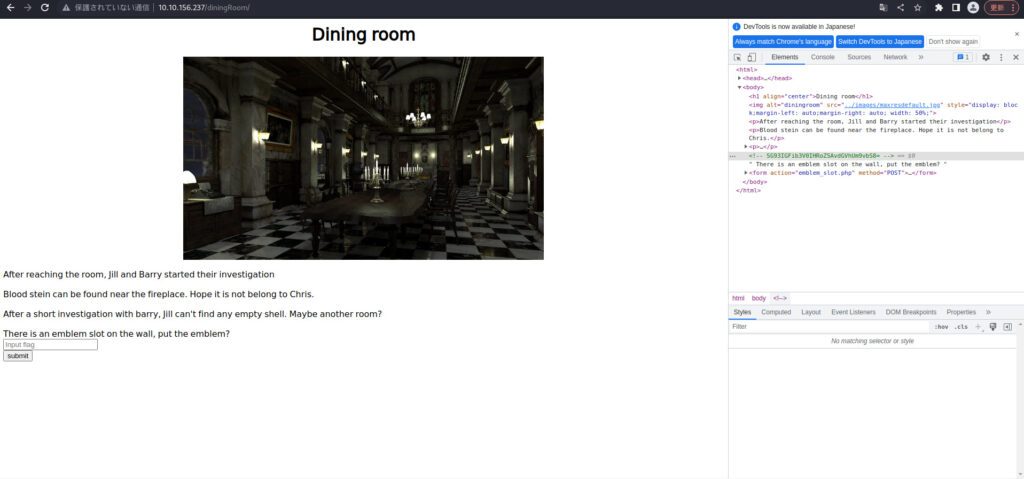
There was a place where I had to enter emblem flag.
I'll try entering what I got just now.
Apparently it's not. . .
There is a hash in the source of the Dining room, so I analyzed it.
<!-- SG93IGFib3V0IHRoZSAvdGVhUm9vbS8= -->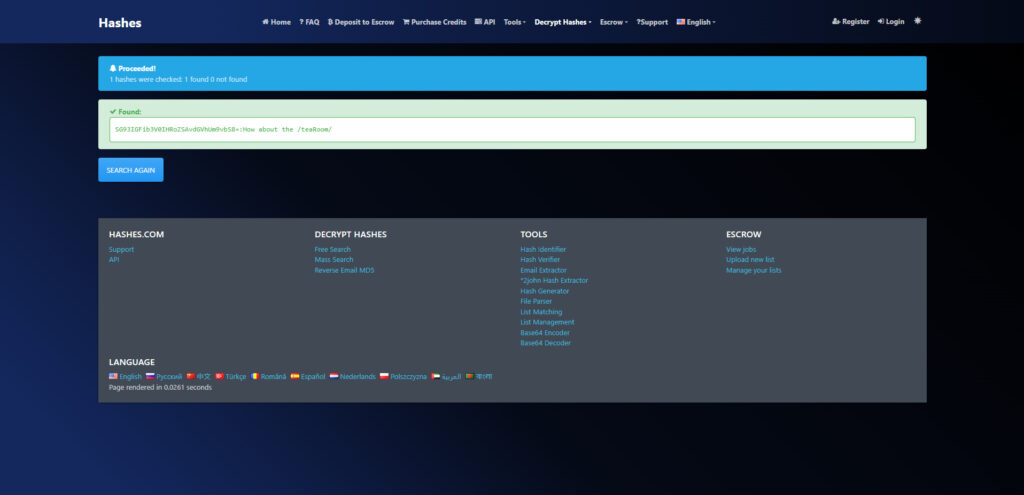
┌──(hacklab㉿hacklab)-[~] └─$ echo "SG93IGFib3V0IHRoZSAvdGVhUm9vbS8=" | base64 -d How about the /teaRoom/ I found it to be encoded in base64.
Just follow the instructions to move to Tea Room.
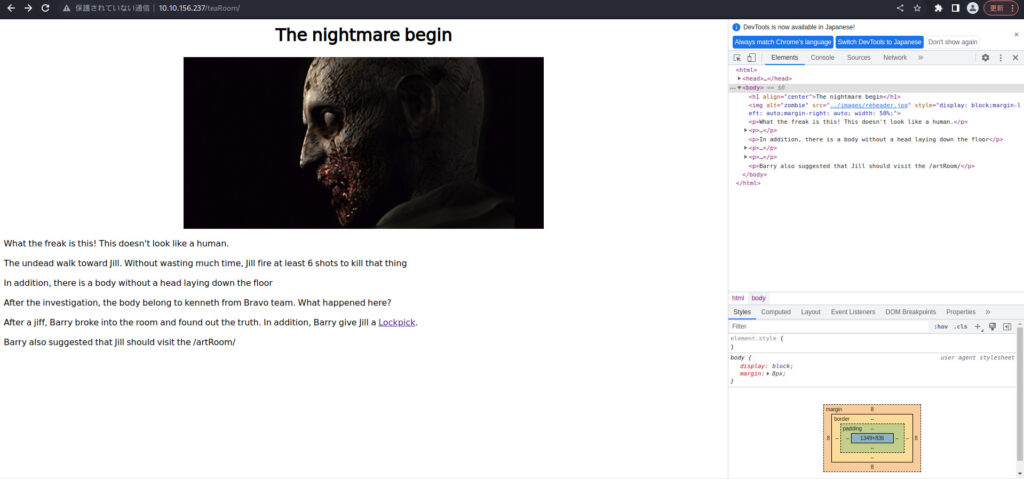
Try pressing the Lockpik link.
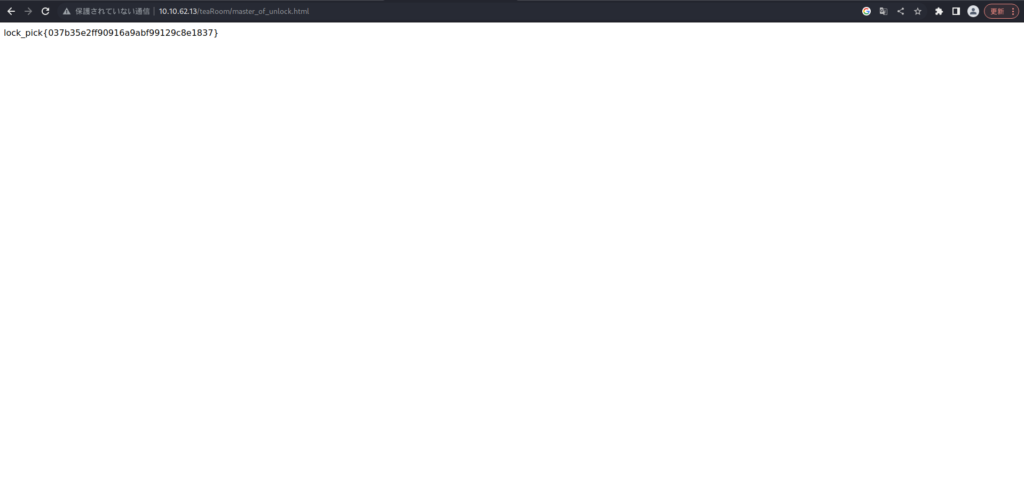
There was a lock pick flag!
Answer

What is the music sheet flag
This is the Tea Room pass from earlier.
It says "Barry also suggested that Jill should visit the /artRoom/", so I'll try moving to Art room.
Let's press YES.
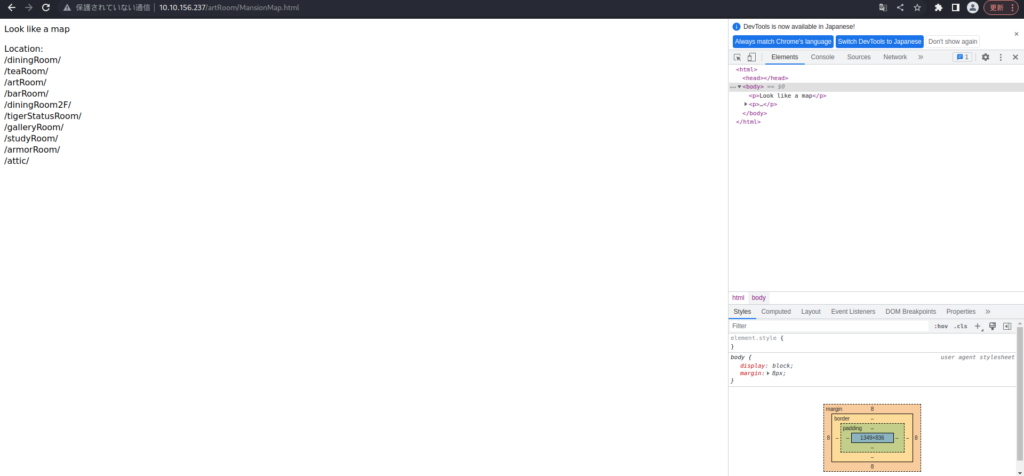
Look like a map Location: /diningRoom/ /teaRoom/ /artRoom/ /barRoom/ /diningRoom2F/ /tigerStatusRoom/ /galleryRoom/ /studyRoom/ /armorRoom/ /attic/Apparently it's information about the directory (room).
Let's move to a directory you've never mentioned before.
Enter the lock pick flag you just got and submit.
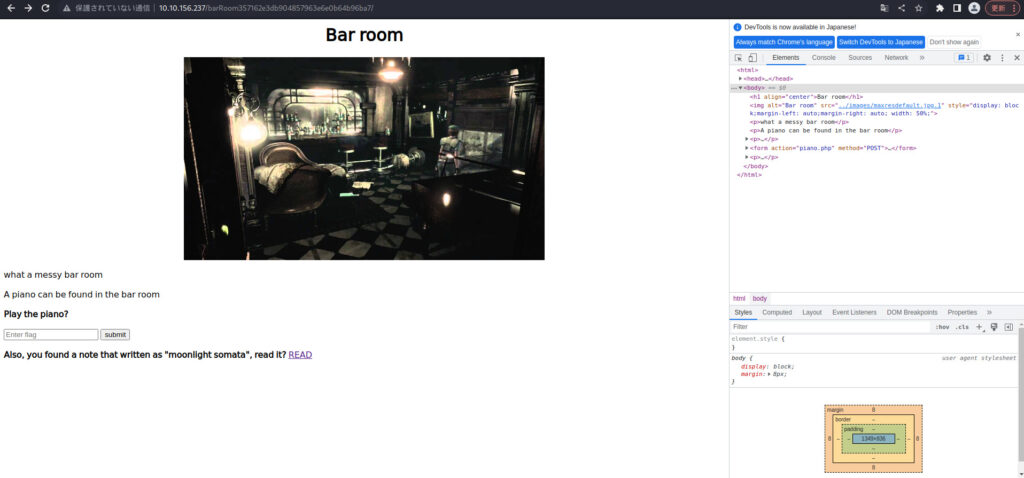
I put it in the Bar Room.
Let's select READ.
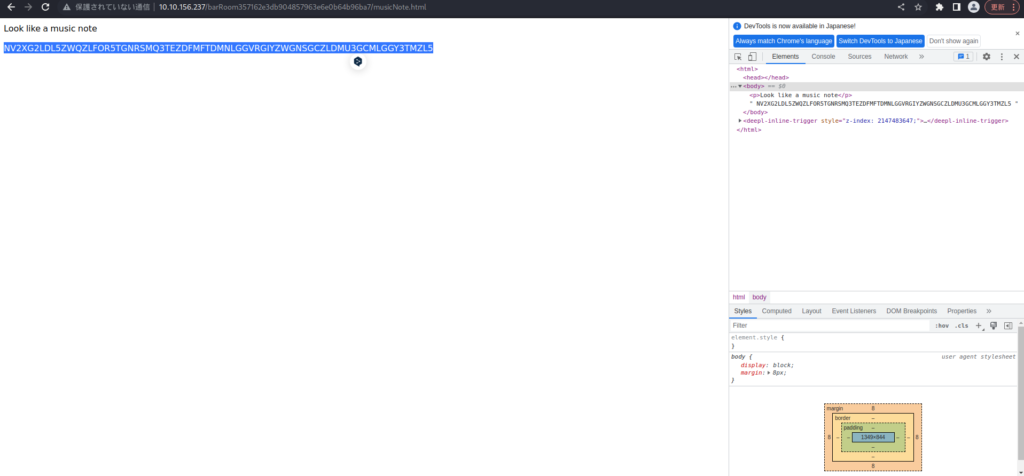
NV2XG2LDL5ZWQZLFOR5TGNRSMQ3TEZDFMFTDMNLGGVRGIYZWGNSGCZLDMU3GCMLGGY3TMZL5Once again, there's a hash. . .
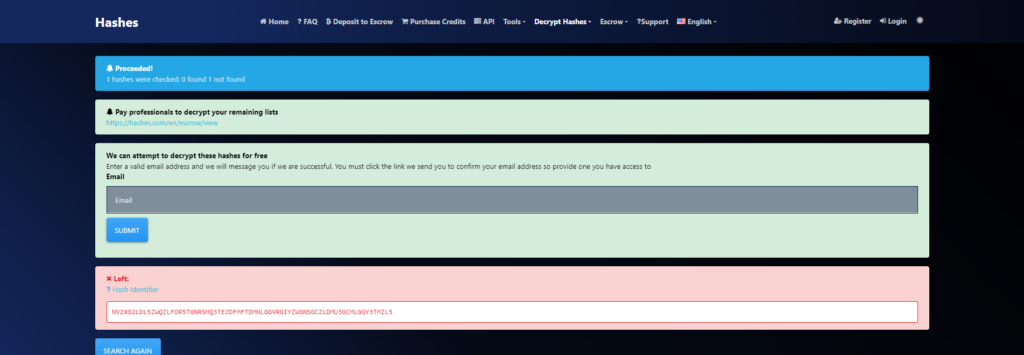
Since there were no matches, I tried out various things using https://gchq.github.io/CyberChef/

music_sheet{362d72deaf65f5bdc63daece6a1f676e}After trying it, I found that it was encoded in base32. Is there a better way to do it? . .
Answer

What is the gold emblem flag
I've returned to Bar Room.
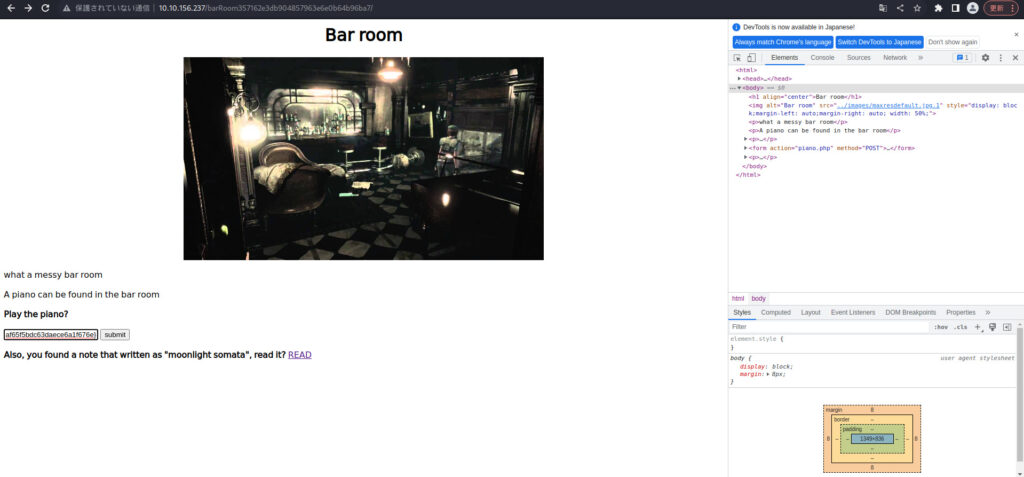
Now that you know the music_sheet, enter it and submit.

