"I tried creating a bulletin board app that can use HTML tags!"
What if a work by a beginner engineer would be "taken over" with just one line post
we will introduce a demonstration using an example of
Cross-Site Scripting (XSS) the basics of security, and explain how vulnerable sites are actually attacked
🎬If you want to watch the video, click here
▶ Watch the demo on YouTube
💻If you want to actually try it, click here
🔗 GitHub repository (XSS demo code)
*This content is for
educational purposes and security awareness It is not intended to attack actual services or third parties.
- The crisp typing feel that is unique to the capacitive non-contact system!
- REALFORCE's first wireless compatible device! Wired connection also available!
- Unlike the HHKB, the Japanese keyboard layout has no quirks and is easy for anyone to use!
- Equipped with a thumb wheel, horizontal scrolling is very easy!
- It also has excellent noise reduction performance, making it quiet and comfortable!
- Scrolling can be switched between high speed mode and ratchet mode!
What is XSS (Cross Site Scripting)?
XSS (Cross-Site Scripting) is an attack in which malicious
scripts (such as JavaScript) are injected onto a web page and executed
For example, if the following code is posted on the message board or comment section,
<img src="invalid.jpg" onerror="alert('XSS')">another user sees the page may be stolen.
Possible damage caused by XSS
- Theft of user cookies and session information
- A selfish page redirection (phishing)
- Web app UI tampering and inserting fake forms
- Advertising fraudulent display and lead to fraudulent links
Why does XSS occur?
XSS occurs when a developer "displays user input directly on the screen."
- What the user sentor
I just embed it ininnerHTML - "You can use HTML freely," allowing tags to be entered.
- No filtering or sanitization processing to prevent JavaScript execution
With this design, attackers can "inject" illegal source code into HTML
Dangerous code examples
postContainer.innerHTML += `<p> ${userInput}</p> `;At first glance, it looks like a normal display process, but the userInput contains the following code?
<img src="invalid.jpg" onerror="alert('XSS')">this
at that time alert('XSS') installed in oneror will be executed.
This example may look harmless since alert
<img src="x" onerror="location='https://hack-lab-256.com/'">This can cause
realistic damage , such as users who open the message board automatically redirected to malicious sites Of course, if you obtain cookies, you may be able to log in unauthorizedly.
How do hackers find attacks?
Actual attackers (hackers) observe and investigate published web apps to identify vulnerabilities.
- Check the URL and form
⇒ Are there any input fields? Can I enter HTML tags? - Check the results of the post
⇒"Try a test string like" - Find a developer's mistake
⇒ Are there any parts that useinnerHTMLAre there any areas that have not been filtered or escaped? - Write the preparation code
⇒
The typical XSS attack string is as follows:
Of course, they attack in a wide variety of other ways.
| kinds | Attack code | Features and Notes |
|---|---|---|
| <script>alert('XSS')</script> | A classic among the classics. Recently, it is often disabled in innerHTML |
<img onerror> | <img src="x" onerror="alert('XSS')"> | High success rate. Alert fire when image loading fails |
<svg onload> | <svg onload="alert('XSS')"></svg> | SVG is よりブロックされにくい。シンプルで強力 |
| <iframe src="javascript:alert('XSS')"></iframe> | It doesn't run in some browsers, but it was effective in older environments. |
I actually tried hacking it with XSS!!
Now, I'll actually try hacking web apps using XSS.
The code is published, so I think it would be good if you could try it while running it on your own PC.
*Distributed via docker.
💻If you want to actually try it, click here
🔗 GitHub repository (XSS demo code)
*This is a demonstration for security education. This video does not recommend unauthorized access.
