This time, we will be taking on TryHackMe Room, which is based on how to use Nmap.
"TryHackMe-Nmap: https://tryhackme.com/room/furthernmap "
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, let's prepare. There are two tasks.
* Translated in Japanese using Chrome. Please note that there may be some difficulties to see. . .
deployment
First, select "Start Machine" and launch the machine for scanning.
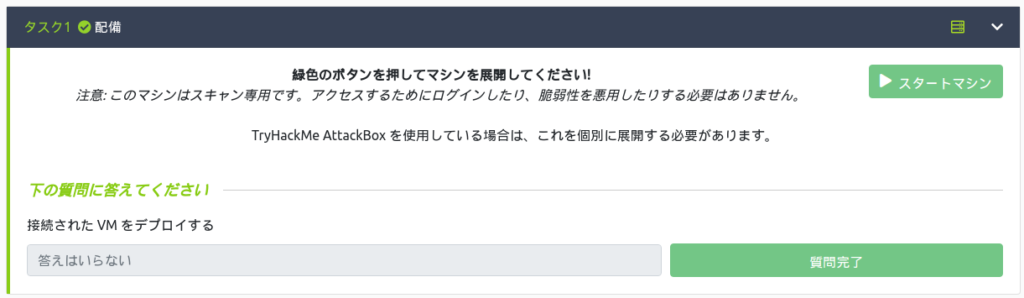
It's fine as long as the machine information is displayed like this.
Introduction
What is portscan? Why is that necessary? Why nmap? This is explained in a simple way.
I recommend reading this all the way through. My notes look like this:
- When connecting to a web page, you may open port:49534 and connect to port:443 on your server
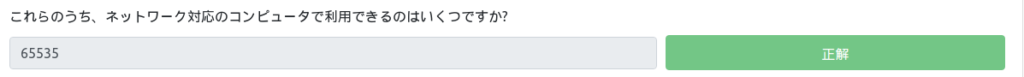
- The computer has a total of 65,535 available ports
- Many are registered as standard ports. (HTTP: 80, HTTPS: 443, Windows NETBIOS: 139, SMB: 445)
- If the server is not sure which port is open, it is impossible to attack the target (so port scanning is important).
- Why Nmap? Because it is currently an industry standard tool. Because other portscan tools can't compare to the capabilities of Nmap.
- Nmap can perform a variety of port scans
- The basic port scan is "Connect to each port ⇒ Check port response (closed, open, filtered (mainly FW) ⇒ enumerate services running on open ports)."
Let's take a quick understanding of the above and answer the questions.
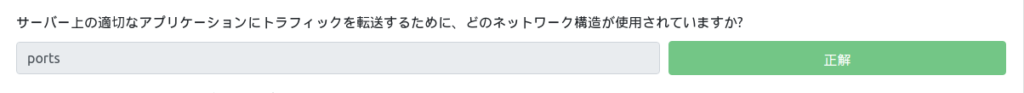
Which network structure is used to forward traffic to the appropriate applications on the server?
This was also mentioned in the explanation. At first I thought it was "port", but it was "ports". . .
How many of these are available on network-enabled computers?
How many well-known ports are there?
Please be careful as this will make it difficult to understand if translated in Chrome.
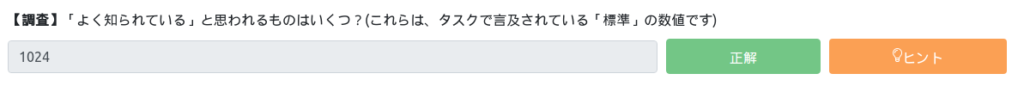
Well-known ports are port numbers from 0 to 1023 and are reserved for general TCP/IP applications.
This time, there are a few questions asked, so the answer is "1024".
Nmap Switches
Next, we will explain about Napm's switch.
This is a way to understand the problem while solving it.
Switch is apparently a command argument that instructs nmap to perform various processes.
What is the first switch listed in the "Syn Scan" Help menu
Let's do this quietly and run the following command:
nmap -h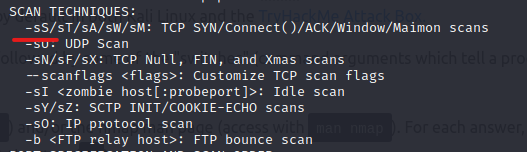
The answer is "-sS."