Let's select YES.
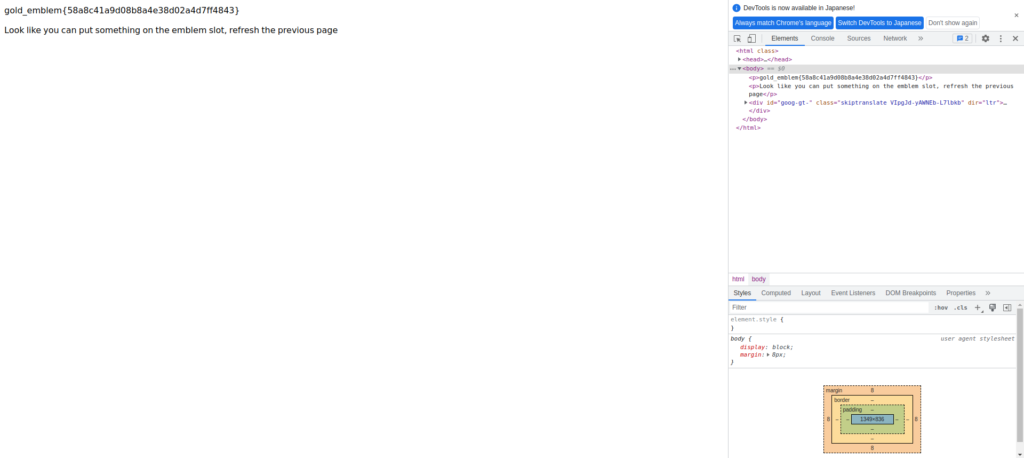
gold_emblem{58a8c41a9d08b8a4e38d02a4d7ff4843} Look like you can put something on the emblem slot, refresh the previous pageThere was also gold_emblem.
Answer

What is the shield key flag
Returning back to Secret bar room.
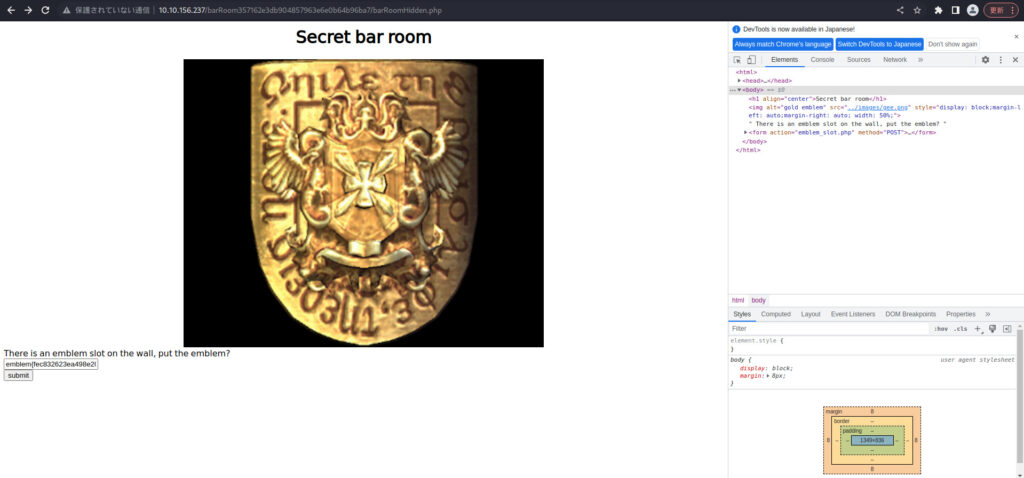
When I entered "gold_emblem", nothing happened, so I entered "emblem", and was able to move to the next screen.
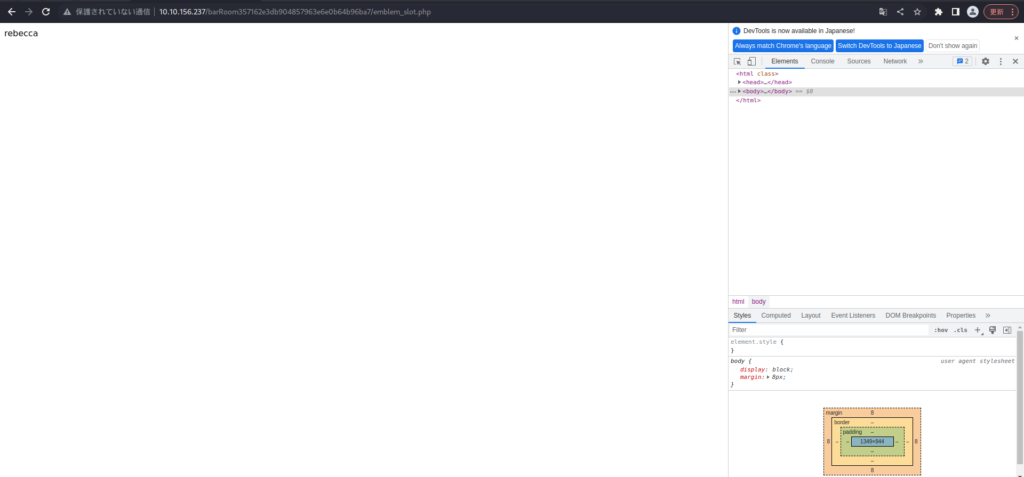
Is "rebecca" a key to some sort of thing? For now, I'll make a note of this.
For now, I have nowhere to go, so I'll try adding "gold emblem flag" to the part where nothing happened when I first entered emblem.
Let's go back to diningRoom.
Now, try entering "gold emblem flag" into emblem's input flag.
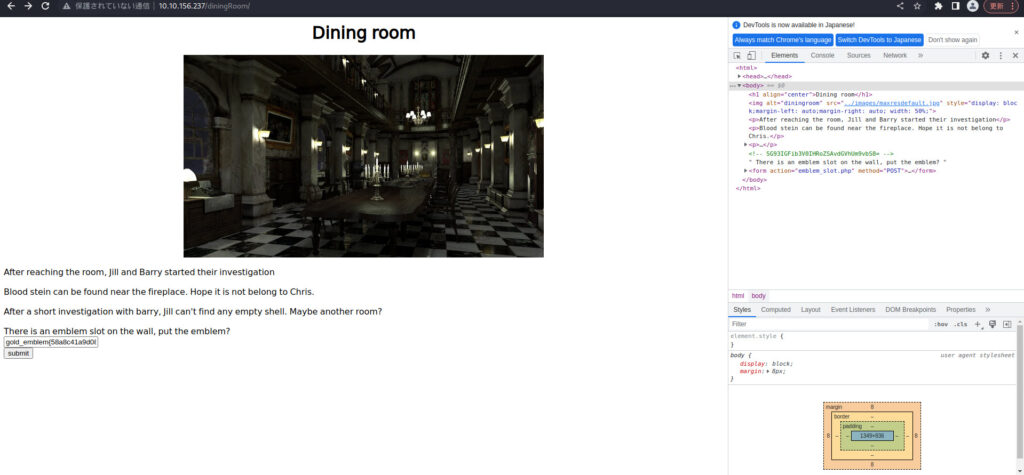
It seemed right.

klfvg ks r wimgnd biz mpuiui ulg fiemok tqod. Xii jvmc tbkg ks tempgf tyi_hvgct_jljinf_kvcThe text appears to be shifted, so I'll try CyberChef with doubts about ROT13.

Hmm, it seems different.
Let's use " https://www.boxentriq.com/code-breaking/cipher-identifier

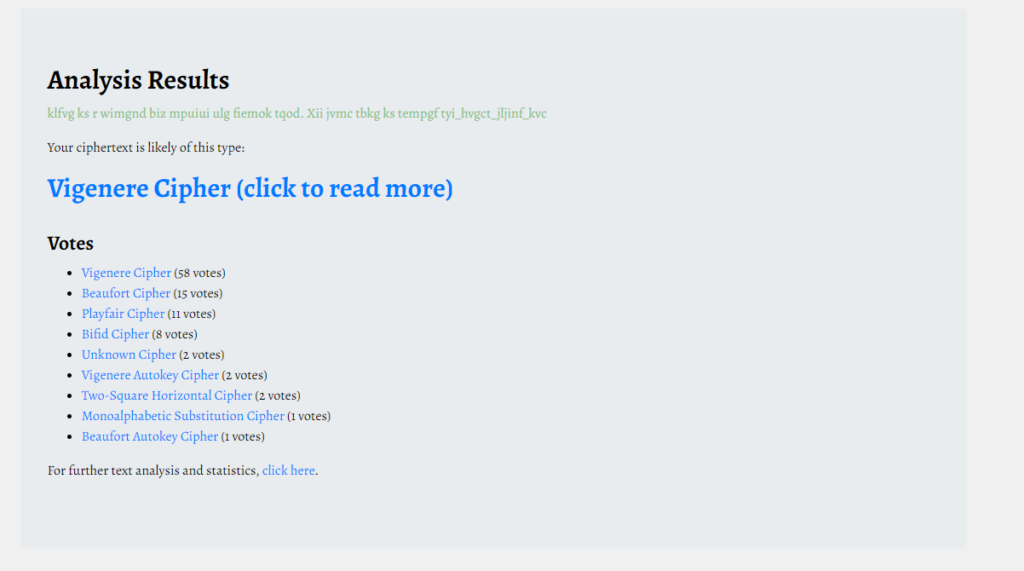
Apparently it was encoded in "Vigenere Cipher."
When encoding with Vigenere, you need a private key, but we can assume that this is "rebecca".
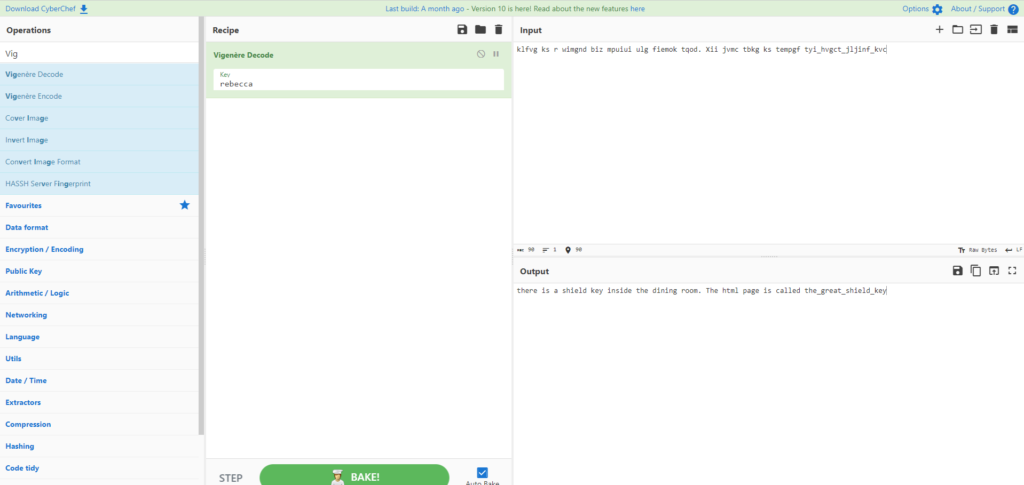
There is a shield key inside the dining room. The html page is called the_great_shield_key (There is a shield key inside the dining room. The html page name is the_great_shield_key.)I was able to encode it successfully.
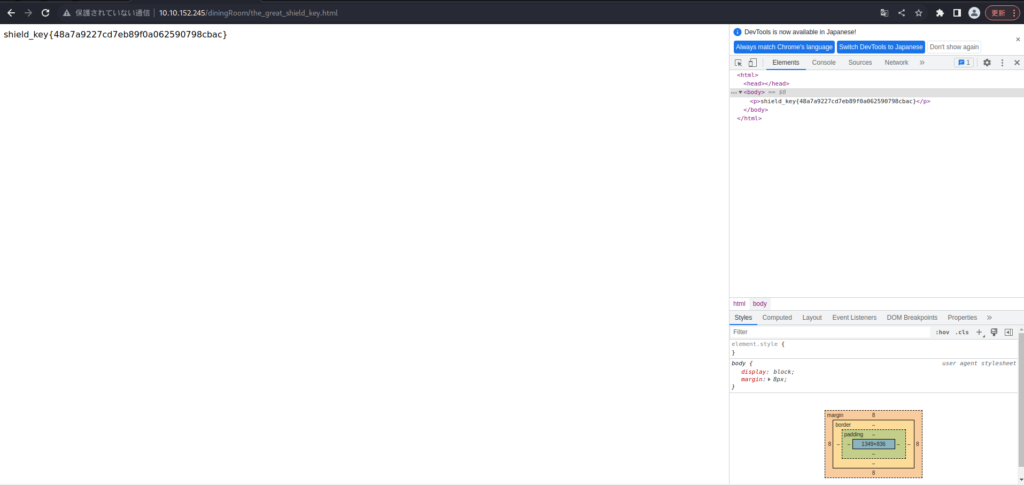
shield_key{48a7a9227cd7eb89f0a062590798cbac}Answer