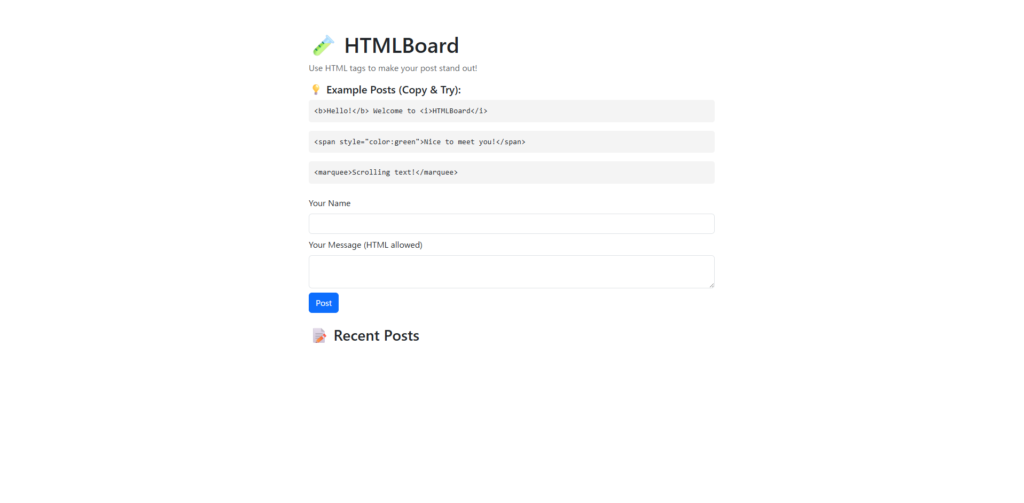
A New Engineer Challenge: We've created a bulletin board that allows you to use HTML tags!
I've been programming for six months now, and I'm still a beginner engineer.
I thought, "I want to create a web app that can be moved with my own hands!" and decided to create a message board app.A super simple design that will be displayed as is when posted.
What's more, we've also made it possible to use HTML tags to customize the appearance.happy when it was implemented and
seriously thought, "Isn't this going to go buzz a bit?"
With this kind of story in mind, we created a "Bulletin Board App" that can use HTML tags.
Main features:
- Enter your name and message in the post form and send it and it will appear immediately below
- Messages are displayed with HTML tags, so you can change the text color and size, and display images.
- Post content is saved on the server and continues to display even after reloading the page
You can change the color of the text like this!
Actual behavior
- You can use tags such as
boldorred text - "Playable bulletin board" that is fun to customize at first glance
However, this high degree of freedom leads to a "single pitfall"...
Hackers appear: Scouting the message board
He found a message board.
It looks simple and anyone can post freely.When you look at the post form, you simply enter your name and message.
Moreover, the posted content appears to be displayed as HTML."Hmm...
Will the tag pass?
"This is も通っちゃったりして?」He lightly peeks through the source and opens DevTools in his browser.
ApparentlyinnerHTMLis used and not filtered.── "I see. This is...can be used."
With this kind of story in mind, we will try scouting the message board app.
Check what tags are passing
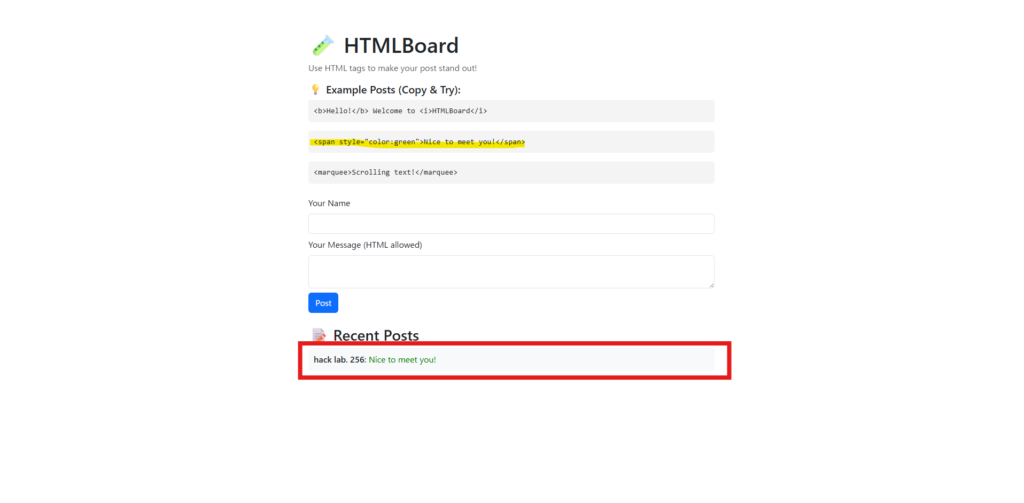
This is a bulletin board that can be customized with HTML tags, so I think you can use HTML tags, but to see if there are any restrictions, I'll try running an HTML tag that can use XSS.