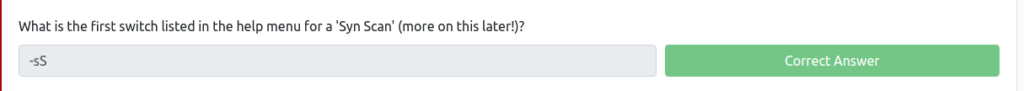
Which switch is used for "UDP Scan"?
Next is UDP scan.
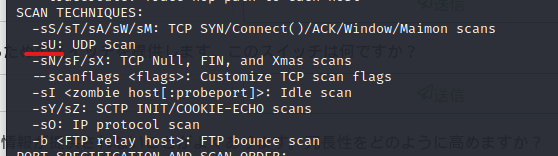
It's under the switch above.

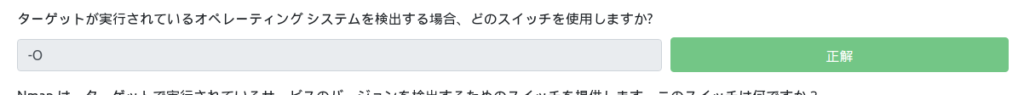
Which switch do you use to discover the operating system the target is running on?
Next is the switch that detects the OS.
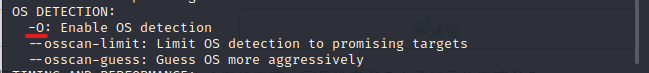
It was here.
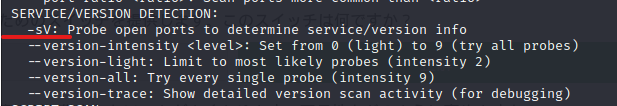
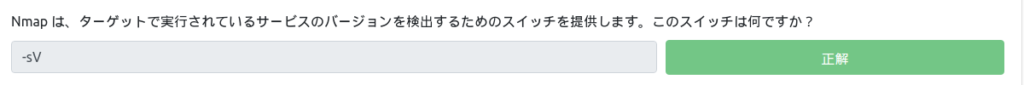
Nmap provides a switch to detect the version of services running on the target. What is this switch?
It's a switch for detecting the version of a service.
You can find it in SERVICE/VERSION DETECTION.
This one is also no problem.
The default output provided by nmap often does not provide sufficient information for the pentester. How do you increase redundancy?
Translation in Japanese is difficult, so let's go back to English.
Verbosity level one is good, but verbosity level two is better! How would you set the verbosity level to two?
https://tryhackme.com/room/furthernmap
Looking at it, it seems like you should look for a switch that will increase your verbosity level.
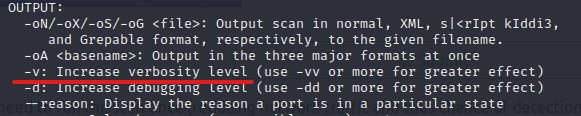
There was. I'll try to see how this will change the output later.
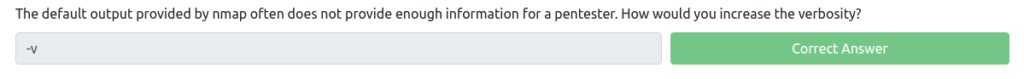
Detail Level 1 is good, but Detail Level 2 is better. How do I set the level of detail to 2?
This was in the previous (). "-vv" is the answer.
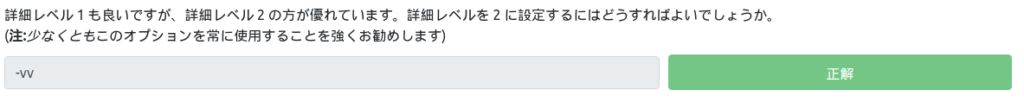
Which switch do you use to store nmap results in three main formats?
I thought I'd seen it on OUTPUT, so I was looking for it
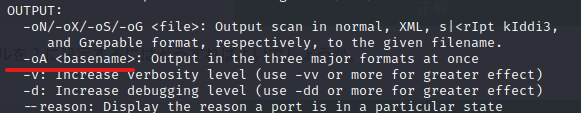
There was a description. "-oA" is the answer.
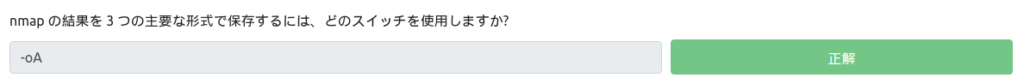
Which switch do you use to save nmap results in "regular" format?