What is the blue gem flag
Next, we will proceed to the new dining Room 2F.
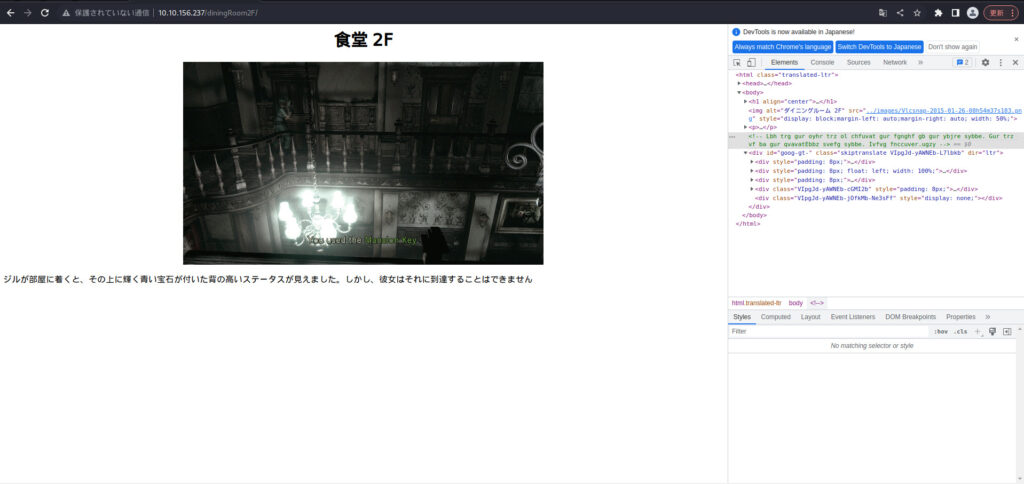
Looking at the source, I found the following comment:
I'll try CyberChef too, suspecting ROT13.
<!-- Lbh trg gur oyhr trz ol chfuvat gur fgnghf gb gur ybjre sybbe. Gur trz vf ba gur qvavatEbbz svefg sybbe. Ivfvg fnccuver.ugzy -->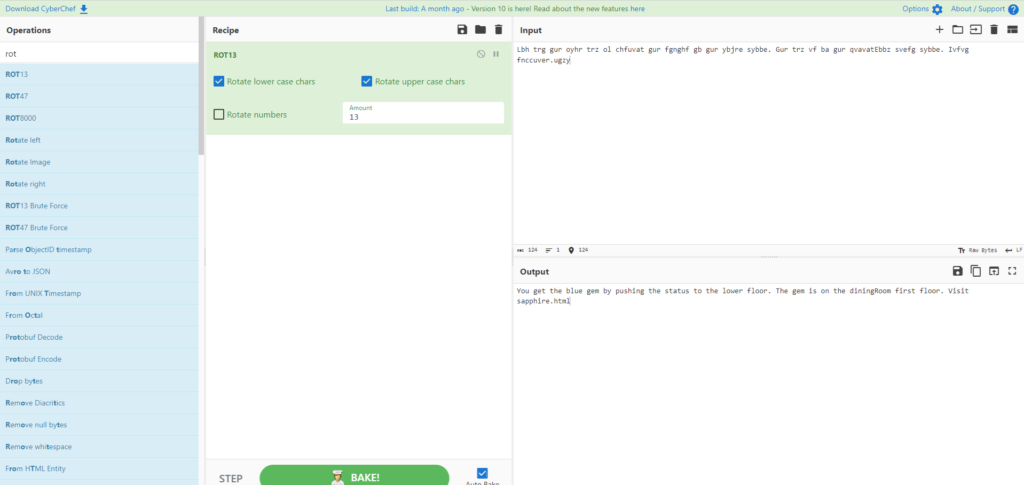
You get the blue gem by pushing the status to the lower floor. The gem is on the diningRoom first floor. Visit sapphire.html (If you press status and go downstairs, you will get the blue gem. The gem is on diningRoom1F. View sapphire.html)As expected, I was able to decipher the string with ROT13.
Let's literally look at "/diningRoom/sapphire.html".
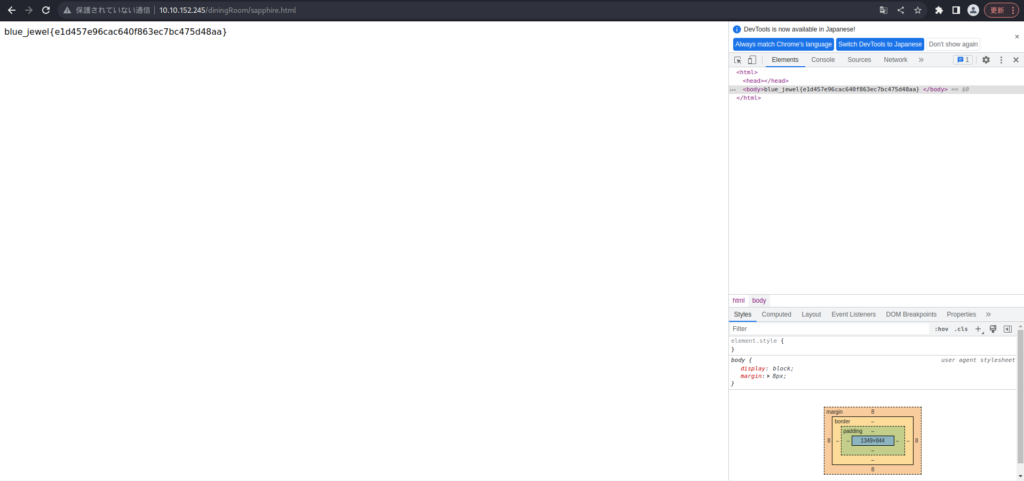
blue_jewel{e1d457e96cac640f863ec7bc475d48aa}Answer
What is the FTP username
Next, we'll look for our FTP username.
Let's take a look at the new "/tigerStatusRoom/".
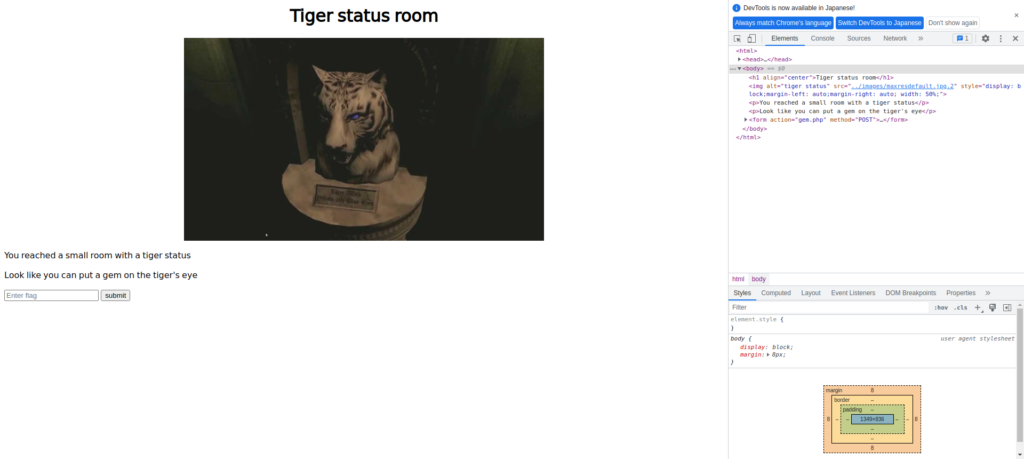
I'll try submitting "blue_jewel{e1d457e96cac640f863ec7bc475d48aa}".
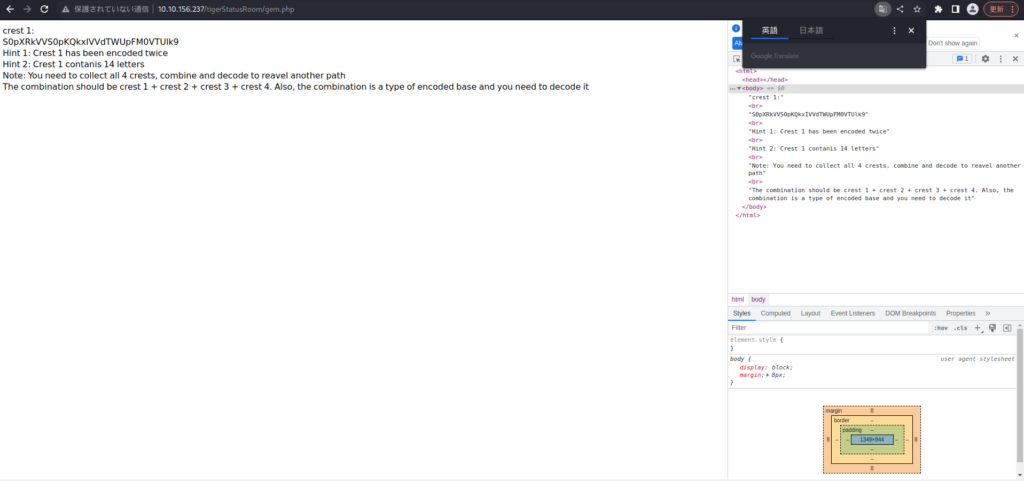
crest 1: S0pXRkVVS0pKQkxIVVdTWUpFM0VTUlk9 Hint 1: Crest 1 has been encoded twice Hint 2: Crest 1 contanis 14 letters Note: You need to collect all 4 crests, combine and decode to reveal another path The combination should be crest 1 + crest 2 + crest 3 + crest 4. Also, the combination is a type of encoded base and you need to decode it --Translation Crest 1 S0pXRkVS0pKQkxIVVdTWUpFM0VTUlk9 Tip 1: Emblem 1 is encoded twice Tip 2: Emblem 1 contains 14 characters Note: By collecting, combining and deciphering all four emblems, you can go on a different path. The combinations are 1 crest, 2 crest, 3 crest, and 4 crest. Also, this combination is a type of encrypted base and needs to be decrypted.It seems that four coats of arms must be combined.
For now, let's try unraveling Emblem 1. It appears to be encoding twice.
I'll try base32-64 to see what the first encoding is.
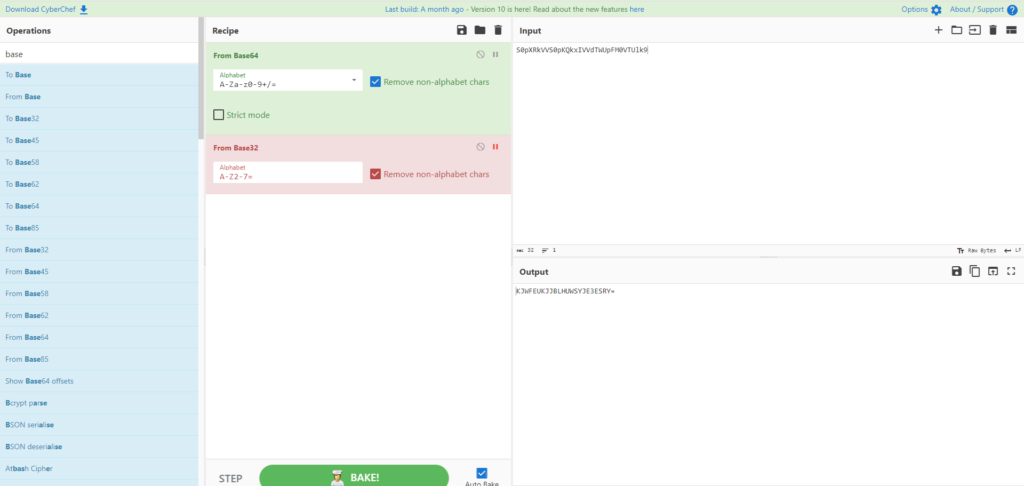
The trailing point was "=" so it seemed to be decoded correctly.
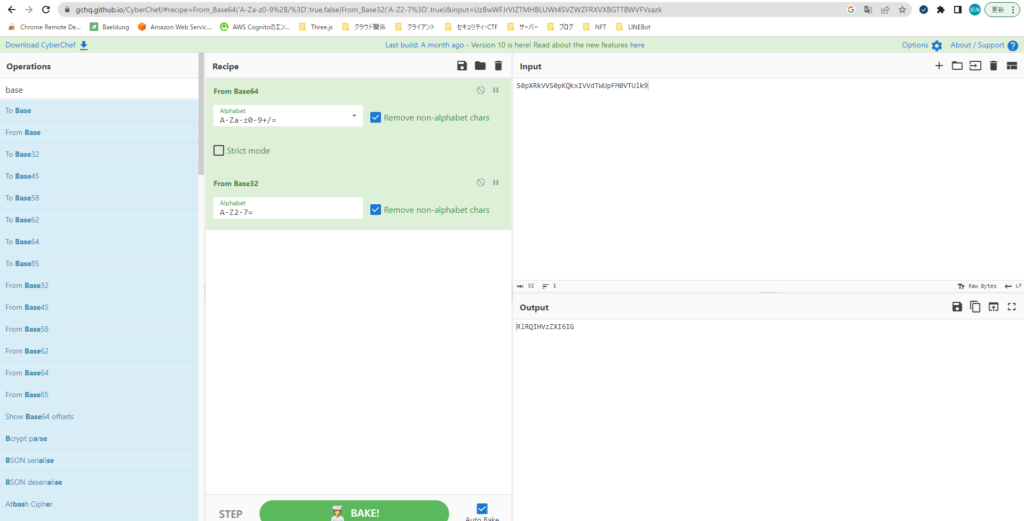
Next, try the same procedure the second time.
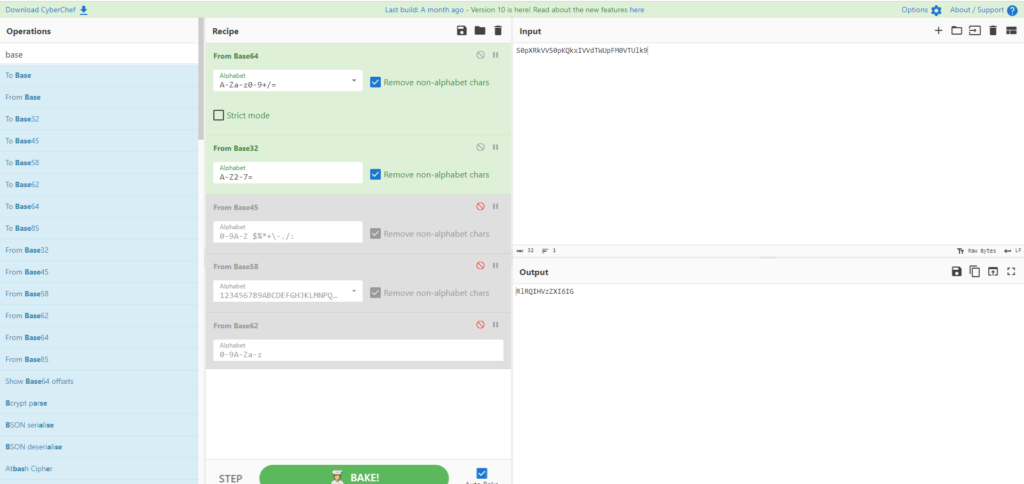
When I decoded it in base32, I was able to get the following:
The number of characters is also 14. It probably seems correct.
RlRQIHVzZXI6IGMove through rooms to find the coat of arms 2.
Next, proceed to "/galleryRoom/".
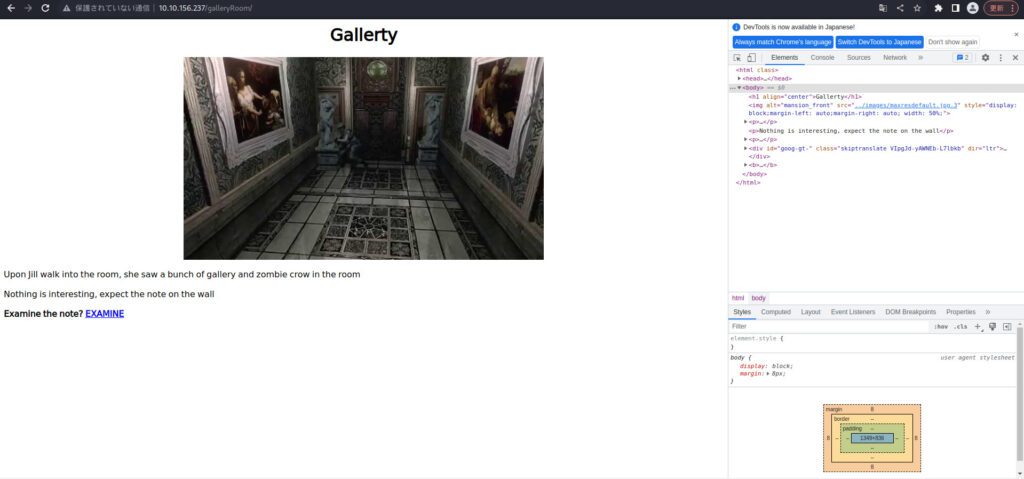
When I selected EXAMINE, I got Emblem 2.
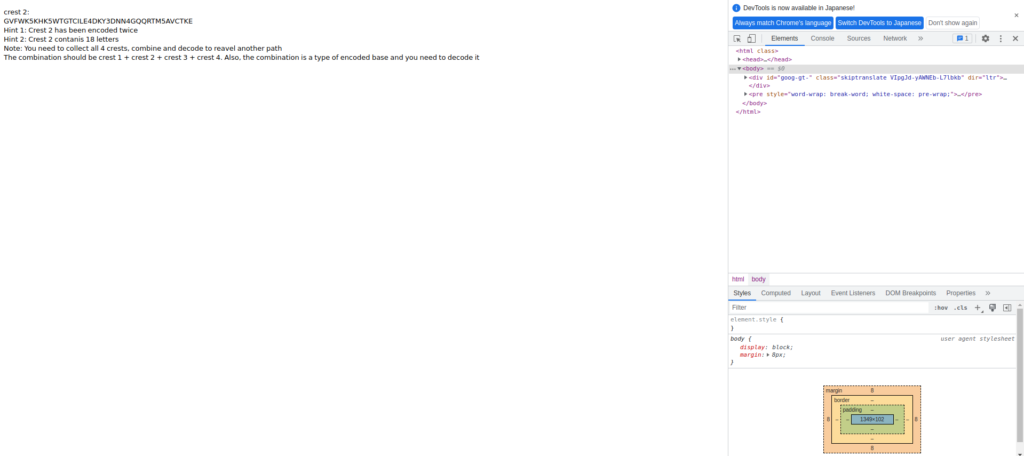
crest 2: GVFWK5KHK5WTGTCILE4DKY3DNN4GQQRTM5AVCTKE Hint 1: Crest 2 has been encoded twice Hint 2: Crest 2 contanis 18 letters Note: You need to collect all 4 crests, combine and decode to reveal another path The combination should be crest 1 + crest 2 + crest 3 + crest 4. Also, the combination is a type of encoded base and you need to decode it --Translation Emblem 2 GVFWK5KHK5WTGTCILE4DKY3DNN4GQQRTM5AVCTKE Tip 1: Emblem 2 is encoded twice Tip 2: Emblem 2 contains 18 characters Note: You can go on a different path by collecting, combining and deciphering all four emblems. The combinations are 1 crest, 2 crest, 3 crest, and 4 crest. Also, this combination is a type of encrypted base and needs to be decrypted.Once again, it's encoded twice. . .
I'll try the same from base32 to 64.
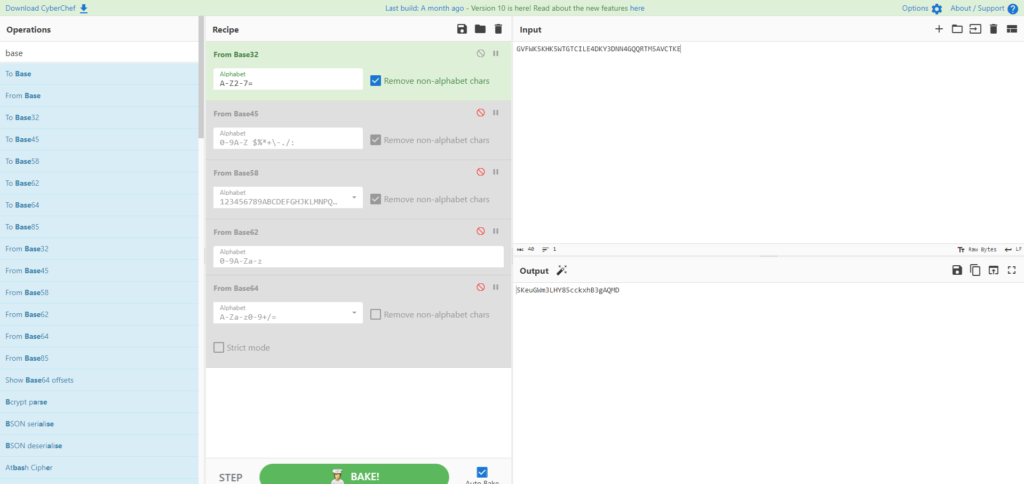
It seems that base32 is able to output the correct string.