<script>alert('xss')</script> ← Will the script tag be passed?<img src="x" onerror="alert('xss')"> ← Does the event attribute work?<svg onload="alert('xss')"></svg> ← Execute attributes of SVG tags<iframe src="https://hack-lab-256.com/"></iframe> ← Is iframe embedding allowed? <math><mtext></mtext><script>alert(1)</script> </math>← Check script tag bypassFirst, I posted a script tag.
<script>alert('xss')</script>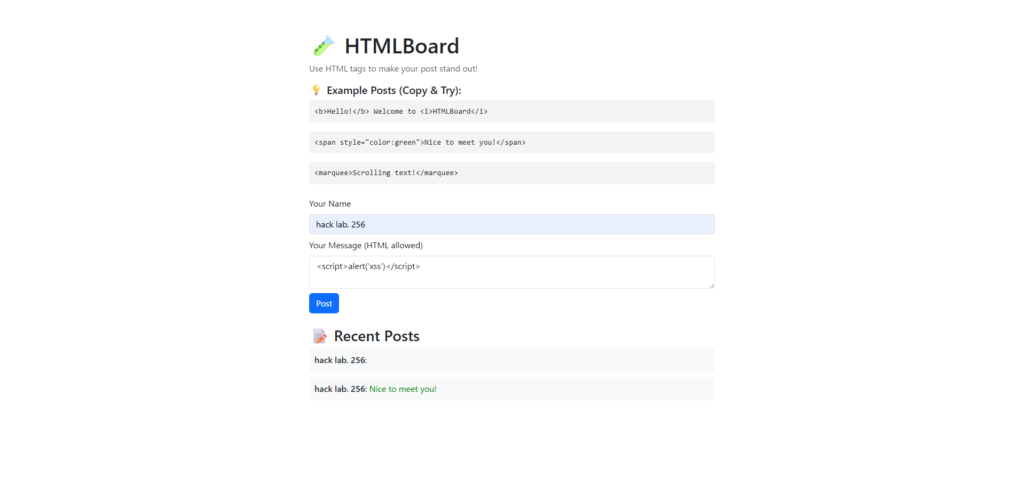
This was displayed, but no alerts were issued.
This is due to the browser's specification that script tags are not executed in innerHTML
Next, I tried posting an iframe tag.
<iframe src="https://hack-lab-256.com/"></iframe>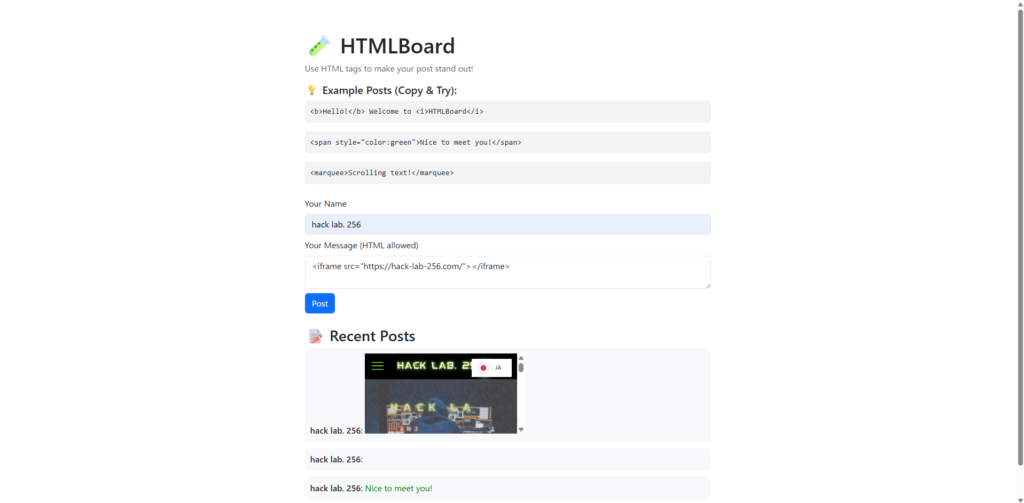
This page has been successfully embedded .