It was on the switch above. "-oN" is correct.
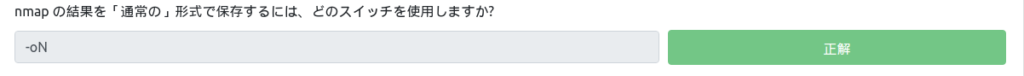
Very useful output format: How can I save the results in "grep-enabled" format?
Japanese is a little difficult to understand. . .
However, it is listed in the same place as before. It's a Grepable format.
So "-oG" is the answer.
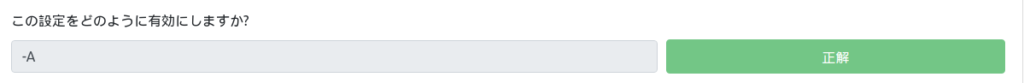
How do I enable aggressive mode?
There are various switches to enable.
You might want to look for a switch that will enable all of these.
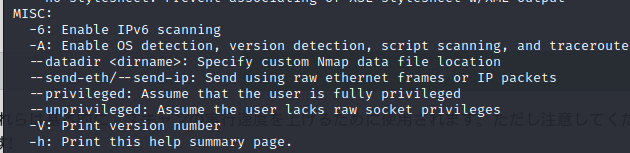
The answer is "-A."
How do I set the timing template to level 5?
For timing switches, you should look at TIMING AND PERFORMANCE.
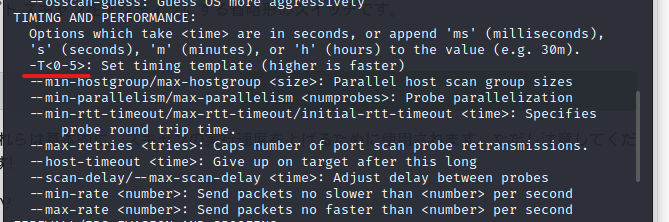
I want to level 5, so "-T5" is the correct answer.
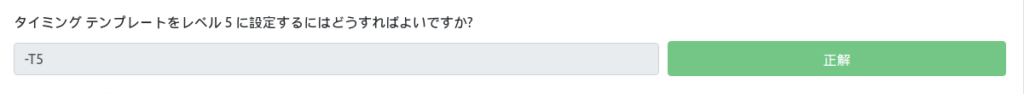
How do you tell nmap to scan only port 80?
Find the switch you want to narrow down the ports you want to scan.
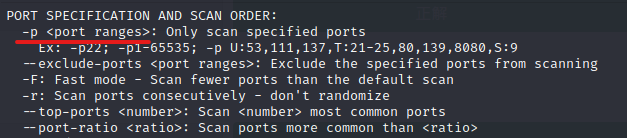
Is it possible to add port ranges to -p?
Since it's only port 80, -p 80 seems to be correct.

How do you tell nmap to scan ports 1000-1500?
It seems that the switch is the same as before.
Since it's 1000-1500, "-p 1000-1500" is probably the correct answer.

How do you tell nmap to scan all ports?
I didn't know this so I did some research.
"-p-" is the answer. I guess it's treated like an abbreviation for "-p 0-65535".

How do I enable scripts from the nmap script library?
It was stated on SCRIPT SCAN.
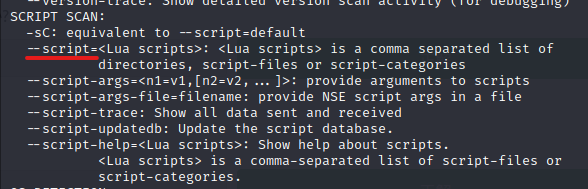
"–script=" is the answer.
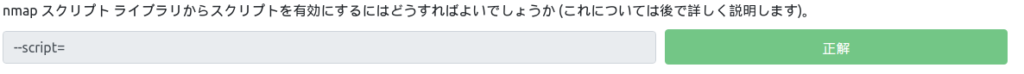
How do you activate all the scripts in the "Vulnerability" category?
It's a bit unclear in Japanese, so think about it in English.
How would you activate all of the scripts in the “vuln” category?
https://tryhackme.com/room/furthernmap
It looks like you use the switch mentioned earlier to enable vuln.