Try decoding the second time as well.
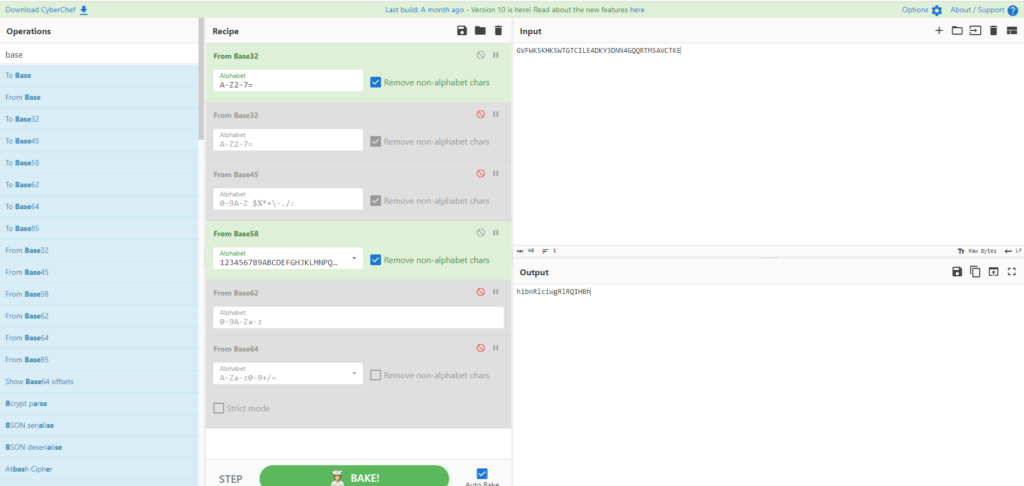
The correct string was base58.
The number of characters is also correct, so I think the following is correct.
h1bnRlciwgRlRQIHBhNext, we will move to "/armorRoom/" and look for Emblem 3. (/studyRoom/ required helmet key flag...)
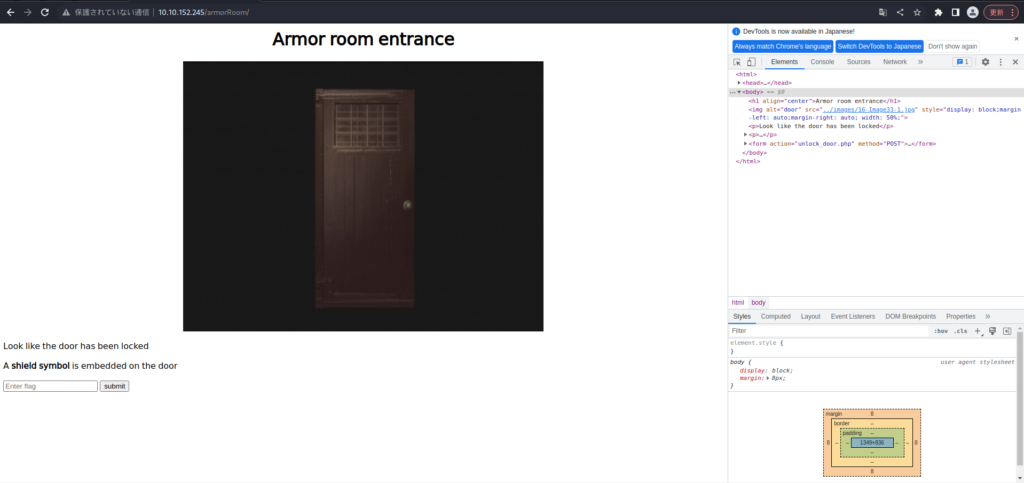
Enter "shield key flag" and submit.
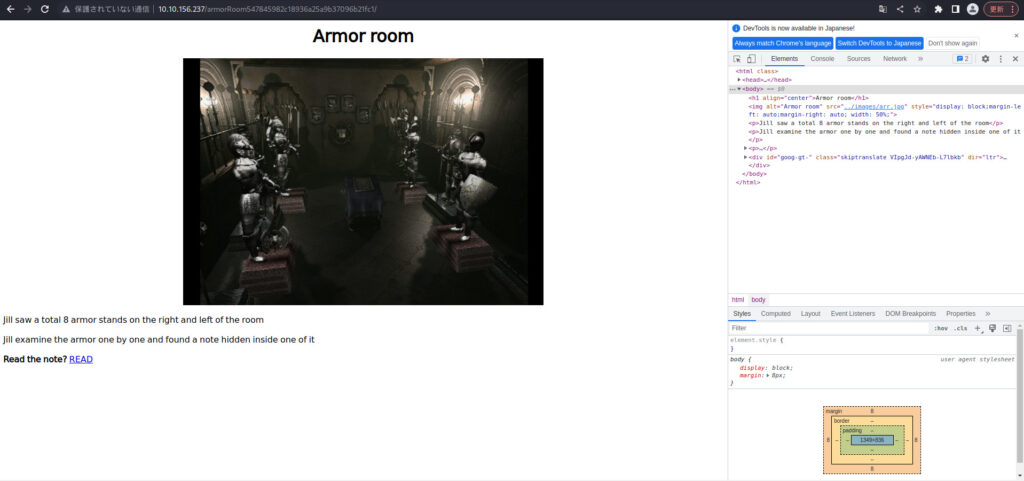
I put it in ArmorRoom.
Try selecting READ. .
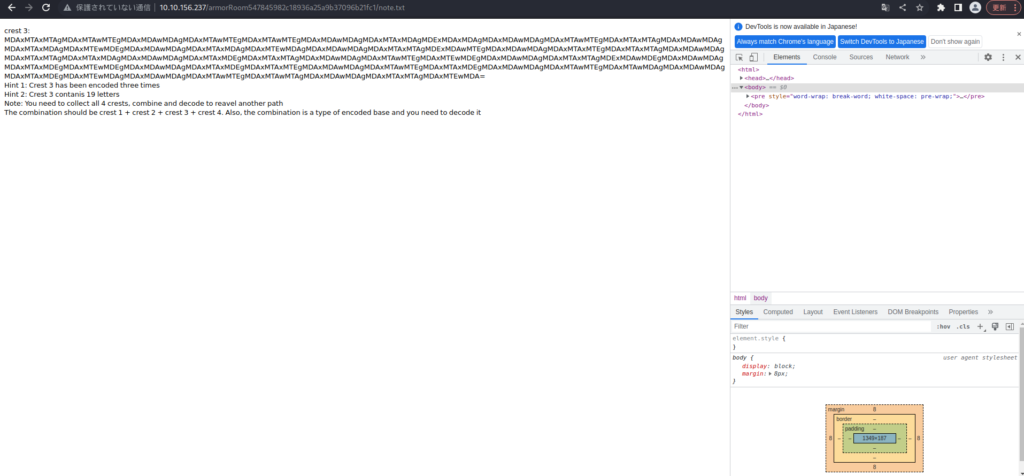
crest 3: = Hint 1: Crest 3 has been encoded three times Hint 2: Crest 3 contanis 19 letters Note: You need to collect all 4 crests, combine and decode to reveal another path The combination should be crest 1 + crest 2 + crest 3 + crest 4. Also, the combination is a type of encoded base and you need to decode it -- Translation Emblem 3 = Hint 1: Crest 3 has been encoded three times Hint 2: Crest 3 contains 19 characters Note: Collect, synthesize and decipher all four crests to take another path. The combinations are 1 crest, 2 crest, 3 crest, and 4 crest. Also, this combination is a type of encrypted base and needs to be decrypted.Next, it was encoded three times. . .
First, I'll try using base32-64.
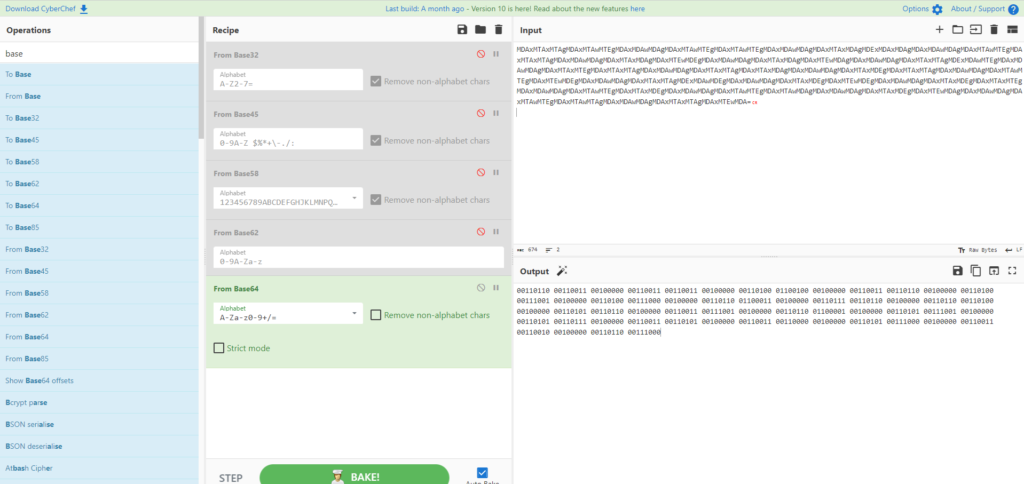
Base64 seems to be correct.
The output result is binary (binary data), so it decodes the binary.
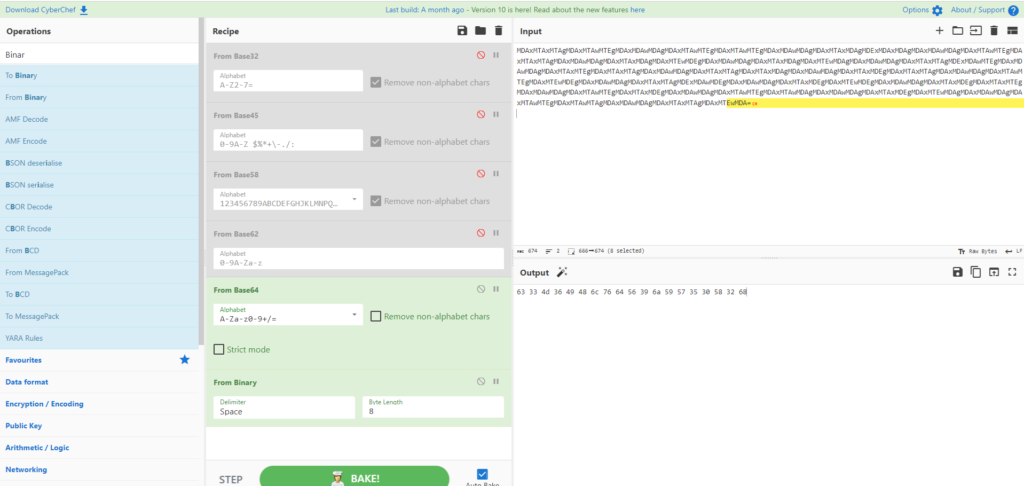
When I decoded it in binary, I got Hex (hex).
I'll try decoding it with Hex.
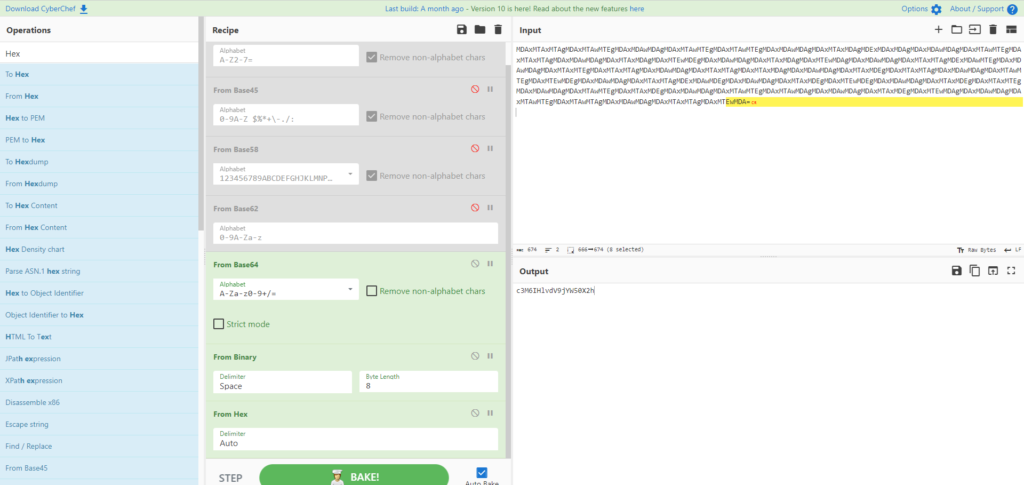
I managed to decode it. The number of characters seems to be correct too!
c3M6IHlvdV9jYW50X2hYou will be redirected to the last room "/attic/".
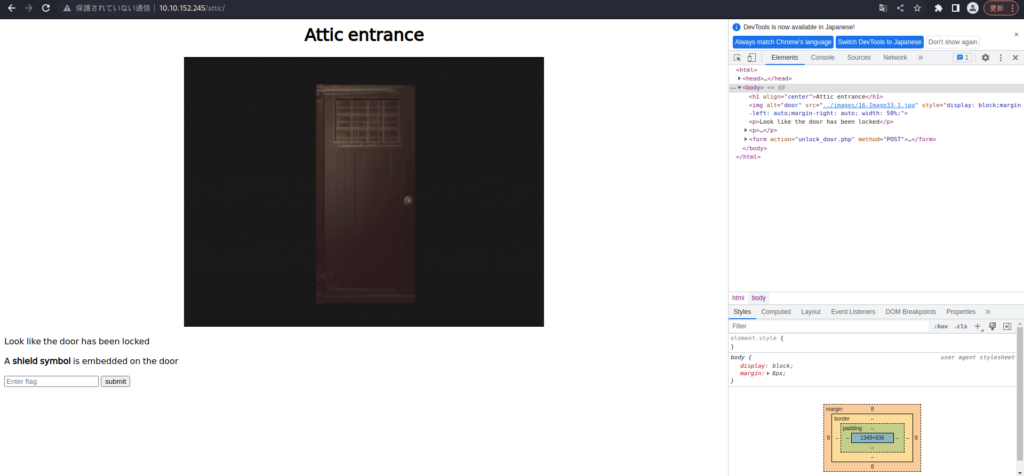
You also need a shleld symbol.
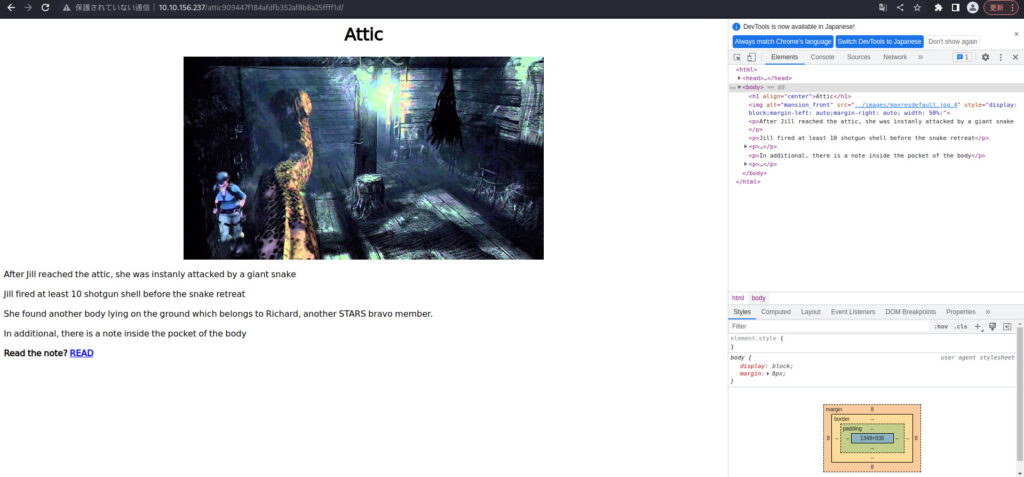
There's a note, let's try READ.
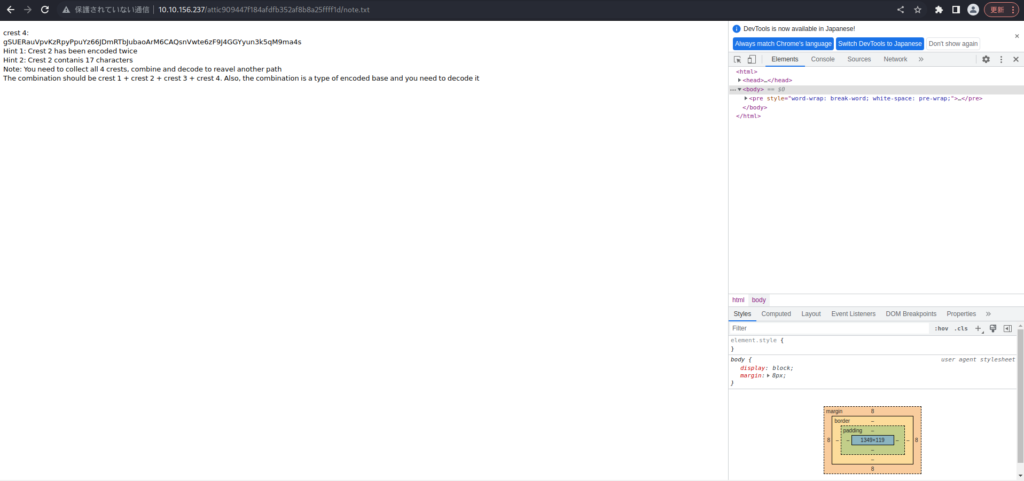
crest 4: gSUERauVpvKzRpyPpuYz66JDmRTbJubaoArM6CAQsnVwte6zF9J4GGYyun3k5qM9ma4s Hint 1: Crest 2 has been encoded twice Hint 2: Crest 2 contanis 17 characters Note: You need to collect all 4 crests, combined and decode to reveal another path The combination should be crest 1 + crest 2 + crest 3 + crest 4. Also, the combination is a type of encoded base and you need to decode it -- Translation Emblem 4 gSUERauVpvKzRpyPpuYz66JDmRTbJubaoArM6CAQsnVwte6zF9J4GGYyun3k5qM9ma4s Tip 1: Emblem 2 is encoded twice Tip 2: Emblem 2 contains 17 characters Note: You can go on a different path by collecting, combining and deciphering all four emblems. The combinations are 1 crest, 2 crest, 3 crest, and 4 crest. Also, this combination is a type of encrypted base and needs to be decrypted.It says Emblem 2, but it probably refers to Emblem 4. I think it was a mistake. . .
For now, forget about the details. . . Let's decode it.
This time, I will try base32-64 as before.
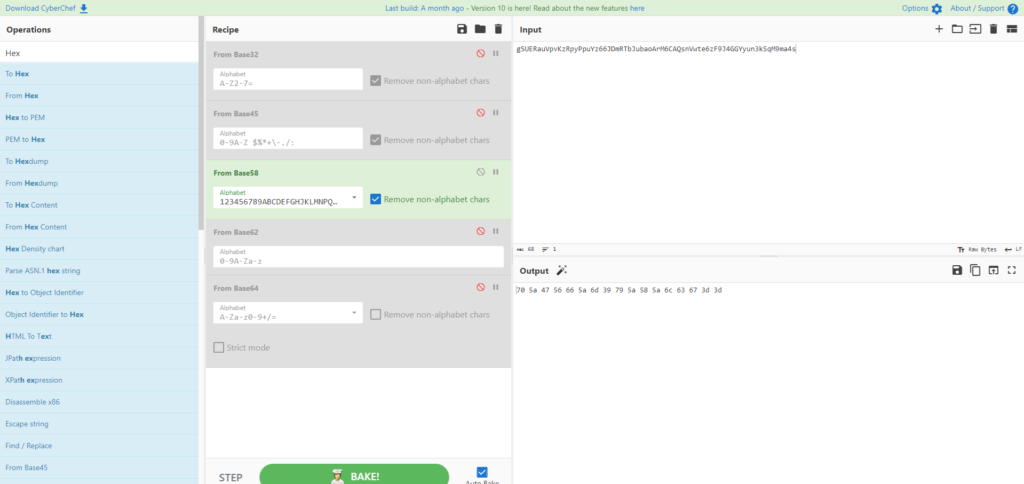
Base58 seems to be correct.
It's hex (hex), so I'll try decoding it.
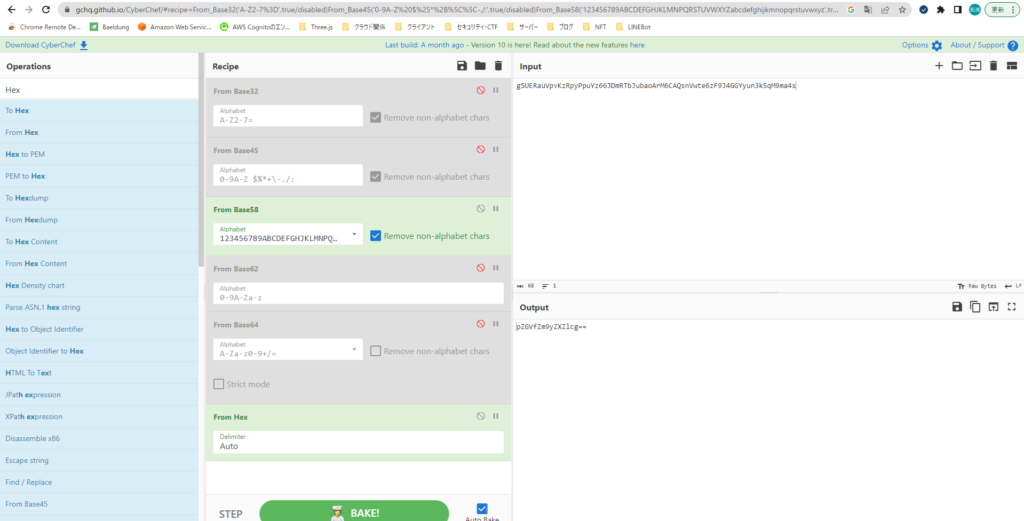
It seems correct below.
pZGVfZm9yZXZlcg==If you connect emblems 1 to 4, you will see the following:
RlRQIHVzZXI6IGh1bnRlciwgRlRQIHBhc3M6IHlvdV9jYW50X2hpZGVfZm9yZXZlcg==For now, I'll try playing Hashes.
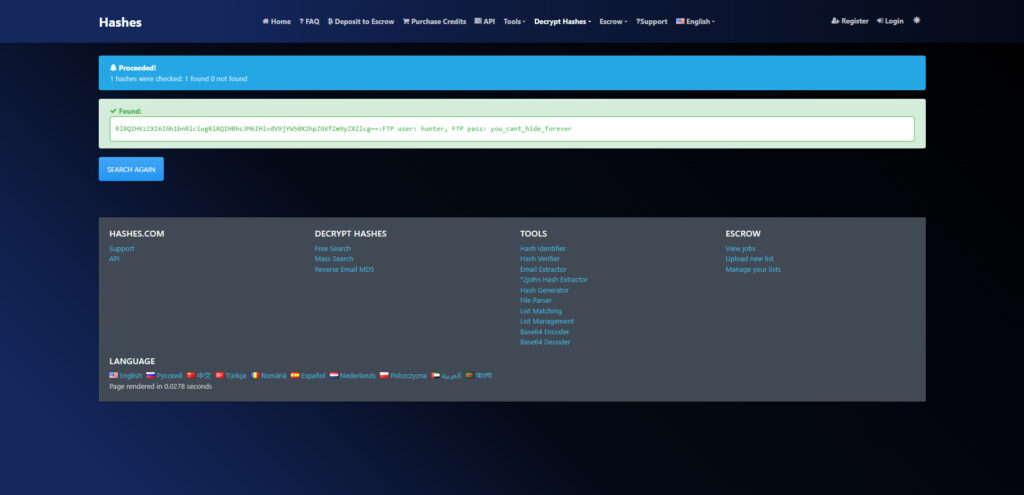
Apparently it was base64. I was able to get the FTP user and pass.
FTP user: hunter, FTP pass: you_cant_hide_foreverAnswer
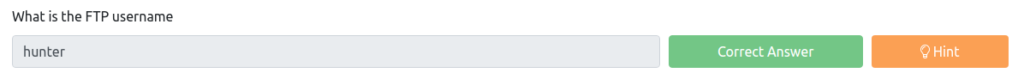
What is the FTP password
This answer is the pass from earlier.
Answer