It's not XSS, but it could be a stepping stone for phishing and clickjacking
<iframe src="javascript:alert('XSS')"></iframe>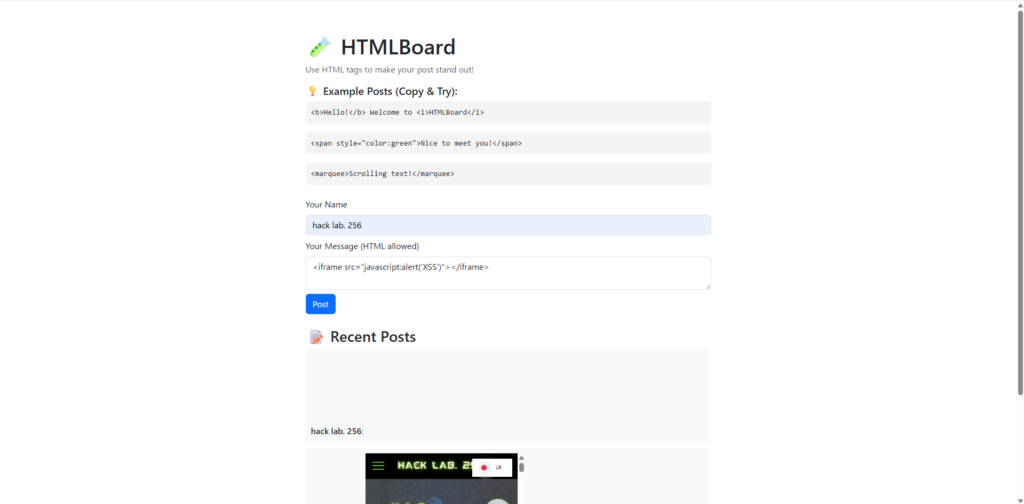
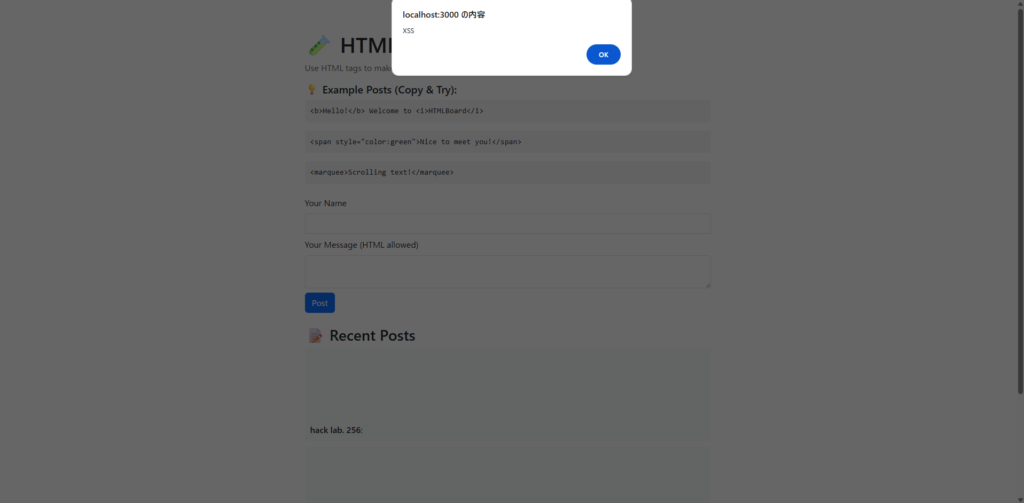
Surprisingly, an alert was executed.
It is often blocked in normal browsers, but
on this message board src="javascript:..." is still working.
I'll also post the img tag.