I think "–script=vuln" is fine.
As for Nmap Switches, that's it.
It has a wide range of functions, so I think it's more important to be able to use it by looking at the help and find it useful rather than memorizing it. . .
[Scan Type] Overview
Read the explanation here and once you understand it, you'll be done.
I'll leave my notes here.
- -sT: TCP connection scan
- -sS:SYN (harf-open) scan
- -sU:UDP Scan
- The following is not general
- -sN: TCP Null Scan
- -sF: TCP FIN Scan
- -sX: TCP Xmas Scan
[Scan type] TCP Connect Scan
There is information about TCP Connect scans.
Finally, there's a little problem.
For now, let's understand the explanation.
- TCP Connect Scan works by running 3 Way Handshake
- That is, you can connect to each TCP port and check if the service is open by replying
- If sent to a closed port, a TCP packet with the RST flag is responded
- If sent to an open port, a TCP packet with the SYN/ACK flag set will be answered
- When there is an FW, many FWs are configured to DROP the packet.
Therefore, even if you send a TCP SYN request, nothing will be returned. This can be considered protected by the FW. - By configuring the FW to respond with RST TCP packets, it can act as if it was closed.
In Linux IPtables, it can be supported by "iptables -I INPUT -p tcp -dport -j REJECT -reject-with tcp-reset".
This can make reading very difficult.
There is a problem so I'll post the answer.
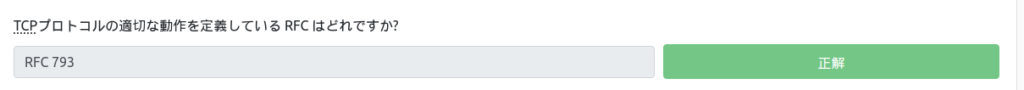
Which RFCs define the proper behavior of the TCP protocol?
This was at the top of the explanation.
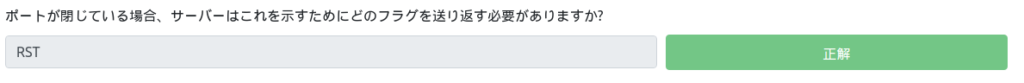
If the port is closed, what flag should the server send back to indicate this?
This is also in my notes.
The FW can be said to be difficult to read by responding "RST" and pretending to be closed.
[Scan type] SYN scan
Next, let's talk about SYN scans.
There are various explanations, so I'll read them.
- SYN scans are also known as half-open scans or stealth scans.
- After receiving a SYN/ACK, replying with RST does not completely establish a 3-way handshake.
- Older intrusion detection systems monitor the full 3-way handshake so you can avoid it
- In general, SYN scans are not recorded because the connection is fully established
- 3 No need to complete (and disconnect) Way Handshake, faster than TCP Connect scan
- Sodu permissions are required to work properly on Linux. Because the ability to create raw packets is required.
- SYN scans on unstable services may cause the service to go down
Now let's answer the question.
There are two other names for SYN scan, what are they?
This is easy.
Write half-open and stealth in English.

Can Nmap use SYN scans without sudo permissions (Y/N)?
The answer is No.
You need sodu permissions, and the reason is that you need the ability to create raw packets.

[Scan type] UDP scan
Let's read the explanation about UDP scanning.
- UDP just keeps sending packets to the target port and expects success
- UDP is often used for connections that rely more on speed than quality (such as video sharing).
- No acknowledgement makes scanning much more difficult
- If a packet is sent, if there is no response, it is open or protected by FW (it is difficult to identify)
- Rarely, if a response is returned, it will be marked as open
- If answered with an ICMP packet, it is recognized as a closed port.
Because UDP does not respond, it is difficult to determine whether it is actually open.
Now, let's solve the problem.
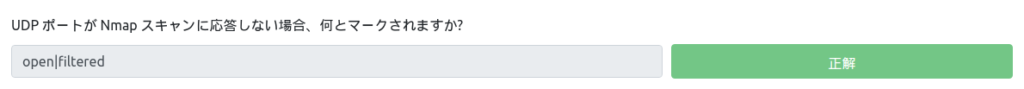
What is marked if a UDP port does not respond to an Nmap scan?
Since UDP is not known whether it is open or DROP in FW, it will be marked "open|filtered".