The guard house
After gaining access to the FTP server, you need to solve another puzzle .
So I'll go to the FTP server for now.
┌──(hacklab㉿hacklab)-[~] └─$ ftp hunter@10.10.156.237 Connected to 10.10.156.237. 220 (vsFTPd 3.0.3) 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> I was able to access the FTP server safely with the user and pass mentioned earlier.
Where is the hidden directory mentioned by Barry
First, they look for a hidden directory.
ftp> ls 229 Entering Extended Passive Mode (||10379|) 150 Here comes the directory listing. -rw-r--r-- 1 0 0 7994 Sep 19 2019 001-key.jpg -rw-r--r-- 1 0 0 2210 Sep 19 2019 002-key.jpg -rw-r--r-- 1 0 0 2146 Sep 19 2019 003-key.jpg -rw-r--r-- 1 0 0 121 Sep 19 2019 helmet_key.txt.gpg -rw-r--r-- 1 0 0 170 Sep 20 2019 important.txt 226 Directory send OK.For now, I have a file and something that looks like a key, so I'll drop it locally.
ftp> mget * mget 001-key.jpg [anpqy?]? 229 Entering Extended Passive Mode (|||51303|) 150 Opening BINARY mode data connection for 001-key.jpg (7994 bytes). 100% |************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************ Transfer complete. 7994 bytes received in 00:03 (2.39 KiB/s) mget 002-key.jpg [anpqy?]? 229 Entering Extended Passive Mode (|||24041|) 150 Opening BINARY mode data connection for 002-key.jpg (2210 bytes). 100% |************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************ BINARY mode data connection for 003-key.jpg (2146 bytes). 100% |************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************** 229 Entering Extended Passive Mode (|||28546|) 150 Opening BINARY mode data connection for helmet_key.txt.gpg (121 bytes). 100% |************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************** 00:00 (0.38 KiB/s) mget important.txt [anpqy?]? 229 Entering Extended Passive Mode (|||57273|) 150 Opening BINARY mode data connection for important.txt (170 bytes). 100% |************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************ 226 Transfer complete. 170 bytes received in 00:00 (0.67 KiB/s) ftp> The first thing I would like to do is "important.txt."
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ cat important.txt Jill, I think the helmet key is inside the text file, but I have no clue on decrypting stuff. Also, I come across a /hidden_closet/ door but it was locked. From, Barry -- Translation This is Jill, I think the helmet key is in the text file, but there are no clues for decryption. I also came across the door to /hidden_closet/, but it was locked. Because, BarryThe hidden directory appears to be "/hidden_closet/".
Answer