<img src="x" onerror="alert('img-xss')">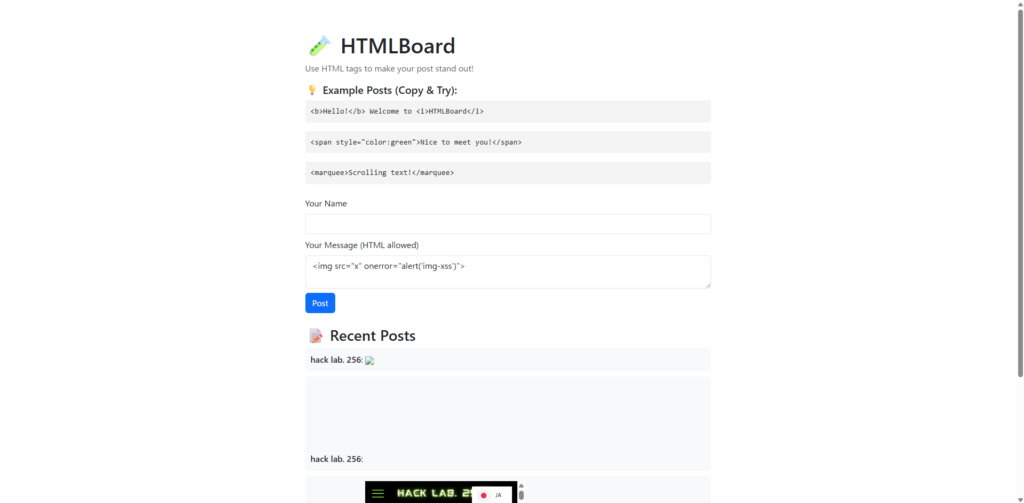
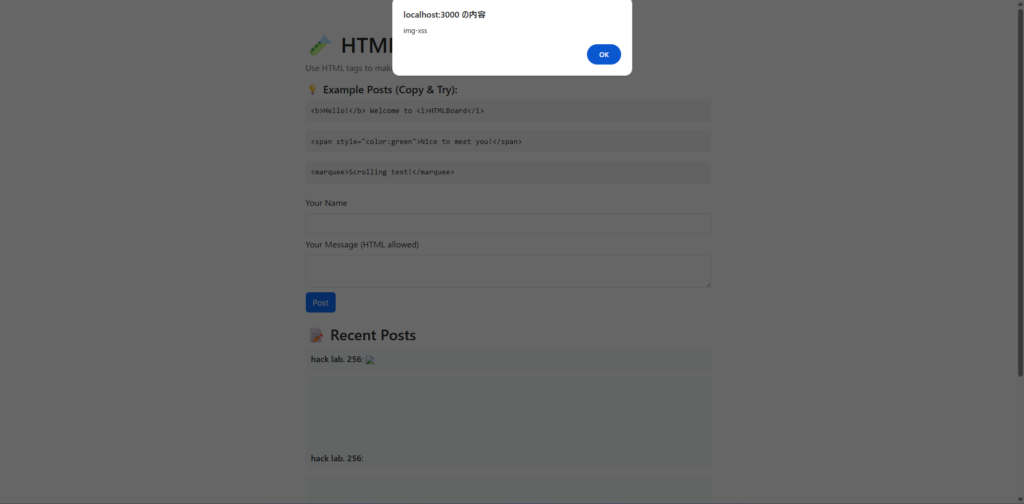
This is one of the commonly used XSS techniques, and executing JavaScript in case of an image loading error .
When I posted, an alert was fired the moment I viewed the page.
Check the source code too
We were able to confirm in the previous experiment that XSS is actually possible, but just to be sure, check the source code
If it is implemented in client-side JavaScript, you can also view the code directly from DevTools .