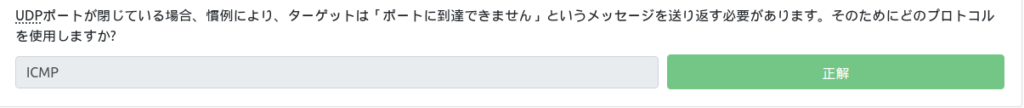
If the UDP port is closed, by convention, the target must send a message "port cannot be reached" back. Which protocol do you use for that?
This was also mentioned in the explanation. You need to respond with an ICMP (ping) packet that contains a message that the port cannot be reached, right?
[Scan type] NULL, FIN and Xmas
It contains explanations about NULL scans, FIN scans, and Xmas scans.
Understand this in the same way before proceeding to the question.
- Scanning methods are not commonly used
- A NULL scan sends a TCP request with no flags. According to the RFC, if the port is closed, an RST is responded.
- A FIN scan is sent using the FIN flag, whereas a null scan sends a completely empty packet.
Verify that the port is closed by RST replying. - Xmas Scan: Basically, I expect an RST response. Scan by sending malformed TCP packets.
- RFC793 simply requires that open ports not respond at all.
- For example, Microsoft Windows responds with RST to malformed TCP packets regardless of whether the port is actually open. ⇒This will make it appear as if all ports are closed.
Now let's answer the question.
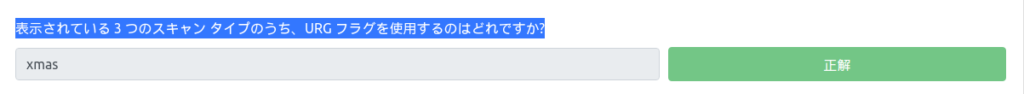
Of the three scan types shown, which use the URG flag?
As explained, this is an "xmas scan".
Why are NULL, FIN, Xmas scans commonly used?
It looks a bit weird in Japanese.
Rather, it's like, "What are the common purposes for NULL, FIN, and Xmas?"
If that's the case, the purpose of this was to avoid FWs, so "firewall evasion" is the answer.

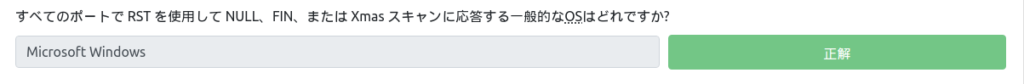
Which OS is a common one that responds to NULL, FIN, or Xmas scans using RST on all ports?
This was also in my notes. "Microsoft Windows" is the answer.
[Scan type] ICMP Network Scan
This is the last time I'll explain the scan.
This seems to be a scan to see which IP addresses contain the active host.
- Sends ICMP packets to each possible IP address on the specified network.
Once a response is received, the IP address becomes valid. - This is called ping sweep.
- It's not necessarily accurate, but it's worth doing it as a base.
I will answer the questions.
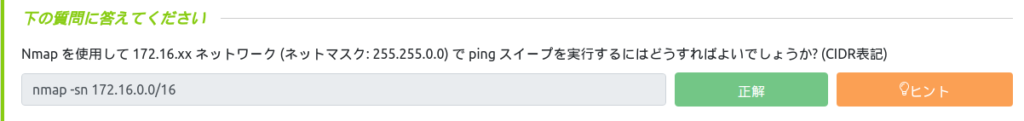
How can I perform a ping sweep on a 172.16.xx network (netmask: 255.255.0.0) using Nmap? (CIDR notation)
The CIDR for Class B network is /16, so the answer is "nmap -sn 172.16.0.0/16".
[NSE] Overview
Up until now I've learned a lot about scanning, but from here on I've become an NSE.
The NSE is written in Lua and seems to be able to do a variety of things, from vulnerability scanning to automating Exploit.
- safe: Does not affect targets
- intrusive: Possible to affect targets
- vuln: vulnerability scan
- exploit: exploit vulnerability
- auth: Attempt to avoid authentication of a running service (e.g. log in anonymously to an FTP server)
- brute: Attempt to brute force authentication information to run the service
- discovery: Query the running service for more information about the network (for example, query the SNMP server)
There seem to be many other things, but I think I'll try using them again and remember them.
Now, let's answer.