Password for the encrypted file
First, let's look at the hidden directory "/hidden_closet/".
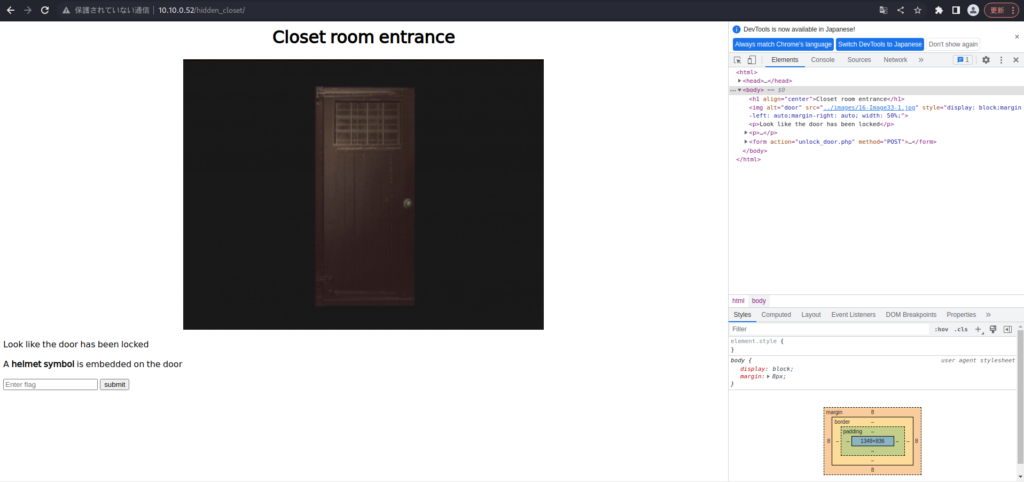
You're told that you need a helmet symbol, so let's look for a helmet symbol.
The one that's suspicious is helmet_key.txt.gpg, but unfortunately it's locked.
It seems like it's necessary to decipher 00x-key.jpg.
I'll start from the beginning. I first looked it up with exiftool, but there was no great information.
Just to be safe, I extracted the file using steghide.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ steghide extract -sf 001-key.jpg Enter passphrase: write extracted data to "key-001.txt".I was able to extract key-001.txt.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ ll Total 28 -rw-r--r-- 1 hacklab hacklab 7994 September 19 2019 001-key.jpg -rw-r--r-- 1 hacklab hacklab 2210 September 19 2019 002-key.jpg -rw-r--r-- 1 hacklab hacklab 2146 September 19 2019 003-key.jpg -rw-r--r-- 1 hacklab hacklab 121 September 19 2019 helmet_key.txt.gpg -rw-r--r-- 1 hacklab hacklab 170 September 20 2019 important.txt -rw-r--r-- 1 hacklab hacklab 15 April 20 21:55 key-001.txt ┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ cat key-001.txt cGxhbnQ0Ml9jYW
When I checked the contents it looked like a hash of something.
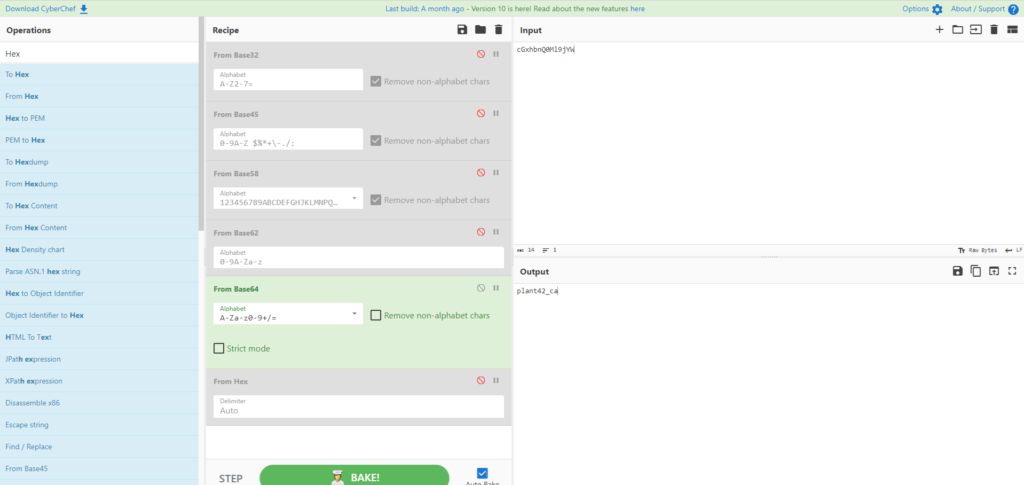
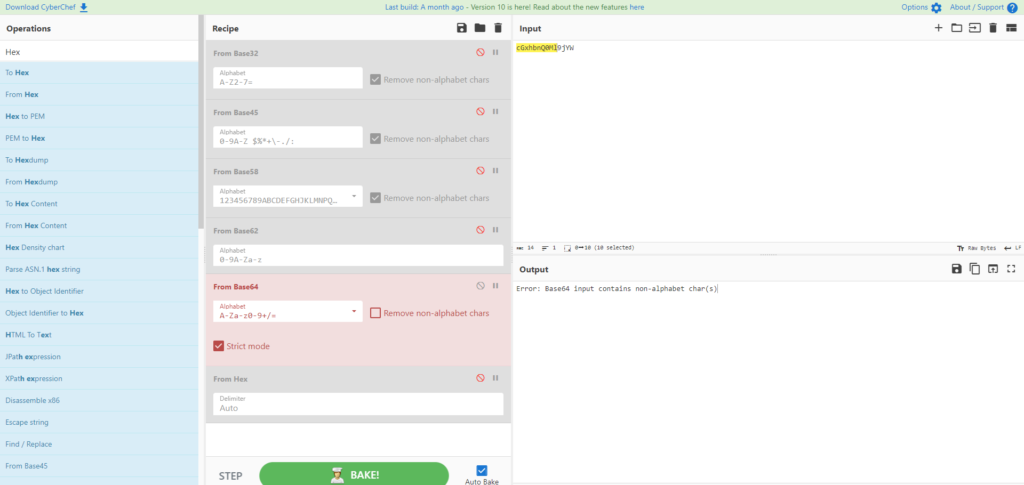
I think it's base64, but if you set it to Strict mode, it will cause an error, so there's not enough information.
Let's solve 002-key.
When I looked at the meta information on exiftool, I found a hash.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ exiftool 002-key.jpg ExifTool Version Number: 12.57 File Name: 002-key.jpg Directory: . File Size: 2.2 kB File Modification Date/Time: 2019:09:19 15:08:31+09:00 File Access Date/Time: 2023:04:20 21:47:47+09:00 File Inode Change Date/Time: 2023:04:20 21:47:47+09:00 File Permissions: -rw-r-- File Type: JPEG File Type Extension: jpg MIME Type: image/jpeg JFIF Version: 1.01 Resolution Unit: None X Resolution: 1 Y Resolution: 1 Comment: 5fYmVfZGVzdHJveV9 Image Width: 100 Image Height: 80 Encoding Process: Progressive DCT, Huffman coding Bits Per Sample: 8 Color Components: 3 Y Cb Cr Sub Sampling: YCbCr4:2:0 (2 2) Image Size: 100x80 Megapixels: 0.008The hash is in the Comment.
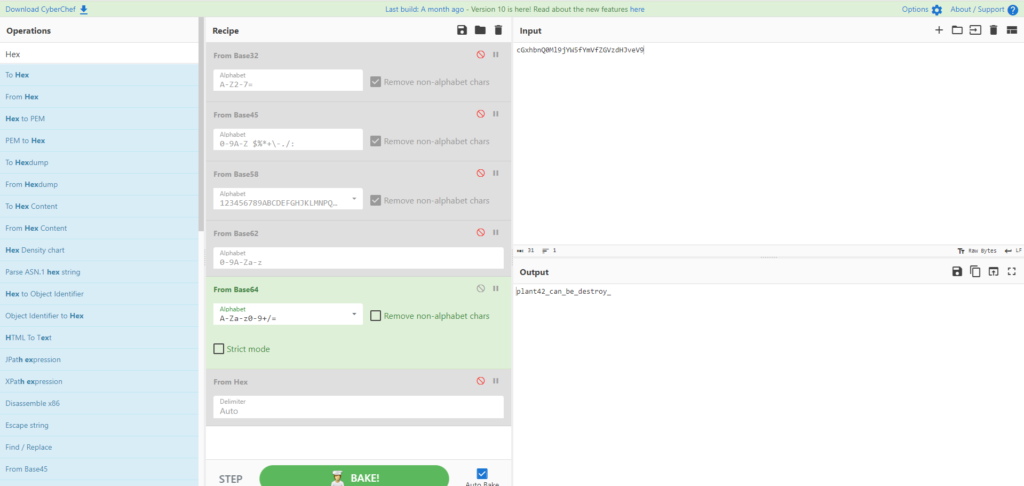
When I connected it, something that looked like a string came out.
I'll also solve the final 003.
This also runs exiftool.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ exiftool 003-key.jpg ExifTool Version Number: 12.57 File Name: 003-key.jpg Directory: . File Size: 2.1 kB File Modification Date/Time: 2019:09:19 15:19:17+09:00 File Access Date/Time: 2023:04:20 21:47:49+09:00 File Inode Change Date/Time: 2023:04:20 21:47:49+09:00 File Permissions: -rw-r-- File Type: JPEG File Type Extension: jpg MIME Type: image/jpeg JFIF Version: 1.01 Resolution Unit: None X Resolution: 1 Y Resolution: 1 Comment: Compressed by jpeg-recompress Image Width: 100 Image Height: 80 Encoding Process: Progressive DCT, Huffman coding Bits Per Sample: 8 Color Components: 3 Y Cb Cr Sub Sampling: YCbCr4:2:0 (2 2) Image Size: 100x80 Megapixels: 0.008
This was also stated in the Comment: "Compressed by jpeg-recompress."
It is said to be compressed using jpeg-recompress, so I'll decompress using binwalk.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ binwalk -e 003-key.jpg DECIMAL HEXADECIMAL DESCRIPTION ----- 0 0x0 JPEG image data, JFIF standard 1.01 1930 0x78A Zip archive data, at least v2.0 to extract, uncompressed size: 14, name: key-003.txt 2124 0x84C End of Zip archive, footer length: 22I was able to thaw it safely. Let's take a look at the contents.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ cd _003-key.jpg.extracted ┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard/_003-key.jpg.extracted] └─$ ll Total 8 -rw-r--r-- 1 hacklab hacklab 216 April 20 22:03 78A.zip -rw-r--r-- 1 hacklab hacklab 14 September 19 2019 key-003.txt ┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard/_003-key.jpg.extracted] └─$ cat key-003.txt 3aXRoX3Zqb2x0There was key-003.txt, the last hash was found.
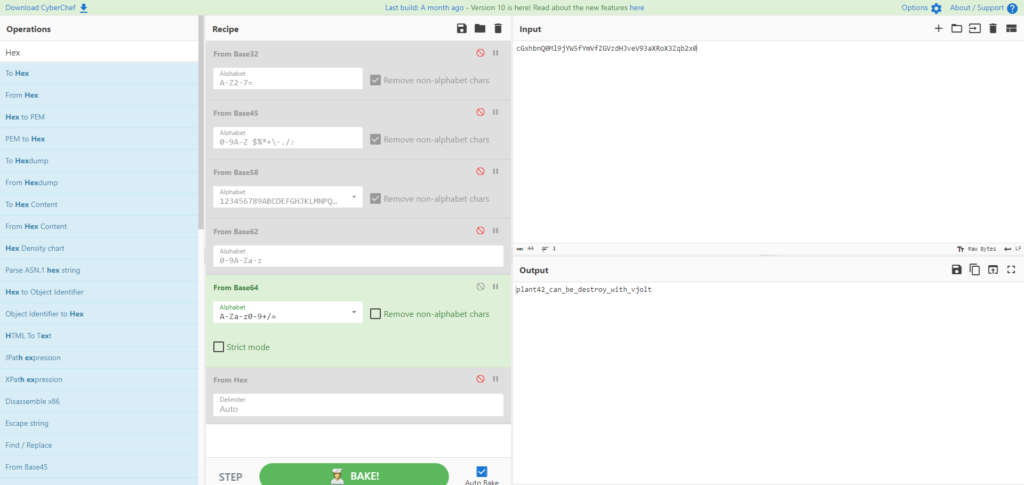
Answer