Looking at the code
, it was using the process of inserting the content of the post as is innerHTML
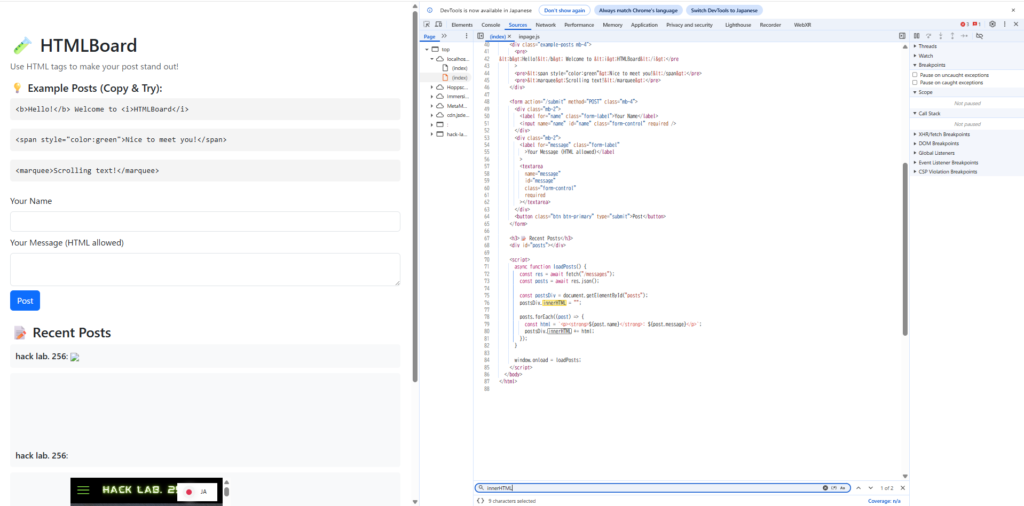
you can see that the posted messages are also displayed on the screen with tags without being sanitized
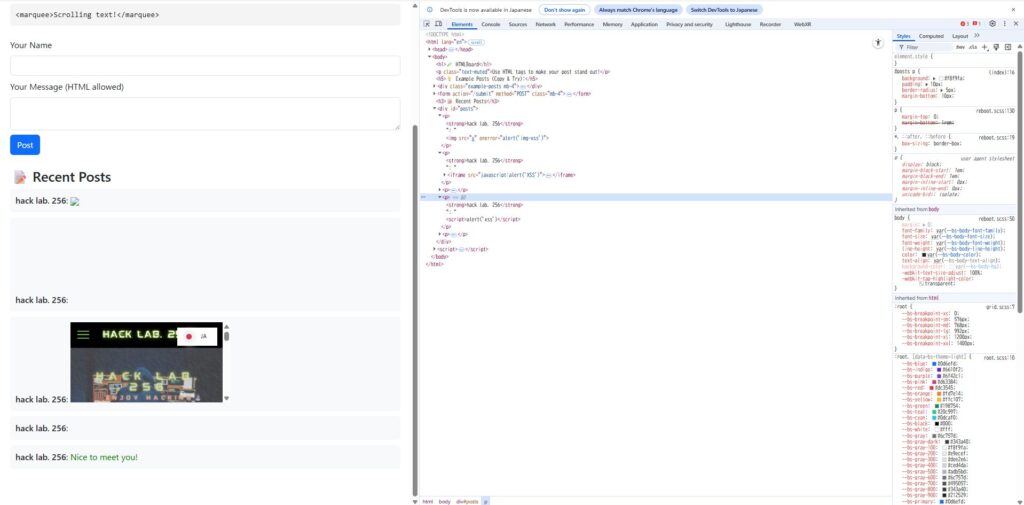
At this point it has become clear
that the message board is a "script-executable environment." In other words, it seems safe to say that you are ready to attack
Run: Try redirecting to your site using XSS
In the reconnaissance so far, we found that the message board displays posts with HTML tags as is, and
that the JavaScript event attributes (such as onerror) are not blocked.
So I'll post the code below.