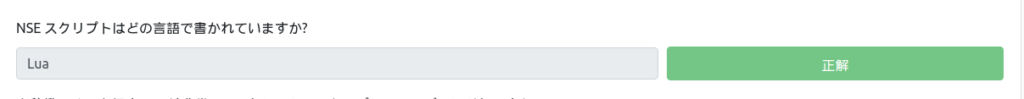
In which language is the NSE script written?
It's Lua.
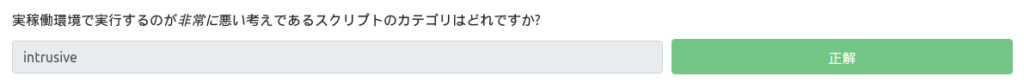
Which category of scripts is a very bad idea to run in a production environment?
The problem is "intrusive", which affects the target.
[NSE]
Here's just how to use it.
If you use it in particular, you'll probably be able to remember, so you'll just solve the problems and finish it.
What optional arguments can the ftp-anon.nse script take?
So I tried doing the following:
nmap --script-help ftp-anon.nse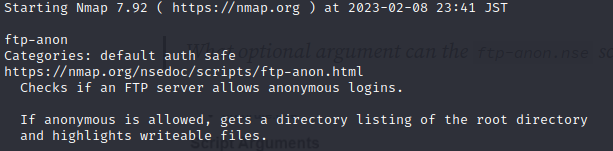
I'll open the link.
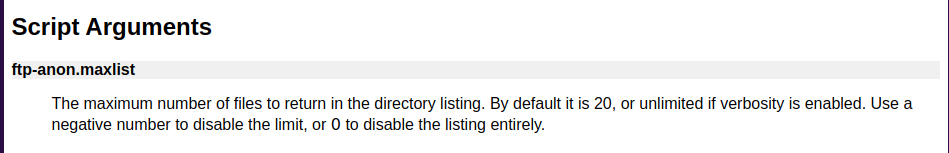
The argument is apparently "maxlist".
[NSE] Script search
This is basically an explanation of how to use it, so I will only answer the questions.
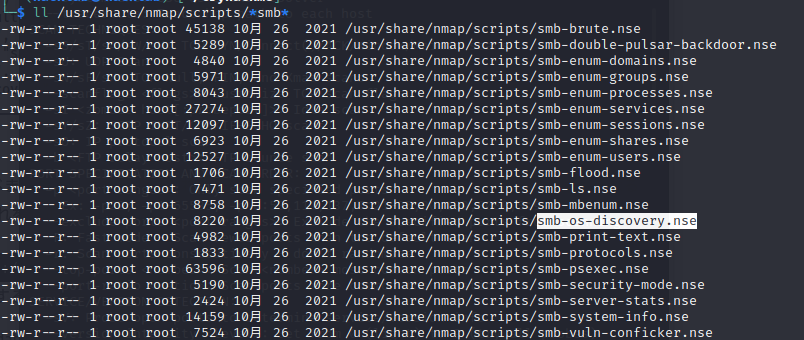
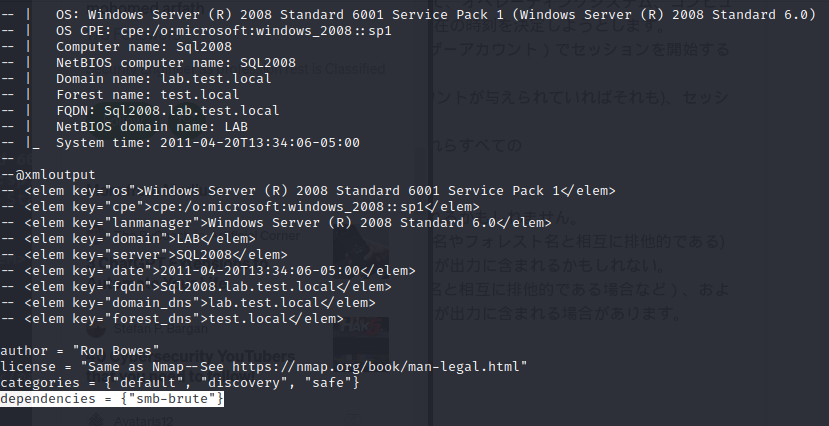
Search for the "smb" script in the directory using one of the methods shown. What is the filename for the script that determines the underlying OS of an SMB server?
This time I'll try searching using ls -l.
ll /usr/share/nmap/scripts/*smb*There are various scripts that support smb, but it's "smb-os-discovery.nse."
Please read this script. What does it depend on?