What is the helmet key flag
Let's use the keys above to look at helmet_key.txt.gpg.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ gpg helmet_key.txt.gpg gpg: *Warning*: No command specified. Let's guess what it means... gpg: AES256.CFB encrypted data gpg: Encrypted with 1 passphraseIt looks like there's a helmet key flag in helmet_key.txt.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ ll Total 36 -rw-r--r-- 1 hacklab hacklab 7994 September 19 2019 001-key.jpg -rw-r--r-- 1 hacklab hacklab 2210 September 19 2019 002-key.jpg -rw-r--r-- 1 hacklab hacklab 2146 September 19 2019 003-key.jpg drwxr-xr-x 2 hacklab hacklab 4096 April 20 22:05 _003-key.jpg.extracted -rw-r--r-- 1 hacklab hacklab 45 April 20 22:11 helmet_key.txt -rw-r--r-- 1 hacklab hacklab 121 September 19 2019 helmet_key.txt.gpg -rw-r--r-- 1 hacklab hacklab 170 September 20 2019 important.txt -rw-r--r-- 1 hacklab hacklab 15 April 20 21:55 key-001.txt ┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ cat helmet_key.txt helmet_key{458493193501d2b94bbab2e727f8db4b}Finally, I got the helmet_key.
Answer

The Revisit
Done with the puzzle? There are places you have explored before but yet to access .
What is the SSH login username
The room that you can't enter without helmet symbol is "/studyRoom/" yet.
I'll try using helmet symbol.

Select EXAMINE to download "doom.tar.gz".
Let's try unzipping this.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ tar -xf doom.tar.gz ┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ ll Total 44 -rw-r--r-- 1 hacklab hacklab 7994 September 19 2019 001-key.jpg -rw-r--r-- 1 hacklab hacklab 2210 September 19 2019 002-key.jpg -rw-r--r-- 1 hacklab hacklab 2146 September 19 2019 003-key.jpg drwxr-xr-x 2 hacklab hacklab 4096 April 20 22:05 _003-key.jpg.extracted -rw-r--r-- 1 hacklab hacklab 149 April 21 22:32 doom.tar.gz -rw-r--r-- 1 hacklab hacklab 25 September 20 2019 eagle_medal.txt -rw-r--r-- 1 hacklab hacklab 45 April 20 22:11 helmet_key.txt -rw-r--r-- 1 hacklab hacklab 121 September 19 2019 helmet_key.txt.gpg -rw-r--r-- 1 hacklab hacklab 170 September 20 2019 important.txt -rw-r--r-- 1 hacklab hacklab 15 April 20 21:55 key-001.txt ┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ cat eagle_medal.txt SSH user: umbrella_guest
There was eagle_medal.txt, and there was an SSH user inside.
Answer

What is the SSH login password
Another room I couldn't get in because there was no helmet symbol is "/hidden_closet/".
Enter the helmet symbol you just got and submit.

Let's select EXAMINE.
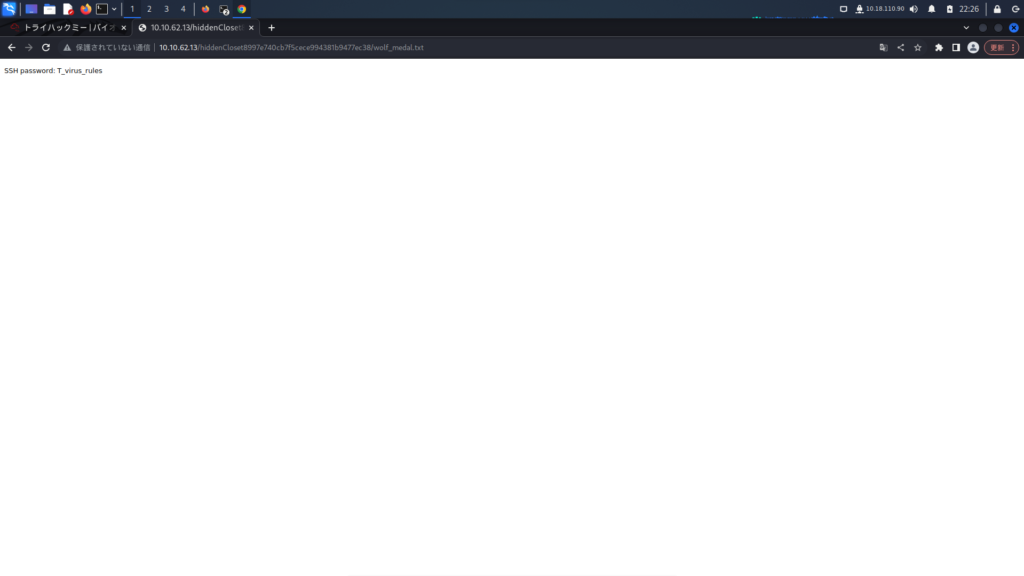
SSH password: T_virus_rulesI had the SSH key.
Answer
Who the STARS bravo team leader
This was mentioned in the Closet Room!
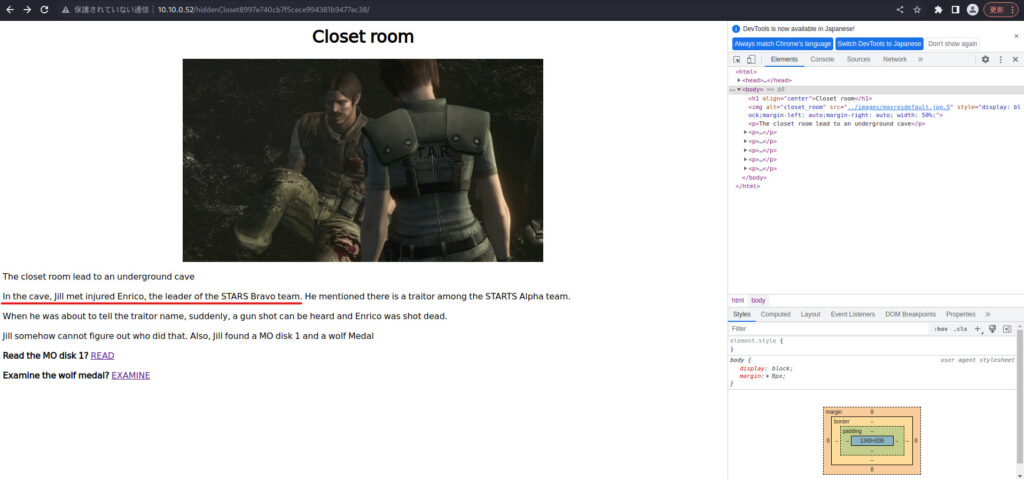
Answer
Underground laboratory
the
final showdown. Can you escape the nightmare?
Finally, I reached the end. (It was a long time...)
Where you found Chris
For now, let's take a look at the MO disk 1 in Closet Room, which we just mentioned earlier.
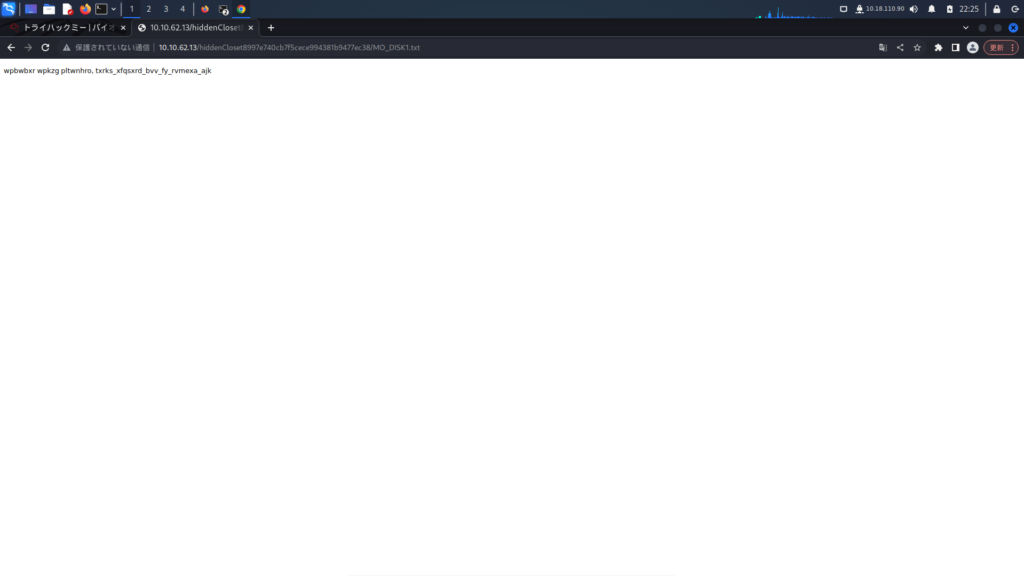
wpbwbxr wpkzg pltwnhro, txrks_xfqsxrd_bvv_fy_rvmexa_ajkThere's a hash.
I tried decoding it with ROT13, but it didn't work, so I'll check if it's encrypted.