<img src="x" onerror="location='https://hack-lab-256.com/'">This mechanism involves attempting to load an image that does not exist and causing an error, and
the onerror attribute is executed when that error occurs
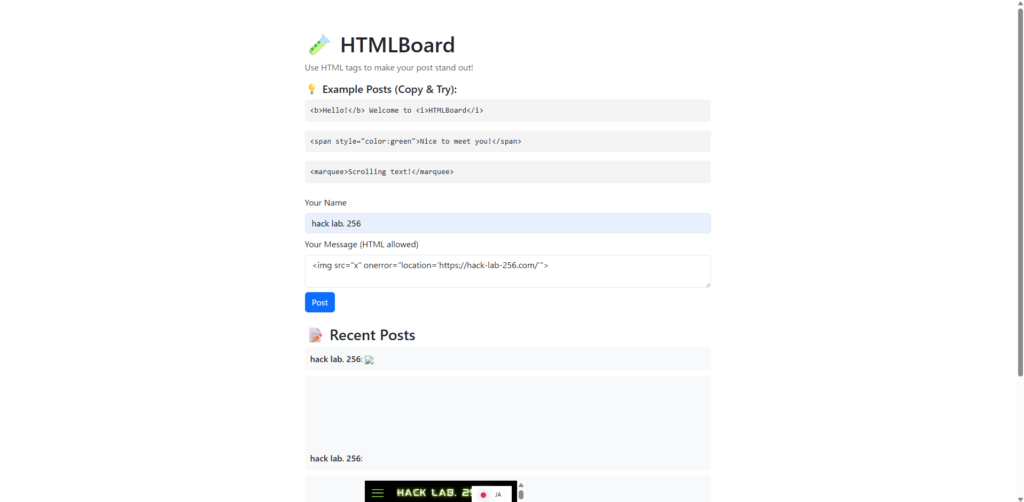
After submitting my post, I opened the message board page and
it automatically redirected to https://hack-lab-256.com/
An attack is established in which the user has not been operating anything but simply displaying the message board and the attacker is forced to transition to the site designated by the attacker

From this point onwards, this site will not be available for use. This phenomenon has led to the forced transition to this site.
In this way, just one line of code can cause damage to the overall trust of the message board
Previous case: XSS was also occurring on YouTube
In July 2010 (currently revised),
the comments section was added タグを含めることで JavaScript が実行されてしまうという、深刻なXSS脆弱性が存在していました。
Vulnerability details
On YouTube, it is originally in the comments section. などの危険なタグが入力された場合、
自動で無効化(エスケープ)する仕組みになっていました。
However, the implementation at the time was the first タグだけが正しくエスケープされ、2つ目以降はそのまま通ってしまうという重大な処理漏れがあったのです。
✅ Multiple タグを投稿すれば、実行可能なコードが差し込めた
What actually happened
Shortly after the vulnerability was made public, malicious users embedded the script into numerous video pages.
- Show fake popup messages
- Displays a dialogue that imitates a fake news article
- Redirecting to a malicious external site
It is said that some codes stole cookie information and displayed fake login pages.
What's in common with this demo
The XSS demo I went to this time and the YouTube case study are very similar in structure.
- "Embed code in the post field"
- "JavaScript runs when viewed"
- "Redirects and other damages occur."
Although this demonstration intentionally omitted the escape process, actual attackers are aiming for such "minor filtering errors .
Many XSS vulnerabilities have been discovered in the past, and even major web services are no exception .
If you're interested, please check out other examples.
Finally
we showed how
an XSS attack was carried out in which a web page could be taken over by posting just one line of code on a simple bulletin board that can use HTML tags
XSS is often thought to be "it happens because it's an app created by beginners," but
a very realistic threat that has been seen in major services such as YouTube and Google in the past .
Nowadays, we can automatically generate apps using AI.
It is becoming increasingly important to be aware of whether it works safely , rather than just "just move it, it's OK
Even services you have created can easily be taken over in just one line
📺 YouTube introduces this content in an easy-to-understand video.
We will continue to provide security explanations and demos, so
if you don't want to miss out on the latest information, please subscribe to our channel!
🎬If you want to watch the video, click here
▶ Watch the demo on YouTube
💻If you want to actually try it, click here
🔗 GitHub repository (XSS demo code)


![[XSS Demo] I tried hacking a website in just one line!!](https://hack-lab-256.com/wp-content/uploads/2025/07/hack-lab-256-samnail-23.jpg)