They are told to read the script, so read it quietly.
cat /usr/share/nmap/scripts/smb-os-discovery.nseWhen I looked for the dependency, it said "smb-brute."

Avoiding the firewall
Because regular Windows hosts block all ICMP packets with the default firewall, Nmap disables hosts with this firewall configuration and no longer scans at all.
So there's a way to get around this.
- Before scanning the host, avoid pinging every time, and Nmap always treats the target host as alive.
- However, it takes a very long time, so be careful.
Now let's answer the question.
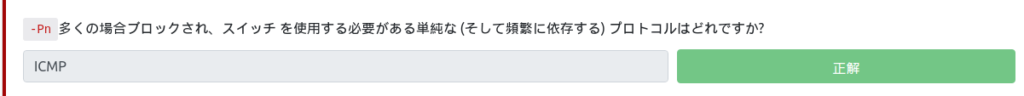
Which simple (and often dependent) protocols are often blocked and require the use of -Pn switches?
Is the -Pn switch to prevent ICMP packets from being blocked?
[Survey] Which Nmap switches allow you to add random data of any length to the end of a packet?
Let's take a look at nmap's help.
nmap -help 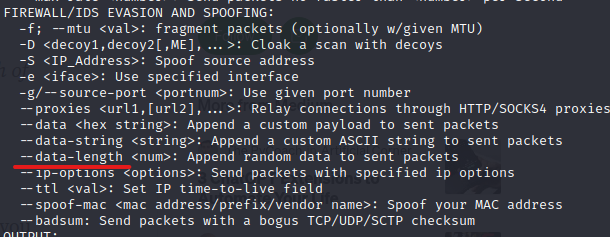
It says "–data-length" to add random data.
Practice
From here on, it's a practical idea! ! (at last...)
Now let's do our best while answering the questions.
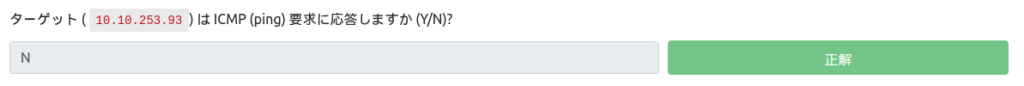
Does the target (10.10.253.93) respond to ICMP (ping) requests (Y/N)?
Now, let's send a ping appropriately.
PING 10.10.253.93 (10.10.253.93) 56(84) bytes of data. --- 10.10.253.93 ping statistics --- 5 packets transmitted, 0 received, 100% packet loss, time 4094msIt didn't respond to the request, so it's "N".
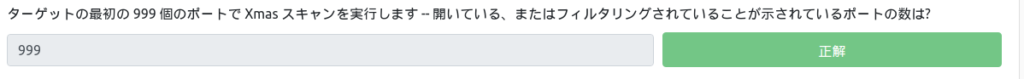
Run a Xmas scan on the first 999 ports on the target — what number of ports are shown to be open or filtered?
$ sudo nmap -sX -p 1-999 10.10.156.142 Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-09 00:58 JST Note: Host seems down. If it is really up, but blocking our ping problems, try -Pn Nmap done: 1 IP address (0 hosts up) scanned in 3.14 secondsThis was no good. Since ping will not pass, you will need to attach -Pn.
$ sudo nmap -sX -p 1-999 10.10.156.142 -Pn -vv Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-09 01:00 JST Initiating Parallel DNS resolution of 1 host. at 01:00 Completed Parallel DNS resolution of 1 host. at 01:00, 0.00s elapsed Initiating XMAS Scan at 01:00 Scanning 10.10.156.142 [999 ports] XMAS Scan Timing: About 15.52% done; ETC: 01:03 (0:02:49 remaining) XMAS Scan Timing: About 30.53% done; ETC: 01:03 (0:02:19 remaining) XMAS Scan Timing: About 45.55% done; ETC: 01:03 (0:01:49 remaining) XMAS Scan Timing: About 60.56% done; ETC: 01:03 (0:01:19 remaining) XMAS Scan Timing: About 75.58% done; ETC: 01:03 (0:00:49 remaining) Completed XMAS Scan at 01:03, 201.93s elapsed (999 total ports) Nmap scan report for 10.10.156.142 Host is up, received user-set. Scanned at 2023-02-09 01:00:14 JST for 201s All 999 scanned ports on 10.10.156.142 are in ignored states. Not shown: 999 open|filtered tcp ports (no-response) Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 202.00 seconds Raw packets sent: 1998 (79.920KB) | Rcvd: 0 (0B)
Now I know that open|filtered is 999.