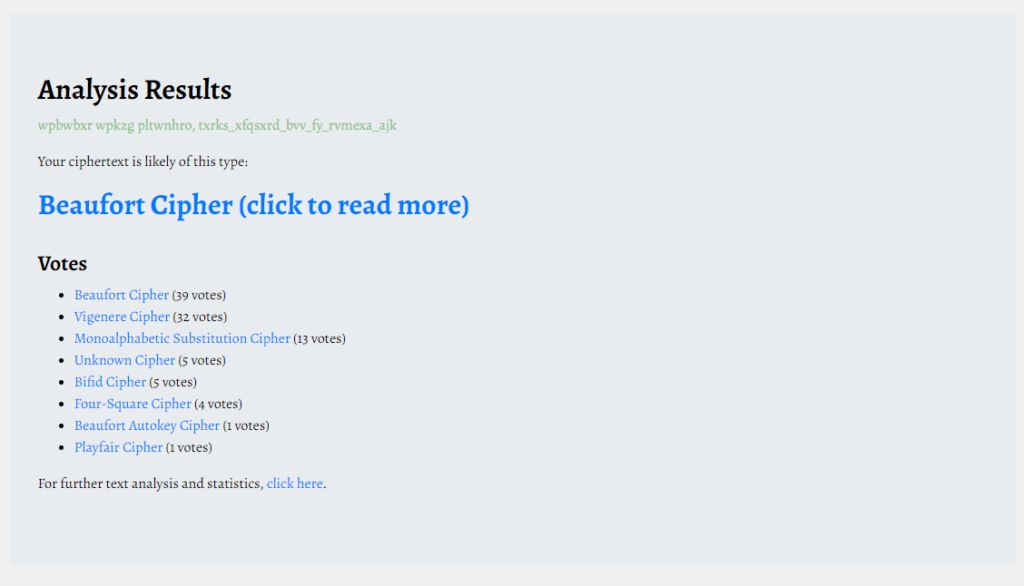
It appears to be encrypted with Beaufort.
It's CyberChef, but there's no Beaufort, but Vigenere looks good.
There is no key, so I live looking for the key.
Just now, you can SSH, so try connecting via SSH.
┌──(hacklab㉿hacklab)-[~/tryhackme/biohazard] └─$ ssh umbrella_guest@10.10.62.13 The authenticity of host '10.10.62.13 (10.10.62.13)' can't be established. ED25519 key fingerprint is SHA256:dOQYq6o72K3z+Nn6HtAR4ZFXoEZklDafT3VuF728yWc. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.62.13' (ED25519) to the list of known hosts. umbrella_guest@10.10.62.13's password: Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage * Canonical Livepatch is available for installation. - Reduce system reboots and improve kernel security. Activate at: https://ubuntu.com/livepatch 320 packages can be updated. 58 updates are security updates. Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings Last login: Fri Sep 20 03:25:46 2019 from 127.0.0.1 umbrella_guest@umbrella_corp:~$ I was able to connect safely.
umbrella_guest@umbrella_corp:~$ ll -a total 64 drwxr-xr-x 8 umbrella_guest umbrella 4096 Sep 20 2019 ./ drwxr-xr-x 5 root root 4096 Sep 20 2019 ../ -rw-r--r-- 1 umbrella_guest umbrella 220 Sep 19 2019 .bash_logout -rw-r--r-- 1 umbrella_guest umbrella 3771 Sep 19 2019 .bashrc drwxrwxr-x 6 umbrella_guest umbrella 4096 Sep 20 2019 .cache/ drwxr-x 11 umbrella_guest umbrella 4096 Sep 19 2019 .config/ -rw-r--r-- 1 umbrella_guest umbrella 26 Sep 19 2019 .dmrc drwx----- 3 umbrella_guest umbrella 4096 Sep 19 2019 .gnupg/ -rw--------- 1 umbrella_guest umbrella 346 Sep 19 2019 .ICEauthority drwxr-xr-x 2 umbrella_guest umbrella 4096 Sep 20 2019 .jailcell/ drwxr-x 3 umbrella_guest umbrella 4096 Sep 19 2019 .local/ -rw-r--r-- 1 umbrella_guest umbrella 807 Sep 19 2019 .profile drwx----- 2 umbrella_guest umbrella 4096 Sep 20 2019 .ssh/ -rw-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------I searched a lot and found a file that caught my eye on .jailcell.
umbrella_guest@umbrella_corp:~$ cd .jailcell/ umbrella_guest@umbrella_corp:~/.jailcell$ ll total 12 drwxr-xr-x 2 umbrella_guest umbrella 4096 Sep 20 2019 ./ drwxr-xr-x 8 umbrella_guest umbrella 4096 Sep 20 2019 ../ -rw-r--r-- 1 umbrella_guest umbrella 501 Sep 20 2019 chris.txt umbrella_guest@umbrella_corp:~/.jailcell$ cat chris.txt Jill: Chris, is That you? Chris: Jill, you finally come. I was locked in the Jail cell for a while. It seems that weasker is behind all this. Jil, What? Weasker? He is the traitor? Chris: Yes, Jill. Unfortunately, he play us like a damn fiddle. Jill: Let's get out of here first, I have contact brad for helicopter support. Chris: Thank Jill, here, take this MO Disk 2 with you. It looks like the key to decipher something. Jill: Alright, I will deal with him later. Chris: see ya. MO disk 2: albert -- Translation This is Jill: Chris, are you? Chris: Jill, you finally came. He was locked up in jail for a while. Apparently Whiskers are the mastermind. Jill, what? Wheesker? Is he a traitor? Chris: That's right, Jill. Unfortunately, he plays us like a damn violin. Jill Let's get out of here first, contact Brad for helicopter support. Chris: Thank you Jill, come on, take this MO disc 2. It seems like it will be the key to interpreting something. Jill: Okay, I'll talk to him later. Chris: See you later.The chris was in .jailcell.
There was also MO disk 2. It seems albert is the key.
Answer

Who is the traitor
Earlier, Chris said that weasker was a traitor.
Answer

The login password for the traitor
Now that I know the key, I'll try decoding it.
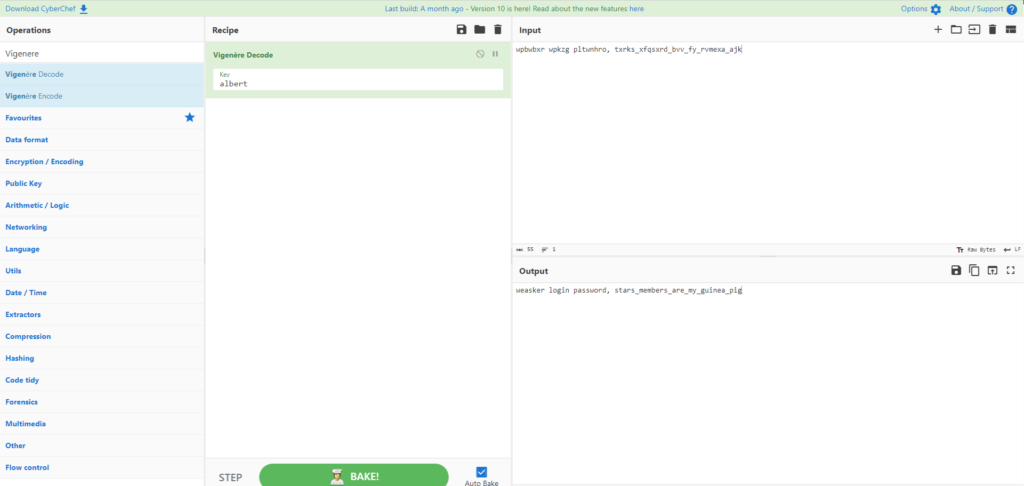
weasker login password, stars_members_are_my_guinea_pigIt was the weasker password.
Answer

The name of the ultimate form
Now that you know the password, switch the user to weasker with su.
umbrella_guest@umbrella_corp:~$ su weasker Password: weasker@umbrella_corp:/home/umbrella_guest$ cd weasker@umbrella_corp:~$ Let's check what's inside your home directory.
weasker@umbrella_corp:~$ ll total 80 drwxr-xr-x 9 weasker weasker 4096 Sep 20 2019 ./ drwxr-xr-x 5 root root 4096 Sep 20 2019 ../ -rw------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ weasker 4096 Sep 20 2019 .cache/ drwxr-xr-x 11 weasker weasker 4096 Sep 20 2019 .config/ drwxr-xr-x 2 weasker weasker 4096 Sep 19 2019 Desktop/ drwx--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- drwx--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2019 .Xauthority -rw------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------It seems weasker_note.txt is suspicious.
weasker@umbrella_corp:~$ cat weasker_note.txt Weaker: Finally, you are here, Jill. Jill: Weasker! stop it, You are destroying the mankind. Weasker: Destroying the mankind? How about creating a 'new' mankind. A world, only the strong can survive. Jill: This is insane. Weasker: Let me show you the ultimate lifeform, the Tyrant. (Tyrant jump out and kill Weasker instantly) (Jill able to stun the tyrant will a few powerful magnum round) Alarm: Warning! warning! Self-detruct sequence has been activated. All personal, please evacuate immediately. (Repeat) Jill: Poor bastard -- Translation weakened: Finally, Jill. Jill: Weeker! Stop it, I'll destroy humanity. Weeker: Will you destroy humanity? How about creating a new humanity? A world where only the strong can survive. Jill: I don't think I'm sane. Weesker: Show us the ultimate life form, Tyrant. (Tyrant pops out and kills Weesker instantly) (Jil can stun Tyrant with several powerful Magnum bullets) Alarm: Warning! Warning! The self-destruction device has been activated. All individuals should be evacuated immediately. (Repeat) This is Jill: Poor manIt seems to be called Tyrant.
Answer

The root flag
Finally, get the Root flag.
Try checking the permissions with sudo -l.
weasker@umbrella_corp:~$ sudo -l [sudo] password for weasker: Matching Defaults entries for weasker on umbrella_corp: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/snap/bin User weasker may run the following commands on umbrella_corp: (ALL : ALL) ALLYou can access almost all of your permissions.
If so, it's easy. Let's get root with sudo su.
weasker@umbrella_corp:~$ sudo su root@umbrella_corp:/home/weasker# whoami root root@umbrella_corp:/home/weasker# cd root@umbrella_corp:~# ls root.txt root@umbrella_corp:~# ll total 36 drwx-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- root root 3106 Apr 9 2018 .bashrc drwx------ 2 root root 4096 Apr 26 2018 .cache/ drwxr-xr-x 3 root root 4096 Sep 19 2019 .local/ -rw-r--- 1 root root 148 Aug 17 2015 .profile -rw-r--- 1 root root 493 Sep 20 2019 root.txt -rw-r--- 1 root root 207 Sep 19 2019 .wget-hsts root@umbrella_corp:~# cat root.txt In the state of emergence, Jill, Barry and Chris are reaching the helicopter and awaiting for the helicopter support. Suddenly, the Tyrant jump out from nowaday. After a tough fight, brad, throw a rocket launcher on the helicopter. Without thinking twice, Jill pick up the launcher and fire at the Tyrant. The Tyrant shredded into pieces and the Mansion was blown. The Survivor could escape with the helicopter and prepare for their next fight. The End flag: 3c5794a00dc56c35f2bf096571edf3bfNow you can also get the root flag!
Answer

summary
This time, we tried out CTF based on TryHackME's Resident Evil.
Wow, it was difficult. Game format? It was my first time at CTF, so it was quite satisfying.
I've been trying one by one to see how the hash is encoded, but is there any good tools? . .
I'll try to find it in the future.
References and Sites
Hassan Sheikh: https://infosecwriteups.com/tryhackme-biohazard-ctf-writeup-detailed-3d9dd491539e
Yebberdog: https://yebberdog.medium.com/try-hack-me-biohazard-walkthrough-4c43fda578ed


![[TryHackMe] Biohazard CTF Writeup! A detailed explanation in line with the flow!](https://hack-lab-256.com/wp-content/uploads/2023/04/hack-lab-256-samnail-18.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)