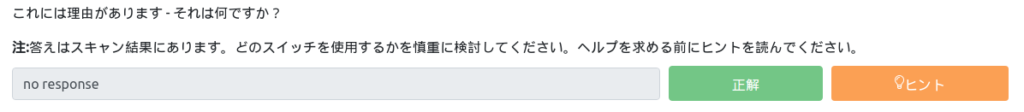
There's a reason for this – what is it?
I just added -vv, so the reason is written.
That means it's no response.
Perform a TCP SYN scan on the first 5000 ports of the target. How many open ports are there?
$ sudo nmap -sS -p 1-5000 10.10.156.142 -Pn -vv Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-09 01:12 JST Initiating Parallel DNS resolution of 1 host. at 01:12 Completed Parallel DNS resolution of 1 host. at 01:12, 0.00s elapsed Initiating SYN Stealth Scan at 01:12 Scanning 10.10.156.142 [5000 ports] Discovered open port 135/tcp on 10.10.156.142 Discovered open port 21/tcp on 10.10.156.142 Discovered open port 53/tcp on 10.10.156.142 Discovered open port 80/tcp on 10.10.156.142 Discovered open port 3389/tcp on 10.10.156.142 Completed SYN Stealth Scan at 01:13, 37.75s elapsed (5000 total ports) Nmap scan report for 10.10.156.142 Host is up, received user-set (0.27s latency). Scanned at 2023-02-09 01:12:25 JST for 38s Not shown: 4995 filtered tcp ports (no-response) PORT STATE SERVICE REASON 21/tcp open ftp syn-ack ttl 127 53/tcp open domain syn-ack ttl 127 80/tcp open http syn-ack ttl 127 135/tcp open msrpc syn-ack ttl 127 3389/tcp open ms-wbt-server syn-ack ttl 127 Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 37.82 seconds Raw packets sent: 10017 (440.748KB) | Rcvd: 27 (1.188KB)
Looking at this, you can see that open is 5.

Expand the script against the box. Can ftp-anonNmap successfully log in to the FTP server on port 21? (Yes/No)
$ nmap --script=ftp-anon -p 21 10.10.156.142 -vv Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-09 01:21 JST NSE: Loaded 1 scripts for scanning. NSE: Script Pre-scanning. NSE: Starting runlevel 1 (of 1) scan. Initiating NSE at 01:21 Completed NSE at 01:21, 0.00s elapsed Initiating Ping Scan at 01:21 Scanning 10.10.156.142 [2 ports] Completed Ping Scan at 01:21, 0.26s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 01:21 Completed Parallel DNS resolution of 1 host. at 01:21, 0.00s elapsed Initiating Connect Scan at 01:21 Scanning 10.10.156.142 [1 port] Discovered open port 21/tcp on 10.10.156.142 Completed Connect Scan at 01:21, 0.26s elapsed (1 total ports) NSE: Script scanning 10.10.156.142. NSE: Starting runlevel 1 (of 1) scan. Initiating NSE at 01:21 NSE Timing: About 0.00% done Completed NSE at 01:22, 31.32s elapsed Nmap scan report for 10.10.156.142 Host is up, received syn-ack (0.26s latency). Scanned at 2023-02-09 01:21:49 JST for 31s PORT STATE SERVICE REASON 21/tcp open ftp syn-ack | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_Can't get directory listing: TIMEOUT NSE: Script Post-scanning. NSE: Starting runlevel 1 (of 1) scan. Initiating NSE at 01:22 Completed NSE at 01:22, 0.00s elapsed Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 32.00 seconds
You have probably confirmed that you were able to log in using "ftp-anon: Anonymous FTP login allowed (FTP code 230)."
summary
This time, I tried out TryHackMe Room to learn how to use Nmap.
Nmap is a powerful network scanning tool, but it's rich in functionality so it will take some time to master it.
I think it would be good to try a lot of things and master how to use it.


![[TryHackMe] I tried using Nmap, a powerful network scanning tool! Nmap Writeup](https://hack-lab-256.com/wp-content/uploads/2023/02/hack-lab-256-samnail-1.jpg)

![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)